CCNA – Access List Questions
Here you will find answers to CCNA Access list questions
Note: If you are not sure about how to use Access list, please read my Access list tutorial
Question 1
Your boss is learning a CCNA training course, refer to the exhibit. The access list has been configured on the S0/0 interface of router RTB in the outbound direction. Which two packets, if routed to the interface, will be denied? (Choose two)
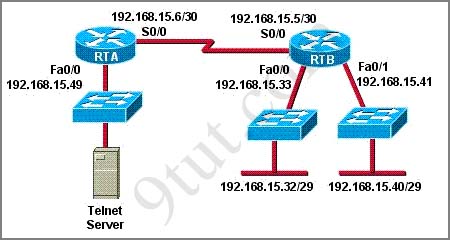
access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
access-list 101 permit ip any any
A. source ip address: 192.168.15.5; destination port: 21
B. source ip address: 192.168.15.37 destination port: 21
C. source ip address: 192.168.15.41 destination port: 21
D. source ip address: 192.168.15.36 destination port: 23
E. source ip address: 192.168.15.46; destination port: 23
F. source ip address: 192.168.15.49 destination port: 23
Answer: D E
Explanation
First we notice that telnet uses port 23 so only D, E & F can satisfy this requirement.
The purpose of this access-list is to deny traffic from network 192.168.15.32 255.255.255.240 (to find out the subnet mask just convert all bit “0″ to “1″ and all bit “1″ to “0″ of the wildcard mask) to telnet to any device. So we need to figure out the range of this network to learn which ip address will be denied.
Increment: 16
Network address: 192.168.15.32
Broadcast address: 192.168.15.47
-> Only 192.168.15.36 (Answer D) & 192.168.15.46 (Answer E) belong to this range so they are the correct answer.
Question 2
Refer to the graphic. It has been decided that PC1 should be denied access to Server. Which of the following commands are required to prevent only PC1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two)
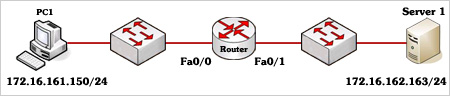
A – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 out
B – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 in
C – Router(config)# access-list 101 deny ip host 172.16.161.150 host 172.16.162.163
Router(config)# access-list 101 permit ip any any
D – Router(config)# access-list 101 deny ip 172.16.161.150 0.0.0.255 172.16.162.163 0.0.0.0
Router(config)# access-list 101 permit ip any any
Answer: B C
Question 3
Refer to the exhibit. Why would the network administrator configure RA in this manner?

A. to give students access to the Internet
B. to prevent students from accessing the command prompt of RA
C. to prevent administrators from accessing the console of RA
D. to give administrators access to the Internet
E. to prevent students from accessing the Internet
F. to prevent students from accessing the Admin network
Answer: B
Explanation
Although the access-list is used to “permit” network 10.1.1.0/24 but the best answer here is “to prevent students from accessing the command prompt of RA”. From the picture above, we know that 10.1.1.0/24 is the “Admin” network. This access list is applied to “line vty 0 4″ so it will permit only Telnet traffic from “Admin” to RA while drop all other traffic (because of the implicit “deny all” command at the end of the access list). Therefore we can deduce that it will “prevent students from accessing the command prompt of RA”.
This access list only filters Telnet traffic (because it is applied to vty line) so it will not prevent or allow anyone to access the Internet -> A, D, E are not correct.
C is not correct as this access list allows administrators to access the console of RA.
F is not correct as this access list does not proceed TCP, UDP or IP traffic so the students still access the Admin network.
(Notice that the “command prompt” here implies telnet as telnet is the only way to remotely access RA)
Question 4
An access list was written with the four statements shown in the graphic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?
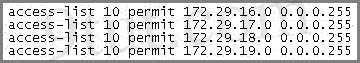
A. access-list 10 permit 172.29.16.0 0.0.0.255
B. access-list 10 permit 172.29.16.0 0.0.1.255
C. access-list 10 permit 172.29.16.0 0.0.3.255
D. access-list 10 permit 172.29.16.0 0.0.15.255
E. access-list 10 permit 172.29.0.0 0.0.255.255
Answer: C
Explanation
Four statements above allow 4 networks (from 172.29.16.0/24 to 172.29.19.0/24) to go through so we can summary them as network 172.29.16.0/22.
/22 = 255.255.252.0 so it equals 0.0.3.255 when converting into wildcard mask -> C is correct.
A, B, D are not correct as their wildcard masks are false. For example:
Answer A allows from 172.29.16.0 to 172.29.16.255
Answer B allows from 172.29.16.0 to 172.29.17.255
Answer D allows from 172.29.16.0 to 172.29.31.255
Both the network address and wildcard mask of answer E are false as it allows the whole major network 172.29.0.0/16 to go through.
Question 5
A network administrator wants to add a line to an access list that will block only Telnet access by the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?
A – access-list 101 deny tcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
B – access-list 101 deny tcp 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
C – access-list 1 deny tcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21
access-list 1 permit ip any any
D – access-list 1 deny tcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23
access-list 1 permit ip any any
Answer: A
Explanation:
First the question asks to block only Telnet access so the port we have to use is 23 -> C is not correct.
Next we need to block traffic from hosts on the subnet 192.168.1.128/28, which is 192.168.1.128 0.0.0.15 if we convert to wildcard mask (just invert all bits of the subnet mask,from 0 to 1 and from 1 to 0 we will get the equivalent wildcard mask of that subnet mask) -> so B is incorrect
In this case, we have to use extended access list because we need to specify which type of traffic (TCP) and which port (23) we want to block -> so D is incorrect because it uses standard access list.
Question 6
As a network administrator, you have been instructed to prevent all traffic originating on the LAN from entering the R2 router. Which the following command would implement the access list on the interface of the R2 router?
A – access-list 101 in
B – access-list 101 out
C – ip access-group 101 in
D – ip access-group 101 out
Answer: C
Question 7
The following access list below was applied outbound on the E0 interface connected to the 192.169.1.8/29 LAN:
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
How will the above access lists affect traffic?
A – FTP traffic from 192.169.1.22 will be denied
B – No traffic, except for FTP traffic will be allowed to exit E0
C – FTP traffic from 192.169.1.9 to any host will be denied
D – All traffic exiting E0 will be denied
E – All FTP traffic to network 192.169.1.9/29 will be denied
Answer: D
Explanation:
There is always an implicit “deny all” command at the end of every access list, so if an access list doesn’t have any “permit” command, it will block all the traffic.
Note: This access list is applied on outbound direction so only packets exiting E0 will be checked. Packets entering E0 will not be checked and they all are allowed to pass through.
Question 8
The access control list shown in the graphic has been applied to the Ethernet interface of router R1 using the ip access-group 101 in command. Which of the following Telnet sessions will be blocked by this ACL? (Choose two)
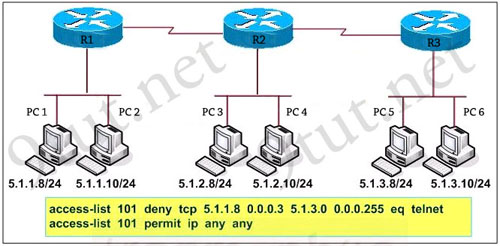
A – from host PC1 to host 5.1.1.10
B – from host PC1 to host 5.1.3.10
C – from host PC2 to host 5.1.2.10
D – from host PC2 to host 5.1.3.8
Answer: B D
Explanation
Below is the simple syntax of an extended access list:
access-list access-list-number {deny | permit} {ip|tcp|udp|icmp} source [source-mask] dest [dest-mask] [eq dest-port]
Notice that this access list is applied to the Ethernet interface of R1 in the “in direction” so in this case, it will filter all the packets originated from E1 network (host PC1 and PC2) with these parameters:
Source network: 5.1.1.8 0.0.0.3 which means 5.1.1.8/252 (just invert all the wildcard bits to get the equivalent subnet mask) -> Packets from 5.1.1.8 to 5.1.1.11 will be filtered.
Destination network: 5.1.3.0 0.0.0.255 which means 5.1.3.0/24-> Packets to 5.1.3.0/24 will be filtered
Therefore packets originated from 5.1.1.8 to 5.1.1.11 and have the destination to the host 5.1.3.x (via Telnet) will be denied.
Question 9
The following configuration line was added to router R1
Access-list 101 permit ip 10.25.30.0 0.0.0.255 any
What is the effect of this access list configuration?
A – permit all packets matching the first three octets of the source address to all destinations
B – permit all packet matching the last octet of the destination address and accept all source addresses
C – permit all packet matching the host bits in the source address to all destinations
D – permit all packet from the third subnet of the network address to all destinations
Answer: A



Hi All,
I’m taking the exam in 2 weeks. Anyone can please send me the latest dump? ladyflavia34@yahoo.com
Thanks!
Can someone please email me the latest CCNA dumps. I will be taking the exam in a couple of weeks.
Thank you much
email: akilimak@yahoo.com
Thanks,
-Reg
Q1
- the increment is 8 NOT 16.
With a 29 prefix length you have 32 subnets with 6 usable hosts in each. The subnet mask is 255.255.255.248
Correct answer is D only.
Correction!
Q1
Wildcard bits 0.0.0.15 are 255.255.255.240 mask – and indeed an 16 increment
My mistake!
Can someone please email me the latest CCNA dumps. I will be taking the exam in a couple of weeks.
Thank you much
email: nelkrson@juno.com
Thanks,
Keith
Hy can someone please email me the latest dump.
am taking my exam next week. rafan.fatima@gmail.com
Thanks
Rafi
Can someone send latest dump please
thanks 9tut
email:ibrahim.naguib@live.com
Are Eigrp, ACL2 and VTP are only the sims in the exam??
I’ll have my exam this week…
please help..
thank you..
can someone send latest dump to sanukavanattu@gmail.com
thank youuuuuuuuuuuuuuuu.
Dears
if you have any latest dumps please send me because my exam is on this week end
hossam.saber4@gmail.com
thnx in advance
In q1 wouldn’t make more sense to deny 192.168.15.0 network. instead of saying 192.168.15.32 from telnet? i don’t understand how answers d/e work. Because the question for an extended access-list is permit/deny source protocol destination and then port. someone please explain.
thanks
@mikey
Read instruction thoroughly, and will help you to solve the problem.
access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
access-list 101 permit ip any any
/29 is increment of 8……..32+8=40+8=48
47 is a broadcast address.
telnet is port 23
Options A through C is pointing to port 21 FTP
Option F does not belong to subnet, but port number is right though.
Now analyze the wildcard mask. Only options D and E fits the scenario.
ACL is not set up to block a whole network….192.168.15.32 0.0.0.15
@koffy,
Maybe i am missing something. Your example is /29 increment of 8 and the example is increment of 16 which one is correct. i know they both would get the same answer. So, if i understand this right becasue answers d/e are 36/46 they fall within their respective ranges and .49 is the beginning of the next network is that correct? i also, was looking at the .32 as being an actual host on the newtork.
@mikey
Well, lets go with /28 increment of 16.
Subnet 32 ……range 32~48
Don’t focus too much on whether .32 is host or not. Analyze the ACL, and the result coming out of it:
“Which two packets, if routed to the interface, will be denied?”
@koffy,
Thanks for the clarification. i will have to pay make sure i look at as a network and not just a host.
For Question # 7, shouldn’t the access list read as follows :
access-list 135 deny tcp 192.169.1.8 0.0.0.7 any eq 20
access-list 135 deny tcp 192.169.1.8 0.0.0.7 any eq 21
instead of :
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
I appreciate your feedback on this.
@resolved: Both are correct. In the “access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any” command, 20 is the source port while in the “access-list 135 deny tcp 192.169.1.8 0.0.0.7 any eq 20″ command, 20 is the destination port.
On Question 7, I don’t know but maybe there is something wrong with this question, since the access list was applied outbound, therefore because of implicit deny all, any traffic going out of E0 will be denied. D is correct but then so is A and E (any traffic from any address).
@Vanessa
Q7.
The above statement is incomplete without the third line, regardless of which interface access-list is applied on, IN or OUT.
A single-entry ACL with only one deny entry has the effect of denying all traffic. You must have at least one permit statement in an ACL or all traffic is blocked. “Implicit deny all”.
Option D seem like the most suitable solution. Thanks.
PlZ send me latest dumps
Hossam.saber4@gmail.com
thnx in advance
I wrote CCNA exam today passing with a score of 920.
Sims were ACL, VTP & Eigrp
Many thanks to 9Tut
pls rly me if anybody knw the answres for access-list simulation qtn (in which pinging frm switch)
if anybody got latest dumps pls sent me urgent,its my third attempt….renjucek@gmail.com
I dont really understand how to ascertain the direction to apply the access-list. Also, when do we use access-list and when do we use access-group?
Can anyone assist?
@CCIE wannabe
First of all, let get the commonalities out of the way:
Extended ACL: close to the source as closely as possible.
Standard ACL: close to the destination as closely as possible.
Which interface to place ACL, (filtering and direction)…IN or OUT, usually base on network flow.
ie When a group of host are either to be permitted or deny via TCP(http) or IP connection.
Inbound access-list process packets before they are routed to an outbound interface.
Outbound access-list process packets after they are routed to an interface.
When your written policy or statement contain terms like: PERMIT ANY or DENY ANY, you will use “ip access-group IN or OUT” depending on the scenario presented to you.
Any explanations or suggestions are welcome. I hope this piece helps to share some light on the subject. Thanks.
dearest ccna’s
pls sed me latest dumps,i am writing my exam soonest. thank you very much.
chiprosper2009@yahoo.com
Can Someone please send me the latest dump, i am going to take the exam next week.
pranay.srivastava23@gmail.com
Hello All i want to configure i Cisco ASA in GNS3 how can i get IOS Images to Configure ASA or Pix plz help me how to get this is my Email : Mohamed.ahh@hotmail.com
im going to take my ccna exam please can anyone send me the latest dumps??
Thanks
asifmwi@gmail.com
Can any one provide me the web link to download the packet tracer
i already dne ccna xam in the date of november 30 th ,i failed.becoz of access list stumulation.i want to knw abt tat twisted access list qusestion.can u pls send it to me………….any new stimulation is there pls send it to me…………..
my mail id : manju_raghavee@yahoo.com
Please, could someone send me the latest dumps to guzmonne@hotmail.com??? Best Regards.
Can someone explain to me why question 8 is not A, D?
@Question 8
PC 1 is 5.1.1.8 and PC 2 is 5.1.1.10 This is the source.
PC 5 is 5.1.3.8 and PC 6 is 5.1.3.10 This is the destination.
Option A is pointing to PC 2. 5.1.1.10…..PC 2 is a source not a destination.
I hope this helps. Thanks.
Question 8:
http://www.say002.com/upload/201102181618018885.jpg
@xallax
in Q8
5.1.1.8 0.0.0.3 is defined, this means the hosts between 5.1.1.8 through 5.1.1.11 will be blocked
however, the first blocked host in this subnet will be 5.1.1.9 and the last will be 5.1.1.10, so how can Host1 be blocked from telnet using this ACL ?
In every ACL we define, we use the network address of the subnet and then wildcard mask in the definition ? If so, then this ACL does not block Host 1.
@anonymous
that wildcard does NOT create a subnet. it just says “filter IPs starting HERE and ending HERE”
starting at .9, ending at .11
can someone send me the latest dump? I am writing my CCNA exam in 2weeks time.
Regards
ontarioboy75@hotmail.com
I need the latest dumps as well my email address is big83j@gmail.com
Could any one explain about Question 2, why is B the right answer?
Router(config-if)# ip access-group 101 in
Would this not deny access to everything on the Fa 0/0?
Thanks
@hello
PC1 is 172.16.161.150
it has to be denied from reaching 172.16.162.163 (the server)
all other traffic is permitted
the ACL would be
access-list # deny ip host PC1 host SERVER
access-list # permit ip any any
this is what option C states and it is correct.
now we have to apply this ACL so that the traffic is filtered.
we can apply it as close to the source as possible (this is an extended ACL and the rule says that it should be closer). the closest spot is interface fa0/0.
which direction? in
same as option B
maybe you just overlooked “ip permit any any” under the first line on option B”. please pay more attention next time
@xallax
thanks a lot
this was very helpful
good questions about ACL. thanx
block all private ip address using access list 20
and block all private ip address using standard acl name
Dears
if you have any latest dumps please send me because my exam is on Jan-2012
my e-mail sahab171@gmail.com
found a free video tutorial on access-lists:
http://www.bosscbt.tv/icnd2/intro-to-access-lists/
:)
i think answr for the 4th one is incorrect. It shud b (D). pls correct me if i am wrong
I think answer to Question # 4 is D also. Because /22 only gives you 172.29.16.0 to 172.29.17.255 ?
I gave my exam on 3-Jan-2012. This site is valid and and had 90% of the questions on exam. I passed with 905/1000. But in my humble opinion try to cover your basics, even if you don’t you will still pass using this website but don’t do it this way, study and then use this website! Good job 9tut guys!