CCNA Access List Sim 2
Question
A network associate is adding security to the configuration of the Corp1 router. The user on host C should be able to use a web browser to access financial information from the Finance Web Server. No other hosts from the LAN nor the Core should be able to use a web browser to access this server. Since there are multiple resources for the corporation at this location including other resources on the Finance Web Server, all other traffic should be allowed.
The task is to create and apply a numbered access-list with no more than three statements that will allow ONLY host C web access to the Finance Web Server. No other hosts will have web access to the Finance Web Server. All other traffic is permitted.
Access to the router CLI can be gained by clicking on the appropriate host.
All passwords have been temporarily set to “cisco”.
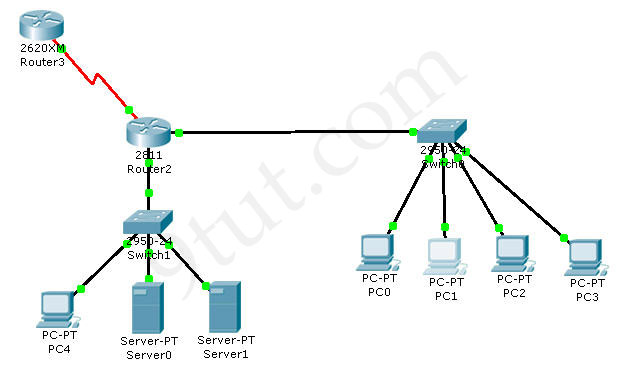
The Core connection uses an IP address of 198.18.196.65
The computers in the Hosts LAN have been assigned addresses of 192.168.33.1 – 192.168.33.254
Host A 192.168.33.1
Host B 192.168.33.2
Host C 192.168.33.3
Host D 192.168.33.4
The servers in the Server LAN have been assigned addresses of 172.22.242.17 – 172.22.242.30
The Finance Web Server is assigned an IP address of 172.22.242.23.
The Public Web Server is assigned an IP address of 172.22.242.17

Answer and Explanation
(Note: If you are not sure how to use access-list, please check out my access-list tutorial at: http://www.9tut.com/access-list-tutorial, also some modifications about the access-list have been reported so you should read the “Some modifications” section at the end of this question to understand more. You can also download this sim to practice (open with Packet Tracer) here: http://www.9tut.com/download/9tut.com_Access-list_sim2.pkt
Corp1>enable (you may enter “cisco” as it passwords here)
We should create an access-list and apply it to the interface which is connected to the Server LAN because it can filter out traffic from both Sw-2 and Core networks. The Server LAN network has been assigned addresses of 172.22.242.17 – 172.22.242.30 so we can guess the interface connected to them has an IP address of 172.22.242.30 (.30 is the number shown in the figure). Use the “show running-config” command to check which interface has the IP address of 172.22.242.30.
Corp1#show running-config

We learn that interface FastEthernet0/1 is the interface connected to Server LAN network. It is the interface we will apply our access-list (for outbound direction).
Corp1#configure terminal
Our access-list needs to allow host C – 192.168.33.3 to the Finance Web Server 172.22.242.23 via web (port 80)
Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Deny other hosts access to the Finance Web Server via web
Corp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80
All other traffic is permitted
Corp1(config)#access-list 100 permit ip any any
Apply this access-list to Fa0/1 interface (outbound direction)
Corp1(config)#interface fa0/1
Corp1(config-if)#ip access-group 100 out
Notice: We have to apply the access-list to Fa0/1 interface (not Fa0/0 interface) so that the access-list can filter traffic coming from both the LAN and the Core networks. If we apply access list to the inbound interface we can only filter traffic from the LAN network.
In the real exam, just click on host C and open its web browser. In the address box type http://172.22.242.23 to check if you are allowed to access Finance Web Server or not. If your configuration is correct then you can access it.
Click on other hosts (A, B and D) and check to make sure you can’t access Finance Web Server from these hosts.
Finally, save the configuration
Corp1(config-if)#end
Corp1#copy running-config startup-config
(This configuration only prevents hosts from accessing Finance Web Server via web but if this server supports other traffic – like FTP, SMTP… then other hosts can access it, too.)
Notice: In the real exam, you might be asked to allow other host (A, B or D) to access the Finance Web Server so please read the requirement carefully.
Some modifications:
Modification 1:
| permit host B from accessing finance server | access-list 100 permit ip host 192.168.33.2 host 172.22.242.23 |
| deny host B from accessing other servers (not the whole network) | access-list 100 deny ip host 192.168.33.2 172.22.242.16 0.0.0.15 |
| permit everything else | access-list 100 permit ip any any |
Modification 2:
| Only allow Host C to to access the financial server | access-list 100 permit ip host 192.168.33.3 host 172.22.242.23 |
| Not allow anyone else in any way communicate with the financial server | access-list 100 deny ip any host 172.22.242.23 |
| Allow all other traffic | access-list 100 permit ip any any |
Modification 3:
| - Host C should be able to use a web browser(HTTP)to access the Finance Web Server | access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80 |
| - Other types of access from host C to the Finance Web Server should be blocked - All access from hosts in the Core or local LAN to the Finance Web Server should be blocked |
access-list 100 deny ip any host 172.22.242.23 (because the requirement says we can not use more than 3 statements so we have to use “any” here for the hosts in the Core and hosts in local LAN) |
| - All hosts in the Core and local LAN should be able to access the Public Web Server * | access-list 100 permit ip any host (If the question asks this, surely it has to give you the IP of Public Web Server) but in the exam you should use “access-list 100 permit ip any any” |
Modification 4:
| Host C should be able to use a web browser to access the financial web server | access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80 |
| Other types of access from host C to the finance web server should be blocked | access-list 100 deny ip host 192.168.33.3 host 172.22.242.23 |
| All hosts in the core and on the local LAN should be able to access the Public web server * | access-list 100 permit ip any host (The IP of Public Web Server will surely be given in this question) but in the exam you should use “access-list 100 permit ip any any” |
* There are some reports about the command of “All hosts in the core and on the local LAN should be able to access the Public web server” saying that the correct command should be “access-list 100 permit ip any any”, not “access-list 100 permit ip any host (IP of Public Web Server)”. Although I believe the second command is better but maybe you should use the first command “access-list 100 permit ip any any” instead as some reports said they got 100% when using this command (even if the question gives you the IP address of Public Web Server). It is a bug in this sim.
(Note: Don’t forget to apply this access list to the suitable interface or you will lose points
interface fa0/1
ip access-group 100 out
And in the exam, they may slightly change the requirements, for example host A, host B instead of host C… so make sure you read the requirement carefully and use the access-list correctly)
I created this sim in Packet Tracer v5.2.1 so you can practice with it. You will need new version of Packet Tracer to open it (v5.1+).
Download this sim here
Notice: After typing the commands above, if you make a “ping” from other hosts (PC0, PC1, PC3) then PC4 (Finance Web Server) can still reply because we just filter HTTP traffic, not ICMP traffic. To generate HTTP traffic, select “Web Browser” in the “Desktop” tab of these PCs. When a web browser opens, type the IP address of Finance Web Server and you can see how traffic flows in Simulation Mode.

And notice that in the initial configuration of this sim the Core network can ping Finance Web Server. We have to create an access-list that can filter this traffic too.
Other lab-sims on this site:



All posted configurations work well on PT 5.3.3.0019
No Problem Mike. Here it is:
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Switch(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80
Switch(config)#access-list 100 permit ip any any
Switch(config)#interface fa0/1
Switch(config-if)#ip access-group 100 out
^
% Invalid input detected at ‘^’ marker.
@anon
Why would you do it on a switch?
I am such an idiot. Thanks Mike. DUH!!!!!
One more question Mike. I ran the following commands and can STILL ping the finance server from all hosts. Shouldnt the following commands only allow Host C access to the finance server when pinged?
Please advise.
Thanks
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.30 eq 80
Router(config)#access-list 100 deny tcp any host 172.22.242.30 eq 80
Router(config)#access-list 100 permit ip any any
Router(config)#interface fa0/1
Router(config-if)#ip access-group 100 out
Router(config-if)#end
Router#
%SYS-5-CONFIG_I: Configured from console by console
Router#copy running-config startup-config
Destination filename [startup-config]? startup-config
Building configuration…
[OK]
It looks like it works when using a web browser Mike, just not a ping from each user station.
Is it because I am configured to access / deny via HTTP vs ICMP?
@anon
You denied only tcp port 80. So only specific hosts will be denied on port 80, everything else is permitted. even both HTTP and ICMP using TCP.
So that leads me back to my original question Mike. Is the only way to check this set of commands is to check the WEB Browser of each host ONLY?
Additionally is this the way it will be on the test as well? If its different can you tell me what other configurations people are seeing on the test that they have to setup for this particular question? IE Browser only to verify, CLI to verify,ect.
Thanks for all your help Mike.
That’s my router’s config.: I hope that you can help me. I’m running PT on Ubuntu
Router#sh run
Building configuration…
Current configuration : 1050 bytes
version 12.4
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
hostname Router
ip name-server 0.0.0.0
spanning-tree mode pvst
interface FastEthernet0/0
ip address 192.168.33.254 255.255.255.0
duplex auto
speed auto
interface FastEthernet0/1
ip address 172.22.242.30 255.255.255.240
ip access-group 100 out
duplex auto
speed auto
interface Serial1/0
ip address 198.18.196.66 255.255.255.0
interface Serial1/1
no ip address
shutdown
interface Serial1/2
no ip address
shutdown
interface Serial1/3
no ip address
shutdown
interface Vlan1
no ip address
shutdown
router rip
network 172.22.0.0
network 192.168.33.0
network 198.18.196.0
ip classless
access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq www
access-list 100 deny tcp any host 172.22.252.23 eq www
access-list 100 permit ip any any
access-list 100 deny tcp any host 172.22.242.23 eq www
line con 0
line vty 0 4
login
end
Router#
@eric
You have wrong ACL, means last line will never be considered. Watch Train Signal or CBT Nuggets, my advice. After you can start to understand the rules of ACL. Don’t get me wrong, but I cannot to explaine you all theory here.
anyone who take exam last day? is this simulation still used in CCNA Exam? I prepare for my exam on 3rd october..
Thanks!
hello everybody , i passed my CCNA exam this morning with 973/1000 ; i am very happy …and an advise for those are preparing their exam: cbtnuggets videos,9tut (almost all questions on this website where there, they just change IP addresses or host) and also do the dump of Sekhar with 697 questions….Good luck…..
now i am seeing how i can go to Koenig for my CCNP training ……any advise?
Guys, I need your helps.
For acl questions :
permit host B from accessing finance server
deny host B from accessing the OTHER server (not the whole network)
permit everything else
can I do :
access-list 100 permit ip host 192.168.33.2 host 172.22.242.23
access-list 100 deny ip host 192.168.33.2 host 172.22.242.17
access-list 100 permit ip any any
rather than (this is the exact answer from 9tut) :
access-list 100 permit ip host 192.168.33.2 host 172.22.242.23
access-list 100 deny ip host 192.168.33.2 172.22.242.16 0.0.0.15
permit ip any any
The difference is just on the 2nd acl syntax, since the question wanted deny host B to other server (not the whole network) & the other server is just only 172.22.242.17, so i just deny 172.22.242.17 :) correct or not ?
Merci Bouku..
Which of the dumps is the best and latest
hey guys, i was able to make it work in packet tracer 5.3.3
here is my config (extracted from the sh run)
access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq www
access-list 100 deny tcp any host 172.22.242.33 eq www
access-list 100 permit tcp any any
( i wrote eq 80, but in the sh run its showing www)
interface FastEthernet0/1
ip access-group 100 out
copy running-config startup-config
At the begining it was not working, i was able to enter 172.22.242.23 in the web browser for all the pc’s and the page came up, but it was actually a packet tracer issue, so i saved it, closed PT and re-open it. once the whole network was converged, i tried 172.22.242.23 in the browser for the pc’s and only host C was able to get the web page.
@ezuedeen
I have the same problem.
Hey guys plz answer his question.
For acl questions :
permit host B from accessing finance server
deny host B from accessing the OTHER server (not the whole network)
permit everything else
can I do :
access-list 100 permit ip host 192.168.33.2 host 172.22.242.23
access-list 100 deny ip host 192.168.33.2 host 172.22.242.17
access-list 100 permit ip any any
rather than (this is the exact answer from 9tut) :
access-list 100 permit ip host 192.168.33.2 host 172.22.242.23
access-list 100 deny ip host 192.168.33.2 172.22.242.16 0.0.0.15
permit ip any any
The difference is just on the 2nd acl syntax, since the question wanted deny host B to other server (not the whole network) & the other server is just only 172.22.242.17, so i just deny 172.22.242.17 :) correct or not ?
Pls im still asking, which dumps is the best and latest. How long can dumps stay befor it expires.
Go to exam collection. Download latest dumps with high ratings.
Have a question. In the actual exam, would we have to erase the 1st. access list when the 2nd. is applied?, and so for the rest of the acl’s?. Because what i can see is that 1st. access list would interfere with the 2nd.
If we have to erase it in order to get the right results out of the 2nd., by the time to save run into startup-config wouldn’t be wrong the hole lab?, since only the last acl would apply to filter the traffic.
Ceaser,
No in exam you don’t have to earse any ACL 9tuts example is what the exam will look like.
Thanks Anonymous. It has been mentioned here a lot of times that 9tut’s ACL2 lab is 1 of the 3 labs that comes into actual exam. So I thought the exam would come with the same quantity of acl’s to resolve.
I had not taken the exam before, next friday will be my first ccna try, and I am studying like a crazy all day and almost all night from 9tut, material I got from the course, and also from testking virtual server then people from the course gave to me. Someony told me to study acl’s a lot, it is suppose that there would be a lot of questions on that.
Any advise would be appreciate it.
I had this question with some changes
host C can only use web browser to reach finance server
All other types of access is prevented from host C
All other host shouldn’t have any access to finance web server
All other traffic is permitted
I got 100% in the ACL according to the score sheet.I did the following in the exam
permit tcp [host c ip]host [finance ip] eq 80
deny ip any [finance ip]
permit ip any any
taking the test soon! I have a feeling I will get EIGRP, VTP and ACL… Bring it on!I hope to get frame relay though, that’s so easy.
I just took the test and I got the VTP, ACL2, and EIGRP. The ACL2 was different that posted. They asked me to allow a host to access the web server and to DENY all other traffic to the server from all the hosts. Here is the answer
access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
access-list 100 deny ip any host 172.22.242.23
access-list 100 permit ip any any
The EIGRP sim was exactly as described, there was a passive interface, but it was to the ISP and does not need to be removed. After fixing the EIGRP statement, I did not see an adjaceny statement, I had to add the network to the main router. Make sure you do a “show ip eigrp neighbors” command and see all the networks on the main router and the new router, just to make sure.
Hi,
I have been trying to download the accesslist Sim 2 and run it on Packet tracer but the simulation does not work on Packet tracer. Is any one facing the same problem. Same is the case with VTP sim (VTP sim says “file invalid”). The EIGRP seems to be working fine. Does any one have any suggestions. Please share. I have my exam on Wednesday, October 3rd.
Thank you.
@four pls explain how to go about adding the network to the main router
Hi Took the exam yesterday, used the access-list as shown (different IP Addresses) but would not allow me to put in the host address of host C, it kept flagging as a mistake, i have complained to the testing centre and just waiting to see if this was a fault with the simulator or information given in question.
Looking for resit of exam as time spent trying to work out what was wrong (Nothing wrong) meant i ran out of time… the EIGRP simulation was in exam and as per shown :)
taking the exam on friday for the first time what can i expect/
taking the exam on friday for the first time what can i expect?
– Host B should be able to use a web browser(HTTP)to access the Finance Web Server
– Other types of access from host B to the Finance Web Server should be blocked
– All access from hosts in the Core or local LAN to the Finance Web Server should be blocked
– All hosts in the Core and local LAN should be able to access the Public Web Server
How to configure this task ?
Core1(config)#access-list 100 permit tcp host 192.168.33.2 host 172.22.242.23 eq 80
Core1(config)#access-list 100 deny ip any host 172.22.242.23
Core1(config)#access-list 100 permit ip any host 172.22.242.17
Should I apply this ACL ip access-list 100 out with fa0/0 or fa0/1?
Core1(config)#access-list 100 permit tcp host 192.168.33.2 host 172.22.242.23 eq 80
Core1(config)#access-list 100 deny ip any host 172.22.242.23
Core1(config)#access-list 100 permit ip any host 172.22.242.17
Core1(config)#int f0/1
Core1(config-if)#ip access-group 100 out
Core1(config-if)#end
Core1#copy running-config startup-config
acess-list 100 permit tcp hostbxxxx hostF.server eq 80
access-list 100 deny ip any hostbxxxx
access-list 100 permit ip any any
Extended IP access list 105
permit tcp host 192.168.33.3 host 172.22.242.23 eq www
deny ip any host 172.22.242.23
permit tcp any host 172.22.242.22 eq www
line 1 : allows host X to access finance web server
line 2 : denies all other type of traffic to web server
line 3 : allows other hosts to access the other web server
Hi Anonymous , I still don’t understand the question is “–All hosts in the Core and local LAN should be able to access the Public Web Server ” .why did you configure with “access-list 100 permit ip any any” ? ,can you explain me more clearly about this question?
Thanks!
Hi all,
I took the exam today. I passed!
Thank you 9tut!!!!!
Sims were VTP, EIGRP, ACL 2…
be careful guys, though most of the dumps questions were present,
there were some differences and different patterns of asking the same questions.
Study the material
Get the concept
Familiar with dumps (Mr bean and Sekhar dumps were accurate! my only two dumps)
Apply them in the real exam!
Good luck guys!
Questions are easy but you should pay more attention to what answers you should provide cuz with CCNA things are always what it seems!
Hi guys,
Is the (access-list number) given in the actual exam? I mean, how do we know on what access-list number to use? I’m confuse cause someone uses 100 and the other 101.
plzz help.
thanks.
@jcalzzz
It is an Numbered EXTENDED ACL so it can be any number in the range 100-199 or 2000-2699
For Numbered STANDARD ACLs use statements in the range 1-99 or 1300-1999
Regards
@Román
thanks. :D
Cheers 9tut, passed with 920 today.
hi dabears, am sitting for the exam tomorrow are dumps valid?
@@Jaymo
A Question paper…. ;) :P
can some one send me the lastst dump? i m goin to write this morning
sopprosbarbosa@hotmail.com
Hi guys. Wrote ccna this am. Sims vtp eigrp modified , acl similiar with different hosts. Thanks 9tut and everyone for all the assistance.
Guys,
I need explanation from 9tut which has been highlighted under “Some modifications :”. I still can’s understand the answered explained here.
The example from 9tut said :
Questions :
permit host B from accessing finance server
deny host B from accessing the OTHER server (not the whole network)
permit everything else
Answer :
access-list 100 permit ip host 192.168.33.2 host 172.22.242.23
access-list 100 deny ip host 192.168.33.2 172.22.242.16 0.0.0.15
permit ip any any
Why did 9tut put while card mask for the 2nd acl syntax ?
access-list 100 deny ip host 192.168.33.2 172.22.242.16 0.0.0.15
as if you configure like that, you shall block the whole network (all the server shall not be accessible) by 9tut put the remarks (not the whole network)..
Could someone explain to me.. :(
thanks
why not?
in fa 0/0
ip access-group 100 in
Читай внимательно:
Notice: We have to apply the access-list to Fa0/1 interface (not Fa0/0 interface) so that the access-list can filter traffic coming from both the LAN and the Core networks. If we apply access list to the inbound interface we can only filter traffic from the LAN network.
https://rapidshare.com/files/1052466536/ACCESS LIST SIM2.pkt
just done, all working with Cisco Packet Tracer Version: 5.2.1.0006
https://rapidshare.com/#!download|277p2|1052466536|ACCESS%20LIST%20SIM2.pkt|17|0|0
ezuedeen
not really sure about this one, this is what I understand.
The Sim say this:
“The servers in the Server LAN have been assigned addresses of 172.22.242.17 – 172.22.242.30″
knowing this you can figure out the network is 172.22.242.16 to 172.22.242.31 (Broadcast)
the mask would be 255.255.255.240 for this network.
As you said using this mask 0.0.0.15 we will block the whole network. but don’t forget there is an statement before saying, “Allow host B to the financial Server”
With the first Statement you allow Host B to access the Finance Server. if host B want to access another server it will be blocked.
Also if another host, let say A, want to access the public or DNS server, they will be allow, because the first and second statement applied only to host B, and the Third statement applies to any other host (including B as well) and that statement is “permit ip any any”