CCNA – Subnetting Questions 4
Here you will find answers to Subnetting Questions – Part 4
Note: If you are not sure about Subnetting, please read my Subnetting tutorial.
Question 1
You are working in a data center environment and are assigned the address range 10.188.31.0/23. You are asked to develop an IP addressing plan to allow the maximum number of subnets with as many as 30 hosts each.Which IP address range meets these requirements?
A. 10.188.31.0/27
B. 10.188.31.0/26
C. 10.188.31.0/29
D. 10.188.31.0/28
E. 10.188.31.0/25
Answer: A
Explanation
Each subnet has 30 hosts < 32 = 25 so we need a subnet mask which has at least 5 bit 0s -> /27. Also the question requires the maximum number of subnets (which minimum the number of hosts-per-subnet) so /27 is the best choice -> A is correct.
Question 2
Refer to the exhibit. The Lakeside Company has the internetwork in the exhibit. The Administrator would like to reduce the size of the routing table to the Central Router. Which partial routing table entry in the Central router represents a route summary that represents the LANs in Phoenix but no additional subnets?

A. 10.0.0.0 /22 is subnetted, 1 subnet
D 10.0.0.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
B. 10.0.0.0 /28 is subnetted, 1 subnet
D 10.2.0.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
C. 10.0.0.0 /30 is subnetted, 1 subnet
D 10.2.2.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
D. 10.0.0.0 /22 is subnetted, 1 subnet
D 10.4.0.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
E. 10.0.0.0 /28 is subnetted, 1 subnet
D 10.4.4.0 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
F. 10.0.0.0 /30 is subnetted, 1 subnet
D 10.4.4.4 [90/20514560] via 10.2.0.2 6w0d, serial 0/1
Answer: D
Explanation
All the above networks can be summarized to 10.0.0.0 network but the question requires to “represent the LANs in Phoenix but no additional subnets” so we must summarized to 10.4.0.0 network. The Phoenix router has 4 subnets so we need to “move left” 2 bits of “/24″-> /22 is the best choice -> D is correct.
Question 3
Which address range efficiently summarizes the routing table of the addresses for router main?
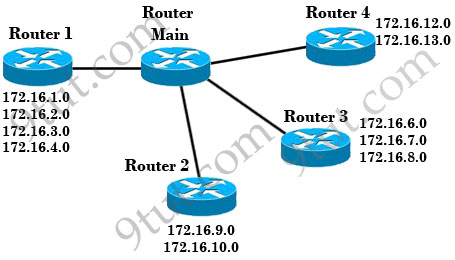
A. 172.16.0.0/18
B. 172.16.0.0/16
C. 172.16.0.0/20
D. 172.16.0.0/21
Answer: C
Explanation
To summarize these networks efficiently we need to find out a network that “covers” from 172.16.1.0 -> 172.16.13.0 (including 13 networks < 16). So we need to use 4 bits (24 = 16). Notice that we have to move the borrowed bits to the left (not right) because we are summarizing.
The network 172.16.0.0 belongs to class B with a default subnet mask of /16 but in this case it has been subnetted with a subnet mask of /24 (we can guess because 172.16.1.0, 172.16.2.0, 172.16.3.0… are different networks).
Therefore “move 4 bits to the left” of “/24″ will give us “/20″ -> C is the correct answer.
Question 4
Refer to the exhibit. A new subnet with 60 hosts has been added to the network. Which subnet address should this network use to provide enough usable addresses while wasting the fewest addresses?
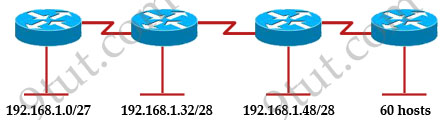
A. 192.168.1.56/27
B. 192.168.1.64/26
C. 192.168.1.64/27
D. 192.168.1.56/26
Answer: B
Explanation
60 hosts < 64 = 26 -> we need a subnet mask of at least 6 bit 0s -> “/26″. The question requires “wasting the fewest addresses” which means we have to allow only 62 hosts-per-subnet -> B is correct.
Question 5
The network technician is planning to use the 255.255.255.224 subnet mask on the network. Which three valid IP addresses can the technician use for the hosts? (Choose three)
A. 172.22.243.127
B. 172.22.243.191
C. 172.22.243.190
D. 10.16.33.98
E. 10.17.64.34
F. 192.168.1.160
Answer: C D E
Explanation
From the subnet mask of 255.255.255.224 we learn:
Increment: 32
Network address: In the form of x.x.x.(0,32, 64, 96, 128, 160, 192, 224)
Broadcast address: In the form of x.x.x.(31,63,95,127,159,191,223)
-> All IP addresses not in the above forms are usable for host -> C D E are correct answers.
Question 6
In the implementation of VLSM techniques on a network using a single Class C IP address, which subnet mask is the most efficient for point-to-point serial links?
A. 255.255.255.240
B. 255.255.255.254
C. 255.255.255.252
D. 255.255.255.0
E. 255.255.255.248
Answer: C
Explanation
The subnet mask of 255.255.255.252 gives only 2 usable host addresses because it has only 2 bit 0s (22 – 2 = 2) so it is the most efficient subnet mask for point-to-point serial links (and you should remember it).
Question 7
Refer to the exhibit. HostA cannot ping HostB. Assuming routing is properly configured, what could be the cause of this problem?

A. HostA is not on the same subnet as its default gateway.
B. The address of SwitchA is a subnet address.
C. The Fa0/0 interface on RouterA is on a subnet that can’t be used.
D. The serial interfaces of the routers are not on the same subnet.
E. The Fa0/0 interface on RouterB is using a broadcast address.
Answer: D
Explanation
Now let’s find out the range of the networks on serial link:
For the network 192.168.1.62/27:
Increment: 32
Network address: 192.168.1.32
Broadcast address: 192.168.1.63
For the network 192.168.1.65/27:
Increment: 32
Network address: 192.168.1.64
Broadcast address: 192.168.1.95
-> These two IP addresses don’t belong to the same network and they can’t see each other -> D is the correct answer.
Question 8
The network administrator is asked to configure 113 point-to-point links. Which IP addressing scheme best defines the address range and subnet mask that meet the requirement and waste the fewest subnet and host addresses?
A. 10.10.0.0/18 subnetted with mask 255.255.255.252
B. 10.10.0.0/25 subnetted with mask 255.255.255.252
C. 10.10.0.0/24 subnetted with mask 255.255.255.252
D. 10.10.0.0/23 subnetted with mask 255.255.255.252
E. 10.10.0.0/16 subnetted with mask 255.255.255.252
Answer: D
Explanation
We need 113 point-to-point links which equal to 113 sub-networks < 128 so we need to borrow 7 bits (because 2^7 = 128).
The network used for point-to-point connection should be /30.
So our initial network should be 30 – 7 = 23.
So 10.10.0.0/23 is the correct answer.
You can understand it more clearly when writing it in binary form:
/23 = 1111 1111.1111 1110.0000 0000
/30 = 1111 1111.1111 1111.1111 1100 (borrow 7 bits)
Question 9
If an Ethernet port on a router was assigned an IP address of 172.1.1.1/20, what is the maximum number of hosts allowed on this subnet?
A. 4094
B. 1024
C. 8190
D. 2046
E. 4096
Answer: A
Explanation
In the prefix /20 we have 12 bit 0s so the number of hosts-per-subnet is 212 – 2 = 4094.
Question 10
A network administrator receives an error message while trying to configure the Ethernet interface of a router with IP address 10.24.24.24/29. Which statement explains the reason for it?
A. The address is a broadcast address
B. The Ethernet interface is faulty
C. VLSM-capable routing protocols must be enable first on the router.
D. This address is a network address.
Answer: D



If an Ethernet port on a router was assigned an IP address of 172.1.1.1/20, what is the maximum number of hosts allowed on this subnet?
A. 4094
B. 1024
C. 8190
D. 2046
E. 4096
Answer: A
Explanation
In the prefix /20 we have 12 bit 0s so the number of hosts-per-subnet is 212 – 2 = 4094
When we will write the 2^k-2
/20 is equal to 255.255.240.0
in binary its 1111 1111.1111 1111.1111 0000.0000 0000
so you have 12 bits of 0′s =2 power 12=4096-2=4094
answer A comes like that
Q9: If an Ethernet port on a router was assigned an IP address of 172.1.1.1/20, what is the maximum number of hosts allowed on this subnet?
A. 4094
B. 1024
C. 8190
D. 2046
E. 4096
We have 2 methods to find it out :
Using Method 1 (Logical): 172.1.1.1 /20
Resolving /20
where n=network bits and H= host bits
1st octet = 8 bits N
2nd octet =8 bits N
3rd octet = 4 bits N
The Magic number i.e. incremental value would be last shifting bit which is 20th bit or the fourth bit of 3rd octet i.e. =====>>> 16. so the range would be like
1st subnet 172.1.1.1 ————————- 172.1.16.255 [ 16 N X 256 H - 2 = 4094 ]
2nd subnet 172.1.17.0 ———————–
Using Method 2 (simply formulatic):
Resolving /20
where n=network bits and H= host bits
1st octet = 8 bits N
2nd octet =8 bits N
3rd octet = 4 bits N
Total bits in IPv4 are 32, of which 20 are network bits and the
Remaining 12 host bits will be represented like 2^12.
And we know the formula to find the number of host i.e. 2^n-2 so….2^12-2= 4094
Q.8
D. 10.10.0.0/23 subnetted with mask 255.255.255.252
base on the prefix /23 should we not have a 255.255.254.0 SM rather then 255.255.255.252?
or is it because the question is asking point-to-point link that’s why we end up with 255.255.255.252?
@jonths
“or is it because the question is asking point-to-point link”
you got it correct there :)
thanks Xallax, but what if the p2p is out of the question but instead just to configure 113 subnet and asking the SM … , does 255.255.254.0 sm should be pick?
@jonths
well…
your questions is this:
I need 113 subnets with ### hosts each. What subnet mask would comprise all of those subnets if they weren’t discontinuous?
with max 2 hosts: /23
with max 6 hosts: /22
with max 14 hosts: /21
with max 30 hosts: /20
with max 1022 hosts: /14 (took pen and paper for this one)
logic:
each subnet occupies N IPs. i need 113 subnets with N IPs each.
113 * N < 2^P
for the last example, 1022 hosts, my logic was:
i need 113 subnets with 1024 IPs (1022 + 2)
113*1024 < 2^18 (2^18 is 128*1024)
that leaves 2^32 (maximum number of bits) : 2^18 (how many bits are occupied by all those subnets) = 2^14 (i'm interested in that 14 because that's the number of bits left)
the mask to comprise the range with 113 subnets of 1022 hosts each is… /14, 255.252.0.0
this is just simple math with a bit of logic.
@xallax/all ; pls help me on this…I’m getting confused on how to solve this:
Refer to the exhibit. In this VLSM addressing scheme, what summary address would be sent from router A?
A.172.16.0.0 /16
B.172.16.0.0 /20
C.172.16.0.0 /24
D.172.32.0.0 /16
E.172.32.0.0 /17
F.172.64.0.0 /16
appreciate your follow-up question Xallax, still trying to figure out your explanation especially on how u came up with those prefix….bit confuse at the moment but i’ll try to disect the logic.
Thanks thou,
@onslaught
would love to see the exhibit :)
can not reply without it, sorry
@jonths
you can convert the numbers to binary, that’s messy and time wasteful, or you can think in powers of 2 (2-4-8-16-32-64-128-256-512-1024. these are the first 10. not hard to remember).
scenario:
Johnny needs 53 subnets with 5 hosts on each subnet. He also wants to know what subnet mask could he use to all the hosts be part of one big subnet if he ever needs that.
how many hosts? 5.
what subnet would accommodate 5 hosts? a subnet with a mask of 255.255.255.248
how many IPs are used by each subnet? 256-248 = 8 IPs (6 usable IPs, 2 for subnet/broadcast)
how many subnets? 53
53 subnets * 8 IPs = 424 IPs
let’s see what subnet mask can be used to best fit for 424 IPs.
424 is bigger than 128 – 2^8
424 is bigger than 256 – 2^9
424 is lesser than 512 – 2^10
the answer is a subnet mask that has 10 bits reserved for the hosts.
we can do this binary style:
1111 1111.1111 1111.1111 1100.0000 0000
255.255.252.0
or we can think it like this:
how many bits are there in a subnet mask? 32
how many used by hosts? 10
how many left for subnetting? 32 – 10 = 22
what does /22 mean? 8 + 8 + 6 + 0
8 + 8 + 6 + 0 means 255.255.252.0
the bits are always assigned from left to right in a group of 8 bits.
0 bits means 0000 0000
3 bits means 1110 0000
7 bits means 1111 1110
and so on
bits to decimal chart
0 – 0
1 – 128
2 – 192
3 – 224
4 – 240
5 – 248
6 – 252
7 – 254
8 – 255
there is also a nice tutorial written by 9tut for subnetting. link:
http://www.9tut.com/subnetting-tutorial
oops…
424 is bigger than 128 – 2^7
424 is bigger than 256 – 2^8
424 is lesser than 512 – 2^9
the mask should be 255.255.254.0…
sorry
Thanks X*X (-_-)
with max 14 hosts: /21
with max 30 hosts: /20
on…. with max 1022 hosts: /14 (took pen and paper for this one)…
is it a /14…. and not /15?
max 1022 host:/15…
@jonths
yes, /15 :D
i should start reading at least once what i’m posting…
I’m a little confused on Q8…
If you need to account for 113 links, wouldn’t that be 226 host addresses? If I’m correct there, then you would need to borrow 8 bits to account for 226 < 254 host addresses. The mask would still be 255.255.255.252 because you need point-to-point links (only 2 hosts per link), but the subnet would be 10.10.0.0/22 (/30 – 8 = /22). Obviously this is wrong, but can someone explain to me why it is wrong?
Disregard my comment on Q8… of course I would figure it out once I post something… :)
Q1 address range 10.188.31.0/23. You are asked to develop an IP addressing plan to allow the maximum number of subnets with as many as 30 hosts each.Which IP address range meets these requirements?
2^5 (5 extra bits) = 32 or 30 Hosts- fine- but surely /23 + 5 = a /28 mask doesn’t it?
So that would mean option D. 10.188.31.0/28
Cheers -Rob
@Roblightwater and @9tut:
At Q1 10.188.31.0/23 is an INVALID network address. I don’t know if it’s a typo or this question was conceived like this, but I believe that it was intended with /24 mask.
One can easily see that /23 networks will always have an even number in the 3rd octet, like: 10.188.0.0
10.188.2.0
10.188.4.0
….
10.188.30.0
10.188.32.0
So in order for the question to be right, something needs to be changed, be it the prefix length or the third octet’s value.
@AdyM: Yes, I agree 10.188.31.0/23 is an invalid network address. Maybe in this question we should ignore the question’s detail, just need to understand how to get the result.
guys i av been today in CCNA exam and its exactly the same question from here and from http://www.examcollection.com i did pass the exam but unfortunately with low score 828 cause of the EIGRP didnt work with me and i have no idea why and because of that i lost 30 mins from 90 mins anyways my question is this will affect me or cisco wont send the certificate for me ????
Regarding Question 3, i think the right answer would be D. 172.16.0.0/21 which is a summarization of 172.16.1.0, 172.16.2.0, 172.16.3.0 and 172.16.4.0 networks. Summary route must point to the same interface.So, i think we can’t summarize all networks 172.16.1.0 through 172.16.13.0 because they don’t resolve to the same interface.I need your opinion about this, are u sure C is the correct answer?
@beginner
Let me try break it down for you. I’m going to use a different approach, so just stay with me.
Question 3 states:
Which address range efficiently summarizes the routing table of the addresses for router main?
This is a class B address. 172.16.0.0…….
Router1 has 4 addresses….Router2 has 2 addresses…..Router3 has 3 addresses….Router4 has 2 addresses. All together equals 11 addresses.
With class B we can only use the last two octet for hosts.
Therefore 11 addresses or hosts falls in the third octet.
128…192….224….240….248….252….254….256
/17 /18 /19 /20
/20=2^4=16 hosts…………We need 11 addresses.
Option C is correct….. To summarized 11 addresses……172.16.0.0/20
I hope this helps.
@koffu
I understand the process of summarization, but the question is tricky i think.It states to efficently summarizes the Table addresses.I think it should be done by each interfeces separately, not the whole table and all addresse.
The routing table for Router Main should look something like this:
S 172.16.0.0/21 out Fa0/1 -> for 1,2,3,4 on the Router1
S 172.16.8.0/22 out Fa0/2 -> for 9,10 on the Router2
S 172.16.0.0/20 out Fa0/3 -> for 6,7,8 on the Router3
S 172.16.12.0/23 out Fa0/3 -> for 12,13 on the Router4
We can summarize only static routes that use the same exit-interface.
How would look like routing table of the Router Main with 172.16.0.0/20, to which exit interface will that route point.
If there was another Router connected to Router Main let’s say via interfaces Fa0/0, then 172.16.0.0/20 in his router table could point to exit-inteface Fa0/0 toward Router Main.
Since English is not my native language maybe i’m missing something.
Thanks for your reply Koffu
@beginner
You are not missing the point. I think you do have a point. I believe in the real world, your idea may jell. The above configuration is just to test your knowledge about how to efficiently summarize addresses.
The objective is power conservation in terms of bandwidth and load, and also keeping the routing table tidy. Routers have the capability of breaking down summary addresses when the need arises.
Basically, this is how i have come to understand it. Thanks.
Thank’s again for your reply, i assume you are right.
Here are some questions that i have found in some dumps and i’m confused about the answers, can anyone help me to clear up the issues:
Question 1. Which component of VPN technology ensures that data can be read only by its intended recipient?
A. data integrity
B. encryption
C. key exchange
D. authentication
Answer is D.
My opinion is that the correct answer should be B because authentication is just a verification of the identity of a person or process that sent the data.
Question 2. What is the function of the command switchport trunk native vlan 999 on a trunk port?
A. It designates VLAN 999 for untagged traffic.
B. It blocks VLAN 999 traffic from passing on the trunk.
C. It creates a VLAN 999 interface.
D. It designates VLAN 999 as the default for all unkown tagged raffic.
Answer is D.
I think answer A is the correct answer, since all tagged frames on the native vlan are dropped.
Question 3. VLAN 3 is not yet configured on your switch.What happens if you set the switchport access vlan 3 commmand interface configuration mode?
A. The command is accepted and the respective VLAN is added to vlan dat.
B. The command is rejected.
C. The command is accepted and you must configure the VLAN manually.
D. The port turns amber.
Answer is A.
I think it should be B.I’ve tried and it was rejected.Cisco tutorial stated that u must first create the VLAN.
Question 4.What is the result of setting the no login command?
Router#config t
Roter(config)#line vty 0 4
Router(config-line)#password c1sco
Router(config-line)#no login
A. The is a virtually limitless supply of IP addresses
B. Telnet access requires a new password at first login
C. Telnet access requires a password
D. Telnet access is denied
Answer is D.
I don’t have a clue what could be the right answer.I know that the command no login removes the requirement for authentication, so anyone could connect to the line using Telnet and it’s a major risk.
I would appriciate your opinions on these issues.
@beginner
Question 1. Which component of VPN technology ensures that data can be read only by its intended recipient?
Option A. Data Integrity……..ensures confidentiality that data is read by only its intended recipient.
Question 2. What is the function of the command switchport trunk native vlan 999 on a trunk port?
Option A. It designates VLAN 999 for untagged traffic……..You can interpret command as an instruction.
Question 3. VLAN 3 is not yet configured on your switch.What happens if you set the switchport access vlan 3 commmand interface configuration mode?
Option A. The command is accepted and the respective VLAN is added to vlan dat……..This command can be describe as a process.
Question 4.What is the result of setting the no login command?
Router#config t
Roter(config)#line vty 0 4
Router(config-line)#password c1sco
Router(config-line)#no login
Option D. Telnet access is denied………..Option D describes or fits the scenario more.
Maybe others may have different option, all is welcome. Thanks.
@koffy
regarding the answer you gave to the 4th question… i disagree…
i’m telling you the effect of that configuration would be to let anyone connect to the device via VTY lines 0-4 without prompting for a password.
@xallax
Thanks. I will check it out on PT sim. I wasn’t too sure of it myself. I learn something new everyday.
@xallax
Do you mean the answer to question 4 is none of the options provided? Advise. Thanks.
@Koffu and xallax
Option A. Data Integrity……..ensures confidentiality that data is read by only its intended recipient.
VPNs achieve confidentiality using mechanisms of encapsulation and encryption.
Data integrity guarantees that no tampering or alterations occur to data while it travels between the source and destination.
So, it should be encryption i suppose.
About Question 3. VLAN 3 is not yet configured on your switch.What happens if you set the switchport access vlan 3 commmand interface configuration mode?
Option A. The command is accepted and the respective VLAN is added to vlan dat……..This command can be describe as a process.
Did u accomplished to assign an interface to a VLAN that does not exist.I can’t do it in Packet Tracer, although i’ve read this somewhere:
A convenient feature of the CLI is that if you assign an interface to a VLAN that does not exist, the new VLAN is created for you.
Thanks
@koffy
the given options were:
A. The is a virtually limitless supply of IP addresses
B. Telnet access requires a new password at first login
C. Telnet access requires a password
D. Telnet access is denied
i don’t know why but option A doesn’t fit in the picture, does it?
i got a feeling option A was the correct answer but its text got messed up doring copy/paste
@beginner
yes, you can assign an interface to a VLAN that is not create and it will get created
@beginner
try this one on a switch:
Switch>en
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#interface fa0/1
Switch(config-if)#switchport access vlan 10
% Access VLAN does not exist. Creating vlan 10
@beginner
Data Integrity/Data Confidentiality are basically the same thing. This is achievable due to encryption protocol/ algorithm(mechanism) placed on the original message into its coded form.
@Koffy
Thank’s for your reply.So you think the right answer is encryption?
Can you give me your opinion abou this question?
When a DHCP server is configured, which two IP addresses should never be assignable to hosts? (Choose two)
A. network or subnetwork IP address
B. broadcast address on the network
C. IP address leased to the LAN
D. IP address used by the interfaces
E. manually assigned address to the clients
F. designated IP address to the DHCP server
Correct answers are A and B.
Could it be C and F also?
I suppose DHCP server automaically exclude network and broadcast addresses.
In every example i’ve saw they excluded addresses like: 192.168.10.1, 192.168.10.1, 192.168.10.254, static addresses reserved for the router interface, switch management IP address, servers, and local network printers and never network and broadcast addresses like 192.168.10.0 or 192.168.10.255
Sorry, not C and F, correct answers may be E and F, or even D if the interfaces are switch management or router interface.
@beginner
it says that they should NEVER ever ever EVER be assignable to hosts.
A and B should never be assignable no matter how the network is designed.
i agree that D, E and F could be problems in a given scenario. for that we use manual bindings to exclude those addresses from pool (they aren’t usable by others, but we know that they are used) or just exclude them all together and avoid a future headache.
problem is that static IPs aren’t permanent, sooner or later that host/device will get removed from the network and you will end up losing 1 IP address. if it’s on a private network you couldn’t care less, right?
i would add to the list the IP address of the DHCP server as cisco says it should never be assignable either
http://www.cisco.com/en/US/docs/ios/12_0t/12_0t1/feature/guide/Easyip2.html#wp22658
@Koffu
Why they mantioned DHCP configuration in the first place? When u lokk at ip dhcp server pool there is a range 192.168.1.1-192.168.1.254 on the interface 192.168.1.254.
I suppose dhcp server use pings to find usable addresses and there are not pings for network and broadcast addresses.If we try to manually assign those two addresses there is error line probably.So, e can’t assign them even if we want to.
If host with static IP address go down, i suppose that static IP address could be assigned via DHCP server to another host when server find no ping on that address , but the problem could arise when the first host comes back up.
What answers would u choose?
@beginner
Addresses are leased to host. A host will usually keep the same address by periodically contacting the DHCP sever to renew the lease.
If a host goes down, the address goes back to the pool. A host will send DHCPDISCOVERY message to DHCP server for an address assignment. This is a process that goes back and forth between the host(client) and the DHCP server.
There are instances where a host(client) might request for a particular address from DHCP server. This sort of thing is more like a negotiation(process) that goes on between client and dhcp server.
Router(config)#line vty0 4
Router(config)#no password
Router(config)#no login
Will prompt to access the remote device without virtual terminal password.
It can cause the network severely risky because no authorized personnels can access the device.
Hello,
i have a question to Q9:
With a mask of /20 you can add 4094 hosts, thats right. But in the Question is an layer 3 interface with 172.1.1.1/20! I think, the correct answer is 2^12 = 4096 – 2 – 1 = 4093!
@Xallaxi
I’ve passed CCNA yesterday, and i suppose the question about DHCP was the only incorrect answer i gave.I’m still waiting for the Final score report from my testing center but i had just one incorrect answer and suppose it was about DHCP. So, i think u were right about it. I was hopping till the end of the exam they wan’t give me that question but supprising it was the last 48 question. I was pretty sure that i will pass the exam and i was in a situation to answer it like i think it should be answered.:)
@beginner
congrats :)
@xallax
Thank’s
@xallax and @9tut
Guys, I have a problem understanding your way of solution in Q8.
Here is how I understand:
You have 113 P2P links, so you need 226 valid host IP adressess. Since netmask is/30 you have 4 IP addresses in each subnet. First is network, then 2 valid host addresses and last broadcast address.
By simple math you get 226*2=452 (since on every 2 valid host addresses you have 2 unusable, broadcast and network) IP addresses.
This leads to conclusion that we need 9 bits to borrow from /32, which is /23.
PS.Good job guys and thanks for this site
Regards
@milos
each P2P subnet takes up 4 IPs. you need 113 subnets.
4*113 = 452
452 consecutive IPs fit in a subnet with a mask of 255.255.254.0 or /23
will 192.168.1.2/24 and 192.168.2.1/25 Both ping ? explain me the procedure thank you
@Slash
What question are you referring to?
hi guys. I don’t understand Q2. How did you come up with /22?
@tohritz
LANs in phoenix are
10.4.0.0/24
10.4.1.0/24
10.4.2.0/24
10.4.3.0/24
the range is 10.4.0.0 ~ 10.4.3.255
if you were to have a single subnet that would accommodate that range which subnet would it be?
how many bits do we need for hosts?
2 bits in the 3rd octet and 8 in the 4th. that’s 10 bits for hosts
how many bits left for networks? 32-10=22
a single subnet would be 10.4.0.0/22
thanks xallax