CCNA – NAT & PAT Questions
Here you will find answers to NAT & PAT Questions
Note: If you are not sure about NAT & PAT, please read my NAT tutorial.
Question 1
Refer to the exhibit. What does the (*) represent in the output?
| 02:16:29: NAT: s=10.10.0.2->1.2.4.2, d=1.2.4.1 [51607] 02:16:29: NAT: s=1.2.4.1, d=1.2.4.2->10.10.0.2 [55227] 62:16:29: NAT*: s=10.10.0.2->1.2.4.2, d=1.2.4.1 [51608] 02:16:29: NAT*: s=10.10.0.2->1.2.4.2, d=1.2.4.1 [51609] |
A. Packet is destined for a local interface to the router.
B. Packet was translated, but no response was received from the distant device.
C. Packet was not translated, because no additional ports are available.
D. Packet was translated and fast switched to the destination.
Answer: D
Explanation
The above output is from the “debug ip nat” command. In this output, the first two lines show the Domain Name System (DNS) request and reply debugging output.
In the first line (DNS request):
s=10.10.0.2->1.2.4.2: source of the IP address (10.10.0.2) and how it is being translated (to 1.2.4.2)
d=1.2.4.1: destination address of the packet
[51607]: the IP identification number of the packet
In the second line (DNS reply):
s=1.2.4.1: source of the reply
d=1.2.4.2->10.10.0.2: how the destination is being translated
The remaining lines show debugging output from a Telnet connection from a host on the inside of the network to a host on the outside of the network. All Telnet packets, except for the first packet, were translated in the fast path, as indicated by the asterisk (*).
Note: If the connection is already established, the security appliance does not need to re-check packets and the packets are sent to the Fast Path.
(Reference: http://www.cisco.com/en/US/docs/ios/12_3t/debug/command/reference/dbg_i2gt.html)
Question 2
Refer to the exhibit. What command sequence will enable PAT from the inside to outside network?
| ip nat pool isp-net 1.2.4.10 1.2.4.240 netmask 255.255.255.0 ! interface ethernet 1 description ISP Connection ip address 1.2.4.2 255.255.255.0 ip nat outside ! interface ethernet 0 description Ethernet to Firewall eth0 ip address 10.10.0.1 255.255.255.0 ip nat inside ! access-list 1 permit 10.0.0.0 0.255.255.255 |
A. (config)# ip nat pool isp-net 1.2.4.2 netmask 255.255.255.0 overload
B. (config-if)# ip nat outside overload
C. (config)# ip nat inside source list 1 interface ethernet1 overload
D. (config-if)# ip nat inside overload
Answer: C
Explanation
The command “ip nat inside source list 1 interface ethernet1 overload” means:
+ “ip nat”: use NAT
+ “inside”: NAT from inside to outside
+ “source list 1″: the source addresses can be found in access list 1
+ “interface ethernet1″: NAT out of this interface
+ “overload”: use NAT overload (PAT)
Question 3
Refer to the exhibit. A junior network engineer has prepared the exhibited configuration file. What two statements are true of the planned configuration for interface fa0/1? (Choose two)

A. The two FastEthernet interfaces will require NAT configured on two outside serial interfaces.
B. Address translation on fa0/1 is not required for DMZ Devices to access the Internet.
C. The fa0/1 IP address overlaps with the space used by s0/0.
D. The fa0/1 IP address is invalid for the IP subnet on which it resides.
E. Internet hosts may not initiate connections to DMZ Devices through the configuration that is shown.
Answer: B E
Explanation
Both inside FastEthernet interfaces can use only one outside interface to go to the Internet -> A is not correct.
DMZ devices use IP addresses in the range of 128.107.1.128/25 which are public IP addresses so they don’t need address translation to access the Internet -> B is correct.
The fa0/1 interface’s IP address is 128.107.1.254 255.255.255.128 (range from 128.107.1.128 to 128.107.1.255) while the IP address of s0/0 is 128.107.1.1 255.255.255.252 (ranges from 128.107.1.0 to 128.107.1.4) so they are not overlapped with each other -> C is not correct.
DMZ devices are in the range of 128.107.1.128/25 (from 128.107.1.128 to 128.107.1.255) and fa0/1 IP address (128.107.1.254) is a valid IP address on this subnet -> D is not correct.
DMZ devices (and other internal hosts) are using dynamic PAT, which is a type of dynamic NAT. With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. In other words, if DMZ devices communicate with outside hosts first, dynamic translation works fine. But if outside hosts communicate with DMZ devices first, no translation is created in NAT table and the packets will be dropped. This is the reason why “Internet hosts may not initiate connections to DMZ Devices through the configuration that is shown” -> E is correct.
Question 4
Refer to the exhibit. What statement is true of the configuration for this network?

A. The configuration that is shown provides inadequate outside address space for translation of the number of inside addresses that are supported.
B. Because of the addressing on interface FastEthernet0/1, the Serial0/0 interface address will not support the NAT configuration as shown.
C. The number 1 referred to in the ip nat inside source command references access-list number 1.
D. ExternalRouter must be configured with static routers to network 172.16.2.0/24
Answer: C
Explanation
The “list 1″ refers to the access-list number 1.
Question 5
What are two benefits of using NAT? (choose two)
A. NAT protects network security because private networks are not advertised.
B. NAT accelerates the routing process because no modifications are made on the packets.
C. Dynamic NAT facilitates connections from the outside of the network.
D. NAT facilitates end-to-end communication when IPsec is enable.
E. NAT eliminates the need to re-address all host that require external access.
F. NAT conserves addresses through host MAC-level multiplexing.
Answer: A E
Explanation
By not reveal the internal Ip addresses, NAT adds some security to the inside network -> A is correct.
NAT has to modify the source IP addresses in the packets -> B is not correct.
Connection from the outside of the network through a “NAT” network is more difficult than a more network because IP addresses of inside hosts are hidden -> C is not correct.
In order for IPsec to work with NAT we need to allow additional protocols, including Internet Key Exchange (IKE), Encapsulating Security Payload (ESP) and Authentication Header (AH) -> more complex -> D is not correct.
By allocating specific public IP addresses to inside hosts, NAT eliminates the need to re-address the inside hosts -> E is correct.
NAT does conserve addresses but not through host MAC-level multiplexing. It conserves addresses by allowing many private IP addresses to use the same public IP address to go to the Internet -> F is not correct.
Question 6
Which two statements about static NAT translations are true? (choose two)
A. They are always present in the NAT table.
B. They allow connection to be initiated from the outside.
C. They can be configured with access lists, to allow two or more connections to be initiated from the outside.
D. They require no inside or outside interface markings because addresses are statically defined.
Answer: A B
Explanation
With static NAT, translations exist in the NAT translation table as soon as you configure static NAT command(s), and they remain in the translation table until you delete the static NAT command(s).
With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. Dynamic translations have a timeout period after which they are purged from the translation table.
-> A is correct.
Because static NAT translations are always present in the NAT table so outside hosts can initiate the connection without being dropped -> B is correct.
Static translations can not be configured with access lists. To configure static NAT, we only need to specify source IP, NAT IP, inside interface & outside interface.
-> C is not correct.
We have to specify which is the inside and outside interface -> D is not correct.
For your information, below is an example of configuring static NAT:
R0(config)#int f0/0
R0(config-if)#ip nat inside
R0(config-if)#int f0/1
R0(config-if)#ip nat outside
R0(config)#ip nat inside source static 10.0.0.1 200.0.0.2
(Reference: http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080093f31.shtml)
Question 7
Refer to the exhibit. Which statement about packet addresses are true during data exchange when host A makes Web-request to WWW Server, considering that there is NAT overload scheme for data passing from Corp LAN hosts to outside networks in use?
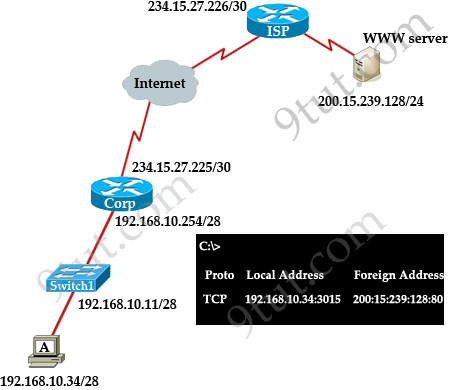
A. Source 234.15.27.226:3015 and destination 234.15.27.225:80
B. Source 200.15.239.128:3015 and destination 192.168.10.34:80
C. Destination 192.168.10.11:3015 and source 200.15.239.128:80
D. Source 192.168.10.34:80 and destination 192.168.10.254:3015
E. Destination 234.15.27.225:3015 and source 200.15.239.128:80
Answer: E
Explanation
From A to Corp router:
+ Source: 192.168.10.34: 3015 & Destination: 200.15.239.128:80
From Corp to WWW Server:
+ Source: 234.15.27.225:3015 & Destination: 200.15.239.128:80
From WWW Server to Corp:
+ Source: 200.15.239.128:80 & Destination: 234.15.27.225:3015
From Corp to Host A:
+ Source: 200.15.239.128:80 & Destination: 192.168.10.34:3015
So the only correct answer is E (from WWW server to Corp)



@xallax
Great NAT and PAT questions.
So let me get this straight: The flow is from the WEB Server back to host A. Hence, option E chosen as the right answer.
Let say, if the flow is from host A to WEB Server. Would option D be considered the correct answer? Or would it be: Source 192.168.10.34:80 Destination 234.15.27.225:3015
And by the way, how do you figure out the flow? If you don’t mind explaining. Thanks.
@xallax
Above comment inregard to Q7. Thanks.
The destination port for a web server is ALWAYS port 80. the source port from a host can be anything in the random port scope. If you look at the cmd prompt output you notice the source port on th ehost is 3015 and the destination port on the web server is 80. the web server will than have to send the packet back to the PUBLIC IP of the host (because of nat) on the port that the host orginally sent it out on (3015).
the IPs you would choose by looking at the NATs and the IP schema.
@anonymous
Thanks for explanation.
@anonymous
about Q7
the only option that could be true is option E
you must take into consideration both L3 and L4 information (IP and port)
Thanks. Explanation very clear. My point is since host A initiated the request, why is the data flow not from host A to WWW server? Thanks.
@last poster
are you referring to Q7?
i’ve said it above
“the only option that could be true is option E
you must take into consideration both L3 and L4 information (IP and port)”
what makes you think it isn’t from A to server at start? it is.
but then it also has to return to A so it will be from the server to A and this is where the flow reverses
@xallax
Thanks.
Yep. referring to Q7.
Anyway, it seems the only option that makes sense is E. The flow is reverse.
i am not clear Q7 writing, I know about NAT and PAT concept very well any so many time testing with GNS3 and Packet Tracer. But i don’t understand what they ask.
>>>>>>
Refer to the exhibit. Which statement about packet addresses are true during data exchange when host A makes Web-request to WWW Server, considering that there is NAT overload scheme for data passing from Corp LAN hosts to outside networks in use?
>>>>>>
they say host A makes Web-request to WWW Server >>>>
data passing from Crop LAN hosts to outside network >>>>
that mean packet is going to Host A to outside network >>> right?
pls explain me ! ! !
@Anonymous: Q7 wants to test you the whole process when host A sends a request until it gets a reply. That means the traffic goes in both ways:
+ From host A to WWW server (request)
+ From WWW server back to host A (reply)
Maybe you think they only ask the outgoing traffic but it is not true.
Q7 was on the ICND2 today.
Wow Nat questions are very much tricky :|
Can some body send me latest dump?
I will really appreciate it
Amjadstocks@gmail.com
Thanks
Can some body send me latest dump of ccna
chaudaryimran@hotmail.com
question # 3
At first I was confused by the answer “E” for this one. However, I think I see why this is correct. Please advise if I am on the right track. “This is “Dynamic Nat” because there was no “pool” of ip addresses defined for the IP’s to be natted to. The access list defines that are permitted to be natted and the “source list” command is the 2ns step that ‘allows’ the ip’s to be natted dynamically to the outside interface where ‘overloading’ is enabled. Dynamic Nat does not use a pool.”
@certnow
I think you are confusing yourself.
Option B simply mean since DMZ device already has a public ip, it will not subjected to Address Translation. 128.107.1.128 is a public ip, it cannot be translated any further. And option E simply means, since this is a DMZ device, therefore this configuration cannot be initiated via the internet.
My advice is, you try and figure out the differences between Dynamic Nat, Static Nat, PAT, Port Forwarding. This will improve your understanding a great deal. Thanks.
Can you explain why in question 5, in your explaination you said C is correct?
@ Anonymous
I’m pretty sure is a typo. Option C is definitely not correct. Thanks for pointing it out.
@xallax
Q5
Can you kindly correct the explanation pointing to Option C as being correct. Thanks.
Answer C of question 5 is not correct. It is a typo, I updated it! Thanks all.
@9tut
regarding Q1
[51607]: the IP identification number of the packet
shouldn’t that be the port number used to identify which host is the source?
thank you
@xallax
Yes, it seems the IP identification number should be used to identify which host is the source.
This is pertinent in the return trip. The router has already assigned unique port number to enable it map packet to the right source(host)……eg inside global(unique port number/IP identification number) to inside local(Source IP/Host)
I hope this makes some sense. Thanks.
Q7:
I understand the answer, but i was confused because of the Corp [192.168.10.254 /28] address. I assume this was the gateway for host A, no ? If so how is that possible ?
@Pete
Q7
Yes, it is the gateway. And this where the translation(NAT) takes place…[Inside local to global local]
I hope this helps.Thanks.
Experts,
Just had a doubt regarding Q7 .
So, what are the outside local & global address in this scheme. I understand that the Inside local is 192 address of host A, and the inside global is 234.15 address, but is someone could guide me on the outside local and global addresses, would appreciate!
Thanks.
To add to the previous question, is it that the 200.15 address of the web server is the outside local while the 234.15.27.226 the outside global?
Please guide!
Thanks a tonne
@xallax: It is not the port number, it is just an identification number. We can view the port number with the “show ip nat translations” command.
@Vinie: When the packet moves from the inside to the outside network, the outside local and global address are the same: 200.15.239.128.
@9tut
thank you!
some WAN questions came out that i havent seen before… pls
I have the first CCNA exam after two weeks please forward the new dump by email shiferaw123@yahoo.com
Can someone please email me the latest CCNA dumps. I will be taking the exam in a couple of weeks.
Thank you much
email: akilimak@yahoo.com
Thanks,
-Reg
Dears
if you have any latest dumps please send me because my exam is on this week end
hossam.saber4@gmail.com
thnx in advance
The key here is that a private IP can’t directly with a public IP address, and a public IP address can’t talk directly with a private address. Only public addresses can talk with public addresses directly and that’s where the role of CORP comes in, as local hosts using NAT must communicate through it
The key here is that a private IP can’t talk directly with a public IP address, and a public IP address (ON THE INTERNET) can’t talk directly with a private address. Only public addresses can talk with public addresses directly and that’s where the role of CORP comes in, as local hosts using NAT must communicate through it
Can Someone please send me the latest dump, i am going to take the exam next week.
pranay.srivastava23@gmail.com
can someone explain dis fr q7)
From A to Corp router:
+ Source: 192.168.10.34: 3015 & Destination: 200.15.239.128:80
here why u didn’t put destination as 234.15.27.225???
pl make me clear in this question. i’m so confused totally
Hi,
Can someone send me the latest dump, I’m going to take the exam this weekend.
Thank you so much.
Hi,
Can someone send me the latest dump, I’m going to take the exam this weekend.
Thank you so much.
michel0906@gmail.com
Thank you again.
@bakki
Q7.
First, you have to identify the data flow.
There are kinds of data flow to the above example, The Forward Flow, and The Reverse Flow.
The question asked above is for the Reverse Flow. From the Foreign Address(www) to Local address(host A). Assuming host A has already made the request.
Foreign address is the Source 200.15.239.128:80 / Local address is the Destination 192.168.10.34:3015
So basically, on the reverse flow, from the ISP-www. The Corp router is where Natting takes place. Translating outside local address(outside global address) to inside global address, thus, Source 200.15.239.128:80 to Destination 235.15.27.225:3015
The question you are asking is for the forward flow.
I hope this helps. Thanks.
@koffy
In the question,indicate that
“when host A makes Web-request to WWW Server”.If host A makes web-request to www server, normally we consider host A to www. but u mentionsioned www to host A. so how can you tell that is reversed flow?can u make this clear to me??
Anyone know if these are the same questions for the icnd2?
@bakky
I meant the assumption is that host A has already placed the request. Which we are not concerned about. We are more concern about the returned request. www returning the request placed by host A.
Host A to www>>>Forward flow
www to Host A>>>Reverse flow or call it Backward flow
Bareinmind, this scenario is just related to the above example.
I hope this helps. Thanks.
somebody plz explain..i found this Q also on todd lammle book
http://uploadpic.org/v.php?img=tn173wzBfp
@z
as far as i know, we pick the one with the longest prefix length, 19
option A
@ xallax
but dont u think it should b “prefix-length 21″.?
cause that way it cover from 1.1.18.0–1.1.135.255
@z
yet, that’s the best option given. i’m just saying it after reading comments on cisco’s site…
Sorry, I don’t understand.
Quote:
********************
From Corp to Host A:
+ Source: 192.168.10.254:80 & Destination: 192.168.10.34:3015
********************
192.168.10.254 is the Router LAN interface. I think it should be:
From Corp to Host A:
+ Source: 200.15.239.128:80 & Destination: 192.168.10.34:3015
Am I wrong?
@JK
I agree with you, but I’m not sure!
@ All
Please explain if we are wrong!
thanks!:)
Sorry because my Eng.
QUESTION 2:
what if you want to use the pool of public ip’s(many private to many public)? will the command below work?
ip nat inside source list 1 pool isp-net overload
Also,
on your nat inside interface, if you have sub-interfaces for a router-on-a-stick configuration, where would you execute the command “ip nat inside”, at the physical interface or each sub-interfaces?
TIA