Access List Tutorial
In this tutorial we will learn about access list.
Access control lists (ACLs) provide a means to filter packets by allowing a user to permit or deny IP packets from crossing specified interfaces. Just imagine you come to a fair and see the guardian checking tickets. He only allows people with suitable tickets to enter. Well, an access list’s function is same as that guardian.
Access lists filter network traffic by controlling whether packets are forwarded or blocked at the router’s interfaces based on the criteria you specified within the access list.
To use ACLs, the system administrator must first configure ACLs and then apply them to specific interfaces. There are 3 popular types of ACL: Standard, Extended and Named ACLs.
Standard IP Access List
Standard IP lists (1-99) only check source addresses of all IP packets.
Configuration Syntax
| access-list access-list-number {permit | deny} source {source-mask} |
Apply ACL to an interface
| ip access-group access-list-number {in | out} |
Example of Standard IP Access List
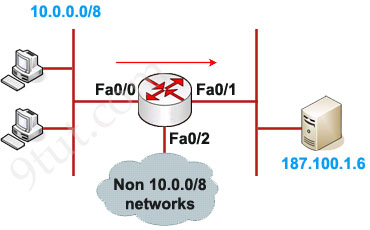
Configuration:
In this example we will define a standard access list that will only allow network 10.0.0.0/8 to access the server (located on the Fa0/1 interface)
Define which source is allowed to pass:
Router(config)#access-list 1 permit 10.0.0.0 0.255.255.255
(there is always an implicit deny all other traffic at the end of each ACL so we don’t need to define forbidden traffic)
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 1 out
The ACL 1 is applied to permit only packets from 10.0.0.0/8 to go out of Fa0/1 interface while deny all other traffic. So can we apply this ACL to other interface, Fa0/2 for example? Well we can but shouldn’t do it because users can access to the server from other interface (s0 interface, for example). So we can understand why an standard access list should be applied close to the destination.
Note: The “0.255.255.255″ is the wildcard mask part of network “10.0.0.0″. We will learn how to use wildcard mask later.
Extended IP Access List
Extended IP lists (100-199) check both source and destination addresses, specific UDP/TCP/IP protocols, and destination ports.
Configuration Syntax
| access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port] |
Example of Extended IP Access List
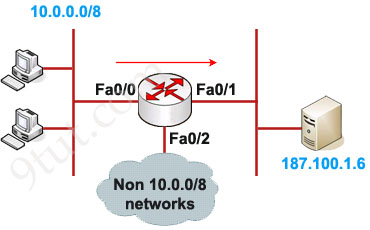
In this example we will create an extended ACL that will deny FTP traffic from network 10.0.0.0/8 but allow other traffic to go through.
Note: FTP uses TCP on port 20 & 21.
Define which protocol, source, destination and port are denied:
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 21
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 20
Router(config)#access-list 101 permit ip any any
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 101 out
Notice that we have to explicit allow other traffic (access-list 101 permit ip any any) as there is an “deny all” command at the end of each ACL.
As we can see, the destination of above access list is “187.100.1.6 0.0.0.0″ which specifies a host. We can use “host 187.100.1.6″ instead. We will discuss wildcard mask later.
In summary, below is the range of standard and extended access list
| Access list type | Range |
| Standard | 1-99, 1300-1999 |
| Extended | 100-199, 2000-2699 |



Thanks for clarifying it 9tut.
what’s the main difference btw standard and extended access list
pls share some point about this
thx
@akhil: The main difference is in the extended acl you can specify protocol (IP, UDP or TCP) and the port number.
In example for standard ACLs, i have a question.
i think in the interface f0/1, we need to apply (IN instead OUT).
interface f0/1
ip access-group 1 in
Because the ip come in f0/1 ALCs filter and allow or deny packet to server. If we use “OUT” all IP packet come in f0/1 will allow to server and server reply at f0/1 the packet will be deny. why we don’t deny first time ?
Hi akhil
Main difference between standard and extended access list are:
Standard filter only source address and extended check source, destination and specific UDP/TCP/IP protocols, and destination ports.
Hi 9tut
i Know how using OUT :| “shy”.
OUT at router and IN at server. ALC apply at this router. So very helpfull. Thank all
ANU TU..i did not understand yur last statement.can u please explain…..y IN and OUT we are applying
In Extended ACL i think it should be configured on interface f0/0 (Extended IP access lists should be placed close to the source.).
We apply to fa0/1 since we are interested in permitting telnet to 187.x.x.x network only but if non 10.0.0.0/8 ntwk was included then ACL could have been applied at fa0/0 ……
hi all brother i’m going to take the CCNA exam at the end of November 2011, so any one who can send me the latest sample exams at abduha006@yahoo.com
is highly appriciated tanks All
To deny telnetting to any router from a specific host
access-list .. deny SOURCE IP 0.0.0.0
go to telnet port
line vty 0 4
access-class .. in
hi all…my ccna xam on 11 dec 2011… please share any latest expereince and dumps
i’m taking the ccna exam really soon, can you plz send me the latest dumps to the email of:
raykhal@yahoo.com
Thank you
Very nice platform to Learn & to discuss. Thanks 9tut.
guys, i am gonna appear in ccna exam in a week. kindly send me latest dumps at art_imran@yahoo.com
Thanks you all
Hello,
@9tut, there is still a mistake here :
For example, we want to create a standard ACL which will only allow network 172.23.16.0/28 to pass through. We need to write an ACL, something like this:
access-list 1 permit 172.23.16.0 255.255.240.0
The network should be 172.23.16.0 /20, no ?
@ciscoman
you do not use subnet masks on access lists, you use wildcard masks.
the correct wildcard mask on this particular scenario would be 0.0.15.255
@ 9tut, just a little confused here. Standard ACL’s are supposed to be close to the source, as you state up above. So we have a packet leaving from FA0/0 to FA0/1, so the ACL should be placed near FA0/0?So why in you explanation do you say that standard ACL should be near the destination??
@BIGD: It’s just a recommendation. In some cases we can put standard ACL near the source, depending which networks we want to filter.
@9tut, so I fully understand, if that was a real network, where would you exactly place that ACL?
@BIGD: If that is a real network then we should place it near the source.
@xallax
Yes, you right, I’ve just put a copy paste of the text in this tutorial, which should be modified.
@9tut, can you do the modifications?
@CiscoMan: Maybe you should re-post your comment.
@9tut, i though that that STANDARD ACL is placed near the destination and an EXTENDED is placed near the source or destination, am I correct here?
@BIGD: It is just a recommendation. In real life you can place ACL near the source or destination, it depends on the requirements.
For the first Extended access-list example, wouldn’t you apply it as shown below? being that the traffic is coming from network 10.0.0.0/8, and the rule states that “Extended IP access lists should be placed close to the source.” I realize that in real life, it would depend on other variables, but if we follow the guides lines provided on this example, the access-list should have been apply as indicated below. Please advise when possible. Thanks, and yes good stuff!!!
Router(config)#interface Fa0/0
Router(config-if)#ip access-group 101 in
Thank you for the tutorial.
Anyone is studying CCNA now? Anyone with the latest dumps? tycoonrp@hotmail.com
Thanks in advance.
when we should use “in” and when we should use “out”?
thank you
‘In’ should be used when you want to filter traffic from the source address before they enter the router. In most cases, it is used for extended access-list. I.e based on d source address or protocol before they enter the router for processing. ‘out’ are mostly used in cases of standard access-list when you filter traffic close to the destination i.e after being proccessed by the router and is being forwarded outbound.
In short, ‘in’ is mostly used for extended while ‘out’ is used for standard. But its not limited to that, thats jst to allow u rmb easily
That’s to my own little undestanding. If am wrong kindly let me know.
I think named ACL has a problem associated.
Since we can not type “ip access-list extended in_to_out permit tcp host 10.0.0.1 host 187.100.1.6 eq telnet” as a single line in the Global Mode.
Correct commands would be:
Router(config)#ip access-list extended in_to_out
Router(config-ext-nacl)#permit tcp host 10.0.0.1 host 187.100.1.6 eq telnet
just found this site and it was awesome
Anyway im gonna take ccna on march, please send new dumps randiard90@gmail.com
Thanks before
Hi friends could you please explain that access list number “Access list 101″ what is this is?
Hi Srini,
Standard ACL 1-99
Extended ACL 100-199
So Access list 101 extended ACL…
dont know if it was mentioned, but regarding wildcards masks: is it not easier to subtract the subnet mask from 255.255.255.255 and you dont need to convert it to binary?
for example:
255.255.255.255
-255.255.240.0
————————–
0.0.15.255
Good explain, it would be better if 9tut explain regarding , that why we put SAC near to destination and EAC near to source ?
@9tut
Can I configure numbered acl like this:
Router(config)#ip access-list extended 101
Router(config-ext-nacl)#permit tcp host…..
Thanks!
hi could anyone translate this conditions for me in a more simpler manner. ^^
1. Your router is to block access to and from “host number 10″ on each of your subnets.
2. You are not to block other networks “host number 10″ from accessing your subnets.
can any one provide, explain about in and out on interface for acl?
can any one tell me about inbound and outbound, suppose we have applied an accesslist to ethernet interface inbound direction, so router will filter the traffic that is destined for our lan or that is leaving our lan? i am confused plz.
Love this site. A lot easier to stay awake reading here than reading my Cisco books.
Can someone please send me the lastest dumps to Bran743@yahoo.com? Thanks.
“Extended IP access lists should be placed close to the source.”
in this case why we applied it on interface 0/1 , my point of view is that if we apply on interface 0/0 we could have save Router CPU resources from processing those packets trans-versing from interface 0/1 to interface 0/0.
i thought the access list should be applied to telnet traffic from leaving 10.0.0.0 network and going out through the fa0/0 interface, if dats correct, y isn’t it applied in the out direction. since it will go out of the fa0/0 interface on to the 187.x.x.x network? pls can some1 xplain.
Plzz send new dumps here sid.rembhotkar@gmail.com
Why need Wildcard Mask instead of SM?
@arafat
ACLs dont use subnet masks.
you have to specify the range being filter by using a wildcard mask.
thank u for explaining access-list…………….
I believe there is something wrong with the Access-list command above
access-list 1 permit 172.23.16.0 255.255.240.0
/28 should have been
255.255.255.240
As a result 172.23.16.0 255.255.255.240 and since we can not use subnet mask it will be
access-list permit 172.23.16.0 0.0.0.15
regards,
I wonder on your extended access-list, what if I apply the command
ip access-group 101 in on interface fa0/0
assuming there is no FTP server behind fa0/2 interface.
Will i get wrong on the real exam?
What happened to the theory of applying Extended Access-list as close to the source?
regards,
@xallax: Thannks
@ethioloin
i agree with “eh.my.way” the best way to go is ip access-group fa0/0 in. since it will save router cpu. instead of consuming router cpu on deciding which interface the packet from fa0/0 will go, the router can just filter it before it enters the fa0/0