Access List Tutorial
In this tutorial we will learn about access list.
Access control lists (ACLs) provide a means to filter packets by allowing a user to permit or deny IP packets from crossing specified interfaces. Just imagine you come to a fair and see the guardian checking tickets. He only allows people with suitable tickets to enter. Well, an access list’s function is same as that guardian.
Access lists filter network traffic by controlling whether packets are forwarded or blocked at the router’s interfaces based on the criteria you specified within the access list.
To use ACLs, the system administrator must first configure ACLs and then apply them to specific interfaces. There are 3 popular types of ACL: Standard, Extended and Named ACLs.
Standard IP Access List
Standard IP lists (1-99) only check source addresses of all IP packets.
Configuration Syntax
| access-list access-list-number {permit | deny} source {source-mask} |
Apply ACL to an interface
| ip access-group access-list-number {in | out} |
Example of Standard IP Access List
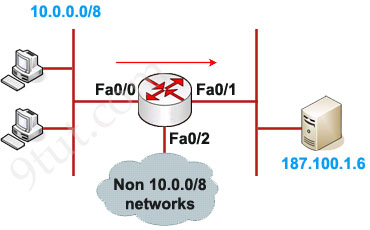
Configuration:
In this example we will define a standard access list that will only allow network 10.0.0.0/8 to access the server (located on the Fa0/1 interface)
Define which source is allowed to pass:
Router(config)#access-list 1 permit 10.0.0.0 0.255.255.255
(there is always an implicit deny all other traffic at the end of each ACL so we don’t need to define forbidden traffic)
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 1 out
The ACL 1 is applied to permit only packets from 10.0.0.0/8 to go out of Fa0/1 interface while deny all other traffic. So can we apply this ACL to other interface, Fa0/2 for example? Well we can but shouldn’t do it because users can access to the server from other interface (s0 interface, for example). So we can understand why an standard access list should be applied close to the destination.
Note: The “0.255.255.255″ is the wildcard mask part of network “10.0.0.0″. We will learn how to use wildcard mask later.
Extended IP Access List
Extended IP lists (100-199) check both source and destination addresses, specific UDP/TCP/IP protocols, and destination ports.
Configuration Syntax
| access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port] |
Example of Extended IP Access List
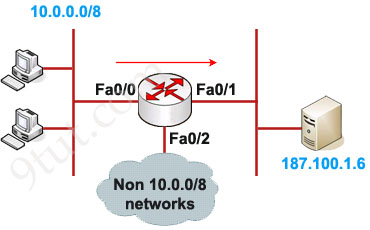
In this example we will create an extended ACL that will deny FTP traffic from network 10.0.0.0/8 but allow other traffic to go through.
Note: FTP uses TCP on port 20 & 21.
Define which protocol, source, destination and port are denied:
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 21
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 20
Router(config)#access-list 101 permit ip any any
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 101 out
Notice that we have to explicit allow other traffic (access-list 101 permit ip any any) as there is an “deny all” command at the end of each ACL.
As we can see, the destination of above access list is “187.100.1.6 0.0.0.0″ which specifies a host. We can use “host 187.100.1.6″ instead. We will discuss wildcard mask later.
In summary, below is the range of standard and extended access list
| Access list type | Range |
| Standard | 1-99, 1300-1999 |
| Extended | 100-199, 2000-2699 |



thank for shareing document,it’s very usefull for me
172.23.16.0 /28
/28 = 11111111.11111111.11111111.11110000 = 255.255.255.240
255.255.255.240 doesn’t convert to 0.0.15.255
11111111.11111111.11111111.11110000 = 255.255.255.240
00000000.00000000.00000000.00001111 = 0.0.0.15
not
00000000.00000000.00001111.11111111 = 0.0.15.255
Unless I missed something…
Roger tat, althought this tut is bit more screwed up than this wildcard.
Sentence
Therefore 255.255.255.240 can be written in wildcard mask as 00000000.00000000.00001111.11111111 = 0.0.15.255
should be replaced by
Therefore 255.255.240.0 can be written in wildcard mask as 00000000.00000000.00001111.11111111 = 0.0.15.255
(decimal mask is jut typo I suppose, since they talk /28, please fix this 9tut Guys)
oops, now I screwed ;) CIDR should be set to /20
Yes, it is a typo. I fixed it. Thanks for your detection!
Extended IP access lists should be placed close to the source.
in this case why we applied it on interface 0/1 ?
i think we should apply it on interface 0/0
also the ACL number is wrong !!
Router(config)#interface Fa0/0
Router(config-if)#ip access-group 101 in
am I right?
Explain pls
@extended: “Extended IP access lists should be placed close to the source” but it is not always the case. We can apply it to either Fa0/0 (inbound) or Fa0/1 (outbound)
In the first example.
access-list 1 permit 10.0.0.0 0.0.0.255
should be
access-list 1 permit 10.0.0.0 0.255.255.255
as the example says 10.0.0.0/8 network.
Please fix it to avoid further confusion.
@Otakking: Yes, I fixed it. Thanks for your detection!
blog.ine.com/2008/09/15/binary-math-part-i/
blog.ine.com/2008/09/16/binary-math-part-i-answers/
blog.ine.com/2008/11/03/binary-math-part-ii/
blog.ine.com/2008/11/05/binary-math-part-ii-answers/
Hi 9tut,
for Extended ACL example, kindly edit the wildcard mask to 0.255.255.255 and also to apply ACL, it should be “ip access-group 101 out” . hope this is helpful.
thanks for the great tutorials.
Yes, @hadezproj is right..
Yes, I updated it. Thanks for your detection!
Hi 9tut,
Thanks for the tutorials.
Can you please provide a situation where an ‘IN’ statement is use. Both examples only used the ‘OUT’ statements
just realize there is an “inbound” example on the next page.
Very handy!
What are dumps?
i think subnet mask of /28 will be 255.255.255.240 and so wild card mask should be 0.0.0.15……….is it right????plzzz explain reply…..
@nikhil: Yes, first convert subnet mask 255.255.255.240 into binary form, then replace all “1″ with “0″ and all “0″ with “1″ and convert back to decimal you will get 0.0.0.15.
Easy way to find a wild card mask from given network address is to do minus last or interested octet of subnet mask from 256 remaing will be the block size and 1 minus from it U’ll have a wild card mask
Eg
192.168.5.1 /28 Its means that the subnet mask will be 255.255.255.240
256-240=16(16 will be the block size means that netowrk will be 192.168.5.0 OR 192.165.5.16 or .32 OR .48 muliple of 16′s)
do 1 minus from it
15..
this means that u’ll have 15 inyour last octet of the MCM
0.0.0.15
Do inform me if i m wrong
Hi Moiz,
Yes that is correct and is the easiest way to figure out VLSM for me anyway!!!
you say in
Router(config)#access-list 1 permit 10.0.0.0 0.255.255.255
(there is always an implicit deny all other traffic at the end of each ACL so we don’t need to define forbidden traffic)
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 1 out
how it is out ?????????
Answer for bokbok july 28th ,2011
apart from 10.0.0.0 0.255.255.255 network it will deny all the traffic which is going out from the interface Fa0/1.
Please some one correct me if i am wrong
/// (notice that we can use ‘telnet’ instead of port 20,21)
Telnet listen on port 23
No qeustion this is the place to get this info, thanks y’all.
/28 is 255.255.255.240 not .240.0
255.255.240.0 is d /20
i am going to appear in the ccna exame so plz guide me and send me the latest dums and a friend who recently passed ccna exame plz contect me my email is
shafqat_25@yahoo.com
9tut, Pls kindly upload about NAT explanation here.
I love to read ur explanation here.
Thanks a million.
@darwin
try here:
http://en.wikipedia.org/wiki/Network_address_translation
@Darwin: For NAT explanation please read: http://www.9tut.com/network-address-translation-nat-tutorial
Please put some light on dark world of Subnetting
Regards,
its very simple way to understand.
thanks
Thanks 9tut.I’m searching for that one http://www.9tut.com/network-address-translation-nat-tutorial.
Hi all, how do you all identify when to apply an access list as inbound or outbound? any tips on how to identify from a diagram?
hii am going to appear in the ccna exam so plz guide me and send me the latest dums.My email id is bhavanavarshney123@yahoo.com
I just took the ccna. The ACL question was hard. It was a large network and it had many portions that were to be allowed. This is what confused me. I can do a simple example but a larger network makes me panic. Help?? How do I handle a large network??
it is very good tutorial
tanks sharing
very nice tutorial….
thanks champ
Hi all
This is with in regards to the Extended IP Access List section of the notes….
I am thinking won’t it be better applying the access list to F0/0 as we want to block FTP traffic from network 10.0.0.0/8 coming into F0/0 interface of the router….as below
Router(config)#interface Fa0/0
Router(config-if)#ip access-group 101 in
Please correct me as I am may be wrong… I was going through this as I ready myself for the exam…
Thanks
can anyone explain me difference between these 2 commands
access-list 100 permit tcp host 10.0.0.1 eq telnet host 20.0.0.2
access-list 100 permit tcp host 10.0.0.1 host 20.0.0.2 eq telnet
thanx..!!!
@shashika
access-list 100 permit tcp host 10.0.0.1 eq telnet host 20.0.0.2
permit TCP
source host: 10.0.0.1
source port: 23 (telnet)
destination host: 20.0.0.2
destination port: any
access-list 100 permit tcp host 10.0.0.1 host 20.0.0.2 eq telnet
permit TCP
source host: 10.0.0.1
source port: any
destination host: 20.0.0.2
destination port: 23 (telnet)
first line allows traffic returning from a telnet server to a telnet client
second line allows traffic from a telnet client to a telnet server
@xallax
I got your idea. Thanx..
@xallaxCould you PLEASE the port numbers below its creating false knowledge.
I went through all the tutorial ” Excellent” wish can describe when to use Access-Group?
Many Thanks
fix the Define the ACL:
Router(config)#ip access-list extended in_to_out permit tcp host 10.0.0.1 host 187.100.1.6 eq telnet
(notice that we can use ‘telnet’ instead of port 20,21)
@bmw
hey and thank you
@9tut
bmw is referring to the second page on this post. please fix it. thank you
@BMW, @xallax: Thanks, I updated it!
@sanjay….what is your reasoning for applying the extended access list to F0/0 rather than as suggested in the notes…
can anyone please explain?
@mac
it’s an extended ACL and it should be placed as close to the source as possible
Hi 9tut:
On second page, in “Some additional examples”, you have not used the word “Extended” while configuring an ACL 101. Is it not mandatory to use “Extended” keyword while defining them?
Thanks!!
@Nash D: The “extended” word is only used when configuring named ACL. With numbered ACL (like ACL 101) we don’t need to use that word because router 101 is in the range of extended acl.