CCNA – Access List Questions
Here you will find answers to CCNA Access list questions
Note: If you are not sure about how to use Access list, please read my Access list tutorial
Question 1
Your boss is learning a CCNA training course, refer to the exhibit. The access list has been configured on the S0/0 interface of router RTB in the outbound direction. Which two packets, if routed to the interface, will be denied? (Choose two)
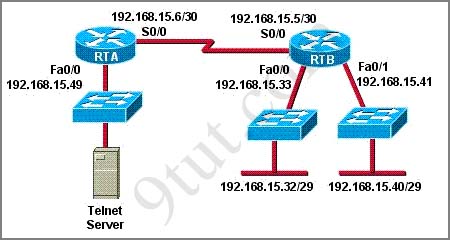
access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
access-list 101 permit ip any any
A. source ip address: 192.168.15.5; destination port: 21
B. source ip address: 192.168.15.37 destination port: 21
C. source ip address: 192.168.15.41 destination port: 21
D. source ip address: 192.168.15.36 destination port: 23
E. source ip address: 192.168.15.46; destination port: 23
F. source ip address: 192.168.15.49 destination port: 23
Answer: D E
Explanation
First we notice that telnet uses port 23 so only D, E & F can satisfy this requirement.
The purpose of this access-list is to deny traffic from network 192.168.15.32 255.255.255.240 (to find out the subnet mask just convert all bit “0″ to “1″ and all bit “1″ to “0″ of the wildcard mask) to telnet to any device. So we need to figure out the range of this network to learn which ip address will be denied.
Increment: 16
Network address: 192.168.15.32
Broadcast address: 192.168.15.47
-> Only 192.168.15.36 (Answer D) & 192.168.15.46 (Answer E) belong to this range so they are the correct answer.
Question 2
Refer to the graphic. It has been decided that PC1 should be denied access to Server. Which of the following commands are required to prevent only PC1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two)
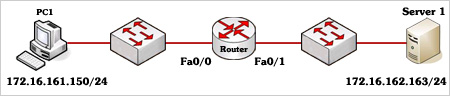
A – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 out
B – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 in
C – Router(config)# access-list 101 deny ip host 172.16.161.150 host 172.16.162.163
Router(config)# access-list 101 permit ip any any
D – Router(config)# access-list 101 deny ip 172.16.161.150 0.0.0.255 172.16.162.163 0.0.0.0
Router(config)# access-list 101 permit ip any any
Answer: B C
Question 3
Refer to the exhibit. Why would the network administrator configure RA in this manner?

A. to give students access to the Internet
B. to prevent students from accessing the command prompt of RA
C. to prevent administrators from accessing the console of RA
D. to give administrators access to the Internet
E. to prevent students from accessing the Internet
F. to prevent students from accessing the Admin network
Answer: B
Explanation
Although the access-list is used to “permit” network 10.1.1.0/24 but the best answer here is “to prevent students from accessing the command prompt of RA”. From the picture above, we know that 10.1.1.0/24 is the “Admin” network. This access list is applied to “line vty 0 4″ so it will permit only Telnet traffic from “Admin” to RA while drop all other traffic (because of the implicit “deny all” command at the end of the access list). Therefore we can deduce that it will “prevent students from accessing the command prompt of RA”.
This access list only filters Telnet traffic (because it is applied to vty line) so it will not prevent or allow anyone to access the Internet -> A, D, E are not correct.
C is not correct as this access list allows administrators to access the console of RA.
F is not correct as this access list does not proceed TCP, UDP or IP traffic so the students still access the Admin network.
(Notice that the “command prompt” here implies telnet as telnet is the only way to remotely access RA)
Question 4
An access list was written with the four statements shown in the graphic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?
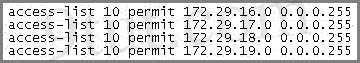
A. access-list 10 permit 172.29.16.0 0.0.0.255
B. access-list 10 permit 172.29.16.0 0.0.1.255
C. access-list 10 permit 172.29.16.0 0.0.3.255
D. access-list 10 permit 172.29.16.0 0.0.15.255
E. access-list 10 permit 172.29.0.0 0.0.255.255
Answer: C
Explanation
Four statements above allow 4 networks (from 172.29.16.0/24 to 172.29.19.0/24) to go through so we can summary them as network 172.29.16.0/22.
/22 = 255.255.252.0 so it equals 0.0.3.255 when converting into wildcard mask -> C is correct.
A, B, D are not correct as their wildcard masks are false. For example:
Answer A allows from 172.29.16.0 to 172.29.16.255
Answer B allows from 172.29.16.0 to 172.29.17.255
Answer D allows from 172.29.16.0 to 172.29.31.255
Both the network address and wildcard mask of answer E are false as it allows the whole major network 172.29.0.0/16 to go through.
Question 5
A network administrator wants to add a line to an access list that will block only Telnet access by the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?
A – access-list 101 deny tcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
B – access-list 101 deny tcp 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
C – access-list 1 deny tcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21
access-list 1 permit ip any any
D – access-list 1 deny tcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23
access-list 1 permit ip any any
Answer: A
Explanation:
First the question asks to block only Telnet access so the port we have to use is 23 -> C is not correct.
Next we need to block traffic from hosts on the subnet 192.168.1.128/28, which is 192.168.1.128 0.0.0.15 if we convert to wildcard mask (just invert all bits of the subnet mask,from 0 to 1 and from 1 to 0 we will get the equivalent wildcard mask of that subnet mask) -> so B is incorrect
In this case, we have to use extended access list because we need to specify which type of traffic (TCP) and which port (23) we want to block -> so D is incorrect because it uses standard access list.
Question 6
As a network administrator, you have been instructed to prevent all traffic originating on the LAN from entering the R2 router. Which the following command would implement the access list on the interface of the R2 router?
A – access-list 101 in
B – access-list 101 out
C – ip access-group 101 in
D – ip access-group 101 out
Answer: C
Question 7
The following access list below was applied outbound on the E0 interface connected to the 192.169.1.8/29 LAN:
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
How will the above access lists affect traffic?
A – FTP traffic from 192.169.1.22 will be denied
B – No traffic, except for FTP traffic will be allowed to exit E0
C – FTP traffic from 192.169.1.9 to any host will be denied
D – All traffic exiting E0 will be denied
E – All FTP traffic to network 192.169.1.9/29 will be denied
Answer: D
Explanation:
There is always an implicit “deny all” command at the end of every access list, so if an access list doesn’t have any “permit” command, it will block all the traffic.
Note: This access list is applied on outbound direction so only packets exiting E0 will be checked. Packets entering E0 will not be checked and they all are allowed to pass through.
Question 8
The access control list shown in the graphic has been applied to the Ethernet interface of router R1 using the ip access-group 101 in command. Which of the following Telnet sessions will be blocked by this ACL? (Choose two)
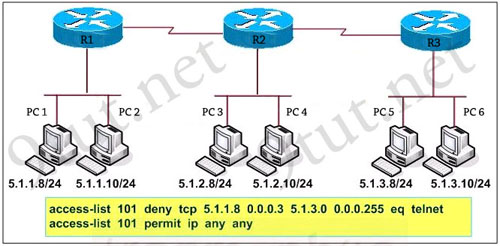
A – from host PC1 to host 5.1.1.10
B – from host PC1 to host 5.1.3.10
C – from host PC2 to host 5.1.2.10
D – from host PC2 to host 5.1.3.8
Answer: B D
Explanation
Below is the simple syntax of an extended access list:
access-list access-list-number {deny | permit} {ip|tcp|udp|icmp} source [source-mask] dest [dest-mask] [eq dest-port]
Notice that this access list is applied to the Ethernet interface of R1 in the “in direction” so in this case, it will filter all the packets originated from E1 network (host PC1 and PC2) with these parameters:
Source network: 5.1.1.8 0.0.0.3 which means 5.1.1.8/252 (just invert all the wildcard bits to get the equivalent subnet mask) -> Packets from 5.1.1.8 to 5.1.1.11 will be filtered.
Destination network: 5.1.3.0 0.0.0.255 which means 5.1.3.0/24-> Packets to 5.1.3.0/24 will be filtered
Therefore packets originated from 5.1.1.8 to 5.1.1.11 and have the destination to the host 5.1.3.x (via Telnet) will be denied.
Question 9
The following configuration line was added to router R1
Access-list 101 permit ip 10.25.30.0 0.0.0.255 any
What is the effect of this access list configuration?
A – permit all packets matching the first three octets of the source address to all destinations
B – permit all packet matching the last octet of the destination address and accept all source addresses
C – permit all packet matching the host bits in the source address to all destinations
D – permit all packet from the third subnet of the network address to all destinations
Answer: A



i can’t understand Q 3 please i need a discusion
In question 3, access-list 2 is applied to vty lines (from line 0 to line 4). From the command “access-list 2 permit 10.1.1.0 0.0.0.255″ we know that it will only permit packets in the Admin section go through. Therefore we can deduce it is used to prevent students from accessing the command prompt of RA through vty lines. Notice that in this case if the students want to access RA they have to use vty line (telnet) because they are far away from RA so they can not use console line
In question 4 I don’t understand how one can figure out the block size without the subnet mask or the giving the slash notation, e.g. /30. Can someone explain? Thanks.
@Kamran: /30 is a short way to write subnet mask. It means the subnet mask has 30 number 1 in its binary form
/30 = 11111111.11111111.11111111.11111100 (30 number 1 in binary form) = 255.255.255.252 (in decimal form)
Yes, I understand that but my question is in Q4 it does not say anywhere /30, only the answer ‘C’ implies that it is /30.
I have seen few practise questions in Lammle’s CCNA certification book regarding wildcard masks and they all have either / notation specified or subnet masks in the questions. Q4 above does not.
For arguments sake, in Q4, I can use block size of 16 to include valid hosts, 16, 17, 18 and 19, right. If you agree why would not answer D be the right choice.
D is not the correct answer because by using a wildcard mask of 0.0.15.255, you will allow packets in the range of 172.29.16.0 to 172.29.31.255 go through, but the question just wants to let packets from 172.29.16.0 to 172.29.19.255 to go through.
ok, so it seems that one has to go through all choices and eliminate the ones that do not fit the question. I was looking for an answer that will lead me to find the right block size without looking at the answers. Anyhow, thanks for your efforts in answering my questions, I really appreciate a quick response from you.
I have an easy steps to figure it out:
First convert 16, 17, 18 and 19 to binary as shown below:
00010000 –> 16
00010001 –> 17
00010010 –> 18
00010011 –> 19
_________________All same bits, set 1___
11111100
invert the result
00000011 —-convert to Decimal–> 3
172.29.16.0 0.0.3.255
I hope this could clear the picture for others.
I still do not how you found the answer for quetsion 4.
I’d really appreciate if you could explain it in detail.
wildcardmask 0.0.3.255 = subnetmask 255.255.252.0
252=128+64+32+16+8+((4))+2+1
now we know the increment is 4
so subnets would be
172.29.16.0 -172.29.19.255
i understand everything except q1 could someone help me out thanks =(
@aNgeL:
Telnet is port 23, so that immediately eliminates A,B,C
>access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
this access list mask covers the address range 196.168.15.32 to 192.168.15.47. Making D&E the correct answers.
i have confusion in Question NO .4. They use the Wild Card mask 0.0.3.255 which means that in the third octet Last two bits do not match. If the subnet mask will be 255.255.252.0 mean the same last two bits are for host in third octet. Right. But my question is that is you use last two bits you get 4 host 2^2 and you get 4 hosts. In which one is network id and one is broadcast id and their is only 2 valid hosts. So are you think that according to this situation we use wildcard mask 0.0.7.255 instead of 0.0.3.255? I will be very thank full to you.
To Umair,
network address = 172.29.16.0
broadcast address = 172.29.19.255
172.29.16.1 1st useable host
l172.29.19.254 last useable host
So then..
172.29.20.0 – 172.29.23.255
172.29.24.0 – 172.29.27.255
172.29.28.0 -………………….
Please Cisco Experts correct me if am wrong also.
Thanks!
I realized with the help of my friend that we don’t care anymore about networks, subnetting on this etc….Since We really don’t know the network architecture of the given question. To narrow it , our approached Umair is not related to the question.
The question just stated to only allow only the said range.
to further see what I implied..Example the subnet of this
172.29.16.0 – 172.29.23.255
the administrator only want to allow the network range 172.29.16.0 – 172.29.19.0..and that is what we are required to do in the ACL..
Hi, The answer to Q4 is correct! from the books read on subnetting it is clear that you need to maximize the use of your subnet blocks. if you use any block size higher that the one the accommodates what is shown in the question you’re waste the remaining except you intend to increase host on your network which the question doesn’t state. But even with that, one has to be careful cos the redundant addresses might get used up in some other subnets and you know what that means.
Thanks 9tut, your right and your efforts are appreciated
Hi 9tut;
How could I be able to quickly see the answers of question 1(access List)?
I can see that 21 is not telnet and thus A, B, C will be dropped. However, I could not find a valid reason why F is wrong and how D and E could only be also correct. Please explain.
Iskket.
The wildcard mask is 0.0.0.15 so it will affect all IP addresses in the range of 192.168.15.32 to 192.168.15.47 (and they will be filtered out). Please read more about wildcard mask to understand why.
iskket,
The reason that F is not a correct answer in question number 1 is that, you are configuring an access list on RTB. The ip 192.168.15.49 is the fast ethernet address of RTA, which does not pass through RTB to access the Telnet Server.
Hope this clears things up.
For access lists questions it ALWAYS comes down to subnets.
Q1 – is PRIME example. The reason it is D and E is as follows.
access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
access-list 101 permit ip any any
A. source ip address: 192.168.15.5; destination port: 21- This is obviously STUPID if you pick this, its FTP! (port 21 of TCP)
B. source ip address:, 192.168.15.37 destination port: 21
Again its FTP (port 21 of TCP)
C. source ip address:, 192.168.15.41 destination port: 21
Again its FTP (port 21 of TCP)
D. source ip address:, 192.168.15.36 destination port: 23
E. source ip address: 192.168.15.46; destination port: 23
F. source ip address:, 192.168.15.49 destination port: 23
If you were a smart cookie you SEE that the subnet is
D) 192.168.15.32/29 (the increment is 8)
32 + 8 = 40. 33 through 38 is range, .39 is broadcast and .40 is the next network. So naturally the ONLY answer that can fit into that range would be 192.168.15.36!
E)
192.168.15.40/29 (The increment is 8)
So if you added 8 to 40 you get 48 but. You can’t use .40 as that’s the network, you can’t use 47 or 48 because that’s the broadcast address of that network range and you cannot use 48 as that’s the NEXT network.
F) If you pick this you are in trouble. #1 There is no subnet for that range!
192.168.15.49 would be part of the 192.168.15.48 network with a range of 48 through 56. You could not use 49 as it’s in a different subnet that is NOT listed. But FYI the range would be .49 through .54 with .55 and .56 used for broadcast and the next network.
So REMEMBER even though the question is about an ACL, you still have to know subnetting to pick the right answer!
You can *Try* to memorize p4s, but I tell you when you know the material, questions are not that difficult. Take the time to learn subnetting you NEED IT BIG TIME BIG TIME BIG TIME to take the CCNA, the CCNP and just in real life you need to know!!
Learn subnetting. CBT nuggets ccna does a good job, so does trainsignal and Lammle (sybex 6th edition) those are my main study guides and I just glanced at this stuff on this site, but I already knew the answer to over 90% of the questions on here except that STUPID frame relay question about “password required” or not required or it is but they don’t want it.
What’s up with that? Crazy.
@i tr00f,
0.0.0.15 is /28 or .240 giving 16 hosts minus the network and minus the broadcast – so increment of 16 not 8, that said, there are 14 available hosts. .36 and .46 using the telnet port 23 permit. in the acl.
Q1 is correct, answer is DE
Hi There,
Ref Q1. The subnets are indeed /248 so am i reading this right in that the question is misleading?
Would it not be that by stating 0.0.0.15 as the wildcard mask, they are actually saying that anything “from” 192.168.15.32 all the way to 192.168.15.47 (Covering two subnets) would be blocked, thereby making the answer C+D?
I thought I had this sorted but now and confused. Can anyone help clarify?
Currently setting this up in a sim. Will let you know once i’ve got it working……
Cheers
Guys,
The answer must indeed be C+D, assuming i have recreated this right on a simlab using Ciscos Packet Tracer 5.1.
Once the ACL was applied, I could telnet to RTB Router (From a PC with IP Address 192.168.15.44/29) but not to RTA. As soon as I removed the ACL from the S0/0 interface on RTB, i was again able to telnet. So, i’m guessing that the wildcard mask 0.0.0.15 when referencing a /248 subnet, must cover two subnets.
Any other comments most welcome. Want to make sure I have understood it correctly!!! Guess it is one of those questions that makes sure you RTFQ and understand it :-)
Cheers All
oops, i meant Answers are D+E….
I would like to comment on question number 4.
It would appear that answer D would be correct, unless I am tired and not working this out correctly.
0.0.3.255 = 255.255.252.0 right?
172.29.16.0 Network
172.29.16.1 First
172.29.17.254 Last
172.29.17.255 Broadcast
So how does .18.0 and .19.0 work in this? Please explain.
oooo, boy!
256-253 in the third octet = 4.
172.29.16.0 + 4 in the third octet = 172.29.20.0
broadcast – 172.16.19.255
The easiest way to answer Q4 can be achieved by calculating “hot octed”‘s wild card simply by reducing 1 from number of networks (4) and here we get 3. also note that all networks have 0.0.0.255 wild card so to supernet you have to borrow bits from last network octed which is third octed and we call that hot octed so we get 0.0.3.255 for wild card. the lowest network is 16.0 so we get 172.29.16.0 for supernetted network IP.(thank me if this helps not GOD,lool)
My question is about Q2 and why answer A is wrong,I think the reason is cisco recommendation on putting extended access lists as close as possible to source.but practically answer A should work fine.
Q2 answer A is wrong because we need to apply access-list to the inbound direction of Fa0/0, not the outbound direction.
I think you didn’t read the question carefully and think answer A something like this
Router(config)# interface fa0/1
Router(config-if)# ip access-group 101 out
If it were “fa0/1″ then A would be correct too.
Yap 9tut, your right,I read it like fa0/1.I just can’t stand read the questions word by word.don’t know how to deal with that :-)
Help on question number 2!
I’m really confused whether it should be IN or OUT.
my answer is OUT because you’re preventing the PC1 from accessing (from going out the router) the SERVER.
Please help me with this one. thanks a lot!
Traffic flows from PC1 to the Server so port Fa0/0 is the inbound port -> we must use inbound direction
Q4:
I am Extremely Sure that the wild mask is 0.0.0.3
here is my explanation of this case :
We have 16 to 19 so the largest is 19
the largest is smaller than 32 which is from
128 64 32 16 8 4 2 1
so in this case we need 6 bits to represent as ones in the third octet i.e the subnet mask is 252 or /30 , in this case the corresponding wild mask will be 0.0.0.3 .
Wildcard masks are calculated differently with the subnet masks. To cover addresses from 172.29.16.0 to 172.29.19.0 we need a subnet mask of 255.255.252.0. Reverse this subnet mask we get 0.0.3.255 and that is the wildcard mask we need.
I read this question in the Actual Tests Dumps and I am not sure of the validity of AT’s answer as I personally believe it to be “None of the above”. So please help me to the right solution with explanation. Thanks a lot in advance….
Q:
You need to place an access list on the fa0 interface of Home router; that will deny access to all hosts that lie within the range 192.168.160.0 – 192.168.191.0.
Hosts in the 192.168.195.0 network should be granted access. Which one of the following answer choices fulfills your needs?
A. access-list 1 deny 192.168.163.0 0.0.0.255
B. access-list 1 deny 192.168.128.0 0.0.127.255
C. access-list 1 deny 192.168.160.0 0.0.255.255
D. access-list 1 deny 192.168.160.0 0.0.31.255
E. None of the above
Answer: E (my view)
D (as per Actual Test Q. No. 604)
I read this question in the Actual Tests Dumps and I am not sure of the validity of AT’s answer as I personally believe it to be “None of the above”. So please help me to the right solution with explanation. Thanks a lot in advance….
Answer to ur q is D. reason it is correct because 31.255 only block the same range which is in question.
Q:
You need to place an access list on the fa0 interface of Home router; that will deny access to all hosts that lie within the range 192.168.160.0 – 192.168.191.0.
Hosts in the 192.168.195.0 network should be granted access. Which one of the following answer choices fulfills your needs?
A. access-list 1 deny 192.168.163.0 0.0.0.255
B. access-list 1 deny 192.168.128.0 0.0.127.255
C. access-list 1 deny 192.168.160.0 0.0.255.255
D. access-list 1 deny 192.168.160.0 0.0.31.255
E. None of the above
Answer: E (my view)
D (as per Actual Test Q. No. 604)
——————————
in my view, the answer is E because there is a IMPLICIT DENY statement at the end of ACLs, and this one does not have any permit access. So, this will deny all traffic.
it’s D… if they’re only looking for partial answer. but it should be E if you’re looking for a complete statement. Where did you get the question? Is it from the actual cisco exam? it troubles me because, I’ll be taking the exam this month and this question is kind of vague. If I were to take the exam today, my answer would be E.
Refer to the exhibit. Which statement describes the effect that the Router1 configuration has on
devices in the 172.16.16.0 subnet when they try to connect to SVR-A using Telnet or SSH
A. Devices will not be able to use Telnet or SSH.
B. Devices will be able to use SSH, but not Telnet.
C. Devices will be able to use Telnet, but not SSH.
D. Devices will be able to use Telnet and SSH
QUESTION 154
testinside 17.14 why B is correct
AMR BCOS IN CONFIG PORT 22 IS SSH. ACCESING A TRHRU SSH CONFIG IS CORRECT .BUT CONFIG FOR TELNET IS WRONG.(SEE THE SYNTAX).
SECOND FOR INBOUND ACCESS-LIST A CAN TELNET TO 172.16 N/W BUT THATS NOT WHAT IS ASKED.ACOORDING TO QUESTION ASKED 172.16 N/W CAN SSH A.THATS ALL.
@amr maoomon…..
if u check the access lists properly…usually we allow port of server but
in both the access lists 100 & 101, the 20 refers to allowing the telnet port of the host network….
the default deny any any command blocks the rest of the communication which includes blocking the telnet port of the server…
just read the commands and try to understand :)
hey ,can somebody explain me the answer of question no. 4 in Access List Questions in 9tut website ?
Question 4:
An access list was written with the four statements shown in the graphic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?
A. access-list 10 permit 172.29.16.0 0.0.0.255
B. access-list 10 permit 172.29.16.0 0.0.1.255
C. access-list 10 permit 172.29.16.0 0.0.3.255
D. access-list 10 permit 172.29.16.0 0.0.15.255
E. access-list 10 permit 172.29.0.0 0.0.255.255
Answer is c,
Look now the networks it needs to permit are
172.29.16.0 – 172.29.19.0
concentrating on the second octet ->
16, 17, 18,19 = 4 , therefore a block size of 4 would be enough to satisfy the criteria.
1) 0-3, 2) 4-7, 3) 8-11, 4) 12-15, 5) 16-19, 6) 20-23 are all subnets of 4.
The 5th subnet will satisfy the criteria so the network number will be 172.29.16.0 and wildcard mask would be 0.0.3.255 ( because that is the mask that we would use for a block size of 4 )
D. if you choose D then that gives us a block size of 16 thereby permitting network 16,17,18,19,20,…30,31. and that is not the criteria
Hope that helps
Please help with the following question.
What will happen to HTTP traffic comming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
Router#show access-list
Extended IP access list 110
10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet
20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp
30 deny tcp 172.16.0.0 0.0.255.255 any eq http
40 permit tcp 172.16.0.0 0.0.255.255 any
A. Traffic will be dropped per line 30 of the ACL
B. Traffic will be accepted per line 40 of the ACL
C. Traffic will be dropped, because of the implicit deny all at the end of the ACL.
D. Traffic will be accepted, because the source address is not covered by the ACL.
The correct answer from Test Inside is C.
For me the correct answer is A.
Please explain!!!!
Hey, Robbie,
Well, this had me at first, but it’s just a little test on our comprehension.
When we write an extended ACL, we write it as such;
access-list permit/deny source IP + inverse mask destination + inverse mask
The question states the of the traffic is from the internet, therefore we go back to our ACL and see the source in all the statements is identified as 172.16.0.0. We know this not a publicly routable address, therefore the source of the internet traffic would not have this as it’s incoming source address. It must be a non private address.
We also know that there is no ACL statement that permits any public addresses, in our ACL. Though we do know that there is an implicit deny any any at the end of every ACL. This takes effect as non of the other statements are true.
This is why option C is correct :)
Hope that helps your understanding. I had to think about it for a few moments too, lol.
Hello friends
access list 2 with Nat for CCNA simulation in GNS3 and VMware, this video help you to understand the lab as an exam point of view as well as in real world.
Hope you will like
http://www.youtube.com/watch?v=qJVuCFHdoDk
Muhammad Imran
MCP,MCTS,MCITP,CCNA,CCNP
hey guys….. i am totally confused here
please tell me how the in and out occurs in access list….
how can i identify inbound and outbound…?
i dont know which one does what…
please help me…
thank you.
Hey, Max,
After we create an ACL, we have to apply it to an interface so that it may apply the ACL to the traffic that passes or attempts to pass that interface.
We use the inbound and outbound to identify which direction the traffic is propagating through the interface and router.
The best way my instructor said to identify whether to use inbound or outbound was to be the router, as if you were standing on the router and recognize the direction the traffic is running through you. Let’s see if I can make an example below;
Internet traffic –> *(S 0/0)(router, you)(FA 0/0)* –> LAN 1 traffic
*(FA 0/1)
/
|
LAN 2
In the above scenario, sorry so crude but all I got here, the traffic is propagating through the router from the Internet through you the router to your LANs. The * represents the interfaces the router will use to pass traffic to LAN 1 and 2, and the interface that faces the Internet. Let’s say you have an ACL that is designed to block Internet traffic to both your LANs (1 and 2) and you need to know where to apply it, inbound or outbound.
Since you are the router, you have a unique vantage point to notice the traffic is coming IN (and this is important, so pay attention) from the internet to you the router and passing through you to your LANs. Now, we want our ACL to be applied before the traffic gets past the router to our LANs. If you notice the diagram and specifically the interface labeled S 0/0, this is where the traffic is coming IN (inbound) to the router, so if we want the ACL to be processed before it gets past the router to the LANs we would apply the ACL on the S 0/0 interface, in an inbound direction. This is accomplished by going into interface mode for whatever interface you need the ACL applied to, like this for ours (config)# int S 0/0 then once in that interface mode we apply the direction we wish to apply the ACL. Like this for our inbound traffic, it’s inbound because as the router- it’s coming in from the Internet, (config-if)# ip access-group (ACL # or name here) in (or out depending on the direction of the traffic that needs to be processed by the ACL on this interface). With this configuration any traffic that passes through our router to any of our LANs would have its traffic processed by our ACL at the first inbound interface to the router and then the resulting LANs would only receive traffic based on the criteria in the ACL that was processed.
Now, if we want say only traffic from the Internet to LAN 1 to process the ACL and LAN 2 not to be affected then we would be the router and see that the trafffic is traveling through us in an outbound direction to LAN 1. So, we would apply the ACL to the FA 0/0 interface in an outbound direction. Like this — (config)# int FA 0/0 then (config-if)# ip access-group (number or name of ACL) out (as the traffic is traveling OUT of the router to the LAN 1).
That covers both inbound and outbound and since this took me so long to develop now the wife needs the pc, lol :)
So, just reply if you get hung up somewhere but I hope it helps you understand better what the inbound and outbound are used for and when. The whole be the router to determine if the traffic is coming in (inbound) or going out (outbound) through the interfaces is very helpful in determining where to place the direction of the ACL to be placed.
Good Luck!
Sean
For the difference between using inbound and outbound can you question 2 as an example?
Because I am really confused as to why you would apply it inbound instead of outbound.
Don’t you want it as close to the destination as possible? Or do you apply inbound to reduce overhead?
I still have a huge problem figuring this out
thanks
@Pandamania
Well they only give you two options and out fa 0/0 wouldn’t catch the traffic coming from PC1, in question 2 as that traffic would be coming from the server, the wrong direction. So, in order to catch the traffic before it hits the server, you must choose answer B. As the traffic from PC1 is coming IN to fa 0/0 and heading to the server which should NOT be reached by PC1.
Also, for extended ACL’s they are to be located as close to the source as possible, not destination (that’s true for standard ACL’s)but that is not always the case. It depends on the traffic you need to permit or deny. We know this is an extended ACL as it has a number over 99.
Hope that helps :)
Sean
@Sean
OH! Lol, I was looking at the wrong interface. I got Fa 0/0 and Fa0/1 switched, but you are so right. I got the standard ACL and extended ACL rules completely backwards. Now this makes so much more sense, thanks :)
So if I’m understanding this correctly, if this was a standard access list, than I would be applying the ACL to the outbound interface of Fa0/1? This way it’ll be as close to the destination as possible and keeping PC1 traffic from coming out of the router?