Access List Tutorial
In this tutorial we will learn about access list.
Access control lists (ACLs) provide a means to filter packets by allowing a user to permit or deny IP packets from crossing specified interfaces. Just imagine you come to a fair and see the guardian checking tickets. He only allows people with suitable tickets to enter. Well, an access list’s function is same as that guardian.
Access lists filter network traffic by controlling whether packets are forwarded or blocked at the router’s interfaces based on the criteria you specified within the access list.
To use ACLs, the system administrator must first configure ACLs and then apply them to specific interfaces. There are 3 popular types of ACL: Standard, Extended and Named ACLs.
Standard IP Access List
Standard IP lists (1-99) only check source addresses of all IP packets.
Configuration Syntax
| access-list access-list-number {permit | deny} source {source-mask} |
Apply ACL to an interface
| ip access-group access-list-number {in | out} |
Example of Standard IP Access List
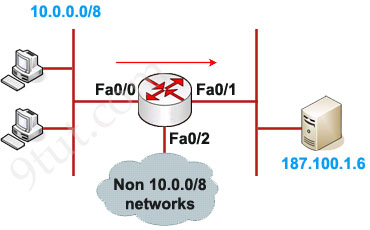
Configuration:
In this example we will define a standard access list that will only allow network 10.0.0.0/8 to access the server (located on the Fa0/1 interface)
Define which source is allowed to pass:
Router(config)#access-list 1 permit 10.0.0.0 0.255.255.255
(there is always an implicit deny all other traffic at the end of each ACL so we don’t need to define forbidden traffic)
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 1 out
The ACL 1 is applied to permit only packets from 10.0.0.0/8 to go out of Fa0/1 interface while deny all other traffic. So can we apply this ACL to other interface, Fa0/2 for example? Well we can but shouldn’t do it because users can access to the server from other interface (s0 interface, for example). So we can understand why an standard access list should be applied close to the destination.
Note: The “0.255.255.255″ is the wildcard mask part of network “10.0.0.0″. We will learn how to use wildcard mask later.
Extended IP Access List
Extended IP lists (100-199) check both source and destination addresses, specific UDP/TCP/IP protocols, and destination ports.
Configuration Syntax
| access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port] |
Example of Extended IP Access List
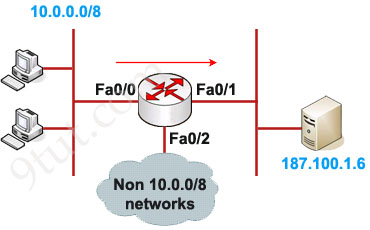
In this example we will create an extended ACL that will deny FTP traffic from network 10.0.0.0/8 but allow other traffic to go through.
Note: FTP uses TCP on port 20 & 21.
Define which protocol, source, destination and port are denied:
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 21
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 20
Router(config)#access-list 101 permit ip any any
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 101 out
Notice that we have to explicit allow other traffic (access-list 101 permit ip any any) as there is an “deny all” command at the end of each ACL.
As we can see, the destination of above access list is “187.100.1.6 0.0.0.0″ which specifies a host. We can use “host 187.100.1.6″ instead. We will discuss wildcard mask later.
In summary, below is the range of standard and extended access list
| Access list type | Range |
| Standard | 1-99, 1300-1999 |
| Extended | 100-199, 2000-2699 |



Anyone please can I get a clear explanation on access-list more especially the question that was in Thursday exam please please send me some dumps on ramabolu@hotmail.com
I believe this also may be stopped at the inbound interface Fa0/1 to avoid the router to process unnecessary denied traffic.
@ Amir: this is how 2 understand the “in/out” concept: See ur router as the reference point, and then let IN mean – “INto the router through this port you are Applying the ACL on and Let OUT mean of the router through the port you are applying the ACL, I hope you get that now Amir?
I am writing the CCNA on 31st Dec, anyone with latest dumps please email me on moses_og@hotmail.com
@amir this is like a single gate and two gatekeeper one is out side of gate and one is inside of gate inside ppl must have permit from gatekeeper to go out side, and out side ppl must have permit to come in side
I didn’t quite anderstand something. If extended IP access lists should be placed close to the source, why this ACL was placed in interface f0/1 out, but didn’t placed in int f0/0 in (ex. extended ACL)?
@serge: It depends on your purpose, you don’t need to follow that rule.
An organization is concerned that too many employees are wasting company time accessing the Internet. Which access list statement would stop World Wide Web access for employees on the range of subnets from 172.16.8.0/24 to 172.16.11.0/24?
A. access-list 103 deny tcp 172.16.8.0 0.0.0.3 any eq 80
B. access-list 103 deny tcp 172.16.8.0 0.0.3.255 any eq 80
C. access-list 103 deny http 172.16.8.0 0.0.7.255 any
D. access-list 103 deny tcp any 172.16.8.0 0.0.3.255 eq 80
E. access-list 103 deny tcp 172.16.8.0 0.0.11.255 any eq 80
The answer is B.
Can someone explain me why? Thanks in advance.
Avp,
You are trying to match 4 networks 172.16.8-11.0/24 because these networks are in the thrid oct”0.0.3.255″ is correct. You have to count how many networks are needed to be satisfied in the statement in this case 4. So all that is needed is to count the bits required to cover the networks:
1 bit would cover 2
2 bits would cover 4 so, thats is what we need, 2 bits, in the thrid oct to satisfy the requirements.
Here is a standard subnet mask that would fufill the requirement:
11111111.11111111.11111100.00000000 = 255.255.254.0 (notice I have taken 2 bits in the third oct and turned them into 0)
Because this requires a wildcard mask we must invert the statement for the correct syntax.
00000000.00000000.00000011.11111111=0.0.3.255
128 64 32 16 8 4 2 1( remember the value of the bits and look below at the bits that are
You are trying to match 4 networks 172.16.8-11.0/24 because these networks are in the thrid oct”0.0.3.255″ is correct. You have to count how many networks are needed to be satisfied in the statement in this case 4. So all that is needed is to count the bits required to cover the networks:
1 bit would cover 2
2 bits would cover 4 so, thats is what we need, 2 bits, in the thrid oct to satisfy the requirements.
Here is a standard subnet mask that would fufill the requirement:
11111111.11111111.11111100.00000000 = 255.255.254.0 (notice I have taken 2 bits in the third oct and turned them into 0)
Because this requires a wildcard mask we must invert the statement for the correct syntax.
00000000.00000000.00000011.11111111=0.0.3.255
128 64 32 16 8 4 2 1( remember the value of the bits and look below at the bits that are “one” in the 3rd oct if you add them up in binary the VALUE IS 3!!!!)
So this means that just the first 22 bits match so just inverting the mask you can see with ease the value of the wildcard in binary
Another way to convert it is to simply subtract
255.255.255.255
– 255.255.252.255
= 0. 0. 3.255
so in fact this would satisfy the requirement:
172.16.8.0/24
172.16.9.0/24
172.16.10.0/24
172.16.11.0/24
Sorry make a mistake on the first binary line:
11111111.11111111.11111100.00000000=255.255.252.0 (NOT 254.0 )
I plan to take the CCNA later this month but the more i study (and this is not my career field but i need it anyway) the less i think I know. may have to opt for the two part test…. been at it for months and still can’t pass a single practice test yet!
jeauslover….thanks for explain …it s cleared my wcm doubts…and what area is should be inbound & outbound interface……i have confused….
it s inside n/w or outside n/w…..???
wla mn lng………………………………………………….
In example of extended ACL, why did you apply this ACL on interface FA0/1 outbound, i think, it can be better, when you place it on FA0/0 inbound .. please explain me this
@Xtrikerpd
you r right, placing the extended acl on fa0/0 would be still better than on fa0/1, but this applies only for denying the packets from 10.0.0.0 network. If you place the acl on fa0/1 ie at termiating path. you can allow or deny packets from any networks even other than 10.0.0.0 in the future.
I’m not in 100% sure but in my opinion there is mistake on extended access list and apply this ACL to the router intefrace. From definition extended ACL is the clothest to the source. So there should be:
Apply this ACL to an interface:
Router(config)#interface Fa0/0
Router(config-if)#ip access-group 101 in
Please tell am I right. Tommorow I’m passing my CCNA.
But in the other hand if there is only one router it does not matter. Don’t you think so?
My explanation is more effective in wide network there is much more routers.
mjahanzaib@hotmail.com please forword me latest dumps .thanks in advance
Very useful. pretty gud to gather easily…
What is a dynamic access list?
plz i didn’t understand that access-list 101 permit ip any any
can somone explaine that plz..
Alternative way of handling this question which I believe is slightly more obvious where the wildcard mask of 0.0.3.255 comes from, is to take a look into these 4 subnets and try to find a summery address representing all 4 as close as possible.
Remember IP address are in class B thus quadrent of interest is the 3.
172.16.8.0 == 172.16.00001000.0
172.16.9.0 == 172.16.00001001.0
172.16.10.0 ==172.16.00001010.0
172.16.11.0 ==172.16.00001011.0
As you can see above these 4 IP address can be summerized to 172.16.8.0/22
Now /22 is 255.255.252.0
The wildcardmask for this 0.0.3.255
Pls help, I don’t seem to understand the range for the example provided below. If the wildcard mask is 0.0.15.255 for 172.23.16.0 what range of IP addresses it includes
Thanks,
hello guys I’ve just done this example on packet tracer . when I did the Standard access one it worked fin but when i did the extended one it wont work i still can ping the network 187.100.1.6 . any help please thank you in advance
zala93@yahoo.com
Pls help, im having a tough time grasping a particular area in extended ACL. From the 3rd edition of wendell odom’s book there’s a particular question i understand but the answer confuses me.
It asks me to to create a one line extended acl that matches the below:
(Permit) ICMP messages from the subnet in which 192.168.7.200/26 resides to all hosts in the subnet where 192.168.7.14/29 resides.
Now initially i thought the answer was:
access-list 103 permit icmp 192.168.7.200 0.0.0.63 192.168.7.0 0.0.07
However this is wrong. the book says the answer is:
access-list 103 permit icmp 192.168.7.192 0.0.0.63 192.168.7.8 0.0.07 Can someone please explain to me how they got .192 and.8 in the final octects for each please?!??!?!?
I am writing the CCNA on 15th march, anyone with latest dumps please email me on
spy_mrigen@yahoo.co.in
@Nas You need to review subnetting mate.
192.168.7.200/26 with the last octet in binary is:
192.168.7.11001000
255.255.255.11000000 (mask)
Meaning obviously that the network is 192.168.7.11000000 or 192.168.7.192, the last 6 bits of the last octet are according to the mask host bits.
Same for 192.168.7.14/29, 14 in binary is 00001110 and according to the mask the 3 last bits are host bits leaving therefore the 00001000 as the network 192.168.7.8/29
Thanks alot E.T. i understand what your saying and i now understand how the answer is .192 and .07 in the final octets for each. Really appreciate your help. Finally i can move on to the next chapter. Cheers
Glad that helped :) Btw if you intend to take the CCNA instead of the ICDNs fast subnet calculations are very important when it comes to saving time
I am writing the CCNA on 15th April , anyone with latest dumps please email me on punkmanish11@gmail.com
Can someone please email me the latest dumps @ wiredup@nf.sympatico.ca
Thank you
please help.what is eq 80
Confused about access list numbers. I know that 1-99 is for standard access list, but how do you determine what number to use in that range when creating an access list. For instance 1, 10 or even 99?
Hi 9tut according to me in your example wildcard mask you mentioned the 00010011=18
but should it not be 00010011=19
@jbctwin1: You can use any number from 1 to 99 for standard acl. That means you can have 99 access-lists.
@Dilsher: Please tell me where do you find the 00010011?
@9tut: Got it! Thank you!
i will do exam at the end of this month, any one with update dump please email to me via, kiruisml@yahoo.com.
i need the last ccna dump
I am passing my ccna next week ,somebdy please email me the latest dumps at
ritsmagical123@gmail.com
of all the topics in CCNA I am scared of ACL’s and there are so many things to remember out here, the real confusion is on the protocols and their port numbers…
i need the last ccna dump
can someone tell me how do you know when to use TCP vs IP?
hi everybody
I will have my exam next week. can someone send me the latest dumps please? here is my e-mail vinhhoidv09@gmail.com
Thanks
can anyone xplain me in_to_out fanda????????
ok i got it.,.its the name of the access-list.,.,.
When are you correcting /28 9tut? :)
@Trainer: Please tell us where is the mistake?
i think what trainer is talking about is that under wildcard section, the IP in the example is 172.23.16.0/28. but the wildcard is for /20: 0.0.15.255.
for /28, it would be 0.0.0.15, wouldn’t it? nice explanation by the way :)
hi guys..
whats the passmark of ccna now?