CCNA EIGRP LAB Question
Question
After adding R3 router, no routing updates are being exchanged between R3 and the new location. All other inter connectivity and Internet access for the existing locations of the company are working properly.
The task is to identify the fault(s) and correct the router configuration to provide full connectivity between the routers.
Access to the router CLI can be gained by clicking on the appropriate host. All passwords on all routers are cisco.
IP addresses are listed in the chart below.

| R1 Fa0/0: 192.168.77.33 S1/0: 198.0.18.6 S0/1: 192.168.60.25 S0/0: 192.168.36.13 |
R2 Fa0/0: 192.168.60.97 Fa0/1: 192.168.60.113 S0/0: 192.168.36.14 |
| R3 Fa0/0: 192.168.77.34 Fa0/1: 192.168.60.65 Fa1/0: 192.168.60.81 |
R4 Fa0/0: 192.168.60.129 Fa0/1: 192.168.60.145 S0/1: 192.168.60.26 |
Answer and explanation
(Note: If you are not sure how EIGRP works, please read my EIGRP tutorial: http://www.9tut.com/eigrp-routing-protocol-tutorial. Note: You can download this sim to practice here: http://www.9tut.com/download/9tut.com_CCNA_EIGRP_sim_question.zip)
We should check the configuration of the new added router first because it does not function properly while others work well. From the command line interface of R3 router, enter the show running-config command

From the output above, we know that this router was wrongly configured with an autonomous number (AS) of 22. When the AS numbers among routers are mismatched, no adjacency is formed.
(You should check the AS numbers on other routers for sure)
To solve this problem, we simply re-configure router R3 with the following commands:
R3>enable (you have to enter cisco as its password here)
R3#configure terminal
R3(config)#no router eigrp 22
R3(config)#router eigrp 212
R3(config-router)#network 192.168.60.0
R3(config-router)#network 192.168.77.0
R3(config-router)#no auto-summary
R3(config-router)#end
R3#copy running-config startup-config
Check R1 router with the show running-config command:
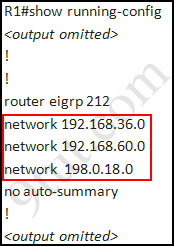
Notice that it is missing a definition to the network R3. Therefore we have to add it so that it can recognize R3 router
R1>enable (you have to enter cisco as its password here)
R1#configure terminal
R1(config)#router eigrp 212
R1(config-router)#network 192.168.77.0
R1(config-router)#end
R1#copy running-config startup-config
Now the whole network will work well. You should check again with ping command from router R3 to other routers!
Modifications:
Maybe in this EIGRP Sim you will see the “passive-interface …” command somewhere in R1 configuration. If the link between R1 to R2; or R1 to R3; or R1 to R4) routers has the “passive interface” then we have to remove it with the “no passive-interface …” command because it prevents EIGRP update from being sent on that interface. But if the “passive interface” is applied to the link between R1 and ISP router like this:
R1:
!
router eigrp 212
passive-interface s1/0
!
then we just leave it. Don’t use the “no passive-interface s1/0″ on R1 because the link between R1 & ISP doesn’t need EIGRP to run on it. A static route from R1 to ISP & “ip default-network” command in R1 are correct so that all the routers (R1, R2, R3, R4) can access the Internet.
(Note: The “ip default-network” command in R1 will advertise the static route of R1 (to go to the Internet) to other routers (R2,R3,R4) so that they can access the Internet too). In the exam you will see these lines in R1 configuration:
!
ip default-network 198.0.18.0
ip route 0.0.0.0 0.0.0.0 198.0.18.5
!
If you want to learn more about “ip default-network” command please read: http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a0080094374.shtml
I read recent comments and realized that you will see the “passive-interface” in the link between R1 & ISP router so just leave it.
Note: Also some readers confuse about if we should use the wildcard masks on the “network” statements under EIGRP process or not. For example should we use:
router eigrp 212
network 192.168.77.0 0.0.0.3
The answer is: we can use wildcard masks or not, it does not matter. Not having a wildcard mask does not make the routes conflicting. The “network …” command in EIGRP (and OSPF, RIP) does not means “advertise this network” but means “If I has interface(s) belongs to this network please turn on EIGRP on that interface. Therefore when you don’t use wildcard mask EIGRP will turn on EIGRP on all interfaces that belongs to the network you specify in the “network …” command.
You should only use wildcard mask on EIGRP if you have 2 or more interfaces that belong to the same major networks but you don’t want to run EIGRP on all of them. For example if your router has 2 interfaces whose IP addresses are 192.168.30.1/28 and 192.168.30.17/28 but you only want to run EIGRP on the first interface, you can type “network 192.168.30.0 0.0.0.15″ under EIGRP process.
Other lab-sims on this site:
CCNA Configuration SIM Question (RIPv2 SIM)



hi Sam did u get same labs???
i mean ,eigrp,acl,???
Taken the exam today. Labs ACL2, EIGRP, VTP. Thanks to all the community and good luck future test takers!
guys i heard the exam of ccan will be change first of JUNE any idea .. u can contact me on skype mohauk-88
Dear All,
I cleared this exam on 21st of May. You only need to prepare spike with full understanding of Subnetting. Labs were EIGRP, ACL2 and VTP. I prepared for this exam for whole 4 months and listened complete CBT Nuggets of ICND1 & ICND2, Sekhar and Spike Dumps.
Hello I took exam and the exam on this sim is a lot different. I was so confused. Study and no concepts because the way they have the sim is not really like the above layout.
*notice that sometimes you MIGHT get an interface Administratively down, you should check carefully the status of interfaces specially on the new router added, use the: “no shutdown”
*Academy wont be available after After 30 June 2013 because new CCNA 200-201 coming out which concentrate on IPV6… if you are doing the 640-802 try finish it before en of October 2013.
*about new announcement of CISCO making a new version of EIGRP which will be compatible in all vendors!!!!! YES all vendors, BUT questions should be answered as EIGRP is cisco propriety as mentions in the curriculum. I think it will be changed on the new CCNA 200-201
* relax, dont panic and think, they will throw at you all kind of tricks so ready carefully, and remember you are going against the clock :)
PD: mentioned above are advices from teachers not all mentioned are my words, my exam is due on the 27 of May, wish me best of luck!
forgot to mention, 9tut.com really deserve donations… so it keep going.
we are all thankful for the great help 9tut does offer!
Took the exam yesterday passed. Lab sims ACL2, VTP, EIGRP, Couldn’t get the routers talking to the ISP router in EIGRP sim, don’t know why. But pretty much all the question were from 9tut. With basic understanding of both the ICNDs and practicing through 9tut is the key, 95% questions from 9tut. Best of luck to everyone who is taking the test ! And thanks 9tut.
In the .pkt file attached, Router R1 is missing network 192.168.77.0. Pls add that to have the network properly. Thanks
how did the exam go CaZa
Done it… 960/1000 :) thanks to 9tut.com and spike.
got EIGRP, ACL2 and VTP! (eigrp straight forward no complications)
I wish you guys best of luck
Alhamdulillah!!! I passed my CCNA last day (27 May 2013). The sim came out during exam were VTP Sim, EIGRP Sim, and ACL Sim. Thx to 9tut.com and spike dump. Thx alot!!!!!!
I think a colleague of mine and I figured out why I didn’t get full credit for the EIGRP sim. I only got a 67% on this sim and did it exactly like the one here on 9tut but what I didn’t do was to set the two ethernet ports to passive-interface on the router I was adding. On this forum there is alot of discussion about not needing to worry about the interface connected to the ISP but I didn’t pay attention to the ethernet ports going directly to the host pc’s. The router and the host pc’s would not exchange routing information and therefore those interfaces need to be set to passive.
Hope that helps someone to get full credit, can’t believe I missed that.
Are you sure we need to set these fastethernet ports into passive mode ?
@ Wayner, another way to miss out on points even if you are spot on is if you don’t copy Running to Start config.
Always always during NA exams save running config or lose points.
thnxxxxxx .. i’m really appreciated that ..
So, do you think that we dont need to set the 2 fast ethernet interfaces into passive mod ein the EIGRP configuration ?
@thxx kram .. guys tomorrow on 30-5 my exam .. any new idea about passive-interface or the exam will be like tut9 .
Passed today 947
thanks 9tut, labs were ACL2, VTP and EIGRP (only the AS has to be changed)
Thanks
Hi guyz… passed today with 986… spike dump & 9tut is spot on! Take a bow guyz! :)
Some changes you might face in the exam:
1. EIGRP: Dont worry too much… only the AS number was changed & a wrong network in R1…
2. VTP: Switch X was server, Switch C was client… Configuration revision is higher in X.. So it will replace all the existing VLANs of Switches…
3. ACL2: Permit IP any any is correct even when public server IP add is provided.
4. Options aren’t in the same order as the dump.. so dont just memorise, try to understand it too… Some IP address might change…
5. in some cases, “Tab” key doesnt work… but “?” does, So dont panick! just type it seeing the options…..
its really easy guyz… have solid prep & go for it… Best of luck…. :)
Hi guys!! Can someone share with me those spike dumps? I will take the test this 10th
!! thanks!!! jockrlos16@hotmail.com
Hi guys!! Can someone share with me those spike dumps? i will take the test on july
shariq898@hotmail.com
You can get the spike dump from exam collection site.
hello everybody , i passed today in the ccna exam with 947/1000 ….. thanks God
3 question drag & drop and 3 sim question ( eigrp , acl2 , vtp )
very easy but u must prepare well before u take the exam
Hey Guys, the lab i see here dates back to last year. Is it still valid?
i think its easy but i’m so worry from Acl & Vtp could u help me please
Can someone please tell me why i cant open the sim files.
It keeps saying not compatible with the version of packet tracer.
I installed 5.1 , 5.2 , and 5.3
please help
hi guys,
Can anyone send me the spike dumps? harthartster@gmail.com
Thank you!
I have the ame issue and i am running PT v5.3
Hi Everyone.
May we know what is the real answer in the question stated below:
- Which of the following is a characteristic of full-duplex communication?
A. It is a CSMAICD network
B. It is a CSMAICA network
C. It is point-to-point network
D. Hub commucication is done via full duplex
Is the answer in real exam C or D?
Please help me on this. Thanks guys in advance :)
@robert the answer is d.
Hi all, I have passed the exam today[894/1000]. Want to thanks 9tut very highly and Abhishek Tutor, Todd, Spike a lot…..
use 9tut only last 2days before exam. sure u can score 1000/1000. if dedicated.
Guys why is the wildcard card mask not used on with eigrp network statements. Why is it using the classful network? Should I just do it 9tut’s way on the ccna?
Just confirm me, if we revise the question of 9tut, it will be easy to succeed the test?
Understand and study the question,practise is a good method?
We don’t have the time to analyse the question. Just be sure.
(It take a long time just to read the 2book and after that study)
Please, can you give me an answer?
@Robert and @Bam, The Hub runs at Half-duplex only and There are exactly two stations connected with a full-duplex point-to-point link. Since there is no contention for use of a shared medium, the multiple access algorithms (i.e., Carrier Sense with Multiple Access and Collision Detect, or CSMA/CD) are unnecessary
So, The answer is C
The sim is not working with PT 5.3.2.0027
“Invalid File” “is not compatible with this version of Packet Tracer.”
Any ideas?
@luu: Please use Packet Tracer v5.3.3.0019 or above to open it.
Can anybody tell me how many lab sims questions are there in CCNA test? Is it the only EIGRP lab sim question here? Thanks!!
@Dave: You can read more sims here: http://www.9tut.com/category/ccna-lab-sim
@9tut: Perfect, thanks!
After adding -
R1(config-router)#network 192.168.77.0
There isnt a ‘no auot-summary’ why is that?
I will pass the CCNA exam tomorrow!! Thank you Lord…
So for the EIGRP sim, am I to understand that we do NOT need to add the following statements to R1:
a) passive-interface s1/0 after the router eigrp 212 line
b) ip route 0.0.0.0 0.0.0.0 198.0.18.5
for you grettle, this is straight from Cisco’s IOS IP Command Reference, (just do a google search no passive interface if you want to check): Download this chapter
EIGRP CommandsEIGRP Commands
Download the complete book
Book-level PDF: Cisco IOS IP Command Reference, Volume 2 of 3: Routing Protocols, Release 12.2Book-level PDF: Cisco IOS IP Command Reference, Volume 2 of 3: Routing Protocols, Release 12.2 (PDF – 5 MB) Feedback Table Of Contents
EIGRP Commands
auto-summary (EIGRP)
clear ip eigrp neighbors
default-information
default-metric (EIGRP)
distance eigrp
distribute-list in (RIP, IGRP, EIGRP)
distribute-list out (RIP, IGRP, EIGRP)
eigrp log-neighbor-changes
eigrp log-neighbor-warnings
eigrp router-id
eigrp stub
ip authentication key-chain eigrp
ip authentication mode eigrp
ip bandwidth-percent eigrp
ip hello-interval eigrp
ip hold-time eigrp
ip split-horizon eigrp
ip summary-address eigrp
metric weights (EIGRP)
neighbor (EIGRP)
network (EIGRP)
offset-list (EIGRP)
router eigrp
set metric (EIGRP)
show ip eigrp interfaces
show ip eigrp neighbors
show ip eigrp topology
show ip eigrp traffic
timers active-time
traffic-share balanced
variance (EIGRP)
EIGRP Commands
——————————————————————————–
Use the commands in this chapter to configure and monitor Enhanced Interior Gateway Routing Protocol (EIGRP). For EIGRP configuration information and examples, refer to the “Configuring IP EIGRP” chapter of the Cisco IOS IP Configuration Guide.
auto-summary (EIGRP)
To restore the default behavior of automatic summarization of subnet routes into network-level routes, use the auto-summary command in router configuration mode. To disable this function and send subprefix routing information across classful network boundaries, use the no form of this command.
auto-summary
no auto-summary
Syntax Description
This command has no arguments or keywords.
Defaults
The behavior of this command is enabled by default (the software summarizes subprefixes to the classful network boundary when crossing classful network boundaries).
Command Modes
Router configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
Route summarization reduces the amount of routing information in the routing tables.
By default, Border Gateway Protocol (BGP) does not accept subnets redistributed from an Interior Gateway Protocol (IGP). To advertise and carry subnet routes in BGP, use an explicit network command or the no auto-summary command. If you disable automatic summarization and have not entered a network command, you will not advertise network routes for networks with subnet routes unless they contain a summary route.
Enhanced Interior Gateway Routing Protocol (EIGRP) summary routes are given an administrative distance value of 5. You cannot configure this value.
Routing Information Protocol (RIP) Version 1 always uses automatic summarization. If you are using RIP Version 2, you can turn off automatic summarization by specifying the no auto-summary command. Disable automatic summarization if you must perform routing between disconnected subnets. When automatic summarization is off, subnets are advertised.
Examples
The following example disables automatic summarization for EIGRP process 1:
router eigrp 1
no auto-summary
Related Commands
Command Description
ip summary-address eigrp
Configures a summary aggregate address for a specified interface.
clear ip eigrp neighbors
To delete entries from the neighbor table, use the clear ip eigrp neighbors command in EXEC mode.
clear ip eigrp neighbors [ip-address | interface-type interface-number]
Syntax Description
ip-address
(Optional) Address of the neighbor.
interface-type interface-number
(Optional) Interface type and number. Specifying these arguments removes the specified interface type from the neighbor table that all entries learned via this interface.
Command Modes
EXEC
Command History
Release Modification
10.0
This command was introduced.
Examples
The following example removes the neighbor whose address is 172.16.8.3:
Router# clear ip eigrp neighbors 172.16.8.3
Related Commands
Command Description
show ip eigrp interfaces
Displays information about interfaces configured for EIGRP.
default-information
To control the candidate default routing information between IGRP or Enhanced Interior Gateway Routing Protocol (EIGRP) processes, use the default-information command in router configuration mode. To suppress IGRP or EIGRP candidate information in incoming or outbound updates, use the no default-information in command.
default-information {in | out} {access-list-number | access-list-name}
no default-information {in | out}
Syntax Description
in
Allows IGRP or EIGRP exterior or default routes to be received by an IGRP process.
out
Allows IGRP or EIGRP exterior routes to be advertised in updates.
access-list-number | access-list-name
Number or name of an access list. It can be a number in the range from 1 to 99 or an access list name.
Defaults
Normally, exterior routes are always accepted and default information is passed between IGRP or EIGRP processes when redistribution occurs.
Command Modes
Router configuration
Command History
Release Modification
10.0
This command was introduced.
11.2
The access-list-number and access-list-name arguments were added.
Usage Guidelines
The default network of 0.0.0.0 used by Routing Information Protocol (RIP) cannot be redistributed by IGRP but can be redistributed by EIGRP.
Examples
The following example allows IGRP exterior or default routes to be received by the IGRP process in autonomous system 1:
router igrp 1
default-information in
The following example allows EIGRP exterior or default routes to be received by the EIGRP process in autonomous system :
router eigrp 1
default-information in
default-metric (EIGRP)
To set metrics for IGRP or Enhanced Interior Gateway Routing Protocol (EIGRP), use the default-metric command in router configuration mode. To remove the metric value and restore the default state, use the no form of this command.
default-metric bandwidth delay reliability loading mtu
no default-metric bandwidth delay reliability loading mtu
Syntax Description
bandwidth
Minimum bandwidth of the route in kilobits per second. It can be from 1 to 4294967295.
delay
Route delay in tens of microseconds. It can be 1 or any positive number that is a multiple of 39.1 nanoseconds.
reliability
Likelihood of successful packet transmission expressed as a number between 0 and 255. The value 255 means 100 percent reliability; 0 means no reliability.
loading
Effective bandwidth of the route expressed as a number from 1 to 255 (255 is 100 percent loading).
mtu
Minimum maximum transmission unit (MTU) size of the route in bytes. It can be from 1 to 65535.
Defaults
Only connected routes can be redistributed without a default metric. the metric of redistributed Connected routes is set to 0.
Command Modes
Router configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
A default metric is required to redistribute a protocol into IGRP or EIGRP, unless you use the redistribute command. Automatic metric translations occur between IGRP and EIGRP. You do not need default metrics to redistributed IGRP or EIGRP into itself.
——————————————————————————–
Note The default metric command does not affect EIGRP-to-EIGRP or IGRP-to-EIGRP distribution. To configure EIGRP-to-EIGRP or IGRP-to-EIGRP distribution, use route maps.
——————————————————————————–
Metric defaults have been carefully set to work for a wide variety of networks. Take great care when changing these values. Keeping the same metrics is supported only when redistributing from IGRP, EIGRP, or static routes.
——————————————————————————–
Note When enabled, the default-metric command applies a metric value of 0 to redistributed connected routes. The default-metric command does not override metric values that are applied with the redistribute command.
——————————————————————————–
Examples
The following example takes redistributed Routing Information Protocol (RIP) metrics and translates them into EIGRP metrics with values as follows: bandwidth = 1000, delay = 100, reliability = 250, loading = 100, and MTU = 1500.
router eigrp 1
network 172.16.0.0
redistribute rip
default-metric 1000 100 250 100 1500
Related Commands
Command Description
redistribute (IP)
Redistributes routes from one routing domain into another routing domain.
distance eigrp
To allow the use of two administrative distances—internal and external—that could be a better route to a node, use the distance eigrp command in router configuration mode. To reset these values to their defaults, use the no form of this command.
distance eigrp internal-distance external-distance
no distance eigrp
Syntax Description
internal-distance
Administrative distance for EIGRP internal routes. Internal routes are those that are learned from another entity within the same autonomous system. The distance can be a value from 1 to 255.
external-distance
Administrative distance for EIGRP external routes. External routes are those for which the best path is learned from a neighbor external to the autonomous system. The distance can be a value from 1 to 255.
Defaults
internal-distance: 90
external-distance: 170
Command Modes
Router configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
An administrative distance is a rating of the trustworthiness of a routing information source, such as an individual router or a group of routers. Numerically, an administrative distance is an integer from 0 to 255. In general, the higher the value, the lower the trust rating. An administrative distance of 255 means the routing information source cannot be trusted at all and should be ignored.
Use the distance eigrp command if another protocol is known to be able to provide a better route to a node than was actually learned via external EIGRP, or if some internal routes should really be preferred by EIGRP.
Table 19 lists the default administrative distances.
Table 19 Default Administrative Distances
Route Source Default Distance
Connected interface
0
Static route
1
EIGRP summary route
5
External BGP
20
Internal EIGRP
90
IGRP
100
Open Shortest Path First (OSPF)
110
Intermediate System-to-Intermediate System (IS-IS)
115
Routing Information Protocol (RIP)
120
Exterior Gateway Protocol (EGP)
140
EIGRP external route
170
Internal Border Gateway Protocol (BGP)
200
Unknown
255
To display the default administrative distance for a specified routing process, use the show ip protocols EXEC command.
Examples
In the following example, the router eigrp global configuration command sets up EIGRP routing in autonomous system number 1. The network router configuration commands specify EIGRP routing on networks 192.168.7.0 and 172.16.0.0. The distance eigrp command sets the administrative distance of all EIGRP internal routes to 80 and all EIGRP external routes to 130.
Router(config)# router eigrp 1
Router(router-config)# network 192.168.7.0
Router(router-config)# network 172.16.0.0
Router(router-config)# distance eigrp 80 130
——————————————————————————–
Note You cannot set the administrative distance in EIGRP against certain routes or sources, as you can with other protocols. The command does not work this way with EIGRP.
——————————————————————————–
Related Commands
Command Description
show ip protocols
Displays the parameters and current state of the active routing protocol process.
distribute-list in (RIP, IGRP, EIGRP)
To filter networks received in updates, use the distribute-list in command in address family or router configuration mode. To disable this function, use the no form of this command.
distribute-list {access-list-number | prefix prefix-list-name [gateway prefix-list-name]} in [interface-type interface-number]
no distribute-list {access-list-number | prefix prefix-list-name [gateway prefix-list-name]} in [interface-type interface-number]
Syntax Description
access-list-number
Standard IP access list number. The list defines which networks are to be received and which are to be suppressed in routing updates.
prefix prefix-list-name
Name of a prefix list. The list defines which networks are to be received and which are to be suppressed in routing updates, based upon matching the network prefix to the prefixes in the list.
gateway prefix-list-name
(Optional) Name of the prefix list to be applied to the gateway of the prefix being updated.
in
Applies the access list to incoming routing updates.
interface-type
(Optional) Interface type.
interface-number
(Optional) Interface number on which the access list should be applied to incoming updates. If no interface is specified, the access list will be applied to all incoming updates.
Defaults
This command is disabled by default.
Command Modes
Address family configuration
Router configuration
Command History
Release Modification
10.0
This command was introduced.
11.2
The access-list-number, interface-type, and interface-number arguments were added.
12.0
The prefix-list-name argument was added.
12.0(7)T
Address family configuration mode was added.
Usage Guidelines
This command is not supported in Intermediate System-to-Intermediate System (IS-IS) or Open Shortest Path First (OSPF).
Using a prefix list allows filtering based upon the prefix length, making it possible to filter either on the prefix list, the gateway, or both for incoming updates.
Specify either an access list or a prefix list with the distribute-list in command.
Use the gateway keyword only with the prefix-list keyword.
To suppress networks from being advertised in updates, use the distribute-list out command.
Examples
In the following example, the BGP routing process accepts only two networks—network 0.0.0.0 and network 172.18.0.0:
access-list 1 permit 0.0.0.0
access-list 1 permit 172.18.0.0
access-list 1 deny 0.0.0.0 255.255.255.255
router bgp 5000
network 172.18.0.0
distribute-list 1 in
In the following example, The RIP process accepts only prefixes with prefix lengths of /8 to /24:
ip prefix-list max24 seq 5 permit 0.0.0.0/0 ge 8 le 24
router rip
network 172.18.0.0
distribute-list prefix max24 in
In the following example, the RIP process filters on packet length and accepts routing updates from address 192.168.1.1 only:
ip prefix-list max24 seq 5 permit 0.0.0.0/0 ge 8 le 24
ip prefix-list allowlist seq5 permit 192.168.1.1/32
router rip
network 172.18.0.0
distribute-list prefix max24 gateway allowlist in
Related Commands
Command Description
access-list (IP extended)
Defines an extended IP access list.
distribute-list out (RIP, IGRP, EIGRP)
Suppresses networks from being advertised in updates.
ip prefix-list
Creates an entry in a prefix list.
redistribute (IP)
Redistributes routes from one routing domain into another routing domain.
distribute-list out (RIP, IGRP, EIGRP)
To suppress networks from being advertised in updates, use the distribute-list out command in address family or router configuration mode. To disable this function, use the no form of this command.
distribute-list {access-list-number | prefix prefix-list-name [gateway prefix-list-name]} out [interface-name | routing-process | as-number]
no distribute-list {access-list-number | prefix prefix-list-name [gateway prefix-list-name]} out [interface-name | routing-process | as-number]
Syntax Description
access-list-number
Standard IP access list number. The list defines which networks are to be received and which are to be suppressed in routing updates.
prefix prefix-list-name
Name of a prefix list. The list defines which networks are to be received and which are to be suppressed in routing updates, based upon matching the network prefix to the prefixes in the list.
gateway prefix-list-name
(Optional) Name of the prefix list to be applied to the gateway of the prefix being updated.
out
Applies the access list to outgoing routing updates.
interface-name
(Optional) Name of a particular interface.
routing-process
(Optional) Name of a particular routing process, or the keyword static or connected.
as-number
(Optional) Autonomous system number.
Defaults
This command is disabled by default.
Command Modes
Address family configuration
Router configuration
Command History
Release Modification
10.0
This command was introduced.
11.2
The access-list-number argument was added.
12.0
The prefix-list-name argument was added.
12.0(7)T
Address family configuration mode was added.
Usage Guidelines
When redistributing networks, a routing process name can be specified as an optional trailing argument to the distribute-list command. Specifying an argument causes the access list or prefix list to be applied to only those routes derived from the specified routing process. After the process-specific access list or prefix list is applied, any access list or prefix list specified by a distribute-list command without a process name argument will be applied. Addresses not specified in the distribute-list command will not be advertised in outgoing routing updates.
Specify either an access list or a prefix list with the distribute-list in command.
Use the gateway keyword only with the prefix-list keyword.
——————————————————————————–
Note To filter networks received in updates, use the distribute-list in command.
——————————————————————————–
Examples
The following example causes only one network (network 172.18.0.0) to be advertised by a RIP routing process:
access-list 1 permit 172.18.0.0
access-list 1 deny 0.0.0.0 255.255.255.255
router rip
network 172.18.0.0
distribute-list 1 out
Related Commands
Command Description
access-list (IP extended)
Defines an extended IP access list.
distribute-list in (RIP, IGRP, EIGRP)
Filters networks received in updates.
ip prefix-list
Creates an entry in a prefix list.
eigrp log-neighbor-changes
To enable the logging of changes in Enhanced Interior Gateway Routing Protocol (EIGRP) neighbor adjacencies, use the eigrp log-neighbor-changes command in router configuration mode. To disable the logging of changes in EIGRP neighbor adjacencies, use the no form of this command.
eigrp log-neighbor-changes
no eigrp log-neighbor-changes
Syntax Description
This command has no arguments or keywords.
Defaults
Adjacency changes are logged.
Command Modes
Router configuration
Command History
Release Modification
11.2
This command was introduced.
Usage Guidelines
This command enables the logging of neighbor adjacency changes to monitor the stability of the routing system and to help detect problems. Logging is enabled by default. To disable the logging of neighbor adjacency changes, use the no form of this command.
Examples
The following configuration disables logging of neighbor changes for EIGRP process 1:
router eigrp 1
no eigrp log-neighbor-changes
The following onfiguration enables logging of neighbor changes for EIGRP process 1:
router eigrp 1
eigrp log-neighbor-changes
eigrp log-neighbor-warnings
To enable the logging of Enhanced Interior Gateway Routing Protocol (EIGRP) neighbor warning messages, use the eigrp log-neighbor-warnings command in router configuration mode. To disable the logging of EIGRP neighbor warning messages, use the no form of this command.
eigrp log-neighbor-warnings [seconds]
no eigrp log-neighbor-warnings
Syntax Description
seconds
(Optional) The time interval (in seconds) between repeated neighbor warning messages. The range of seconds is from 1 to 65535.
Defaults
Neighbor warning messages are logged.
Command Modes
Router configuration
Command History
Release Modification
12.0(5)
This command was introduced.
Usage Guidelines
When neighbor warning messages occur, they are logged by default. With this command, you can disable and enable neighbor warning messages, and configure the interval between repeated neighbor warning messages.
Examples
The following command will log neighbor warning messages for EIGRP process 1 and repeat the warning messages in 5-minute (300 seconds) intervals:
router eigrp 1
eigrp log-neighbor-warnings 300
eigrp router-id
To set the router ID used by Enhanced Interior Gateway Routing Protocol (EIGRP) when communicating with its neighbors, use the eigrp router-id command in router configuration mode. To remove the configured router ID, use the no form of this command.
eigrp router-id ip-address
no eigrp router-id ip-address
Syntax Description
ip-address
Router ID in dotted decimal notation.
Defaults
EIGRP automatically selects an IP address to use as the router ID when an EIGRP process is started. The highest local IP address is selected and loopback interfaces are preferred. The router ID is not changed unless the EIGRP process is removed with the no router eigrp command or if the router ID is manually configured with the eigrp router-id command.
Command Modes
Address family configuration
Router configuration
Command History
Release Modification
12.1
This command was introduced.
Usage Guidelines
The router ID is used to identify the originating router for external routes. If an external route is received with the local router ID, the route is discarded. The router ID can be configured with any IP address with two exceptions; 0.0.0.0 and 255.255.255.255 are not legal values and cannot be entered. A unique value should be configured for each router.
Examples
The following example configures 172.16.1.3 as a fixed router ID:
router eigrp 1
eigrp router-id 172.16.1.3
eigrp stub
To configure a router as a stub using Enhanced Interior Gateway Routing Protocol (EIGRP), use the eigrp stub command in router configuration mode. To disable the EIGRP stub routing feature, use the no form of this command.
eigrp stub [receive-only | connected | static | summary | redistributed]
no eigrp stub [receive-only | connected | static | summary | redistributed]
Syntax Description
receive-only
(Optional) Sets the router as a receive-only neighbor.
connected
(Optional) Advertises connected routes.
static
(Optional) Advertises static routes.
summary
(Optional) Advertises summary routes.
redistributed
(Optional) Advertises redistributred routes from other protocols and autonomous systems.
Defaults
Stub routing is not enabled by default.
Command Modes
Router configuration
Command History
Release Modification
12.0(7)T
This command was introduced.
12.0(15)S
This command was integrated into Cisco IOS Release 12.0(15)S.
12.2
Keyword redistributed was added.
Usage Guidelines
Use the eigrp stub command to configure a router as a stub where the router directs all IP traffic to a distribution router.
The eigrp stub command can be modified with several options, and these options can be used in any combination except for the receive-only keyword. The receive-only keyword will restrict the router from sharing any of its routes with any other router in that EIGRP autonomous system, and the receive-only keyword will not permit any other option to be specified because it prevents any type of route from being sent. The four other optional keywords (connected, static, summary, and redistributed) can be used in any combination but cannot be used with the receive-only keyword.
If any of these four keywords is used with the eigrp stub command, only the route types specified by the particular keyword(s) will be sent. Route types specified by the non-used keyword(s) will not be sent.
The connected keyword permits the EIGRP Stub Routing feature to send connected routes. If the connected routes are not covered by a network statement, it may be necessary to redistribute connected routes with the redistribute connected command under the EIGRP process. This option is enabled by default.
The static keyword permits the EIGRP Stub Routing feature to send static routes. Without the configuration of this option, EIGRP will not send any static routes, including internal static routes that normally would be automatically redistributed. It will still be necessary to redistribute static routes with the redistribute static command.
The summary keyword permits the EIGRP Stub Routing feature to send summary routes. Summary routes can be created manually with the summary address command or automatically at a major network border router with the auto-summary command enabled. This option is enabled by default.
The redistributed keyword permits the EIGRP Stub Routing feature to send other routing protocols and autonomous systems. Without the configuration of this option, EIGRP will not advertize redistributed routes.
——————————————————————————–
Note Multi-access interfaces, such as ATM, Ethernet, Frame Relay, ISDN PRI, and X.25, are supported by the EIGRP Stub Routing feature only when all routers on that interface, except the hub, are configured as stub routers.
——————————————————————————–
Examples
In the following example, the eigrp stub command is used to configure the router as a stub that advertises connected and summary routes:
router eigrp 1
network 10.0.0.0
eigrp stub
In the following example, the eigrp stub command is issued with the connected and static keywords to configure the router as a stub that advertises connected and static routes (sending summary routes will not be permitted):
router eigrp 1
network 10.0.0.0
eigrp stub connected static
In the following example, the eigrp stub command is issued with the receive-only keyword to configure the router as a receive-only neighbor (connected, summary, and static routes will not be sent):
router eigrp 1
network 10.0.0.0 eigrp
eigrp stub receive-only
In the following example, the eigrp stub command is issued with the redistributed keyword to configure the router to advertize other protocols and autonomous systems:
router eigrp 1
network 10.0.0.0 eigrp
eigrp stub redistributed
ip authentication key-chain eigrp
To enable authentication of Enhanced Interior Gateway Routing Protocol (EIGRP) packets, use the ip authentication key-chain eigrp command in interface configuration mode. To disable such authentication, use the no form of this command.
ip authentication key-chain eigrp as-number key-chain
no ip authentication key-chain eigrp as-number key-chain
Syntax Description
as-number
Autonomous system number to which the authentication applies.
key-chain
Name of the authentication key chain.
Defaults
No authentication is provided for EIGRP packets.
Command Modes
Interface configuration
Command History
Release Modification
11.2 F
This command was introduced.
Examples
The following example applies authentication to autonomous system 2 and identifies a key chain named SPORTS:
ip authentication key-chain eigrp 2 SPORTS
Related Commands
Command Description
accept-lifetime
Sets the time period during which the authentication key on a key chain is received as valid.
ip authentication mode eigrp
Specifies the type of authentication used in EIGRP packets.
key
Identifies an authentication key on a key chain.
key chain
Enables authentication of routing protocols.
key-string (authentication)
Specifies the authentication string for a key.
send-lifetime
Sets the time period during which an authentication key on a key chain is valid to be sent.
ip authentication mode eigrp
To specify the type of authentication used in Enhanced Interior Gateway Routing Protocol (EIGRP) packets, use the ip authentication mode eigrp command in interface configuration mode. To disable that type of authentication, use the no form of this command.
ip authentication mode eigrp as-number md5
no ip authentication mode eigrp as-number md5
Syntax Description
as-number
Autonomous system number.
md5
Keyed Message Digest 5 (MD5) authentication.
Defaults
No authentication is provided for EIGRP packets.
Command Modes
Interface configuration
Command History
Release Modification
11.2 F
This command was introduced.
Usage Guidelines
Configure authentication to prevent unapproved sources from introducing unauthorized or false routing messages. When authentication is configured, an MD5 keyed digest is added to each EIGRP packet in the specified autonomous system.
Examples
The following example configures the interface to use MD5 authentication in EIGRP packets in autonomous system 1:
ip authentication mode eigrp 1 md5
Related Commands
Command Description
accept-lifetime
Sets the time period during which the authentication key on a key chain is received as valid.
ip authentication key-chain eigrp
Enables authentication of EIGRP packets.
key
Identifies an authentication key on a key chain.
key chain
Enables authentication of routing protocols.
key-string (authentication)
Specifies the authentication string for a key.
send-lifetime
Sets the time period during which an authentication key on a key chain is valid to be sent.
ip bandwidth-percent eigrp
To configure the percentage of bandwidth that may be used by Enhanced Interior Gateway Routing Protocol (EIGRP) on an interface, use the ip bandwidth-percent eigrp command in interface configuration mode. To restore the default value, use the no form of this command.
ip bandwidth-percent eigrp as-number percent
no ip bandwidth-percent eigrp as-number percent
Syntax Description
as-number
Autonomous system number.
percent
Percent of bandwidth that EIGRP may use.
Defaults
50 percent
Command Modes
Interface configuration
Command History
Release Modification
11.2
This command was introduced.
Usage Guidelines
EIGRP will use up to 50 percent of the bandwidth of a link, as defined by the bandwidth interface configuration command. This command may be used if some other fraction of the bandwidth is desired. Note that values greater than 100 percent may be configured. The configuration option may be useful if the bandwidth is set artificially low for other reasons.
Examples
The following example allows EIGRP to use up to 75 percent (42 kbps) of a 56-kbps serial link in autonomous system 1:
interface serial 0
bandwidth 56
ip bandwidth-percent eigrp 1 75
Related Commands
Command Description
bandwidth (interface)
Sets a bandwidth value for an interface.
ip hello-interval eigrp
To configure the hello interval for the Enhanced Interior Gateway Routing Protocol (EIGRP) routing process designated by an autonomous system number, use the ip hello-interval eigrp command in interface configuration mode. To restore the default value, use the no form of this command.
ip hello-interval eigrp as-number seconds
no ip hello-interval eigrp as-number seconds
Syntax Description
as-number
Autonomous system number.
seconds
Hello interval (in seconds).
Defaults
For low-speed, nonbroadcast multiaccess (NBMA) networks: 60 seconds
For all other networks: 5 seconds
Command Modes
Interface configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
The default of 60 seconds applies only to low-speed, NBMA media. Low speed is considered to be a rate of T1 or slower, as specified with the bandwidth interface configuration command. Note that for the purposes of EIGRP, Frame Relay and Switched Multimegabit Data Service (SMDS) networks may be considered to be NBMA. These networks are considered NBMA if the interface has not been configured to use physical multicasting; otherwise, they are considered not to be NBMA.
Examples
The following example sets the hello interval for Ethernet interface 0 to 10 seconds:
interface ethernet 0
ip hello-interval eigrp 1 10
Related Commands
Command Description
bandwidth (interface)
Sets a bandwidth value for an interface.
ip hold-time eigrp
Configures the hold time for a particular EIGRP routing process designated by the autonomous system number.
ip hold-time eigrp
To configure the hold time for a particular Enhanced Interior Gateway Routing Protocol (EIGRP) routing process designated by the autonomous system number, use the ip hold-time eigrp command in interface configuration mode. To restore the default value, use the no form of this command.
ip hold-time eigrp as-number seconds
no ip hold-time eigrp as-number seconds
Syntax Description
as-number
Autonomous system number.
seconds
Hold time (in seconds).
Defaults
For low-speed, nonbroadcast multiaccess (NBMA) networks: 180 seconds
For all other networks: 15 seconds
Command Modes
Interface configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
On very congested and large networks, the default hold time might not be sufficient time for all routers and access servers to receive hello packets from their neighbors. In this case, you may want to increase the hold time.
We recommend that the hold time be at least three times the hello interval. If a router does not receive a hello packet within the specified hold time, routes through this router are considered unavailable.
Increasing the hold time delays route convergence across the network.
The default of 180 seconds hold time and 60 seconds hello interval apply only to low-speed, NBMA media. Low speed is considered to be a rate of T1 or slower, as specified with the bandwidth interface configuration command.
Examples
The following example sets the hold time for Ethernet interface 0 to 40 seconds:
interface ethernet 0
ip hold-time eigrp 1 40
Related Commands
Command Description
bandwidth (interface)
Sets a bandwidth value for an interface.
ip hello-interval eigrp
Configures the hello interval for the EIGRP routing process designated by an autonomous system number.
ip split-horizon eigrp
To enable Enhanced Interior Gateway Routing Protocol (EIGRP) split horizon, use the ip split-horizon eigrp command in interface configuration mode. To disable split horizon, use the no form of this command.
ip split-horizon eigrp as-number
no ip split-horizon eigrp as-number
Syntax Description
as-number
Autonomous system number.
Defaults
The behavior of this command is enabled by default.
Command Modes
Interface configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
For networks that include links over X.25 packet-switched networks (PSNs), you can use the neighbor router configuration command to defeat the split horizon feature. As an alternative, you can explicitly specify the no ip split-horizon eigrp command in your configuration. However, if you do so, you must similarly disable split horizon for all routers and access servers in any relevant multicast groups on that network.
——————————————————————————–
Note In general, we recommend that you not change the default state of split horizon unless you are certain that your application requires the change in order to properly advertise routes. Remember that if split horizon is disabled on a serial interface and that interface is attached to a packet-switched network, you must disable split horizon for all routers and access servers in any relevant multicast groups on that network.
——————————————————————————–
Examples
The following example disables split horizon on a serial link connected to an X.25 network:
interface serial 0
encapsulation x25
no ip split-horizon eigrp 101
Related Commands
Command Description
ip split-horizon (IGRP)
Enables the split horizon mechanism.
neighbor (IGRP)
Defines a neighboring router with which to exchange routing information.
ip summary-address eigrp
To configure a summary aggregate address for a specified interface, use the ip summary-address eigrp command in interface configuration mode. To disable a configuration, use the no form of this command.
ip summary-address eigrp as-number network-address subnet-mask [admin-distance]
no ip summary-address eigrp as-number network-address subnet-mask [admin-distance]
Syntax Description
as-number
Autonomous system number.
network-address
IP summary aggregate address to apply to an interface.
subnet-mask
Subnet mask.
admin-distance
(Optional) Administrative distance. A value from 0 to 255.
Defaults
No summary aggregate addresses are predefined. The default administrative distance metric for EIGRP is 90.
Command Modes
Interface configuration
Command History
Release Modification
10.0
This command was introduced.
12.0(7)T
The admin-distance argument was added.
Usage Guidelines
EIGRP summary routes are given an administrative distance value of 5. The administrative distance metric is used to advertise a summary without installing it in the routing table.
Examples
The following example sets the IP summary aggregate address for Ethernet interface 0 with an administrative distance of 95:
interface ethernet 0
ip summary-address eigrp 1 192.168.0.0 255.255.0.0 95
Related Commands
Command Description
auto-summary (EIGRP)
Restores the default behavior of automatic summarization of subnet routes into network-level routes.
metric weights (EIGRP)
To allow the tuning of the IGRP or Enhanced Interior Gateway Routing Protocol (EIGRP) metric calculations, use the metric weights command in router configuration mode. To reset the values to their defaults, use the no form of this command.
metric weights tos k1 k2 k3 k4 k5
no metric weights
Syntax Description
tos
Type of service must always be zero.
k1k2 k3 k4 k5
Constants that convert an IGRP or EIGRP metric vector into a scalar quantity.
Defaults
tos: 0
k1: 1
k2: 0
k3: 1
k4: 0
k5: 0
Command Modes
Router configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
Use this command to alter the default behavior of IGRP routing and metric computation and allow the tuning of the IGRP metric calculation for a particular type of service (ToS).
If k5 equals 0, the composite IGRP or EIGRP metric is computed according to the following formula:
metric = [k1 * bandwidth + (k2 * bandwidth)/(256 - load) + k3 * delay]
If k5 does not equal zero, an additional operation is performed:
metric = metric * [k5/(reliability + k4)]
Bandwidth is inverse minimum bandwidth of the path in BPS scaled by a factor of 2.56 * 1012. The range is from a 1200-bps line to 10 terabits per second.
Delay is in units of 10 microseconds. The range of delay is from 10 microseconds to 168 seconds. A delay of all ones indicates that the network is unreachable.
The delay parameter is stored in a 32-bit field, in increments of 39.1 nanoseconds. The range of delay is from 1 (39.1 nanoseconds) to hexadecimal FFFFFFFF (decimal 4,294,967,040 nanoseconds). A delay of all ones (that is, a delay of hexadecimal FFFFFFFF) indicates that the network is unreachable.
Table 20 lists the default values used for several common media.
Table 20 Bandwidth Values by Media Type
Media Type Delay Bandwidth
Satellite
5120 (2 seconds)
5120 (500 megabits)
Ethernet
25600 (1 milliseconds [ms])
256000 (10 megabits)
1.544 Mbps
512000 (20,000 ms)
1,657,856 bits
64 kbps
512000 (20,000 ms)
40,000,000 bits
56 kbps
512000 (20,000 ms)
45,714,176 bits
10 kbps
512000 (20,000 ms)
256,000,000 bits
1 kbps
512000 (20,000 ms)
2,560,000,000 bits
Reliability is given as a fraction of 255. That is, 255 is 100 percent reliability or a perfectly stable link.
Load is given as a fraction of 255. A load of 255 indicates a completely saturated link.
Examples
The following example sets the metric weights to slightly different values than the defaults:
router igrp 1
network 192.168.0.0
metric weights 0 2 0 2 0 0
Related Commands
Command Description
bandwidth (interface)
Sets a bandwidth value for an interface.
delay (interface)
Sets a delay value for an interface.
metric holddown
Keeps new IGRP routing information from being used for a certain period of time.
metric maximum-hops
Causes the IP routing software to advertise as unreachable those routes with a hop count higher than is specified by the command (IGRP only).
neighbor (EIGRP)
To define a neighboring router with which to exchange routing information on a router that is running Enhanced Interior Gateway Routing Protocol (EIGRP), use the neighbor command in router configuration mode. To remove an entry, use the no form of this command.
neighbor ip-address interface-type interface-number
no neighbor ip-address interface-type interface-number
Syntax Description
ip-address
IP address of a peer router with which routing information will be exchanged.
interface-type
Interface through which peering is established.
interface-number
Number of the interface or subinterface.
Command Default
No neighboring routers are defined.
Command Modes
Router configuration
Command History
Release Modification
10.0
This command was introduced.
Usage Guidelines
Multiple neighbor statements can be used to establish peering sessions with specific EIGRP neighbors. The interface through which EIGRP will exchange routing updates must be specified in the neighbor statement. The interfaces through which two EIGRP neighbors exchange routing updates must be configured with IP addresses from the same network.
Note Configuring the passive-interface command suppresses all incoming and outgoing routing updates and hello messages. EIGRP neighbor adjacencies cannot be established or maintained over an interface that is configured as passive.
SO, EIGRP interfaces must not have passive interface enabled, the link to the ISP may.
grettle: Thank you “Studying”. This is EXCELLENT reference material. But my question has to do with the EIGRP sim and it is directed to those that took the cert and scored in the 900′s. When configuring the R1 router that is linked to the ISP, do we need to configure the interface that connects to the ISP (in this case s1/0) as passive? And do we need to configure a default on this same router (R1) that sends all traffic to the ISP router for ip addresses not in its routing table. Thanks.
To grettle, i don’t think you need to configure a default route on R1, because the question stated that the internet access is fine. Just my opinion, what do you think?
All other inter connectivity and Internet access for the existing locations of the company are working properly.
I don’t think EGIRP will propagate the default route as stated in the modification section, please correct me if I am wrong.
Quote:
(Note: The “ip default-network” command in R1 will advertise the static route of R1 (to go to the Internet) to other routers (R2,R3,R4) so that they can access the Internet too). In the exam you will see these lines in R1 configuration:
!
ip default-network 198.0.18.0
ip route 0.0.0.0 0.0.0.0 198.0.18.5
!
I’m going thru Sink dumps. Do I need to review all of the 692 questions in this dump??? That’s a lot! Or maybe there is just a smaller version of it?