CCNA – Access List Questions
Here you will find answers to CCNA Access list questions
Note: If you are not sure about how to use Access list, please read my Access list tutorial
Question 1
Your boss is learning a CCNA training course, refer to the exhibit. The access list has been configured on the S0/0 interface of router RTB in the outbound direction. Which two packets, if routed to the interface, will be denied? (Choose two)
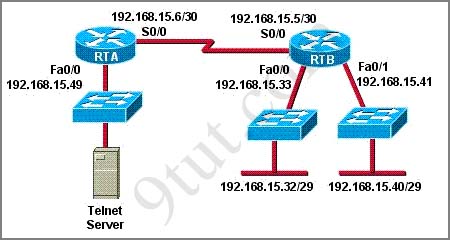
access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet
access-list 101 permit ip any any
A. source ip address: 192.168.15.5; destination port: 21
B. source ip address: 192.168.15.37 destination port: 21
C. source ip address: 192.168.15.41 destination port: 21
D. source ip address: 192.168.15.36 destination port: 23
E. source ip address: 192.168.15.46; destination port: 23
F. source ip address: 192.168.15.49 destination port: 23
Answer: D E
Explanation
First we notice that telnet uses port 23 so only D, E & F can satisfy this requirement.
The purpose of this access-list is to deny traffic from network 192.168.15.32 255.255.255.240 (to find out the subnet mask just convert all bit “0″ to “1″ and all bit “1″ to “0″ of the wildcard mask) to telnet to any device. So we need to figure out the range of this network to learn which ip address will be denied.
Increment: 16
Network address: 192.168.15.32
Broadcast address: 192.168.15.47
-> Only 192.168.15.36 (Answer D) & 192.168.15.46 (Answer E) belong to this range so they are the correct answer.
Question 2
Refer to the graphic. It has been decided that PC1 should be denied access to Server. Which of the following commands are required to prevent only PC1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two)
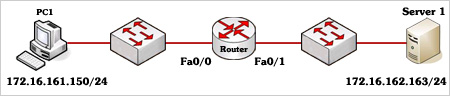
A – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 out
B – Router(config)# interface fa0/0
Router(config-if)# ip access-group 101 in
C – Router(config)# access-list 101 deny ip host 172.16.161.150 host 172.16.162.163
Router(config)# access-list 101 permit ip any any
D – Router(config)# access-list 101 deny ip 172.16.161.150 0.0.0.255 172.16.162.163 0.0.0.0
Router(config)# access-list 101 permit ip any any
Answer: B C
Question 3
Refer to the exhibit. Why would the network administrator configure RA in this manner?

A. to give students access to the Internet
B. to prevent students from accessing the command prompt of RA
C. to prevent administrators from accessing the console of RA
D. to give administrators access to the Internet
E. to prevent students from accessing the Internet
F. to prevent students from accessing the Admin network
Answer: B
Explanation
Although the access-list is used to “permit” network 10.1.1.0/24 but the best answer here is “to prevent students from accessing the command prompt of RA”. From the picture above, we know that 10.1.1.0/24 is the “Admin” network. This access list is applied to “line vty 0 4″ so it will permit only Telnet traffic from “Admin” to RA while drop all other traffic (because of the implicit “deny all” command at the end of the access list). Therefore we can deduce that it will “prevent students from accessing the command prompt of RA”.
This access list only filters Telnet traffic (because it is applied to vty line) so it will not prevent or allow anyone to access the Internet -> A, D, E are not correct.
C is not correct as this access list allows administrators to access the console of RA.
F is not correct as this access list does not proceed TCP, UDP or IP traffic so the students still access the Admin network.
(Notice that the “command prompt” here implies telnet as telnet is the only way to remotely access RA)
Question 4
An access list was written with the four statements shown in the graphic. Which single access list statement will combine all four of these statements into a single statement that will have exactly the same effect?
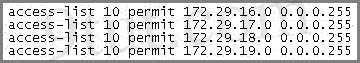
A. access-list 10 permit 172.29.16.0 0.0.0.255
B. access-list 10 permit 172.29.16.0 0.0.1.255
C. access-list 10 permit 172.29.16.0 0.0.3.255
D. access-list 10 permit 172.29.16.0 0.0.15.255
E. access-list 10 permit 172.29.0.0 0.0.255.255
Answer: C
Explanation
Four statements above allow 4 networks (from 172.29.16.0/24 to 172.29.19.0/24) to go through so we can summary them as network 172.29.16.0/22.
/22 = 255.255.252.0 so it equals 0.0.3.255 when converting into wildcard mask -> C is correct.
A, B, D are not correct as their wildcard masks are false. For example:
Answer A allows from 172.29.16.0 to 172.29.16.255
Answer B allows from 172.29.16.0 to 172.29.17.255
Answer D allows from 172.29.16.0 to 172.29.31.255
Both the network address and wildcard mask of answer E are false as it allows the whole major network 172.29.0.0/16 to go through.
Question 5
A network administrator wants to add a line to an access list that will block only Telnet access by the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?
A – access-list 101 deny tcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
B – access-list 101 deny tcp 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
C – access-list 1 deny tcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21
access-list 1 permit ip any any
D – access-list 1 deny tcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23
access-list 1 permit ip any any
Answer: A
Explanation:
First the question asks to block only Telnet access so the port we have to use is 23 -> C is not correct.
Next we need to block traffic from hosts on the subnet 192.168.1.128/28, which is 192.168.1.128 0.0.0.15 if we convert to wildcard mask (just invert all bits of the subnet mask,from 0 to 1 and from 1 to 0 we will get the equivalent wildcard mask of that subnet mask) -> so B is incorrect
In this case, we have to use extended access list because we need to specify which type of traffic (TCP) and which port (23) we want to block -> so D is incorrect because it uses standard access list.
Question 6
As a network administrator, you have been instructed to prevent all traffic originating on the LAN from entering the R2 router. Which the following command would implement the access list on the interface of the R2 router?
A – access-list 101 in
B – access-list 101 out
C – ip access-group 101 in
D – ip access-group 101 out
Answer: C
Question 7
The following access list below was applied outbound on the E0 interface connected to the 192.169.1.8/29 LAN:
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 20 any
access-list 135 deny tcp 192.169.1.8 0.0.0.7 eq 21 any
How will the above access lists affect traffic?
A – FTP traffic from 192.169.1.22 will be denied
B – No traffic, except for FTP traffic will be allowed to exit E0
C – FTP traffic from 192.169.1.9 to any host will be denied
D – All traffic exiting E0 will be denied
E – All FTP traffic to network 192.169.1.9/29 will be denied
Answer: D
Explanation:
There is always an implicit “deny all” command at the end of every access list, so if an access list doesn’t have any “permit” command, it will block all the traffic.
Note: This access list is applied on outbound direction so only packets exiting E0 will be checked. Packets entering E0 will not be checked and they all are allowed to pass through.
Question 8
The access control list shown in the graphic has been applied to the Ethernet interface of router R1 using the ip access-group 101 in command. Which of the following Telnet sessions will be blocked by this ACL? (Choose two)
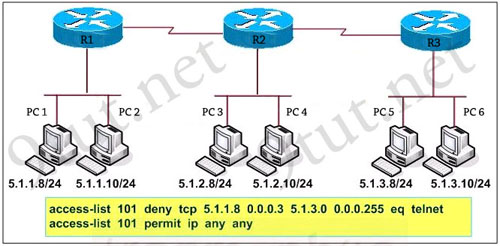
A – from host PC1 to host 5.1.1.10
B – from host PC1 to host 5.1.3.10
C – from host PC2 to host 5.1.2.10
D – from host PC2 to host 5.1.3.8
Answer: B D
Explanation
Below is the simple syntax of an extended access list:
access-list access-list-number {deny | permit} {ip|tcp|udp|icmp} source [source-mask] dest [dest-mask] [eq dest-port]
Notice that this access list is applied to the Ethernet interface of R1 in the “in direction” so in this case, it will filter all the packets originated from E1 network (host PC1 and PC2) with these parameters:
Source network: 5.1.1.8 0.0.0.3 which means 5.1.1.8/252 (just invert all the wildcard bits to get the equivalent subnet mask) -> Packets from 5.1.1.8 to 5.1.1.11 will be filtered.
Destination network: 5.1.3.0 0.0.0.255 which means 5.1.3.0/24-> Packets to 5.1.3.0/24 will be filtered
Therefore packets originated from 5.1.1.8 to 5.1.1.11 and have the destination to the host 5.1.3.x (via Telnet) will be denied.
Question 9
The following configuration line was added to router R1
Access-list 101 permit ip 10.25.30.0 0.0.0.255 any
What is the effect of this access list configuration?
A – permit all packets matching the first three octets of the source address to all destinations
B – permit all packet matching the last octet of the destination address and accept all source addresses
C – permit all packet matching the host bits in the source address to all destinations
D – permit all packet from the third subnet of the network address to all destinations
Answer: A



Hi guys am taking my exam soon. Can someone help me with the latest dumps plsss..
Thanks
spitfire2507@hotmail.com
hi all am writing my ccna exam on 30th june. pls i need the latest dumps.
thanks
leksinblack@yahoo.com
hey guys,
thanks so much for the info. i’m taking the ccna exam on 24th of June please i need the latest dumps
kindly send to meetnosy@yahoo.com
thanks all
Almost ready to take exam in July 2011, but a little afraid what the questions are going to be and I don’t have much money. Could someone please send me the latest dumps, pass4sure etc? I will pay for a portion of the material since you already spent the money.
Thanks
mmonteiro@4-ens.com
Hi guys , i am ready for taking the test but plzzzzzzzz sen me latest dumps on m_bilal056@yahoo.com
send me the latest dump plzzzz…i am planing to take the exam in 2 weeks…help me plzzz……..my email ismohamadfaahdil@hotmail.com
mohamadfaahdil@hotmail.com
Please help a girl taking SSNA in two weeks and send me the latest dumps!
irena_rs@yahoo.com
Thanks a lot to everybody!
Dear All,
Kindly provide latest dumps for ccna, because im going to attempt this next wek inshAllah
pieces_genius@yahoo.com
can i ask for a new dump also off ccna exam? kindly email me on edey_18@yahoo.com thank
can i ask for a new dump also of ccna exam? kindly email me on edey_18@yahoo.com thanks
Dear All,
I will be taking CCNA exam tomorrow, i would really appreciate if any can assist me with latest dump before the end of today.
Thanks so much…..
God Bless you all.
@ 9tut
Q1 it should be D only why did you choose D and E
@do: Both 192.168.15.36 & 192.168.15.46 belong to network “192.168.15.32 0.0.0.15″ (from 192.168.15.32 -> 192.168.15.47) so they are both correct.
I had a problem with Q1 also. I had to redo my math 3 times before it made sense. What’s the quickest method for calculating ranges with wildcard masks?
I’m also taking my test next week, if anyone has any material they can share my mail is zack80cj7@yahoo.com.
Thanks
Which two statements apply to dynamic access lists?(choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: CD
please help wether the answers are correct
please help me for latest dump or any new update i am going to attempt 640-802 at 15th July
lot of thank if any any body help by giving pass4sure latest dumps
please help me for latest dump or any new update i am going to attempt 640-802 at 15th July
lot of thank if any any body help by giving pass4sure latest dumps
my email is adeel519@hotmail.com
Hi Abeel
this is my Email Address Mohamed.ahh@hotmail.com
send me an Email to send you latest Dumps
@9tut
Which two statements apply to dynamic access lists?(choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: CD
please help wether the answers are correct
Hi passed my CCNA exam today with the score of 933…thanx to 9tut.com.
Hi guys,
I am planning to give CCNA exam in next week.
So please pass me latest dums along with latest simulation on my email address
My email address is yogendramodak@yahoo.com
Please help me guys. :-)
Thanks so much!
Benefits of Dynamic ACLs
Dynamic ACLs have the following security benefits over standard and static extended ACLs:
Use of a challenge mechanism to authenticate individual users.
Simplified management in large internetworks.
In many cases, reduction of the amount of router processing that is required for ACLs.
Reduction of the opportunity for network break-ins by network hackers.
Creation of dynamic user access through a firewall, without compromising other configured security restrictions.
A network administrator wants to add a line to an access-list that will block only Telnet access by the host on subnet 192.168.1.128/28 to the ser at 192.168.1.5 .what command sholud be issued to accomplish this task?
A.access-list 101 deny tcp 192.168.1.128.0.0.0.15 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
B.access-list 101 deny tcp 192.168.1.128.0.0.0.240 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
C.access-list 101 deny tcp 192.168.1.128.0.0.0.255 192.168.1.5 0.0.0.0 eq 23
access-list 101 permit ip any any
D.access-list 101 deny tcp 192.168.1.128.0.0.0.15 host 192.168.1.5 eq 23
access-list 101 permit ip any any
Ans.A but I think it is D
which one is correct?
Hi Guys,
I will be taking CCNA exam next week, i would really appreciate if any can assist me with latest dump .My email is nikos_g_s@hotmail.com
Thanks so much!!!!!!!!
Kamal,
You have read the question wrong.
Answer D is incorrect because in the question it uses access-list 1
Extended access-list always start 100 – 199, other than that, the rest of the statement is correct.
Look at the question again
Zak,
Remember that the quickest way to calculate wildcard from subnet mask is to subtract each octet from 255.
e.g. A subnet mask of 255.255.240.0 (subtract each octet from 255) gives wild card of 0.0.15.255
which command shows the mac addresses of stations connected to switchport
-a- show mac-address
-b- show arp
plz tell me which one is the right answer bcos there are two different answers from two different dumps but both are from ACME
plz help
a host is sending packet to another host on a different network , what is the first action that the anding host will take
-a- send the data frames to the default gate-way
-b- create an arp request to get the mac address of the recieving host
plz tell me which one is the right answer bcos there are two different answers from two different dumps but both are from ACME
plz help
Hello Networkers!!!
pls help me for CCNA exam which will be taken on within next week…
send me latest dumps to vikudonald@yahoo.com
i will be grateful for u all for the same….
Regards
@dinesh
“Which two statements apply to dynamic access lists?(choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: CD
please help wether the answers are correct”
That answer is wrong!
Lock and key, also known as dynamic ACLs, was introduced in Cisco IOS Software Release 11.1. This feature is dependent on Telnet, authentication (local or remote), and extended ACLs.
Lock and key configuration starts with the application of an extended ACL to block traffic through the router. Users that want to traverse the router are blocked by the extended ACL until they Telnet to the router and are authenticated. The Telnet connection then drops and a single-entry dynamic ACL is added to the extended ACL that exists. This permits traffic for a particular time period; idle and absolute timeouts are possible.
The correct Answers are: D and F
Allowing packets to be filtered based on upper-layer session information is a characteristic of Reflexive Access Lists. Reflexive ACLs allow IP packets to be filtered based on upper-layer session information. They are generally used to allow outbound traffic and to limit inbound traffic in response to sessions that originate inside the router. So answer C is incorrect!!!
@denish
if you dont know that one you should never apply to a Cisco certification exam. You dont know shit about networking mate and you give us people who are certified a bad name! Those are basics of the basics of networking, if you dont know that, you shouldn’t even go for any networking exam!
Btw, the first action depends on the arp table of the sending host, if the host already has the destination mac address of the gateway associated with that ip address, it sends it right away to the default gateway, if it doesn’t have that mac address, it will first create an Address Resolution Protocol request to find out if that ip address is in the same network segment.
Answer is B
heiio guys. m writing ccna on july 22.can someone pliz send me latest dumps and tips to namataikanyai@yahoo.com
gv_anjania@yahoo.com …latest dumps plz …thx in adv
can someone please email the latest dump to me at nikos_g_s@hotmail.com..thanks!!!!
I hope to sit for the CCNA Exam at the beginning of aug.
Can anybody give me suggestion how to prepare for it?
if somebody has the latest dump please email me at tohin_s@yahoo.com
also want to ask the latest dump… plss help me to.. thank you very much.. romeojr.lazarte@yahoo.com
thaks 9tut >>>>>>>>>>>>>> u r really amazing fourm
::::)
if eny 1 has the latest dump ==========> just send it to
amz_ahmad@yahoo.com
TIS_640-802_v21.24_436Q practice all the question at this dumps, it still valid…
Hi, i will pass my exam in 2 days. could someone advices me how to proceed to be more confident? I’m totally scared!
I lost ccna first time with 815/1000. I didn’t know that when you pass to the next question, you can’t return to the previous one.
So thake care!
Guys please read Acl2 Sim. I pass exam today and it was.
Acceess-list 100 permit TCP Host B Host C eq 80
Access-list 100 deny ip Host B
Permit any any
I got 100% on it so use Permit Ip any any
Access-list 100 deny ip Host C
Hello Dear All,
How are you and i hope be fine and have enjoyable time at your life, Dear Ahmad Helmy, i would like to have this exam next week could you please share your valid dumps with me? it really make me happy, and thankful,
ID: AbdulAhmad.barakzi@yahoo.com
i have question that, all the Sims coming the same as its in there? i mean like there just ansawr the question or need to configureation each question? i hope to find reply from all of you about it,
Sincerely,
AHB
my exam is coming up on 28 July 2011. pls i need latest dumps from you all. thanks
send to maxine.botes@yahoo.com
Hi cris,
where do you download the dump “TIS_640-802_v21.24_436Q” ?
thanks
pls can someone help me with the latest dumps on ccna
Help:I wanna know when to use inbound and outbound because I read that inbound is associated with standard access list but even on extended I read that it could be used! How do you tell when to use one?
pls can you send me the latest dumps Sena000912@yahoo.com