CCNA – Access List Questions
Here you will find answers to CCNA Access list questions
Note: If you are not sure about how to use Access list, please read my Access list tutorial
Question 1
Your boss is learning a CCNA training course, refer to the exhibit. The access list has been configured on the S0/0 interface of router RTB in the outbound direction. Which two packets, if routed to the interface, will be denied? (Choose two)
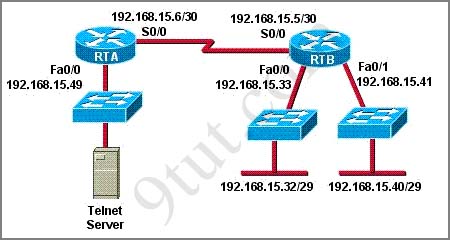
access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
access-list 101 permit ip any any
A. source ip address: 192.168.15.5; destination port: 21
B. source ip address: 192.168.15.37 destination port: 21
C. source ip address: 192.168.15.41 destination port: 21
D. source ip address: 192.168.15.36 destination port: 23
E. source ip address: 192.168.15.46; destination port: 23
F. source ip address: 192.168.15.49 destination port: 23
Answer: D E
Explanation
First we notice that telnet uses port 23 so only D, E & F can satisfy this requirement.
The purpose of this access-list is to deny traffic from network 192.168.15.32 255.255.255.240 (to find out the subnet mask just convert all bit “0″ to “1″ and all bit “1″ to “0″ of the wildcard mask) to telnet to any device. So we need to figure out the range of this network to learn which ip address will be denied.
Increment: 16
Network address: 192.168.15.32
Broadcast address: 192.168.15.47
-> Only 192.168.15.36 (Answer D) & 192.168.15.46 (Answer E) belong to this range so they are the correct answer.
Question 2
Refer to the graphic. It has been decided that PC1 should be denied access to Server. Which of the following commands are required to prevent only PC1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two)
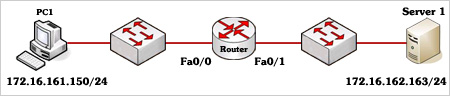
A – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 out
B – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 in
C – Router(config)# access-list 101 deny ip host 172.16.161.150 host 172.16.162.163
Router(config)# access-list 101 permit ip any any
D – Router(config)# access-list 101 deny ip 172.16.161.150 0.0.0.255 172.16.162.163 0.0.0.0
Router(config)# access-list 101 permit ip any any
Answer: B C
Question 3
Refer to the exhibit. Why would the network administrator configure RA in this manner?

A. to give students access to the Internet
B. to prevent students from accessing the command prompt of RA
C. to prevent administrators from accessing the console of RA
D. to give administrators access to the Internet
E. to prevent students from accessing the Internet
F. to prevent students from accessing the Admin network
Answer: B
Explanation
Although the access-list is used to “permit” network 10.1.1.0/24 but the best answer here is “to prevent students from accessing the command prompt of RA”. From the picture above, we know that 10.1.1.0/24 is the “Admin” network. This access list is applied to “line vty 0 4″ so it will permit only Telnet traffic from “Admin” to RA while drop all other traffic (because of the implicit “deny all” command at the end of the access list). Therefore we can deduce that it will “prevent students from accessing the command prompt of RA”.
This access list only filters Telnet traffic (because it is applied to vty line) so it will not prevent or allow anyone to access the Internet -> A, D, E are not correct.
C is not correct as this access list allows administrators to access the console of RA.
F is not correct as this access list does not proceed TCP, UDP or IP traffic so the students still access the Admin network.
(Notice that the “command prompt” here implies telnet as telnet is the only way to remotely access RA)
Question 4
An access list was written with the four statements shown in the graphic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?
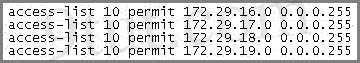
A. access-list 10 permit 172.29.16.0 0.0.0.255
B. access-list 10 permit 172.29.16.0 0.0.1.255
C. access-list 10 permit 172.29.16.0 0.0.3.255
D. access-list 10 permit 172.29.16.0 0.0.15.255
E. access-list 10 permit 172.29.0.0 0.0.255.255
Answer: C
Explanation
Four statements above allow 4 networks (from 172.29.16.0/24 to 172.29.19.0/24) to go through so we can summary them as network 172.29.16.0/22.
/22 = 255.255.252.0 so it equals 0.0.3.255 when converting into wildcard mask -> C is correct.
A, B, D are not correct as their wildcard masks are false. For example:
Answer A allows from 172.29.16.0 to 172.29.16.255
Answer B allows from 172.29.16.0 to 172.29.17.255
Answer D allows from 172.29.16.0 to 172.29.31.255
Both the network address and wildcard mask of answer E are false as it allows the whole major network 172.29.0.0/16 to go through.
Question 5
A network administrator wants to add a line to an access list that will block only Telnet access by the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?
A – access-list 101 deny tcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
B – access-list 101 deny tcp 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
C – access-list 1 deny tcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21
access-list 1 permit ip any any
D – access-list 1 deny tcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23
access-list 1 permit ip any any
Answer: A
Explanation:
First the question asks to block only Telnet access so the port we have to use is 23 -> C is not correct.
Next we need to block traffic from hosts on the subnet 192.168.1.128/28, which is 192.168.1.128 0.0.0.15 if we convert to wildcard mask (just invert all bits of the subnet mask,from 0 to 1 and from 1 to 0 we will get the equivalent wildcard mask of that subnet mask) -> so B is incorrect
In this case, we have to use extended access list because we need to specify which type of traffic (TCP) and which port (23) we want to block -> so D is incorrect because it uses standard access list.
Question 6
As a network administrator, you have been instructed to prevent all traffic originating on the LAN from entering the R2 router. Which the following command would implement the access list on the interface of the R2 router?
A – access-list 101 in
B – access-list 101 out
C – ip access-group 101 in
D – ip access-group 101 out
Answer: C
Question 7
The following access list below was applied outbound on the E0 interface connected to the 192.169.1.8/29 LAN:
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
How will the above access lists affect traffic?
A – FTP traffic from 192.169.1.22 will be denied
B – No traffic, except for FTP traffic will be allowed to exit E0
C – FTP traffic from 192.169.1.9 to any host will be denied
D – All traffic exiting E0 will be denied
E – All FTP traffic to network 192.169.1.9/29 will be denied
Answer: D
Explanation:
There is always an implicit “deny all” command at the end of every access list, so if an access list doesn’t have any “permit” command, it will block all the traffic.
Note: This access list is applied on outbound direction so only packets exiting E0 will be checked. Packets entering E0 will not be checked and they all are allowed to pass through.
Question 8
The access control list shown in the graphic has been applied to the Ethernet interface of router R1 using the ip access-group 101 in command. Which of the following Telnet sessions will be blocked by this ACL? (Choose two)
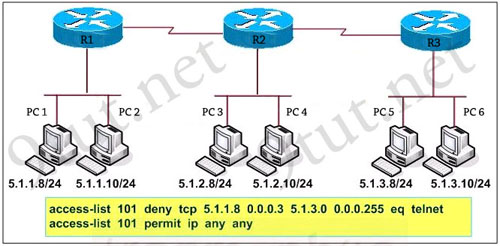
A – from host PC1 to host 5.1.1.10
B – from host PC1 to host 5.1.3.10
C – from host PC2 to host 5.1.2.10
D – from host PC2 to host 5.1.3.8
Answer: B D
Explanation
Below is the simple syntax of an extended access list:
access-list access-list-number {deny | permit} {ip|tcp|udp|icmp} source [source-mask] dest [dest-mask] [eq dest-port]
Notice that this access list is applied to the Ethernet interface of R1 in the “in direction” so in this case, it will filter all the packets originated from E1 network (host PC1 and PC2) with these parameters:
Source network: 5.1.1.8 0.0.0.3 which means 5.1.1.8/252 (just invert all the wildcard bits to get the equivalent subnet mask) -> Packets from 5.1.1.8 to 5.1.1.11 will be filtered.
Destination network: 5.1.3.0 0.0.0.255 which means 5.1.3.0/24-> Packets to 5.1.3.0/24 will be filtered
Therefore packets originated from 5.1.1.8 to 5.1.1.11 and have the destination to the host 5.1.3.x (via Telnet) will be denied.
Question 9
The following configuration line was added to router R1
Access-list 101 permit ip 10.25.30.0 0.0.0.255 any
What is the effect of this access list configuration?
A – permit all packets matching the first three octets of the source address to all destinations
B – permit all packet matching the last octet of the destination address and accept all source addresses
C – permit all packet matching the host bits in the source address to all destinations
D – permit all packet from the third subnet of the network address to all destinations
Answer: A



Hi i have failed ccna twice please help
Have just passed ccna 960/1000. Great website to do revision. Can someone interpret this result score for me. Implenent verify and troubleshoot Nat Acl 50% and implement verify Wan Link 67%. With these two rate i would not be able to get 960/1000. There must be something wrong. I am confident with all sims. I will post my experiences on here tonight
@DNT.. What sims did you complete in the exam? Was it VTP, ALC2 and EIGRP?
@Jamie
Sim VTP, ACL2, Eigrp. there are modiifications. but easy to find.
To All future CCNA Takers
All the dumps and questions on 9 tut are valid. I believed Cisco gives those questions out here for us to learn, revise, and understanding the cisco network before taking exam.
You guys really need to read books and get understanding the network fundamentals then use this web site last. you will be fine and pass exam easily.
I was very nervous and worry alot before taking CCNA. But when i took the exam and found out all the questions from dump and 9tut. 9tut is great because there are a lot of explanation. Some questions from dumps deliberately are wrong in representation and answer because cisco wants to test your knowledge. so you need to justify your answers and knowledge in the exam. Practice alot of time from the dumps because you will not have enough time in the exam if you dont do it at home, particularly for ESL student like me ( English is not my native language). You will not have enough time to analyse the question
It is a great way to learn by posting your problems and question then we are here learning together. Dont ask for valid dump because all the questions are valid you need to ask for your valid knowledge and understanding.
After 10 years driving a truck and now i go back to school to learn this shttttt network at my age. i found myself struggling and hard to cope it. but i prevailed and continue my further education with cisco probably CCNP
Trust me . READ BOOKS and TUTORIAL and THINK then ACTION. YOU WILL BE WINNERs
Good Luck
@Lisa
What are your weakest areas ? Relax and re-read the books then post your problems
Hi Lisa, if CCNA is too much u can try the ICND1/2 approach. It’s what I’m doing now, at least I don’t have to study wireless again for ICND2. But of course it’s always personal preference. If you master sim questions, and the timing, CCNA is always better as it’s one-way ticket to get the qualification.
Hey dude there is problem in q4 the mask is 172.29.16.0 0. 0. 31. 255 this is only coorect
Hi tamilselvan. No 0.0.31.255 is definitely not correct, as 31 in binary is 00011111. As 16 is already taken out and included as base, need only three more IPs, i.e. 00000001 to 00000011 as 1 to 3, so to make up for 16 to 19 in the 3rd octet:
00010000 – 00010011
Therefore in the end only two bits in the 3rd octet needed to be borrowed from the subnet mask, i.e. /24 becomes /22. Converted to wildcard mask it becomes 0.0.3.255
Q1 explanation is incorrect. There are 2 networks each on a /29 mask not one network with a /28 mask as stated.
The answer however remains the same D and E.
In a class C /24 subnet is the subnet address the valid host which can be assigned as an IP address and the broadcast address the next number before the next subnet? Example: 255.255.255.0 = Block size =256-254=2
So it would be in increments of 2 . Right ?
0 being the 1st subnet address, 1 being the broadcast address?
0 first host,1 broadcast address,2 next host,3 next broadcast address so on and so forth.
So when a PC is given the .10 ip add then the next valid host is .12 right?
Hi jfrodo! I’m confused where u get the idea of 254. For /24 mask, the increment is 256, as 256 – 0 – 256
So for example, 192.168.34.56 /24 will have network address 192.168.34.0, broadcast address 192.168.34.255, host range 192.168.34.1 – 192.168.34.254, and the next subnet will be 192.168.35.0 /24.
Don’t have to be a class C address for the /24 mask. I just use it as an example.
Oops stupid typo. I mean 256 – 0 = 256
nice…well done..i’v got a deep knowledge with the explanations…thnx a lot
Q-8 Source network: 5.1.1.8 0.0.0.3 which means 5.1.1.8/252
I think we will have a block size of 4 which will give us only two possible IP addresses. 5.1.1.9 to PC1 and 5.1.1.10 to PC2.
the answer should only be D.
There is no way PC1 would have a subnet IP address configured to its interface.
hi 9tut..
im a little bit confused with Q1
192.168.15.32/ 29 should have the subnet mask of 255.255.255.248 not 255.255.255.240 right?
Hi Elson, you’re thinking 5.1.1.8 is a network address, which is not as it’s with the /24 mask, i.e. PC1 and PC2 are actually under the network 5.1.1.0, with host 5.1.1.1 to 5.1.1.255 The wildcard bit 0.0.0.3 is for summarize the IPs in the access list.
oops it’s getting late I mean host range 5.1.1.1 to 5.1.1.254, with broadcast 5.1.1.255
i am a bit confused about Q7. 1st of all i think access list should be written as follows
access-list 135 deny tcp 192.169.1.8 0.0.0.7 any eq 20
access-list 135 deny tcp 192.169.1.8 0.0.0.7 any eq 21
Any should be first and then eq 20 and 21.
and secondly if you apply outbound on E0 interface it will block the traffic coming from outside not from inside the Lan, so think it should be applied inbound on E0 interface.
Please correct me if i am wrong.thanks
I have understood about the port numbers, they are source port numbers. But still, i think ACL should be applied inbound on E0 interface. Correct me if i am wrong please .thanks
Hi imran! I think u are right. The source IP in the ACL suggests the ACL be applied inbound on E0 interface. However it doesn’t matter in this Q as the lines in the ACL has no effect on the LAN (as it’s wrong direction) and then the implicit deny all command will simply drop the traffic (in this case the incoming traffic towards the LAN)
Hi Alboma! thanks for explanation. What i have understood regarding Q7, traffic coming from lan wont even check this ACL, but traffic coming from outside towards the LAN will check this ACL and all traffic will be dropped (coming from outside) because of implicit deny. Is that right ?
Yes imran, i also think you are correct. Traffic coming from the connected LAN will not be checked since the ACL on E0 outbound. So implicit deny will drop all traffic going out from the E0.
@ice i do agree with you
but maybe someone may clarfy , i think there is an error somewhere because the /29 is correct, bt however the answers seem not to change , whether u increment with 8 or 16
Can someone also help me @ question 1
what do we use for port 21 and 20 just for interest sake
i understand that port 23 is for telnet
@Gushungo
Both ports are used for FTP
port 20 -> data transfer
port 21 -> initiating a connection
or you can search google. always saves the day!
hello
can u guys pls explain me 1 thing…in Q1, they have wildcard bit of 0.0.0.15 ie a subnet mask of 255.255.255.240..which means a value of /28… so why are they using /29 as their subnet mask..if they are using /29 value their wildcard bit shd be 0.0.0.7… is it rite ordo i need more focus??
Explanationto question 1 is incorrect, the increment is 8 not 16. But the answer remain the same
@Shaji-Whales: Could you explain why the increment is 8 not 16?
I think he’s looking at the LAN 192.168.15.32/29. Then the increment is 8. But yes I’m confused too why the access list use wildcard mask 0.0.0.15 instead of 0.0.0.7 if the goal is to deny traffic from 192.168.15.32/29.
Unless, of course, the access list actually deny traffic from BOTH 192.168.15.32/29 and 192.168.15.40/29, as they’re combined into 192.168.15.32 – 192.168.15.48 range, i.e. 192.168.15.32/28. Then the increment is 16. Am I right?
@aJmAL
Define In, Out, Inbound, Outbound, Source, and Destination
This topic is very simple if u draws it from the following scenario
The router uses the terms in, out, source, and destination as references. Traffic on the router can be compared to traffic on the highway. If you were a law enforcement officer in Pennsylvania and wanted to stop a truck going from Maryland to New York, the source of the truck is Maryland and the destination of the truck is New York. The roadblock could be applied at the Pennsylvania–New York border (out) or the Maryland–Pennsylvania border (in). replace with town/cities which u are familiar with.
When you refer to a router, these terms have these meanings.
• Out—Traffic that has already been through the router and leaves the interface. The source is where it has been, on the other side of the router, and the destination is where it goes.
• In—Traffic that arrives on the interface and then goes through the router. The source is where it has been and the destination is where it goes, on the other side of the router.
• Inbound —if the access list is inbound, when the router receives a packet, the Cisco IOS software checks the criteria statements of the access list for a match. If the packet is permitted, the software continues to process the packet. If the packet is denied, the software discards the packet.
• Outbound—if the access list is outbound, after the software receives and routes a packet to the outbound interface, the software checks the criteria statements of the access list for a match. If the packet is permitted, the software transmits the packet. If the packet is denied, the software discards the packet.
The in ACL has a source on a segment of the interface to which it is applied and a destination off of any other interface. The out ACL has a source on a segment of any interface other than the interface to which it is applied and a destination off of the interface to which it is applied.
I just hope that u will grasp one or two things from this scenario.
9tut help me if I am giving this man poison
@9tut
Thnks 4yo valuable website, ques, answers & explanations
Hie all aspiring CCNA network engineers and already in the field?
Can any one send me the vce engine software (Visual CertExam Suite) and dumbs from collision 486q by Jericho 632q or Bruce 564q by DHAKANI 615Q. I tried to google the vce engine, but got a trial version which only exhibited five questions.
My id is musinawellaz@gmail.com
Pliz help- I am preparing for ccna final exam on this month end (August 2012),so pliz again send me latest dumbs from collision 486q by Jericho 632q or Bruce 564q by DHAKANI 615Q.
can you use any any on the exam
Can any one tell me regarding Q5.
In the explanation its said that D is incorrect because it is not an extended ACL. Please explain at arjun.upadhya@yahoo.com. Thanks
I notice the answers A and E in Q3 contradict each other. In this situation, I think students will have access to the Internet, as the access list only check telnet traffic. So answer A is right also. But the best answer will have to be B giving the explanation.
@ Question 3.
We are given 2 networks 10.1.2.0 and 10.1.1.0 and an access-list 2 permit 10.1.1.0 0.0.0.255.
With the given wild card mask also not include the 10.1.2.0 network?
If it does then lets look at the answer again.
@9tut
@ Question 3.
We are given 2 networks 10.1.2.0 and 10.1.1.0 and an access-list 2 permit 10.1.1.0 0.0.0.255.
With the given wild card mask also not include the 10.1.2.0 network?
If it does then lets look at the answer again. Thanks.
@Eugene: The wildcard mask 0.0.0.255 only allows 10.1.1.0 network, not 10.1.2.0 network -> Therefore 10.1.2.0 network will not be permitted.
@9tut
Thanks
I agree with Elson on Q8
9tut, please give your feedback on Question 8. Thank you.
Im confused about the implicit deny rule does it only apply to an
access list that has a deny statement or does the implicit deny happen after a permit acl statement?
@Jfrodo: It applies to all access lists.
@Elson, @Klauss: 5.1.1.8/30 is a network address but 5.1.1.8/24 is not. So in this case 5.1.1.8/24 is also filtered out.
Re q8
An access-list is just a list. The list has specifics for particular addresses or ranges of addresses that need to be filtered or are of interest.
What if in the case of Q8 you only want to filter a group of addresses from 5.1.1.8/24 but not the whole subnet?
Then you would specify on your list ;deny tcp 5.1.1.8 0.0.0.3 meaning addresses 5.1.1.8,.9,.10,.11 only.
0.0.0.3 is not a subnet mask, its a wildcard mask used in this context to denote the forgoing.
@jfrodo
Implicit deny applies to all access list but it is only applied if the interface has an access list applied to it in a particular direction. There will be no implicit deny on an Fa0/1 port if only Fa0/2 port is configured with an access list. Likewise no implicit deny on Fa0/1 out if only Fa0/1 in has acceess-list configured. Access-list is applied per interface, per direction.
Please correct if im wrong.
Hi there, please help with this question that I just found in Pass4sure:
A network administrator is configuring ACLs on a Cisco router, to allow traffic from hosts on networks 192.168.146.0, 192.168.147.0, 192.168.148.0 and 192.168.149.0 only. Which 2 ACL statements, when combined, are the best for accomplishing this task? (Choose 2)
A) access-list 10 permit ip 192.168.146.0 0.0.0.255
B) access-list 10 permit ip 192.168.146.0 255.255.255.0
C) access-list 10 permit ip 192.168.147.0 0.255.255
D) access-list 10 permit ip 192.168.149.0 0.0.255.255
E) access-list 10 permit ip 192.168.148.0 0.0.1.255
F) access-list 10 permit ip 192.168.146.0 0.0.1.255
VALID OPTIONS: E and F
Tx.
Hey Al
What they did for the answer for this was basically take the supernet of the 4 networks and split it up into 2 access lists.
Answer A is wrong because if you notice the networks are increasing in the third octet, so a wildcard mask of 0.0.0.255 would mean that only bits in the 4th octet can be variable.
Answer B is wrong because it is not using a valid wildcard mask, that is the subnet mask of a /24 network
Answer C seems like it could be right, however the wildcard mask is saying that only the first 2 octets must match, the third and forth octets are allowed all ranges of addresses, that is a huge range of addresses, we only want to isolate 4.
Answer D is the same as C, just with a different starting address.
Answer E is correct because by saying 0.0.1.255 (which is a /23) we are saying that we will allow 192.168.148.0 – 192.168.149.255, which is withing our range that we want to allow.
Answer F is also correct because like previously 0.0.1.255 is saying that we will allow network range 192.168.146.0 – 192.168.147.255
An easier way to do this in real life would be to supernet the range of addresses to a 192.168.146.0 255.255.252.0 (/22) and right the ACL list like:
Access-list 10 permit IP 192.168.146.0 0.0.0.3.255
This would mean 192.168.146.0 – 192.168.149.255
But its cisco and they want you to understand what wildcard masks do and what they mean. It’s important to understand that the wildcard mask is specifying a range of addresses. The wildcard mask will always be one less then the block size in its respective octet. 0.0.1.255 means a blocksize of 2 in the third octet.
If its still a little unclear, ICND or CCNA prep books are going to be your best source to learn and understand wildcard masks
I hope this helps.
Hi Malkontent, thanks for your reply. I agree on your comment when you say that the easiest way of achieving this would be by setting this up:
Access-list 10 permit IP 192.168.146.0 0.0.0.3.255
This would mean 192.168.146.0 – 192.168.149.255
But there is something that is not clear to me yet, what do you mean by this? ” The wildcard mask will always be one less then the block size in its respective octet. 0.0.1.255 means a blocksize of 2 in the third octet.”
Thanks.
DID IT!!…907…thx 9tut!!!!..CCNA certified….tons of questions from this site…read from top to bottom every question, because you will not know what pops up….q1 on exam..