Wireless Tutorial
Wireless Encoding
When a wireless device sends data, there are some ways to encode the radio signal including frequency, amplitude & phase.
Frequency Hopping Spread Spectrum(FHSS): uses all frequencies in the band, hopping to different ones after fixed time intervals. Of course the next frequency must be predetermined by the transmitter and receiver.
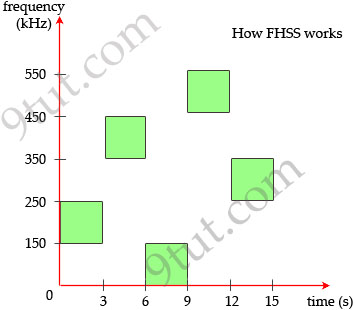
The main idea of this method is signals sent on different frequencies will be received at different levels of quality. By hopping to different frequencies, signals will be greatly improved the possibility that most of it will get through. For example, suppose there is another device using the 150-250 kHz range. If our device transmits in this range then the signals will be significantly interfered. By hopping at different frequencies, there is only a small interference while transmitting and it is acceptable.
Direct Sequence Spread Spectrum (DSSS): This method transmits the signal over a wider frequency band than required by multiplying the original user data with a pseudo random spreading code. The result is a wide-band signal which is very “durable” to noise. Even some bits in this signal are damaged during transmission, some statistical techniques can recover the original data without the need for retransmission.
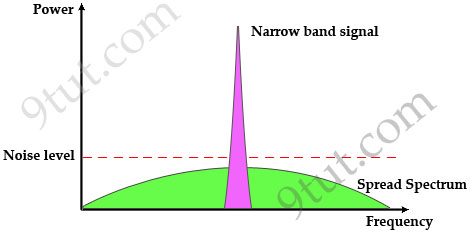
Note: Spread spectrum here means the bandwidth used to transfer data is much wider than the bandwidth needs to transfer that data.
Traditional communication systems use narrowband signal to transfer data because the required bandwidth is minimum but the signal must have high power to cope with noise. Spread Spectrum does the opposite way when transmitting the signal with much lower power level (can transmit below the noise level) but with much wider bandwidth. Even if the noise affects some parts of the signal, the receiver can easily recover the original data with some algorithms.
Now you understand the basic concept of DSSS. Let’s discuss about the use of DSS in the 2.4 GHz unlicensed band.
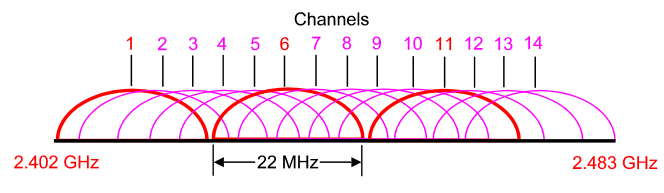
The 2.4 GHz band has a bandwidth of 82 MHz, with a range from 2.402 GHz to 2.483 GHz. In the USA, this band has 11 different overlapping DSSS channels while in some other countries it can have up to 14 channels. Channels 1, 6 and 11 have least interference with each other so they are preferred over other channels.
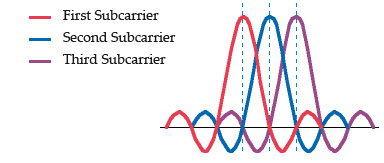
Orthogonal Division Multiplexing (OFDM): encodes a single transmission into multiple sub-carriers to save bandwidth. OFDM selects channels that overlap but do not interfere with each other by selecting the frequencies of the subcarriers so that at each subcarrier frequency, all other subcarriers do not contribute to overall waveform.
In the picture below, notice that only the peaks of each subcarrier carry data. At the peak of each of the subcarriers, the other two subcarriers have zero amplitude.
Below is a summary of the encoding classes which are used popularly in WLAN.
| Encoding | Used by |
| FHSS | The original 802.11 WLAN standards used FHSS, but the current standards (802.11a, 802.11b, and 802.11g) do not |
| DSSS | 802.11b |
| OFDM | 802.11a, 802.11g, 802.11n |
WLAN Security Standards
Security is one of the most concerns of people deploying a WLAN so we should grasp them.
Wired Equivalent Privacy (WEP)
WEP is the original security protocol defined in the 802.11b standard so it is very weak comparing to newer security protocols nowadays.
WEP is based on the RC4 encryption algorithm, with a secret key of 40 bits or 104 bits being combined with a 24-bit Initialisation Vector (IV) to encrypt the data (so sometimes you will hear “64-bit” or “128-bit” WEP key). But RC4 in WEP has been found to have weak keys and can be cracked easily within minutes so it is not popular nowadays.
The weak points of WEP is the IV is too small and the secret key is static (the same key is used for both encryption and decryption in the whole communication and never expires).
Wi-Fi Protected Access (WPA)
In 2003, the Wi-Fi Alliance developed WPA to address WEP’s weaknesses. Perhaps one of the most important improvements of WPA is the Temporal Key Integrity Protocol (TKIP) encryption, which changes the encryption key dynamically for each data transmission. While still utilizing RC4 encryption, TKIP utilizes a temporal encryption key that is regularly renewed, making it more difficult for a key to be stolen. In addition, data integrity was improved through the use of the more robust hashing mechanism, the Michael Message Integrity Check (MMIC).
In general, WPA still uses RC4 encryption which is considered an insecure algorithm so many people viewed WPA as a temporary solution for a new security standard to be released (WPA2).
Wi-Fi Protected Access 2 (WPA2)
In 2004, the Wi-Fi Alliance updated the WPA specification by replacing the RC4 encryption algorithm with Advanced Encryption Standard-Counter with CBC-MAC (AES-CCMP), calling the new standard WPA2. AES is much stronger than the RC4 encryption but it requires modern hardware.
| Standard | Key Distribution | Encryption |
| WEP | Static Pre-Shared | Weak |
| WPA | Dynamic | TKIP |
| WPA2 | Both (Static & Dynamic) | AES |
Wireless Interference
The 2.4 GHz & 5 GHz spectrum bands are unlicensed so many applications and devices operate on it, which cause interference. Below is a quick view of the devices operating in these bands:
+ Cordless phones: operate on 3 frequencies, 900 MHz, 2.4 GHz, and 5 GHz. As you can realize, 2.4 GHz and 5 GHz are the frequency bands of 802.11b/g and 802.11a wireless LANs.
Most of the cordless phones nowadays operate in 2.4 GHz band and they use frequency hopping spread spectrum (FHSS) technology. As explained above, FHSS uses all frequencies in the the entire 2.4 GHz spectrum while 802.11b/g uses DSSS which operates in about 1/3 of the 2.4 GHz band (1 channel) so the use of the cordless phones can cause significant interference to your WLAN.

An example of cordless phone
+ Bluetooth: same as cordless phone, Bluetooth devices also operate in the 2.4 GHz band with FHSS technology. Fortunately, Bluetooth does not cause as much trouble as cordless phone because it usually transfers data in a short time (for example you copy some files from your laptop to your cellphone via Bluetooth) within short range. Moreover, from version 1.2 Bluetooth defined the adaptive frequency hopping (AFH) algorithm. This algorithm allows Bluetooth devices to periodically listen and mark channels as good, bad, or unknown so it helps reduce the interference with our WLAN.
+ Microwaves (mostly from oven): do not transmit data but emit high RF power and heating energy. The magnetron tubes used in the microwave ovens radiate a continuous-wave-like at frequencies close to 2.45 GHz (the center burst frequency is around 2.45 – 2.46 GHz) so they can interfere with the WLAN.
+ Antenna: There are a number of 2.4 GHz antennas on the market today so they can interfere with your wireless network.
+ Metal materials or materials that conduct electricity deflect Wi-Fi signals and create blind spots in your coverage. Some of examples are metal siding and decorative metal plates.
+ Game controller, Digital Video Monitor, Wireless Video Camera, Wireless USB may also operate at 2.4 GHz and cause interference too.



thanx guys for the info but to those who need more shud Todd Lammle book 6th edition, has all the detail
hie
Pliz can some1 tell me if teleworkers are now in the ccna syllabus will be writing August monthed
9tut, A-W-E-S-O-M-E! Realy great. ;D
Thx so much.
Thanks for the info really usefull… Blessings!
thankzzzz for the information of wirless network
Can any1 send me , (danielagboh@yahoo.com) latest dump on 640-802. I wnt 2 write the exam in 2 weeks time.
@ 9tut
please upload tutorial on subnetting & vlsm
@9tut, pls upload 802.11n explanation.Thanks for about WLAN.
@darwin
hey, you can read everything you need about 802.11n here:
http://www.en.wikipedia.org/wiki/IEEE_802.11n-2009
good morning
@xallax…Thanks a lot for ur prompt reply.
what is initialization vector???
Hi, all .
When i config roaming , would I config more AP same SSID ?
@leethao
yes, but use different broadcast channel frequency numbers
nice explaination
Legeds live’s for ever!!!!
i need whole WAN tutorial please help me by sending email to arsadh007@yahoo.com
Hi,
I think there is a mistake here :
+ Listen to ensure the media is free. If it is free, set a random time before sending data
It should be : if it is NOT free, set a random time before sending data.
Thank you for this great website.
@CiscoMan: It is not a mistake, if the environment is free, it still waits a random time before sending data.
@CiscoMan: this further reduces the statistical probability of a collision. Silent -> random wait -> send
i am spellbound…what a precise , easy to understand tutorial…its simply too good:) 9tut…u rock!
dear sir
can i add the manual ip address in ad-hoc peer to peer connection
i think ad-hoc cannection supports nine wi-fi devices
Thanks! Its is a good stuff of wireless networking.
Hi 9tut.. in the explanation of 802.11 why don’t u add 802.11n? I need to know it’s difference than the other ones?
Thank You
I confused OFDM and searched it..found out that you forget to right Frequency.. u just write like this Orthogonal Division Multiplexing (OFDM)..
Thank You
same here.. im looking wheres F heh
nice explanation………..thanks a lot………….
Q6. 172.25.0.0 given. No mask or prefix given. 172 is a class be address with a classful mask of 255.255.0.0 prefix /16. This is only one subnet with range of 172.25.0.0 to 172.25.255.255 /16. We want eight subnets. 2 to the number of host bits borrowed equals the number of subnets gained. So we want 8 subnets. Borrow 3 hosts bit because 2^3 host bits borrowed equals 8 subnets gained from one subnet given. So borrowing 3 hosts bits, we move our classful /16 boundary 3 places to the right which would give us a new /19 prefix. There are 8 subnets gained and we want to know only what the 3rd subnet is and we have a ip subnet zero command configured which means that the first subnet is 172.25.0.0 to 172.25.31.255. The next subnet is 172.25.32.0 to 172.25.32.255. the third subnet is 172.25.64.0 to 172.95.255. Look at the ip address choices in the question and choose those that fit into the third subnet’s range. I hope this helps.
Sorry I made one mistake on Q6. the second subnet range is from 172.25.32.0 to 172.25.63.255.
gr8
@9tut
Now,as i understand from your words
roaming : must have same ssid but both AP must be on different frequencies
so my question is if both AP were on different frequencies so how can roaming happen ?
and if we used different frequencies like 1,6,11 …..so there is no overlapping and there is no roaming ? so why different frequencies
thanks
@jhon: They are in different frequencies. The device must get all necessary information about that AP, including frequency before “jumping” to another AP.
Thx so much.
Hello everybody!!!! Anyone that tell me, where download a study guide of CCNA_Wirless, please…
So, I’m passed CCNA 881 !!! last April 5th, 2013. If anyone need something else, and I help please send me a mail jcgt_83@hotmail.com
Thank you guys…See you soon
Hi 9tut if you have practice material of WAN like your EIGRP it is very educative with packet tracer. I want to practice WLAN in packet tracer but i have no idea how to practice WLAN with packet tracer, if you have some material kindly update.
dilsheramritsar@gmail.com
Thank you……
thanks a bunch!! this helped alot
G R E A T !!
Take a look at this site for a pdf tutorial – I am reading it over the next few days.
http://www.veriwave.com/pdf/07/80211_tutorial.pdf
Awesome lts easy but very comprehensive …….
where is the sec. parts of this tutorial?
Hello, I am writing in an unusual case … Some time ago, I used your services, and one of your employees face was familiar to me. At dinner with my wife, it turned out that he was a burglar, who 5 years ago broke into our home!!! This is ridiculous!!! How you can hire criminals? I found at least 3 bad entries for him at website for background check http://everifies.com !! I am sure there are more!!! Please do something about it, things like that are ridiculous!!!
hey,can I also get the vlsm tutorials on gmail
gachangocmbugua@gmail.com
I’ll appreciate.
Hey 9tut can you give me a server explaining web site.like this :)
Thank You
i never knew anything about networking. but your teachings have come with me this far. thanks very……………………….. much
thanks, for greater information about wlan
am a new student of wlan can some 1 mentol me oluwafemimichael206@yahoo.com and introduce me to any tutoria please
If it is free, set a random time before sending data
Should that read :
If it is NOT free, set a random time before sending data?
Please disregard previous comment – read respond to CiscoMan’s comment
Awesome