CCNA – Switch Questions
Here you will find answers about Switch Questions – Part 1
Question 1
Which two commands can be used to verify a trunk link configuration status on a Cisco switch? (choose two)
A. show interfaces trunk
B. show interfaces switchport
C. show ip interface brief
D. show interfaces vlan
Answer: A B
Explanation
The “show interfaces trunk” command and “show interfaces switchport” command can be used to verify the status of an interface (trunking or not). The outputs of these commands are shown below (port Ethernet 1/0 has been configured as trunk):
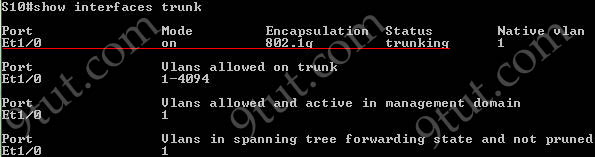
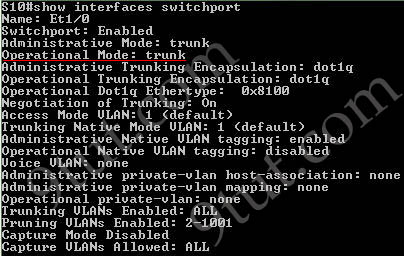
The “show ip interface brief” command only gives us information about the IP address, the status (up/down) of an interface:
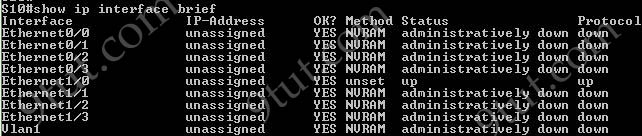
The “show interfaces vlan” command only gives us information about that VLAN, not about which ports are the trunk links:

Question 2
Refer to the exhibit. The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)#switchport port-security
2950Switch(config-if)#switchport port-security mac-address sticky
2950Switch(config-if)#switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two)
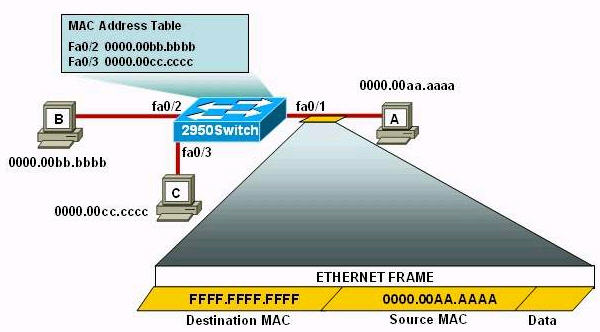
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. Only host A will be allowed to transmit frames on fa0/1.
C. This frame will be discarded when it is received by 2950Switch.
D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.
F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be forwarded out fa0/1.
Answer: B D
Explanation
Please read the explanation at http://www.9tut.net/icnd2/icnd2-operations
Question 3
Which Cisco Catalyst feature automatically disables the port in an operational PortFast upon receipt of a BPDU?
A. BackboneFast
B. UplinkFast
C. Root Guard
D. BPDU Guard
E. BPDU Filter
Answer: D
Explanation
We only enable PortFast feature on access ports (ports connected to end stations). But if someone does not know he can accidentally plug that port to another switch and a loop may occur when BPDUs are being transmitted and received on these ports.
With BPDU Guard, when a PortFast receives a BPDU, it will be shut down to prevent a loop -> D is correct.
Question 4
Why will a switch never learn a broadcast address?
A. Broadcast frames are never sent to switches.
B. Broadcast addresses use an incorrect format for the switching table.
C. A broadcast address will never be the source address of a frame.
D. Broadcasts only use network layer addressing.
E. A broadcast frame is never forwarded by a switch.
Answer: C
Question 5
Which three statements accurately describe layer 2 Ethernet switches? (choose three)
A. Microsegmentation decreases the number of collisions on the network.
B. If a switch receives a frame for an unknown destination, it uses ARP to resolve the address.
C. Spanning Tree Protocol allows switches to automatically share vlan information.
D. In a property functioning network with redundant switched paths, each switched segment will contain one root bridge with all its ports in the forwarding state. All other switches in that broadcast domain will have only one root port.
E. Establishing vlans increases the number of broadcast domains.
F. Switches that are configured with vlans make forwarding decisions based on both layer 2 and layer 3 address information.
Answer: A D E
Explanation
Microsegmentation is a network design (functionality) where each workstation or device on a network gets its own dedicated segment (collision domain) to the switch. Each network device gets the full bandwidth of the segment and does not have to share the segment with other devices. Microsegmentation reduces and can even eliminate collisions because each segment is its own collision domain -> A is correct.
Note: Microsegmentation decreases the number of collisions but it increases the number of collision domains.
D and E are correct based on the theory of STP and VLAN.
Question 6
Switch ports operating in which two roles will forward traffic according to the IEEE 802.1w standard? (Choose two)
A. alternate
B. backup
C. designated
D. disabled
E. root
Answer: C E
Explanation
IEEE 802.1w is the standard of Rapid Spanning Tree Protocol (RSTP). There are 5 port roles in this standard: Root port, Designated port, Alternative port, Backup port and Disabled port. In these 5 port roles, only Root port and Designated port can forward traffic.
Question 7
Select the action that results from executing these commands:
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security mac-address sticky
A. A dynamically learned MAC address is saved in the startup-configuration file.
B. A dynamically learned MAC address is saved in the running-configuration file.
C. A dynamically learned MAC address is saved in the VLAN database.
D. Statically configured MAC addresses are saved in the startup-configuration file if frames from that address are received.
E. Statically configured MAC addresses are saved in the running-configuration file if frames from that address are received.
Answer: B
Explanation
The full syntax of the second command is:
switchport port-security mac-address sticky [MAC]
If we don’t specify the MAC address (like in this question) then the switch will dynamically learn the attached MAC Address and place it into your running-configuration -> B is correct.
Question 8
What is valid reason for a switch to deny port access to new devices when port security is enabled?
A. The denied MAC addresses have already been learned or configured on another secure interface in the same VLAN.
B. The denied MAC address are statically configured on the port.
C. The minimum MAC threshold has been reached.
D. The absolute aging times for the denied MAC addresses have expired.
Answer: A
Explanation
A security violation occurs in either of these situations:
* When the maximum number of secure MAC addresses is reached on a secure port and the source MAC address of the ingress traffic is different from any of the identified secure MAC addresses, port security applies the configured violation mode.
* If traffic with a secure MAC address that is configured or learned on one secure port attempts to access another secure port in the same VLAN, applies the configured violation mode.
From the second statement we can figure out A is the correct answer. But for your information we will discuss other answers as well.
Answer B is not correct because we can’t configured which MAC address will be denied. We can only configure which MAC is allowed.
We can only configure the maximum MAC threshold, not the minimum threshold -> C is not correct.
The aging times are only configured for allowed MAC addresses, not for denied MAC -> D is correct.
For your information about aging time:
When the aging type is configured with the absolute keyword, all the dynamically learned secure addresses age out when the aging time expires
This is how to configure the secure MAC address aging type on the port:
Router(config-if)# switchport port-security aging type absolute
and configure the aging time (aging time = 120 minutes)
Router(config-if)# switchport port-security aging time 120
When this command is used, all the dynamically learned secure addresses age out when the aging time expires
(Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SX/configuration/guide/port_sec.html)
Question 9
A network administrator needs to configure port security on a switch. Which two statements are true? (Choose two)
A. The network administrator can apply port security to dynamic access ports
B. The network administrator can configure static secure or sticky secure mac addresses in the voice vlan.
C. The sticky learning feature allows the addition of dynamically learned addresses to the running configuration.
D. The network administrator can apply port security to EtherChannels.
E. When dynamic mac address learning is enabled on an interface, the switch can learn new addresses up to the maximum defined.
Answer: C E
Explanation
Follow these guidelines when configuring port security:
+ Port security can only be configured on static access ports, trunk ports, or 802.1Q tunnel ports.
+ A secure port cannot be a dynamic access port.
+ A secure port cannot be a destination port for Switched Port Analyzer (SPAN).
+ A secure port cannot belong to a Fast EtherChannel or Gigabit EtherChannel port group.
+ You cannot configure static secure or sticky secure MAC addresses on a voice VLAN.
+ When you enable port security on an interface that is also configured with a voice VLAN, you must set the maximum allowed secure addresses on the port to at least two.
+ If any type of port security is enabled on the access VLAN, dynamic port security is automatically enabled on the voice VLAN.
+ When a voice VLAN is configured on a secure port that is also configured as a sticky secure port, all addresses seen on the voice VLAN are learned as dynamic secure addresses, and all addresses seen on the access VLAN (to which the port belongs) are learned as sticky secure addresses.
+ The switch does not support port security aging of sticky secure MAC addresses.
+ The protect and restrict options cannot be simultaneously enabled on an interface.
Question 10
Refer to the exhibit. Which statement is true?
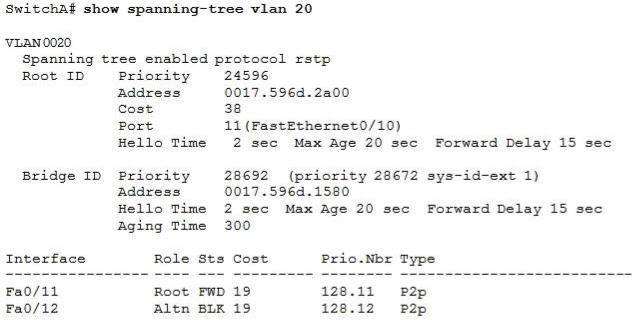
A. The Fa0/11 role confirms that SwitchA is the root bridge for VLAN 20.
B. VLAN 20 is running the Per VLAN Spanning Tree Protocol.
C. The MAC address of the root bridge is 0017.596d.1580.
D. SwitchA is not the root bridge, because not all of the interface roles are designated.
Answer: D
Explanation
Only non-root bridge can have root port. Fa0/11 is the root port so we can confirm this switch is not the root bridge -> A is not correct.
From the output we learn this switch is running Rapid STP, not PVST -> B is not correct.
0017.596d.1580 is the MAC address of this switch, not of the root bridge. The MAC address of the root bridge is 0017.596d.2a00 -> C is not correct.
All of the interface roles of the root bridge are designated. SwitchA has one Root port and 1 Alternative port so it is not the root bridge -> D is correct.
Question 11
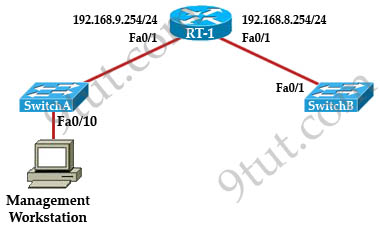
A technician has installed SwithchB and needs to configure it for remote access from the management workstation connected SwitchA. Which set of commands is required to accomplish this task?
A.
SwitchB(config)#interface FastEthernet 0/1
SwitchB(config)#ip address 192.168.8.252 255.255.255.0
SwitchB(config)#no shutdown
B.
SwitchB(config)#ip default-gateway 192.168.8.254
SwitchB(config)#interface vlan 1
SwitchB(config)#ip address 192.168.8.252 255.255.255.0
SwitchB(config)#no shutdown
C.
SwitchB(config)#interface vlan 1
SwitchB(config)#ip address 192.168.8.252 255.255.255.0
SwitchB(config)#ip default-gateway 192.168.8.254 255.255.255.0
SwitchB(config)#no shutdown
D.
SwitchB(config)#ip default-network 192.168.8.254
SwitchB(config)#interface vlan 1
SwitchB(config)#ip address 192.168.8.252 255.255.255.0
SwitchB(config)#no shutdown
Answer: B
Explanation
To remote access to SwitchB, it must have a management IP address on a VLAN on that switch. Traditionally, we often use VLAN 1 as the management VLAN (but in fact it is not secure).
In the exhibit, we can recognize that the Management Workstation is in a different subnet from the SwitchB. For intersubnetwork communication to occur, you must configure at least one default gateway. This default gateway is used to forward traffic originating from the switch only, not to forward traffic sent by devices connected to the switch.
Question 12
A network administrator wants to ensure that only the server can connect to port Fa0/1 on a Catalyst switch. The server is plugged into the switch Fa0/1 port and the network administrator is about to bring the server online. What can the administrator do to ensure that only the MAC address of the server is allowed by switch port Fa0/1? (Choose two)
A. Configure port Fa0/1 to accept connections only from the static IP address of the server.
B. Employ a proprietary connector type on Fa0/1 that is incompatible with other host connectors.
C. Configure the MAC address of the server as a static entry associated with port Fa0/1.
D. Bind the IP address of the server to its MAC address on the switch to prevent other hosts from spoofing the server IP address.
E. Configure port security on Fa0/1 to reject traffic with a source MAC address other than that of the server.
F. Configure an access list on the switch to deny server traffic from entering any port other than Fa0/1.
Answer: C E
Explanation
We can”configure the MAC address of the server as a static entry associated with port Fa0/1″ with this command:
Switch(config-if)#switchport port-security mac-address sticky 0000.00AA.AAAA.AAAA
and “configure port security on Fa0/1 to reject traffic with a source MAC address other than that of the server” with these commands:
Switch(config-if)#switchport port-security maximum 1 (only allow 1 MAC address and that is the static MAC address)
Also we often define what will the switch do if the security is violated:
Switch(config-if)#switchport port-security violation shutdown
Question 13
The network security policy requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy? (Choose two)
A. Switch1(config-if)#switchport port-security maximum 1
B. Switch1(config)#mac-address-table secure
C. Switch1(config)#access-list 10 permit ip host
D. Switch1(config-if)#switchport port-security violation shutdown
E. Switch1(config-if)#ip access-group 10
Answer: A D



Pls can somebody send me the latest dump, i have exam this month,
my email is asholet98@hotmail.com
Thanks
q3—– spanning tree — ensures loop free;; spanning tree allows network to include spare or redundant links;;;; BPDU –special data frame to exchange info about bridge id’s ;;
BPDU guard over Portfast is additional layer of protection –> will put port into error disable mode and admin will have to re-enable port
q2 and q4 — broadcast will never be source of address of a frame — q2 note that broadcast is destination — only source address is recorded
q5d— In a properly functioning network — not property
with redundant switched paths, each switched segment will contain 1 root bridge– all other switches will have 1 root port — this is important to know!!!! or to summarize this — each switched segment will contain 1 root bridge and other switches will have 1 root port
q5 — vlan trunking protocol or vtp — propagates the definition of vlan networks not spanning tree
q6— note the “w” is referring to rapid spanning tree — spanning tree is “d”—
q11— note the order of the commands — ip default gateway command is before going into interface vlan 1 — then the address is assigned
q12 d should be server not sewer
In reference to Q7
•You can configure MAC addresses to be sticky. These can be dynamically learned or manually configured, stored in the address table, and added to the running configuration. If these addresses are saved in the configuration file, the interface does not need to dynamically relearn them when the switch restarts. Although sticky secure addresses can be manually configured, it is not recommended.
You can configure an interface to convert the dynamic MAC addresses to sticky secure MAC addresses and to add them to the running configuration by enabling sticky learning. To enable sticky learning, enter the switchport port-security mac-address sticky command. When you enter this command, the interface converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky secure MAC addresses.
The sticky secure MAC addresses do not automatically become part of the configuration file, which is the startup configuration used each time the switch restarts. If you save the sticky secure MAC addresses in the configuration file, when the switch restarts, the interface does not need to relearn these addresses. If you do not save the configuration, they are lost.
If sticky learning is disabled, the sticky secure MAC addresses are converted to dynamic secure addresses and are removed from the running configuration.
After the maximum number of secure MAC addresses is configured, they are stored in an address table. To ensure that an attached device has the full bandwidth of the port, configure the MAC address of the attached device and set the maximum number of addresses to one, which is the default.
http://www.cisco.com/en/US/docs/switches/lan/catalyst4500/12.2/20ewa/configuration/guide/port_sec.html
@ jhd333 Q7 meaning if the configuration was saved. then it will b copied to the start-up configuration and even the switch is restarted the port will still b secure with for the same mac-address. in this case ans A should be the right ans. because the dynamic learned mac address will be save in the start-up configuraion. i think 9tut choose B because this commands not saved. hence running-config , if i am wrong can u please guide me. because i tasted on a packet trace
can somebody ans this question pls
A host is attempting to send data to another host on a different network. What is the first action that the
sending host will take?
A. Drop the data.
B. Send the data frames to the default gateway.
C. Create an ARP request to get a MAC address for the receiving host.
D. Send a TCP SYN and wait for the SYN ACK with the IP address of the receiving host.
i think the ans is B because the sending host will send the data to the default gateway. router will recieve the frame then use ARP to find the recieving host. but the dump says C.
Q11 is not correct, when write SwitchB(config)#interface vlan 1 , the prompt should be (config-if)#
Q-11 – B and D options are same..is it mistake?
@ sniffer
it’s B….
@9tut or anyone else, on question 8, section http://www.9tut.com/ccna-switch-questions.. on shekar dump says that the answer is B. the denied MAC address are statically configured on the port. and on your site its says the answer is A. Can you rectify what would be the correct answer based on your experience??? please, thank you
I think for Question 8 its not right on Shekar but is correct on 9tut. http://www.cisco.com/en/US/docs/switches/datacenter/sw/4_1/nx-os/security/configuration/guide/sec_portsec.html#wp1258122 it says “After a secure MAC address is configured or learned on one secure port, the sequence of events that occurs when port security detects that secure MAC address on a different port in the same VLAN is known as a MAC move violation” (I know thats Nexus but I think its the same because its port security technology being discussed.
Q-11 – B and D options are same..is it mistake? <– looks like it is.
Q11 is not correct, when write SwitchB(config)#interface vlan 1 , the prompt should be (config-if)# <– true but the correct answer is still valid because the question only asked for 'the set of commands' not the router prompts.
I'd assume it says config-if and not config to dispell any doubts :)
Question 5
Which three statements accurately describe layer 2 Ethernet switches? (choose three)
A. Microsegmentation decreases the number of collisions on the network.
B. If a switch receives a frame for an unknown destination.it uses ARP to resolve the address.
C. Spanning Tree Protocol allows switches to automatically share vlan information.
D. In a property functioning network with redundant switched paths, each switched segment will contain one root bridge with all its ports in the forwarding state. All other switches in that broadcast domain will have only one root port.
E. Establishing vlans increases the number of broadcast domains.
F. Switches that are configured with vlans make forwarding decisions based on both layer 2 and layer 3 address information.
Can anyone advise why “B. If a switch receives a frame for an unknown destination.it uses ARP to resolve the address” is not one of the correct options. I thought a switch would flood the broadcast domain (vlan) with an arp request, is this a wrong understanding I have?
can somebody ans this question pls
A host is attempting to send data to another host on a different network. What is the first action that the
sending host will take?
A. Drop the data.
B. Send the data frames to the default gateway.
C. Create an ARP request to get a MAC address for the receiving host.
D. Send a TCP SYN and wait for the SYN ACK with the IP address of the receiving host.
i think the ans is B because the sending host will send the data to the default gateway. router will recieve the frame then use ARP to find the recieving host. but the dump says C.
I think to answer this question like this. When a host is configured we add subnet mask with the IP address, armed with these two pieces of info (subnetmask and ip address) the host is able to work out the ip address its sending to is not on its own local network. It then sends to its default gateway (if one is configured) which will be in its own (host) arp table. Its this (default) router that would then un-encapsulate the frame because the frame destination address (mac/hardware address) would be its own and it will then pass to its newtwork layer. When the router looks at the destination ip address inside the ip header it sees its not its own ip address and realises it needs to be routed. The IP routing aspect kicks in and the packet is forwarded out across the various paths (hops) until it reaches the final (destination) router. This destination router will then see the destination ip address is directly connected to one of its own interfaces and it will look up its own arp table for the mac address or send out the frames. If one is not known it will arp request the data to populate its own table information. The arp request made by the original host will only hit the switch if its for its local network and not a remote network. Therefore regarding your query sniffer, its the default gateway that is the correct answer.
Q8…
Why A?
Please assist
@sniffer
Q.5, i think about ARP on switches to
switches not use ARP(only hosts), its very probably on ARP, but it known as flooding. if destinations unknown, then switch need to forward the packet to all ports (flooding)
Sorry, for my bad English =)
Answer: A D E – right
Hello guys, some that could help me with this question:
I have not seen next question here in 9tut.
A network administrator needs to allow only one telnet connection to a router. For anyone viewing the configuration and issuing the show run command, the password for telnet access should be encrypted. Which set of commands will accomplish this task?.
Summarizing, the most probable answers are just two:
1.
enable password secret
line vty0
login
password cisco
2.
service password-encryption
line vty1
login
password cisco
I understand 1 is not correct because of the first command, but I tried using vty1 (omitting the 1st line) and I can’t connect to it. It needs to have line vty0 configured in order to be able to access the router.
It skips 0 and 2 – 4 vty lines, so it does not allow to remote connect to router if at least vty 0 is not configured.
I had this question in my first try but asking what if ……. vty1 ……. was configured? and I answered it would allow only one remote connection, I think the way I found this question at the exam, I should have had answered no one could connect, am I right now?
This is the config I get when I do this:
!
line con 0
line vty 0
login
line vty 1
password cisco
loggin
line vty 2 4
login
!
Thanks
I forgot to say that testking answer is 1. Are they correct?
On no.:5, B is correct.
If a switch receives a frame for an unknown destination.it uses ARP to resolve the address.
@cesar
i had the same problem when i use the line vty 1 it does not connect through telnet. maybe the problem is ios?
friends, in case, if somebody fails ccna at first attempt, the re-exam will be after 5 days///
my question is ‘ do we have to pay the exam fee again for re-exam ?
thanks
hi,guyz any 1,with latest dumps plz,help me! mchomethegreat@gmail.com
hi, guys please mail me 64bit crack file for Virtual CertExam manager (VCE) at musabondera@gmail.com.Thank you in advance.
it is so easy
Its a piece of cake ;P
@ i wanna know
you should pay every time when you booked your exam.
Hi All,
Anyone have the latest dumps? can you email me on bluejeans_17@hotmail.com?
Thanks
@Anybody
@9tut
Whether can we use tab key to fill the full cmds??
Also can we use shortcut cmds in exam like we use in gns3 or packet tracer??
eg:sh run, sh ip int br, sh ip rout…
thanks.
passed ccna sec with 955/1000.p4s 4.38 valid.But remember don’t cram the qunitsoes as there are more options in the exam.Go through all the qunitsoes as multiple choice could come in as drag n drop or vice versa.I request careercert to add CCSP track too.thanx.
Can someone pls send me the latest dump to keitha999@yahoo.com?
TY 9tut.
Today I have passed the CCNA. (860/825)
50 questions 3 labs (VTP, EIGRP, ACL). 35 from 9tut.
Also thanks a lot Brar and Sekhar (still valid from examcollection)
Ty again 9tut
from here none
Hi I got my CCNA today… thankx 9tut..
Hi everyone. About Q5 -> why is answer E not correct ? thanks.
@9tut
I am going to give exam in next month,will these be valid for that time,plz confirm me
Thanks in advance
May somebody pls somebody explain to me the reason a switch has a base mac address?
hiya
Please if possible can someone send me the latest dump to sooo_per@hotmail.com
Highly Appreciable
Sana
can you explain question no. 9
failed my exam and will like to retake will I expect to see the same questions?
Valid Que :D
Q:5
Q:7
Q11: none are correct!!
choice (B) looks the most correct one but after putting int vlan 1 as showen below
SwitchB(config)#interface vlan 1
SwitchB(config)#ip address 192.168.8.252 255.255.255.0
SwitchB(config)#no shutdown
we still in global config mode not config-if mode to put the ip address! is this a typo or what?
Can someone pls send me the latest dump to rishidas2001@yahoo.com
BigGuy u dont need an interface for vlan management.
B is correct
I have read people saying that they read questions from 9tut(and i dont mean simulations) and they have passed.if that is so what is the use of the dumps then?can anyone help me with this?
ques no 4 was in my exam