New CCNA – Security Questions
Question 1
Which Cisco Catalyst feature automatically disables the port in an operational PortFast upon receipt of a BPDU?
A. BackboneFast
B. UplinkFast
C. Root Guard
D. BPDU Guard
E. BPDU Filter
Answer: D
Explanation
We only enable PortFast feature on access ports (ports connected to end stations). But if someone does not know he can accidentally plug that port to another switch and a loop may occur when BPDUs are being transmitted and received on these ports.
With BPDU Guard, when a PortFast receives a BPDU, it will be shut down to prevent a loop -> D is correct.
Question 2
Which two commands correctly verily whether port security has been configured on port FastEthernet 0/12 on a switch? (Choose two)
A. SW1# show switchport port-security interface FastEthernet 0/12
B. SW1# show switchport port-secure interface FastEthernet 0/12
C. SW1# show port-security interface FastEthernet 0/12
D. SW1# show running-config
Answer: C D
Explanation
We can verify whether port security has been configured by using the “show running-config” or “show port-security interface ” for more detail. An example of the output of “show port-security interface ” command is shown below:
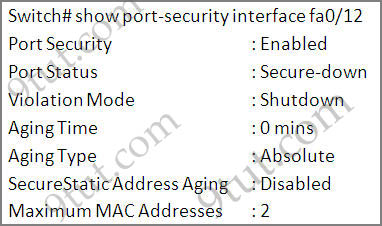
Question 3
Select the action that results from executing these commands:
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security mac-address sticky
A. A dynamically learned MAC address is saved in the startup-configuration file.
B. A dynamically learned MAC address is saved in the running-configuration file.
C. A dynamically learned MAC address is saved in the VLAN database.
D. Statically configured MAC addresses are saved in the startup-configuration file if frames from that address are received.
E. Statically configured MAC addresses are saved in the running-configuration file if frames from that address are received.
Answer: B
Explanation
The full syntax of the second command is:
switchport port-security mac-address sticky [MAC]
If we don’t specify the MAC address (like in this question) then the switch will dynamically learn the attached MAC Address and place it into your running-configuration -> B is correct.
Question 4
Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)#switchport port-security
2950Switch(config-if)#switchport port-security mac-address sticky
2950Switch(config-if)#switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two)
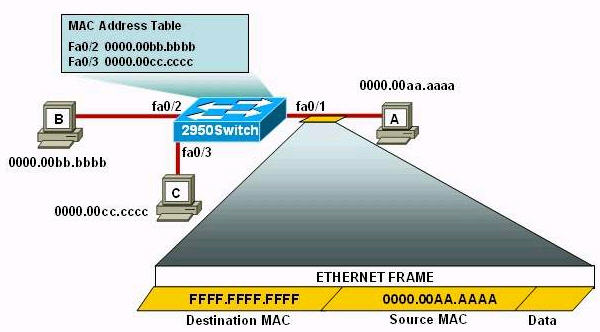
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. Only host A will be allowed to transmit frames on fa0/1.
C. This frame will be discarded when it is received by 2950Switch.
D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.
F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be forwarded out fa0/1.
Answer: B D
Explanation
Please read the explanation at http://www.9tut.net/icnd2/icnd2-operations
Question 5
Which set of commands is recommended to prevent the use of a hub in the access layer?
A.
switch(config-if)#switchport mode trunk
switch(config-if)#switchport port-security maximum 1
B.
switch(config-if)#switchport mode trunk
switch(config-if)#switchport port-security mac-address 1
C.
switch(config-if)#switchport mode access
switch(config-if)#switchport port-security maximum 1
D.
switch(config-if)#switchport mode access
switch(config-if)#switchport port-security mac-address 1
Answer: C
Explanation
Port security is only used on access port (which connects to hosts) so we need to set that port to “access” mode, then we need to specify the maximum number of hosts which are allowed to connect to this port -> C is correct.
Note: If we want to allow a fixed MAC address to connect, use the “switchport port-security mac-address ” command.
Question 6
Refer to the exhibit. A junior network administrator was given the task of configuring port security on SwitchA to allow only PC_A to access the switched network through port fa0/1. If any other device is detected, the port is to drop frames from this device. The administrator configured the interface and tested it with successful pings from PC_A to RouterA, and then observes the output from these two show commands.

Which two of these changes are necessary for SwitchA to meet the requirements? (Choose two)
A. Port security needs to be globally enabled.
B. Port security needs to be enabled on the interface.
C. Port security needs to be configured to shut down the interface in the event of a violation.
D. Port security needs to be configured to allow only one learned MAC address.
E. Port security interface counters need to be cleared before using the show command.
F. The port security configuration needs to be saved to NVRAM before it can become active.
Answer: B D
Explanation
As we see in the output, the “Port Security” is in “Disabled” state (line 2 in the output). To enable Port security feature, we must enable it on that interface first with the command:
SwitchA(config-if)#switchport port-security
-> B is correct.
Also from the output, we learn that the switch is allowing 2 devices to connect to it (switchport port-security maximum 2) but the question requires allowing only PC_A to access the network so we need to reduce the maximum number to 1 -> D is correct.
Question 7
A network administrator needs to configure port security on a switch. Which two statements are true? (Choose two)
A. The network administrator can apply port security to dynamic access ports
B. The network administrator can configure static secure or sticky secure mac addresses in the voice vlan.
C. The sticky learning feature allows the addition of dynamically learned addresses to the running configuration.
D. The network administrator can apply port security to EtherChannels.
E. When dynamic mac address learning is enabled on an interface, the switch can learn new addresses up to the maximum defined.
Answer: C E
Explanation
Follow these guidelines when configuring port security:
+ Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports. -> A is not correct.
+ A secure port cannot be a dynamic access port.
+ A secure port cannot be a destination port for Switched Port Analyzer (SPAN).
+ A secure port cannot belong to a Fast EtherChannel or Gigabit EtherChannel port group. -> D is not correct
+ You cannot configure static secure or sticky secure MAC addresses on a voice VLAN. -> B is not correct.
+ When you enable port security on an interface that is also configured with a voice VLAN, you must set the maximum allowed secure addresses on the port to at least two.
+ If any type of port security is enabled on the access VLAN, dynamic port security is automatically enabled on the voice VLAN.
+ When a voice VLAN is configured on a secure port that is also configured as a sticky secure port, all addresses seen on the voice VLAN are learned as dynamic secure addresses, and all addresses seen on the access VLAN (to which the port belongs) are learned as sticky secure addresses.
+ The switch does not support port security aging of sticky secure MAC addresses.
+ The protect and restrict options cannot be simultaneously enabled on an interface.
Note: Dynamic access port or Dynamic port VLAN membership must be connected to an end station. This type of port can be configured with the “switchport access vlan dynamic” command in the interface configuration mode. Please read more about Dynamic access port here: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3550/software/release/12-1_19_ea1/configuration/guide/3550scg/swvlan.html#wp1103064
Question 8
Which protocol is an open standard protocol framework that is commonly used in VPNs to provide secure end-to-end connections?
A. PPTP
B. IPsec
C. RSA
D. L2TP
Answer: B
Explanation
One of the most widely deployed network security technologies today is IPsec over VPNs. It provides high levels of security through encryption and authentication, protecting data from unauthorized access.



question 4 on exam today
Q 3 today..
Today I Passed The CCNA exam with 993. most of questions from 9tut. I have my vce file with the vce player. asanka11@gmail.com
but nothing more 9tut is more than enough. do not wast your time with any site. follow 9tut.
Thank you very much 9tut.
q8 today on exam
Hi, about Q3: A and B ara correct in fact in my opinion in spite of the exam question could shows only B as correct.
At least in Packet Tracer 6.1 you can see MAC addresses from “switchport port-security mac-address sticky” interface subcomand even in running-config and startup-config. Not sure in real IOS if that is the same…
This is the config I have beeing using:
interface GigabitEthernet0/2
description Trunk_To_L2SW4SAN_VLAN100
switchport trunk allowed vlan 100
switchport mode trunk
switchport port-security
switchport port-security maximum 6
switchport port-security mac-address sticky
switchport port-security violation restrict
switchport port-security mac-address sticky 0010.112C.9C1A
switchport port-security mac-address sticky 0010.1188.313E
switchport port-security mac-address sticky 0010.11C5.3763
switchport port-security mac-address sticky 00E0.F709.7DD3
!
L2SW3FARM#sh port-security interface gigabitethernet0/2
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Restrict
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 6
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 4
Last Source Address:Vlan : 0010.112C.9C1A:1
Security Violation Count : 0
Another observation is: in the explanation of Q.5 it says the following: ” Port security is only used on access port…” Are you sure? Would you like to check my previous GigaEth0/2 interface configuration and try it if possible on a lab to see this also works in Trunk ports? And if were possible could you please explain why you are saying that? Again I recall you I’m using PT6.1 Thanks.
Hi. Me again ;-) Regarding Q.7 oprion D: “D. The network administrator can apply port security to EtherChannels.” I was wondering why it is considered wrong there…? Is this possible they are talking about interface ports that belongs to a Fast or Giga ether-channel instead of the virtual port that bundle those? Otherwise it is a correct answer if you are not applying port-security to a interface/port belonging to a channel making it different from the others, something that obviously exclude this port from the bundle… I didn’t try it but the command is available under configuration in spite there is not available a “show port-security interface port-channel X” command…
Check that:
L2SW3FARM#sh run
…
interface Port-channel 4
description BCKP_Channel_To_L3DIST1SW
switchport trunk allowed vlan 1-99,101-1005
switchport mode trunk
switchport port-security
switchport port-security maximum 4
switchport port-security violation restrict
!
L2SW3FARM#sh port-security interface ?
Ethernet IEEE 802.3
FastEthernet FastEthernet IEEE 802.3
GigabitEthernet GigabitEthernet IEEE 802.3z
L2SW3FARM#
Source: PT6.1 – Cisco WS-C2960-24TT – IOS 12.2(25)FX
L2SW3FARM#sh port-security
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action
(Count) (Count) (Count)
——————————————————————–
Gig0/2 6 1 0 Restrict
Po4 4 0 0 Restrict
———————————————————————-
L2SW3FARM#
Q1 & 2 in my exam today, passed
Q1, Q2 On 15th Feb.
Can someone pls forward the latest dumps to sukumar89v@gmail.com
Thanks
@Claudio: about Q3, configuration can only be saved in start-up config when you save it. In the question, there is no command showing that the configurations have been saved.
Q2
Passed my CCNA exam today (18th Mar)… Q8 in exam
Q6
hallo guys how do u connect two linksys router wirelessly pliz help
Which statement describes an important characteristic of a site-to-site VPN?
It is commonly implemented over dialup and cable modem networks.
It is ideally suited for use by mobile workers.
It must be statically set up.
After the initial connection is established, it can dynamically change connection information.
It requires using a VPN client on the host PC.
Hi guys! i need CCNA 200-120 dumps please. sonfele@gmail.com
in Q5′s explanations, I read :
“Port security is only used on access port (which connects to hosts) ”
and in Q7′s explanation, I read :
“Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports”
it’s not clear about port security on trunk ports : in Q5, it’s forbiddden and in Q7, it’s authorized !!!
in Q5′s explanations, I read :
“Port security is only used on access port (which connects to hosts) ”
and in Q7′s explanation, I read :
“Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports”
it’s not clear about port security on trunk ports : in Q5, it’s forbiddden and in Q7, it’s authorized !!!
@Pascal
It depends on the scenario. Did you read the question at Number 5 Carefully?
“Question 5 Which set of commands is recommended to PREVENT THE USE OF A HUB in the access layer?”
We need to disable the HUB, to do that we need to enable the Port Security on a PORT configured as “Access Mode”. So that is what he mean on the “Port security is only used on access port (which connects to hosts) so we need to set that port to “access” mode…”
In “Question 7 + Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports. “, Well it is already stated that Port Security can be configured on a port configured as “Access mode”, “Trunk mode” and “802.1Q tunnel ports”.