Access List Tutorial
In this tutorial we will learn about access list.
Access control lists (ACLs) provide a means to filter packets by allowing a user to permit or deny IP packets from crossing specified interfaces. Just imagine you come to a fair and see the guardian checking tickets. He only allows people with suitable tickets to enter. Well, an access list’s function is same as that guardian.
Access lists filter network traffic by controlling whether packets are forwarded or blocked at the router’s interfaces based on the criteria you specified within the access list.
To use ACLs, the system administrator must first configure ACLs and then apply them to specific interfaces. There are 3 popular types of ACL: Standard, Extended and Named ACLs.
Standard IP Access List
Standard IP lists (1-99) only check source addresses of all IP packets.
Configuration Syntax
| access-list access-list-number {permit | deny} source {source-mask} |
Apply ACL to an interface
| ip access-group access-list-number {in | out} |
Example of Standard IP Access List
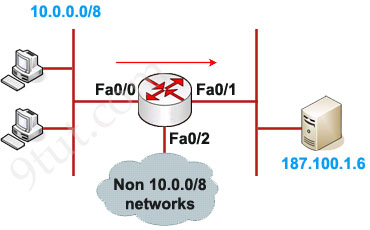
Configuration:
In this example we will define a standard access list that will only allow network 10.0.0.0/8 to access the server (located on the Fa0/1 interface)
Define which source is allowed to pass:
Router(config)#access-list 1 permit 10.0.0.0 0.255.255.255
(there is always an implicit deny all other traffic at the end of each ACL so we don’t need to define forbidden traffic)
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 1 out
The ACL 1 is applied to permit only packets from 10.0.0.0/8 to go out of Fa0/1 interface while deny all other traffic. So can we apply this ACL to other interface, Fa0/2 for example? Well we can but shouldn’t do it because users can access to the server from other interface (s0 interface, for example). So we can understand why an standard access list should be applied close to the destination.
Note: The “0.255.255.255″ is the wildcard mask part of network “10.0.0.0″. We will learn how to use wildcard mask later.
Extended IP Access List
Extended IP lists (100-199) check both source and destination addresses, specific UDP/TCP/IP protocols, and destination ports.
Configuration Syntax
| access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port] |
Example of Extended IP Access List
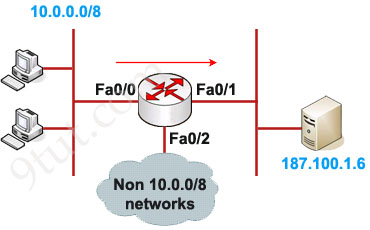
In this example we will create an extended ACL that will deny FTP traffic from network 10.0.0.0/8 but allow other traffic to go through.
Note: FTP uses TCP on port 20 & 21.
Define which protocol, source, destination and port are denied:
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 21
Router(config)#access-list 101 deny tcp 10.0.0.0 0.255.255.255 187.100.1.6 0.0.0.0 eq 20
Router(config)#access-list 101 permit ip any any
Apply this ACL to an interface:
Router(config)#interface Fa0/1
Router(config-if)#ip access-group 101 out
Notice that we have to explicit allow other traffic (access-list 101 permit ip any any) as there is an “deny all” command at the end of each ACL.
As we can see, the destination of above access list is “187.100.1.6 0.0.0.0″ which specifies a host. We can use “host 187.100.1.6″ instead. We will discuss wildcard mask later.
In summary, below is the range of standard and extended access list
| Access list type | Range |
| Standard | 1-99, 1300-1999 |
| Extended | 100-199, 2000-2699 |



About the graphics extended ACL example, why is it ACL is applied at “port f0/1 out”? why not at the “port f0/0 in”?
As far as i know, in standard ACL, the ACL should be applied close to the destination and in extended ACL, be applied close from the source.
I think, because we have two interfaces for input traffic (from f0/0 and from f0/2) and one interface for output traffic (f0/1) and we use only one access list to manage both
That makes since Larissa
About the graphics extended ACL example, why is it ACL is applied at “port f0/1 out”? why not at the “port f0/0 in”?
As far as i know, in standard ACL, the ACL should be applied close to the destination and in extended ACL, be applied close from the source.???????
I see, thanks!
this access applied on int fa0/2 in will accomplish the same purpose !!! and it is actually more correct because it reduces the access-list processing in the router because it only has to filter the traffic generated from network 10.0.0.0/8 going to host 187.100.1.6 .
to make more clear .. if you wanted to ONLY permit network 10.0.0.0/8 (and no other)to have ftp access to host 187.100.1.6 then your extended access-list would go on the int fa0/1 out and look like this..
access-list 101 permit tcp 10.0.0.0 0.255.255.255 host 187.100.16 eq 20
access-list 101 permit tcp 10.0.0.0 0.255.255.255 host 187.100.16 eq 21
but since you are denying protocol access for a specific group then the access list should be implemented near the source…
if you were denying protocol access to many groups and allowing just a few then you implement the extended list near the destination..
thanks 9tut i be taken the exam 640-802 on 15 of july if there are any changes the sims please do inform me at nelsonnebache@yahoo.com i be waiting to here from any one who might be of help
thanks for this great tutorial 9tut… :)
thanx 9 tut for this great platform!
I dont understand what is the meaning of “close to the destination”?
for this example how can we write deny all traffic except 10.0.0.0 /8 ?
@Anonymus
For Standard Access list:
“close to the destination” = interface of the destination of the packet.
In the example, the source = network 10.0.0.0/8 &
destination = 187.100.1.6, interface fa0/1
Thanks so much 4 ur tutoria
Dear all,
Why extended ACL 101 applied at “fa0/1 out” port? If I applied it at “fa0/1 in” port, it is correct or wrong and why?
there is a mistake in How to use the wildcard mask explanation
255.255.240.0 is /20 so address has to be 172.23.16.0/20 not /28
when we want to apply an ACL to an interface, how to know if we should use fa0/0 or fa0/1?
plzz help me
I passed my exam, THANKS for everything 9tut!
I am going to sit my CCNA exam on 28 Sep. Could anybody send me the latest Sim or all the Sim at 9tut is still enough for CCNA 640-802 exam? please do inform and support me. Thank you.
E-mail: inayat291@gmail.com
best regard!
thanks 9tut i be taken the exam 640-802 on 15 of july if there are any changes the sims please do inform me at nelsonnebache@yahoo.com i be waiting to here from any one who might be of help
sorry for mistake!
Guys I have my ccna exam on 20th sept .. does anyone have latest dumps
i will be having my exam too on the 20th..wish me luck :)
for the telnet for apply in the interface i thank we apply by access-class not access-group as
we not from the example
is it right
This is a comment to the webmaster. Your website is missing out on at least 300 visitors per day. I have found a company which offers to dramatically increase your visitors to your website: http://gmbal.com/239r They offer 1,000 free visitors during their free trial period and I managed to get over 30,000 visitors per month using their services, you could also get lot more targeted traffic than you have now. Hope this helps :) Take care.
thank you..9tut… m new in this zone…unaware of thing…bt hope wont be the same …
Dear All, I have the exam tomorrow morning and could use some extra tips! Which lab simulations are the most probable? Any other suggestions??
Thank a lot 9tut.com. i pass my exam on 30 sept scoring 947/1000.
thank!!!!!!!
dont u think ineed yo help?im talking to you
patchrist
What is the difference between ACL and ACL2.
is there any? or it is the same.. thank you!!!
cidr mask asks in exam for acl??
am i right ? ACL mean standard , ACL2 mean EXtended or what ? i m not sure what is it but i guess though !
cna any one link me ccna dump , i got a test following week
why the extended access list 101 is not applied close to the source thus fa0/0 out i dont understand
as far as i know the ACL LOOKS So boarning to me and why instead of ACL WE Can’t use port securities
Hello friends
I am taking the exam this week,please e-mail me the current sims they are testing
Thanks..
Hello friends
I am taking the exam this week,please e-mail me the current sims they are testing barazanalex@gmail.com
Thanks..
i am planning to write my ccna in next week. can anyone please send the latest dumps and sim labs.@ micky.pavani@gmail.com or singam.s@hcl.com
Hello friends
how to create acl between directly connected both in the same subnet (R1-s0/1 to R2-s0/1).when I filtered them, the algorithm find another route and send the updates throw R1-s1/1 via R3 to the R2.thank you
This is really helps in the exam….
thank u do much , very useful
In this Extended Acl why use destination ip ok but why use 0000 (what is meaning of this)
Thanking you
@kannan: 0.0.0.0 represents for a host (only 1 PC) so “187.100.1.6 0.0.0.0″ means “only host 187.100.1.6″
nice
Richard
you are right access-list will be applied fa0/0 in ……………….it will deny access of any FTP traffic from 10.0.0.0 network going towards 187.100.1.6……….as soon as it enters the router………………..this is by far the best way to apply it ………….as it will save the maximum resources………rather than going in the router and then out to deny it…………….hope it is useful info for your guys out there …………….thanks………………….
Atif
kannan
just remember the rule about wild card mask
0 = match the octet value
255 = do not match that octet value at all
so …………..you can say its opposite to the Subnet mask in a way
mani
i think you are confusing………….ACL and STP / RSTP …..
put a diagram and explain……………in a clear language for someone to help you out with.
thanks
Hey I plan to take my ccna exem this week …can I have a latest dumps add lab questions. …I’m waiting
hornella.ngongo@gmail.com
please shar configuration of router and switch
my CCNA certificate has expire. Now i want to write CCNE.Is it possible