CCNA Access List Sim 2
Question
A network associate is adding security to the configuration of the Corp1 router. The user on host C should be able to use a web browser to access financial information from the Finance Web Server. No other hosts from the LAN nor the Core should be able to use a web browser to access this server. Since there are multiple resources for the corporation at this location including other resources on the Finance Web Server, all other traffic should be allowed.
The task is to create and apply a numbered access-list with no more than three statements that will allow ONLY host C web access to the Finance Web Server. No other hosts will have web access to the Finance Web Server. All other traffic is permitted.
Access to the router CLI can be gained by clicking on the appropriate host.
All passwords have been temporarily set to “cisco”.
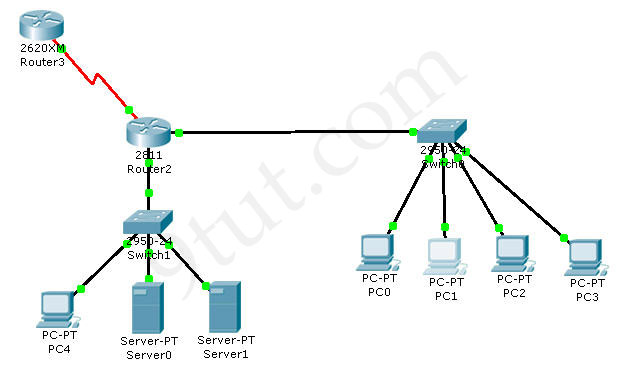
The Core connection uses an IP address of 198.18.196.65
The computers in the Hosts LAN have been assigned addresses of 192.168.33.1 – 192.168.33.254
Host A 192.168.33.1
Host B 192.168.33.2
Host C 192.168.33.3
Host D 192.168.33.4
The servers in the Server LAN have been assigned addresses of 172.22.242.17 – 172.22.242.30
The Finance Web Server is assigned an IP address of 172.22.242.23.
The Public Web Server is assigned an IP address of 172.22.242.17

Answer and Explanation
(Note: If you are not sure how to use access-list, please check out my access-list tutorial at: http://www.9tut.com/access-list-tutorial, also some modifications about the access-list have been reported so you should read the “Some modifications” section at the end of this question to understand more. You can also download this sim to practice (open with Packet Tracer) here: http://www.9tut.com/download/9tut.com_Access-list_sim2.pkt
Corp1>enable (you may enter “cisco” as it passwords here)
We should create an access-list and apply it to the interface which is connected to the Server LAN because it can filter out traffic from both Sw-2 and Core networks. The Server LAN network has been assigned addresses of 172.22.242.17 – 172.22.242.30 so we can guess the interface connected to them has an IP address of 172.22.242.30 (.30 is the number shown in the figure). Use the “show running-config” command to check which interface has the IP address of 172.22.242.30.
Corp1#show running-config

We learn that interface FastEthernet0/1 is the interface connected to Server LAN network. It is the interface we will apply our access-list (for outbound direction).
Corp1#configure terminal
Our access-list needs to allow host C – 192.168.33.3 to the Finance Web Server 172.22.242.23 via web (port 80)
Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Deny other hosts access to the Finance Web Server via web
Corp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80
All other traffic is permitted
Corp1(config)#access-list 100 permit ip any any
Apply this access-list to Fa0/1 interface (outbound direction)
Corp1(config)#interface fa0/1
Corp1(config-if)#ip access-group 100 out
Notice: We have to apply the access-list to Fa0/1 interface (not Fa0/0 interface) so that the access-list can filter traffic coming from both the LAN and the Core networks. If we apply access list to the inbound interface we can only filter traffic from the LAN network.
In the real exam, just click on host C and open its web browser. In the address box type http://172.22.242.23 to check if you are allowed to access Finance Web Server or not. If your configuration is correct then you can access it.
Click on other hosts (A, B and D) and check to make sure you can’t access Finance Web Server from these hosts.
Finally, save the configuration
Corp1(config-if)#end
Corp1#copy running-config startup-config
(This configuration only prevents hosts from accessing Finance Web Server via web but if this server supports other traffic – like FTP, SMTP… then other hosts can access it, too.)
Notice: In the real exam, you might be asked to allow other host (A, B or D) to access the Finance Web Server so please read the requirement carefully.
Some modifications:
Modification 1:
| permit host B from accessing finance server | access-list 100 permit ip host 192.168.33.2 host 172.22.242.23 |
| deny host B from accessing other servers (not the whole network) | access-list 100 deny ip host 192.168.33.2 172.22.242.16 0.0.0.15 |
| permit everything else | access-list 100 permit ip any any |
Modification 2:
| Only allow Host C to to access the financial server | access-list 100 permit ip host 192.168.33.3 host 172.22.242.23 |
| Not allow anyone else in any way communicate with the financial server | access-list 100 deny ip any host 172.22.242.23 |
| Allow all other traffic | access-list 100 permit ip any any |
Modification 3:
| - Host C should be able to use a web browser(HTTP)to access the Finance Web Server | access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80 |
| - Other types of access from host C to the Finance Web Server should be blocked - All access from hosts in the Core or local LAN to the Finance Web Server should be blocked |
access-list 100 deny ip any host 172.22.242.23 (because the requirement says we can not use more than 3 statements so we have to use “any” here for the hosts in the Core and hosts in local LAN) |
| - All hosts in the Core and local LAN should be able to access the Public Web Server * | access-list 100 permit ip any host (If the question asks this, surely it has to give you the IP of Public Web Server) but in the exam you should use “access-list 100 permit ip any any” |
Modification 4:
| Host C should be able to use a web browser to access the financial web server | access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80 |
| Other types of access from host C to the finance web server should be blocked | access-list 100 deny ip host 192.168.33.3 host 172.22.242.23 |
| All hosts in the core and on the local LAN should be able to access the Public web server * | access-list 100 permit ip any host (The IP of Public Web Server will surely be given in this question) but in the exam you should use “access-list 100 permit ip any any” |
* There are some reports about the command of “All hosts in the core and on the local LAN should be able to access the Public web server” saying that the correct command should be “access-list 100 permit ip any any”, not “access-list 100 permit ip any host (IP of Public Web Server)”. Although I believe the second command is better but maybe you should use the first command “access-list 100 permit ip any any” instead as some reports said they got 100% when using this command (even if the question gives you the IP address of Public Web Server). It is a bug in this sim.
(Note: Don’t forget to apply this access list to the suitable interface or you will lose points
interface fa0/1
ip access-group 100 out
And in the exam, they may slightly change the requirements, for example host A, host B instead of host C… so make sure you read the requirement carefully and use the access-list correctly)
I created this sim in Packet Tracer v5.2.1 so you can practice with it. You will need new version of Packet Tracer to open it (v5.1+).
Download this sim here
Notice: After typing the commands above, if you make a “ping” from other hosts (PC0, PC1, PC3) then PC4 (Finance Web Server) can still reply because we just filter HTTP traffic, not ICMP traffic. To generate HTTP traffic, select “Web Browser” in the “Desktop” tab of these PCs. When a web browser opens, type the IP address of Finance Web Server and you can see how traffic flows in Simulation Mode.

And notice that in the initial configuration of this sim the Core network can ping Finance Web Server. We have to create an access-list that can filter this traffic too.
Other lab-sims on this site:



pass my exam today 964. thank you 9tut, brar and people here!!!
Simulations are traditional VTP (5 questions), EIGRP (different look topology but the same thing)
But ACL Sim was pretty different:
1 – permit host A http finance server
2 – deny any other communication from other hosts to finance server
3 – allow all hosts to communicate public server
later i post the sintax
Thanks
@mavmcl: not much different from the 9tut previous exemples…
access-list 100 permit ip host 192.168.33.1 host 172.22.242.23
access-list 100 deny ip any host 172.22.242.23
access-list 100 permit ip any any
and int fa0/1
ip access-group 100 out
ops i read it wrong its
access-list 100 permit tcp host 192.168.33.1 host 172.22.242.23
the rest is the same
omfg eq 80 at the end sorry guys
@mavmcl where is the syntax? please and thnx alot for the feedback
@password not correct answer.
@damnsan:
1 – permit host A http finance server
2 – deny any other communication from other hosts to finance server
3 – allow all hosts to communicate public server
access-list 100 permit tcp host x.x.x.x (ip host A) host x.x.x.x (ip finance server) eq 80
access-list 100 permit ip any host x.x.x.x (ip public server)
access-list 100 deny ip any any
int fa 0/1 ip access-group 100 out (verify the correct interface to apply the ACL with #show ip int brief)
Some new questions. but brar and senkar still valid.
exam was 50 questions long
Eigrp sim locks different but still the same thing (don´t be afraid)
1 – permit host A http finance server
2 – deny any other communication from other hosts to finance server
3 – allow all hosts to communicate public server
=======================================================
access-list 100 permit tcp host 192.168.33.1 host 172.22.242.23 eq 80
access-list 100 deny ip any host 172.22.242.23
access-list 100 permit ip any any
@kambalpogi
also that sintax work in packet tracer. but i use my config in the exam
How to solve the access-list simulation which doesn’t
Provide any information regarding the IP addresses of the interface?
Is it by using commands show run and show cdp neighbors detail
???
Please anyone answer ASAP
Scenario is similar but no information is provided regarding the IP address of the interface
@mavmcl
bro about your third acl statement
is it really access-list 100 deny ip any any?
how about your EIGRP how come it’s a little bit different what is the tweak they use in the exam?
and the VTP questions same with 9tut?
@mavmlc you solution is not right because a deny deny is implicit at the end of the access list and your access list doesnt allow the traffic from core and the other lan
@password
try it on packet tracer, works for me
@Brad no info in my simulation ¨show ip int brief¨ may help you
@KambalPogi
yeah man, i pass with 100% on simulations, try it.
EIGRP
– same thing but the topology have different physical order.
– No passive interfaces
– can configure the 4 routers (can´t remember the router names)
– default route in central router are already configure
– 1 phantom route in central router (i delete it)
– 3 routers are eigrp 212, 1 router eigrp 22
VTP
– same thing
– 5 questions:
1 – Which switch is the root bridge for VLAN 1?
2 – From which switch did Sw-Ac3 receive VLAN information ?
3 – Refer to the exibit, SwX was taken out of the production network for maintenance. It will be reconnected to the Fa 0/16 port of Sw-Ac3. What happens to the network when it is reconnected and a trunk exists between the two switches?
4 – Out of which ports will a frame be forwarded that has source mac-address 0010.5a0c.fd86 and destination mac-address 000a.8a47.e612? (Choose three)
5 – If one of the host connected to Sw-AC3 wants to send something for the ip 190.0.2.5 (or any ip that is not on the same subnet) what will be the destination MAC address?
Ramdom order
@password thanks for ur reply.. But some questions for access-list
Don’t give any info regarding the IP address of the hosts and the servers
How to find them… Show running conf can give some info but how about the host LAN
Is it by show cdp neighbor details
Anyone can you explain this to me plz….
@mavmcl
Thanks for ur info regarding the other labs that is included on your exam
I keep on hearing about the passive interface on EIGRP do we really need to get rid of it in the exam or just leave it there?
The phantom route is out of nowhere network that should not be included on the routing table?
You use the console port of your destined PC to configure your routers?
Hello everyone
Can someone kindly tell me why have we used TCP EQ 80 protocol in this question instead of IP.
As far as I know, TCP EQ 80 will be used to deny a host from accessing a web page.
@KambalPogi
you do need to remove the passive interface if its related with other links
inside the local network(R2,R3,R4), but if its related with the ISP link
just leave it as is, don’t remove it or you will fail on that sims
@Adukmak
port 80 is used for HTTP, therefore you should use it if you need to
deny or to allow a connection via browser.
Small changes were given today, here is what was needed:
Host A should connect to Finance via web:
access-list 100 permit tcp host 192.168.33.1 host 172.22.242.23 eq 80
Deny Host A to reach Finance via anything else than web
Deny other hosts access to the Finance Web Server via anything
Corp1(config)#access-list 100 deny ip any host 172.22.242.23
All hosts must be able to connect to public webserver
Corp1(config)#access-list 100 permit ip any any
I scored 100% on ACL.
I took the exam yesterday, fortunately I passed with 933 the sims were EIGRP, VTP, and ACL2 they were almos exactly the same as 9tut just a littles changes but If you grasp the knowledge you will pass the exam for sure. Thanks 9tut and skehar their question are still valid. I encourage everybody to take the exam and not be scared because if you study with these resources you will have almost a 100 percent to crack the exam.
@KambalPogi, @maxnanabas09 answer your question but i remove the phantom route on central router
i have a question: i pass my exam last week, can i take the security exam after 180 days? in my score page say: Cisco policy requires that you wait a minimum of 180 days before retaking an exam (with an identical exam number). what (with an identical exam number) means??? ccnasec is exam 640-554 not an identical number
can someone explain this
Hi,
I wonder why we need to define a blocking ACL for the other hosts at the first scenario since there is an implicit “deny all” command at the end of the first command to allow only host C?
“Deny other hosts access to the Finance Web Server via web
Corp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80″
???
what the hell is this, arent you supposed to type ip address first, and then wildcard mask?
@ersoy
Because we have to deny other hosts access to the Finance Web Server “via web”. All other accesses like ftp,telnet are still allowed.
@AB
I’m ok with the fact that we need to block other hosts to access Finance web Server via web.
But the thing is that, the first command solely should prevent the other hosts from accessing the Finance web server via web, if there is an implicit “deny all” at the end.
“access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80″
I mean, the second command sounds unnecessary, since you are indicating that you will only allow Host C (by first command); thus, no need to define again blocking traffic.
I did the simulation without the second command, all other hosts accessed to the Finance web server via web. Apparently, the 3 line command are correct, but couldn’t understand still why we need to define blocking traffic.
@ersoy
I agree with you. I took the CCNA recently and my scenario was http traffic from host B allowed to finance server, no other traffic allowed to finance server, all other traffic alllowed to web server. My line of thinking was to make my access list two lines:
access-list 100 permit tcp host b address host finance address eq 80
access-list 100 permit ip any host web address
Explicit deny at the end would take care of every thing else. Didn’t get that question right though….. :-/
Hi Friends,
I will be giving CCNA 640-802 on 18 Feb, any one pls guide me how to prepare for simulators.
i pass my ccna today. Thanks God for the wisdom and for 9tut for giving us this informations.
I get eigrp and vtp same as 9tut. ACL2 is a bit different.
HOST D should be able to access finance server via http.
all other access of host D to finance server should be blocked.
all host should be able to access Public server.
all other from any access should be denied.
@desertfox
same with your configuration?
HOST D should be able to access finance server via http.
all other access of host D to finance server should be blocked.
all other from any access should be denied.
all host should be able to access Public server.
==================================
access-list 100 permit tcp host [host D address] host [finance web server] eq 80
access-list 100 deny ip any host [finance web server]
access-list 100 permit ip any any
@kambalpogi,
my ACLfor
HOST D should be able to access finance server via http.
all other access of host D to finance server should be blocked.
all other from any access should be denied.
all host should be able to access Public server.
=============================================
access-list 100 permit tcp host (host D address) host (finance server address) eq www
access-list 100 permit tcp permit ip any host (public server address)
access-list 100 deny ip any any
I just added the 3rd statement since in the question it prompts me that this is a 3 statement ACL.
ACL2 question
HOST D should be able to access finance server via http.
all other access of host D to finance server should be blocked.
all access from hosts in to the finance web server should be blocked.
all host should be able to access Public server.
@desertfox
about your second statement
access-list 100 permit tcp permit ip any host (public server address)
The condition is :
all other access of host D to finance server should be blocked.
all other from any access should be denied.
How come you use the permit statement? The condition ask to deny any other access to the finance server . Thanks for the clarification!
What is the difference between “deny tcp any host” and “deny ip any host” ?
@gfincher
the difference between the two is when we use “deny tcp any host” we can deny specific source port or a destination port .
http://ciscotests.org/ccna.php?part=12&page=2
kambalpogi@ in your commands you didn’t implement the second statement , but i think it comes under the default last command deny any any which is not implemented by the users
i think both of you are right ( you and desertfox )
regarding your question , don’t look at the configuration line by line , look at the concept and the task is it implemented or not ?
his 2nd statement , he implemented the 4th condition
his 1st statement , he implemented the 1st condition
the 3rd statement , he implemented both conditions 3rd 4th
so sorry , the 3rd statement , he implemented both conditions 2nd and 3rd
1. HOST D should be able to access finance server via http.
2.all other access of host D to finance server should be blocked.
all access from hosts in to the finance web server should be blocked.
3.all host should be able to access Public server.
=============================================
so it should be:
access-list 100 permit tcp host (HOST D) host (finance) eq 80 >>> 1st statement
access-list 100 deny ip any host 172.22.242.23 >>> 2nd statement
access-list 100 permit ip any any >>> 3rd Statement
can you still use tcp any host for the second statement.
access-list 100 deny tcp any host 172.22.242.33
would that be a correct statement?
It’s better to use the command “access-list 100 deny ip any host ” because the statement requires all other access should be block it doesn’t indicate a specific port to be used
ACL2 question
HOST D should be able to access finance server via http.
all other access of host D to finance server should be blocked.
all access from hosts in to the finance web server should be blocked.
all host should be able to access Public server.
My answer:
access-list 100 permit tcp host (host D address) host (finance server address) eq www
—> this statement permits HOST D to access finance server via http.
access-list 100 permit tcp permit ip any host (public server address)
access-list 100 deny ip any any
ACL2 question
HOST D should be able to access finance server via http.
all other access of host D to finance server should be blocked.
all access from hosts in to the finance web server should be blocked.
all host should be able to access Public server.
My answer:
access-list 100 permit tcp host (host D address) host (finance server address) eq www
—> this statement permits HOST D to access finance server via http.
access-list 100 permit tcp permit ip any host (public server address)
–> this statement permits ALL host to access the public server address.
access-list 100 deny ip any any
–>> based on the four security statement, only 2 statements are permitted and the rest are blocked. So by using the first 2 ACL statements, it already satisfies the requirement. Since the question is a 3 ACL statement, then I added the 3rd statement even do I know that it has the implicit deny already. Any opinion?
@maxnanabas09
I think you got it right.. :)
So correct me if iim wrong
so the statement wil be:
access-list 100 permit tcp host Host Address) host (Finance web server address) eq 80
access-list 100 deny ip any host (Finance web server Address) eq 80
access-list 100 permit ip any any
int fao/1
ip access-group 100 out
access-list 100 permit tcp host (Host D Address) host (Finance web server address) eq 80
access-list 100 deny ip any host (Finance web server Address) eq 80
access-list 100 permit ip any any
int fao/1
ip access-group 100 out
So correct me if iim wrong
so the statement wil be:
access-list 100 permit tcp host Host Address) host (Finance web server address) eq 80
access-list 100 deny ip any host (Finance web server Address) eq 80
access-list 100 permit ip any any
int fao/1
ip access-group 100 out
================================
you shouldnt use > access-list 100 deny ip any host (Finance) eq 80
it would be invalid because the requirement is “all other access of host D to finance server should be blocked.
all access from hosts in to the finance web server should be blocked.”
take note: “all access” you NEED to BLOCK ALL ACCESS, so you should use the “ip” protocol instead
I think i need to clear my answer
Requirements:
1. HOST D should be able to access finance server via http.
2.all other access of host D to finance server should be blocked.
all access from hosts in to the finance web server should be blocked.
3.all host should be able to access Public server
Answer:
access-list 100 permit tcp host (HOST D) host (finance) eq 80 >>> 1st statement states that Host D SHOULD access the server via HTTP(Port 80)
access-list 100 deny ip any host 172.22.242.23 >>> 2nd statement states that Host D and ALL ACCESS to the FINANCE WEB SERVER SHOULD be BLOCKED, so instead of HTTP you need to use, ip protocol so no one can access the FINANCE WEB SERVER
access-list 100 permit ip any any >>> 3rd Statement states that ALL HOST SHOULD ACCESS the public server, so it means the whole server network,
note that you can use :access-list 100 permit ip any host, BUT 9tut says that use ip any any on lab sims
@maxnanabas09: Yes, your solution is correct!
access-list 100 permit tcp host (HOST D) host (finance) eq 80
access-list 100 deny ip any host (finance)
access-list 100 permit ip any any
this is still on the test took it today and failed with 801 this was question 46 with 5 mins left and i ran out of time.:-(
I’m confused, why in the answer they applied the access list to the int f0/1 out instead of f0/0 in as it’s an extended list? I would appriciate any explination!
@bigguy
The general rule of thumb is to place extended access lists closer to the source so you would think that having it on an IN interface would make sense. But since you’re source is two actually two networks, it makes more sense to put it on the OUT interface towards the target network so that both destinations can be filtered. If you applied it to fa0/0 in, that interface does not have the two source networks behind it so one of the networks won’t get filtered.