CCNA – Access List Questions
Here you will find answers to CCNA Access list questions
Note: If you are not sure about how to use Access list, please read my Access list tutorial
Question 1
Your boss is learning a CCNA training course, refer to the exhibit. The access list has been configured on the S0/0 interface of router RTB in the outbound direction. Which two packets, if routed to the interface, will be denied? (Choose two)
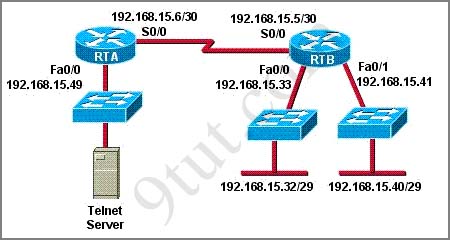
access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
access-list 101 permit ip any any
A. source ip address: 192.168.15.5; destination port: 21
B. source ip address: 192.168.15.37 destination port: 21
C. source ip address: 192.168.15.41 destination port: 21
D. source ip address: 192.168.15.36 destination port: 23
E. source ip address: 192.168.15.46; destination port: 23
F. source ip address: 192.168.15.49 destination port: 23
Answer: D E
Explanation
First we notice that telnet uses port 23 so only D, E & F can satisfy this requirement.
The purpose of this access-list is to deny traffic from network 192.168.15.32 255.255.255.240 (to find out the subnet mask just convert all bit “0″ to “1″ and all bit “1″ to “0″ of the wildcard mask) to telnet to any device. So we need to figure out the range of this network to learn which ip address will be denied.
Increment: 16
Network address: 192.168.15.32
Broadcast address: 192.168.15.47
-> Only 192.168.15.36 (Answer D) & 192.168.15.46 (Answer E) belong to this range so they are the correct answer.
Question 2
Refer to the graphic. It has been decided that PC1 should be denied access to Server. Which of the following commands are required to prevent only PC1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two)
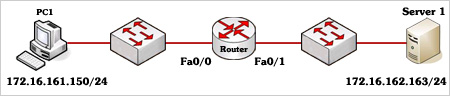
A – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 out
B – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 in
C – Router(config)# access-list 101 deny ip host 172.16.161.150 host 172.16.162.163
Router(config)# access-list 101 permit ip any any
D – Router(config)# access-list 101 deny ip 172.16.161.150 0.0.0.255 172.16.162.163 0.0.0.0
Router(config)# access-list 101 permit ip any any
Answer: B C
Question 3
Refer to the exhibit. Why would the network administrator configure RA in this manner?

A. to give students access to the Internet
B. to prevent students from accessing the command prompt of RA
C. to prevent administrators from accessing the console of RA
D. to give administrators access to the Internet
E. to prevent students from accessing the Internet
F. to prevent students from accessing the Admin network
Answer: B
Explanation
Although the access-list is used to “permit” network 10.1.1.0/24 but the best answer here is “to prevent students from accessing the command prompt of RA”. From the picture above, we know that 10.1.1.0/24 is the “Admin” network. This access list is applied to “line vty 0 4″ so it will permit only Telnet traffic from “Admin” to RA while drop all other traffic (because of the implicit “deny all” command at the end of the access list). Therefore we can deduce that it will “prevent students from accessing the command prompt of RA”.
This access list only filters Telnet traffic (because it is applied to vty line) so it will not prevent or allow anyone to access the Internet -> A, D, E are not correct.
C is not correct as this access list allows administrators to access the console of RA.
F is not correct as this access list does not proceed TCP, UDP or IP traffic so the students still access the Admin network.
(Notice that the “command prompt” here implies telnet as telnet is the only way to remotely access RA)
Question 4
An access list was written with the four statements shown in the graphic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?
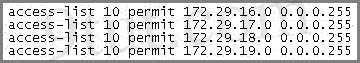
A. access-list 10 permit 172.29.16.0 0.0.0.255
B. access-list 10 permit 172.29.16.0 0.0.1.255
C. access-list 10 permit 172.29.16.0 0.0.3.255
D. access-list 10 permit 172.29.16.0 0.0.15.255
E. access-list 10 permit 172.29.0.0 0.0.255.255
Answer: C
Explanation
Four statements above allow 4 networks (from 172.29.16.0/24 to 172.29.19.0/24) to go through so we can summary them as network 172.29.16.0/22.
/22 = 255.255.252.0 so it equals 0.0.3.255 when converting into wildcard mask -> C is correct.
A, B, D are not correct as their wildcard masks are false. For example:
Answer A allows from 172.29.16.0 to 172.29.16.255
Answer B allows from 172.29.16.0 to 172.29.17.255
Answer D allows from 172.29.16.0 to 172.29.31.255
Both the network address and wildcard mask of answer E are false as it allows the whole major network 172.29.0.0/16 to go through.
Question 5
A network administrator wants to add a line to an access list that will block only Telnet access by the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?
A – access-list 101 deny tcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
B – access-list 101 deny tcp 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
C – access-list 1 deny tcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21
access-list 1 permit ip any any
D – access-list 1 deny tcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23
access-list 1 permit ip any any
Answer: A
Explanation:
First the question asks to block only Telnet access so the port we have to use is 23 -> C is not correct.
Next we need to block traffic from hosts on the subnet 192.168.1.128/28, which is 192.168.1.128 0.0.0.15 if we convert to wildcard mask (just invert all bits of the subnet mask,from 0 to 1 and from 1 to 0 we will get the equivalent wildcard mask of that subnet mask) -> so B is incorrect
In this case, we have to use extended access list because we need to specify which type of traffic (TCP) and which port (23) we want to block -> so D is incorrect because it uses standard access list.
Question 6
As a network administrator, you have been instructed to prevent all traffic originating on the LAN from entering the R2 router. Which the following command would implement the access list on the interface of the R2 router?
A – access-list 101 in
B – access-list 101 out
C – ip access-group 101 in
D – ip access-group 101 out
Answer: C
Question 7
The following access list below was applied outbound on the E0 interface connected to the 192.169.1.8/29 LAN:
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
How will the above access lists affect traffic?
A – FTP traffic from 192.169.1.22 will be denied
B – No traffic, except for FTP traffic will be allowed to exit E0
C – FTP traffic from 192.169.1.9 to any host will be denied
D – All traffic exiting E0 will be denied
E – All FTP traffic to network 192.169.1.9/29 will be denied
Answer: D
Explanation:
There is always an implicit “deny all” command at the end of every access list, so if an access list doesn’t have any “permit” command, it will block all the traffic.
Note: This access list is applied on outbound direction so only packets exiting E0 will be checked. Packets entering E0 will not be checked and they all are allowed to pass through.
Question 8
The access control list shown in the graphic has been applied to the Ethernet interface of router R1 using the ip access-group 101 in command. Which of the following Telnet sessions will be blocked by this ACL? (Choose two)
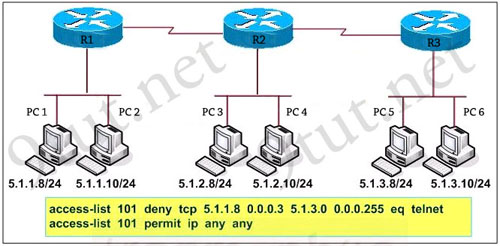
A – from host PC1 to host 5.1.1.10
B – from host PC1 to host 5.1.3.10
C – from host PC2 to host 5.1.2.10
D – from host PC2 to host 5.1.3.8
Answer: B D
Explanation
Below is the simple syntax of an extended access list:
access-list access-list-number {deny | permit} {ip|tcp|udp|icmp} source [source-mask] dest [dest-mask] [eq dest-port]
Notice that this access list is applied to the Ethernet interface of R1 in the “in direction” so in this case, it will filter all the packets originated from E1 network (host PC1 and PC2) with these parameters:
Source network: 5.1.1.8 0.0.0.3 which means 5.1.1.8/252 (just invert all the wildcard bits to get the equivalent subnet mask) -> Packets from 5.1.1.8 to 5.1.1.11 will be filtered.
Destination network: 5.1.3.0 0.0.0.255 which means 5.1.3.0/24-> Packets to 5.1.3.0/24 will be filtered
Therefore packets originated from 5.1.1.8 to 5.1.1.11 and have the destination to the host 5.1.3.x (via Telnet) will be denied.
Question 9
The following configuration line was added to router R1
Access-list 101 permit ip 10.25.30.0 0.0.0.255 any
What is the effect of this access list configuration?
A – permit all packets matching the first three octets of the source address to all destinations
B – permit all packet matching the last octet of the destination address and accept all source addresses
C – permit all packet matching the host bits in the source address to all destinations
D – permit all packet from the third subnet of the network address to all destinations
Answer: A



@xallax
Please, I have one ACL question, and few others i will post on site. I hope you can help me solve it.
An access list has been created that will only deny the host 204.204.7.89 to access an ftp server located at 196.6.13.254.
access-list 111 deny tcp 204.204.7.89 0.0.0.0 196.6.13.254 0.0.0.0 eq 21
access-list 111 permit tcp any any
Which of the following group of command will place this ACL in the proper location?
1. ip access-group 111 out
2. ip access-group 111 in
@xallax
How would you obtain CDP information from a Cisco router that is not directly connected to the admin’s console?
Which of the network devices increases the number of collision domain?
1. A repeater
2. Multiport repeater
3. Hub
4. Switch
Waste and loss of material are normal cost in any cabling project. What is reasonable waste cost to include in BID?
A. 4%…….B. 20%…….C. 8%…….D. 15%…….E. 1%
@xallax
Which dial plan component is responsible for selecting the appropriate path for a call?
1. Call coverage
2. Endpoint addressing
3. Call routing and path selection
4. Call previledges
When implementing a VOIP services, which two designs considerations should be followed?
1. Confirm that network jitter is minimal
2. Establish priority queing to ensure that large data packets are sent uninterrupted
3. Use tcp to reduce delay and dropped packets
4. Disable real-time protocol to reduce queing strategy demand
5. Ensure that packets delays donnot exceed 150ms
@anonymous
these are CCNA voice topics…
Q1: B
answer from this link (page 33):
http://www.scribd.com/doc/10284453/Cisco-642436-v471
Q2: A, E
answer from this link (Q10):
http://www.correct-way.comlu.com/?id=3,128,0,169
wish i knew how to explain them, but i don’t. sorry
@anonymous
An access list has been created that will only deny the host 204.204.7.89 to access an ftp server located at 196.6.13.254.
access-list 111 deny tcp 204.204.7.89 0.0.0.0 196.6.13.254 0.0.0.0 eq 21
access-list 111 permit tcp any any
Which of the following group of command will place this ACL in the proper location?
1. ip access-group 111 out
2. ip access-group 111 in
ANSWER: ip access-group 111 in
This is an extended access list, it should be placed as close to the source as possible.
=============================
How would you obtain CDP information from a Cisco router that is not directly connected to the admin’s console?
OPTION 1: “show cdp neighbor detail” from the current router/switch console if it is connected to the router we want to learn about.
OPTION 2: telnet to a router/switch that is connected to the router we want to learn about and issue the command “show cdp nei det”
=============================
Which of the network devices increases the number of collision domain?
1. A repeater
2. Multiport repeater
3. Hub
4. Switch
A switch increases the number of collision domains.
collision domain = network segment
=============================
Waste and loss of material are normal cost in any cabling project. What is reasonable waste cost to include in BID?
A. 4%…….B. 20%…….C. 8%…….D. 15%…….E. 1%
I honestly do not know. sorry
@xallax
Thank you very much. In any event you’ve been helpful.
Hi my friends all of You
i am going to get my CCNA Exam on Oct, 15 2011 so please if you have any suggestion let me know.
Thanks
Hi my friends all of You
i am going to get my CCNA 640-802 Exam on Oct, 15 2011 so please if you have any suggestion let me know.
Thanks
Thanx 9tut. Ur website helped me pass my exam today.
Thanx a mil.
@mzae please what were the questions like and what sims came out i hope to write mine tomorrow please reply…..what were the sims?
i am going to get my CCNA 640-802 Exam on Oct, 27 2011 so please if you have any suggestion let me know.
Thanks
i am planning to give CCNA in NOV. please any one has latest dumps than please send me.
help me for exam nikunj_ec09@yahoo.com and nec.nikunj@gmail.com
Hi Experts!
I have a quick Basic Question..
What is the difference between the port-security feature, and the switch port access list ?
Thanks,
Vinie
@anonymous
you can apply ACLs to switch ports?
Yes, the mac access-list command does that, if I am not wrong!
@anonymous
thank you! thought ACLs deal only with L3 traffic
ok, went over cisco’s site at this link:
http://www.cisco.com/en/US/docs/switches/lan/catalyst2950/software/release/12.1_9_ea1/configuration/guide/swacl.html
scroll aaaaaall the way to the bottom of the page
ACLs 700~799 are for MAC filtering
i had no idea because i’ve not seen them anywhere for the CCNA preparation. MAC filtering isn’t possible in packettracer either… still, i’m glad i know now :)
anyway… port-security can shut down the interface on error, can just drop the frame and increase a counter or just drop it. that’s under the “switchport port-security violation” list of options. it can save the learned MAC, it can allow a certain number of MACs to be learned…
to be honest, port-security is pretty much like creating an access-list, isnt it?
Xallax :
Precisely my point.!!! There are some subtle intuitive differences, but technically I believe we can achieve the same thing using any of the two..
Is there a concept which we are missing on ??
Thanks anyways for the update and the link :) Surely helpful!
QUESTION: I have 4 department SALES, TRAINING, HR, ACCOUNT. in each department we need 100-100 pc. I have a C-class ip add 192.168.10.20
so how can i connect all 400 pc in MINIMUM cast. and I need to give maximum speed for HR and ACCOUNT.and less speed for sales and training.
pls help me
Question 7
The following access list below was applied outbound on the E0 interface connected to the 192.169.1.8/29 LAN. I agreed with the answer “D”. However, the explanation also said “If we use the command “access-list 135 permit ip any any” at the end of this access list then the answer should be C – FTP traffic from 192.169.1.9 to any host will be denied.” If we applied ACL “outbound” on the E0 interface, should this affect the traffic going out of router interface … why would this affect FTP traffice “FROM” 192.169.1.9 going in to router E0 interface??? Can someone help explain?
@newby
let’s look at the ACL…
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
deny ip any any
the last line it’s added by the router by default at the end of any IP ACL
let’s read the ACL…
first line: deny traffic from 192.169.1.8/29 that comes from port 20 and goes anywhere
second line: deny traffic from 192.169.1.8/29 that comes from port 21 and goes anywhere
so far we’ve killed any FTP traffic from possible FTP servers on the subnetwork
third line: deny traffic from any source to any destination
actually the third line (the “invisible” one) is the one that answers your question
i want newdump question……………
i suggest that the answer to question 4 is D instead. what do u think?
@amogh
to answer that question you have not provided enough information for a reliable answer.
what existing network equipment is available?
your using private IP addresses so those will have to be converted to public ip addresses.
what has your ISP provided for the public IP addresses.
this is just to start.
providing more bandwith for the 2 departments might be a problem if you do not have enough bandwith from your ISP.
how many T1 lines are you going to need to provide the bandwith?
Hi,
Please any one has latest dumps I’m planning to take the exam for CCNA this Nov.2011..
Thanks!
Please send me latest dumps anyone… qbone1221@yahoo.com…
Thanks!
anyone with the latest dumps i am writing in a week please itgoodenough007@yahoo.co.uk
ccna
hello all
my exam is coming up on friday 28 Oct 2011. pls i need latest dumps from you all. thanks
send to vibinnarayanan@gmail.com
@experts : In the router BOOT sequence, after the POST, is it the configuration register’s value which the router checks and then the bootstrap code from ROM is run, or its the other way round i.e. first the bootstrap, and then the conf reg value.
Thanks a lot.
@vinie
hey
please check here:
https://learningnetwork.cisco.com/thread/20889
Question 7
How will the above access lists affect traffic?
C – FTP traffic from 192.169.1.9 to any host will be denied
D – All traffic exiting E0 will be denied
Answer: D
The answer D involve answer C, isnt’it?
I think they are both must be right answers
Vadim,
Question 7 centers around the default Deny any any that is automatically added to the end of any access list. Since the access list only deny FTP traffic and the default deny all denys everthing else
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
Some say it is best practice to add the deny any any at the end of all Access lists so the fact that it is present by default isn’t overlooked.
Dears
if you have any latest dumps please send me because my exam is on this Thursday
farid.amiree@hotmail.com
Thanks
I am planning to take my CCNA exam this weekend. Can you please send me the latest dump ?My id is rhbharath@gmail.com
@xallax
Sorry to bother you. I recalled i posted this question sometime in the past. Just wandering if you can break it down further for me. Thanks.
Q.
What combination of IP address and wildcard mask should be used to specify only the last 8 address in the subnet 192.168.3.32/28?
a. 192.168.3.32 0.0.0.7
b. 192.168.3.32 0.0.0.15
c. 192.168.3.40 0.0.0.7
d. 192.168.3.40 0.0.0.15
Answer is option C.
I do agree with option C. But, since it is specifying the last 8 addresses, doesn’t option A seem somewhat likely?
@koffy
192.168.3.32/28
x.x.x.32 ~ x.x.x.47
the last 8 ones are
x.x.x.40 ~ x.x.x.47
to filter this range we use
x.x.x.40 _ 0.0.0.7
option A would filter the FIRST 8 IPs :)
@xallax
Thanks.
I am planning to CCNA exam next week .Can you please send latest dump to ratna682003@yahoo.ca
Thanks
Hi
The first question in the series is wrong ,where the acces list is applied to /29 subnet ,which will be 255.255.255.248 .and the increment should be 8 not 16,
please confirm with me whether this is correct or wrong
Plzzzzz friends send me latest CCNA dumps..
Also suggest me some materials from which I can prepare myself for CCNA exam..
my email address: m.aasif.khan@hotmail.com
friends I am planning for CCNA exam. Plzzz send me latest CCNA dumps..
Also suggest me some materials from which I can prepare myself for CCNA exam..
my email address: m.aasif.khan@hotmail.com
Can any body say what are the possible proof that we can submit on the day of exam?
Plzzzzz
qs 4
i think d is the correct answer
commom bits are
8+8+4=20
third octat 0001000
0001001
0001010
0001100
common bits are first four
so the ans is d
Im sitting for my CCNA exam end of November.May you assist you with the latest dumps please.You can send on:
smakomichi@yahoo.com
Hi I was a bit confused with the answer on Q8:
According to the required statement given. ACL was applied on R1 per ACL statements
access-list 101 deny tcp 5.1.1.8 0.0.0.3 5.1.3.0 0.0.0.255
access-list 101 permit ip any any
- so with this means Any host under 5.1.1.8 /30 network will be denied to 5.1.3.0 /24 network.. And Im only seeing the the 5.1.1.10 is the one will be denied instead the 5.1.3.0 net since that is the desitination address Please clarrify..
Thanks
@rye
access-list 101 deny tcp 5.1.1.8 _ 0.0.0.3 ___ 5.1.3.0 _ 0.0.0.255
access-list 101 deny tcp – deny all TCP traffic originating from…
5.1.1.8 _ 0.0.0.3 – 5.1.1.8 – .11 will be denied if they have a destination of…
5.1.3.0 _ 0.0.0.255 – the IPs from 5.1.3.0 to .255
also take into consideration that what you call “5.1.1.8 /30″ actually refers to 4 usable IPs here.
B and D are correct because the traffic is telnet (TCP port 23), the source is in the range of 5.1.1.8 to 5.1.1.11 and the destination is in the range of 5.1.3.0 to 5.1.3.255.
now that makes really a lot of sense for me now…. got that right… well, lesson learned , given answers also need to be analyzed deeply.. not just pointing into those figures and you thought it was right but it also needs to see it well how it supposed to be answered.. I see now, how those hosts from R1 have been denied to the hosts on 5.1.3.0 network via telnet traffic.. because I was assuming of the given IP add (5.1.1.10) at end will give you the right answer though it was belong to the same mask of the statements…Tricky!! :) thanks a lot xallax
In Q7 the C answer WOULDN’T be correct even if a “permit ip any any” would be added at the end of the ACL.
Why?
Because FTP ports 20 and 21 are SERVER ports and therefore in order for the ACL to block FTP traffic from the host mentioned in C answer, these FTP ports should lie in the “destination” area of the ACL statements, after the “any” keyword.
But as it is now, the ACL prevents only outbound traffic with “source” ports of 20. 21 and all FTP clients use ports above 1023 as source ports for FTP connections, both in active and passive mode, so those two statements wouldn’t prevent any outbound FTP connection from going out.
Can someine help me with the latest dumps pls
eng.falahrofifanalmajali@yahoo.com
PLEASE 9TUT CREW INEED YOUR HELP,4 THE LATEST DUMP.AM WRITING ON TUESDAY.
shegsytom@yahoo.co.uk
In question 8
“Source network: 5.1.1.8 0.0.0.3 which means 5.1.1.8/252 (just invert all the wildcard bits to get the equivalent subnet mask) -> Packets from 5.1.1.8 to 5.1.1.11 will be filtered.”
isn’t it suppose to be “Packets from 5.1.1.8 to 5.1.1.12 will be filtered” becasue subnet mask is 255.255.255.252 so the increment will be 4 right?