CCNA Access List Sim 2
Question
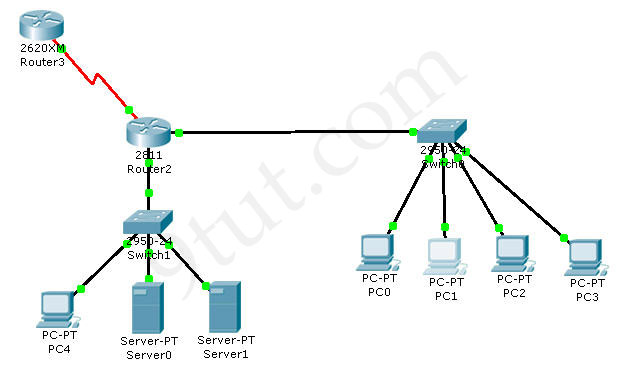
A network associate is adding security to the configuration of the Corp1 router. The user on host C should be able to use a web browser to access financial information from the Finance Web Server. No other hosts from the LAN nor the Core should be able to use a web browser to access this server. Since there are multiple resources for the corporation at this location including other resources on the Finance Web Server, all other traffic should be allowed.
The task is to create and apply a numbered access-list with no more than three statements that will allow ONLY host C web access to the Finance Web Server. No other hosts will have web access to the Finance Web Server. All other traffic is permitted.
Access to the router CLI can be gained by clicking on the appropriate host.
All passwords have been temporarily set to “cisco”.
The Core connection uses an IP address of 198.18.196.65
The computers in the Hosts LAN have been assigned addresses of 192.168.33.1 – 192.168.33.254
Host A 192.168.33.1
Host B 192.168.33.2
Host C 192.168.33.3
Host D 192.168.33.4
The servers in the Server LAN have been assigned addresses of 172.22.242.17 – 172.22.242.30
The Finance Web Server is assigned an IP address of 172.22.242.23.
The Public Web Server is assigned an IP address of 172.22.242.17

Answer and Explanation
(Note: If you are not sure how to use access-list, please check out my access-list tutorial at: http://www.9tut.com/access-list-tutorial, also some modifications about the access-list have been reported so you should read the “Some modifications” section at the end of this question to understand more. You can also download this sim to practice (open with Packet Tracer) here: http://www.9tut.com/download/9tut.com_Access-list_sim2.pkt
Corp1>enable (you may enter “cisco” as it passwords here)
We should create an access-list and apply it to the interface which is connected to the Server LAN because it can filter out traffic from both Sw-2 and Core networks. The Server LAN network has been assigned addresses of 172.22.242.17 – 172.22.242.30 so we can guess the interface connected to them has an IP address of 172.22.242.30 (.30 is the number shown in the figure). Use the “show running-config” command to check which interface has the IP address of 172.22.242.30.
Corp1#show running-config

We learn that interface FastEthernet0/1 is the interface connected to Server LAN network. It is the interface we will apply our access-list (for outbound direction).
Corp1#configure terminal
Our access-list needs to allow host C – 192.168.33.3 to the Finance Web Server 172.22.242.23 via web (port 80)
Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Deny other hosts access to the Finance Web Server via web
Corp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80
All other traffic is permitted
Corp1(config)#access-list 100 permit ip any any
Apply this access-list to Fa0/1 interface (outbound direction)
Corp1(config)#interface fa0/1
Corp1(config-if)#ip access-group 100 out
Notice: We have to apply the access-list to Fa0/1 interface (not Fa0/0 interface) so that the access-list can filter traffic coming from both the LAN and the Core networks. If we apply access list to the inbound interface we can only filter traffic from the LAN network.
In the real exam, just click on host C and open its web browser. In the address box type http://172.22.242.23 to check if you are allowed to access Finance Web Server or not. If your configuration is correct then you can access it.
Click on other hosts (A, B and D) and check to make sure you can’t access Finance Web Server from these hosts.
Finally, save the configuration
Corp1(config-if)#end
Corp1#copy running-config startup-config
(This configuration only prevents hosts from accessing Finance Web Server via web but if this server supports other traffic – like FTP, SMTP… then other hosts can access it, too.)
Notice: In the real exam, you might be asked to allow other host (A, B or D) to access the Finance Web Server so please read the requirement carefully.
Some modifications:
Modification 1:
| permit host B from accessing finance server | access-list 100 permit ip host 192.168.33.2 host 172.22.242.23 |
| deny host B from accessing other servers (not the whole network) | access-list 100 deny ip host 192.168.33.2 172.22.242.16 0.0.0.15 |
| permit everything else | access-list 100 permit ip any any |
Modification 2:
| Only allow Host C to to access the financial server | access-list 100 permit ip host 192.168.33.3 host 172.22.242.23 |
| Not allow anyone else in any way communicate with the financial server | access-list 100 deny ip any host 172.22.242.23 |
| Allow all other traffic | access-list 100 permit ip any any |
Modification 3:
| - Host C should be able to use a web browser(HTTP)to access the Finance Web Server | access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80 |
| - Other types of access from host C to the Finance Web Server should be blocked - All access from hosts in the Core or local LAN to the Finance Web Server should be blocked |
access-list 100 deny ip any host 172.22.242.23 (because the requirement says we can not use more than 3 statements so we have to use “any” here for the hosts in the Core and hosts in local LAN) |
| - All hosts in the Core and local LAN should be able to access the Public Web Server * | access-list 100 permit ip any host (If the question asks this, surely it has to give you the IP of Public Web Server) but in the exam you should use “access-list 100 permit ip any any” |
Modification 4:
| Host C should be able to use a web browser to access the financial web server | access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80 |
| Other types of access from host C to the finance web server should be blocked | access-list 100 deny ip host 192.168.33.3 host 172.22.242.23 |
| All hosts in the core and on the local LAN should be able to access the Public web server * | access-list 100 permit ip any host (The IP of Public Web Server will surely be given in this question) but in the exam you should use “access-list 100 permit ip any any” |
* There are some reports about the command of “All hosts in the core and on the local LAN should be able to access the Public web server” saying that the correct command should be “access-list 100 permit ip any any”, not “access-list 100 permit ip any host (IP of Public Web Server)”. Although I believe the second command is better but maybe you should use the first command “access-list 100 permit ip any any” instead as some reports said they got 100% when using this command (even if the question gives you the IP address of Public Web Server). It is a bug in this sim.
(Note: Don’t forget to apply this access list to the suitable interface or you will lose points
interface fa0/1
ip access-group 100 out
And in the exam, they may slightly change the requirements, for example host A, host B instead of host C… so make sure you read the requirement carefully and use the access-list correctly)
I created this sim in Packet Tracer v5.2.1 so you can practice with it. You will need new version of Packet Tracer to open it (v5.1+).
Download this sim here
Notice: After typing the commands above, if you make a “ping” from other hosts (PC0, PC1, PC3) then PC4 (Finance Web Server) can still reply because we just filter HTTP traffic, not ICMP traffic. To generate HTTP traffic, select “Web Browser” in the “Desktop” tab of these PCs. When a web browser opens, type the IP address of Finance Web Server and you can see how traffic flows in Simulation Mode.

And notice that in the initial configuration of this sim the Core network can ping Finance Web Server. We have to create an access-list that can filter this traffic too.
Other lab-sims on this site:



@aranbada There is detalisation in the text of the task: “No other hosts from the LAN nor the Core should be able to use a web browser to access this server” So if you will add ACL 100 only as in on fa 0/0, possible hosts from the “Core” network will be able to reach Financial Server, which will not meet task’s initial requirement.
@aranbada
I think there’s a bit mistake.
If you applied ACL to the inbound of the interface fa0/0 all traffic from the core network will pass and will not undergo any filtering process … Just remember that extended acl must be implemented closest to the destination (server LAN) so for the task above it’s fa0/1 outbound !!!
Good luck men.
Hi,
Sorry my mistake. I meant the fa0/1. As network traffic from the CORE and LAN tries to access the fa0/1 inbound into the server LAN, the access-list will filter the traffic.
ip access-group 100 in
Let me know your thought.
Cheers.
Passed today, had exactly that SIM!
I now understand your reasoning. You are correct and i was wrong.
Thanks for your replies
@aranbada OK :)
alhamdullilah i m ccna certified scoring 986 in todays exam and very thankful to 9tut and SEKHARS & others and dont be scared like me as i m very confused by reading some comments and i got all three famouse sims
1.vtp
2.eigrp
3.acl
and vtp question is confusing but by the grace of almighty i tackled this question too..
and in eigrp as number is 23 on all router except the newly added router ,and i see the passive interface b/w the central 1 router and isp so i leave it and static route b/w central 1 to isp is also there and ip default network too…
but the response of the show running config on all the router is very bad or u say slow that i dont see all advertsied networks on first time so have to use show run config again and again and there is also a route which is not used in complete so i delete that network
and atlast i ping all routers with each other but i cant ping isp router successfully from any of the four routers but still got 100% in this eigrp lab
and 3rd scenario is acl which is from the 9tut sim and i also got full marks in this sim too by the thankz of almighty ALLAH..
And gud luck to all whos oppting for the exammm
Thanks guys i passed ccna this evening. Keep up the good work.
Thanks guys i passed ccna this evening. Keep up the good work.
@waqas Please what dumps did u use. Kindly mail it to me @ clahws@yahoo.com
@seun
i used 2 dumps one is sekhar and 2nd 1 is prepking
and 1 thing more that nearly all dumps question are same so dont be scared
and if u use brar it can also cover sekhar and other dumps too but i only use sekhar and by the thanks of ALLAH i ppassed this paper and prepking is 80 to 85% same to sekhar so do practice all question well with concepts inshaALLAH u also succeed..
Is SEKHAR’S and 9Tut Sims are enough? or do I have to study Brar’s as well ?
@seun
How much Time did u spend to read all this ?
@Zinger @aks
thanks a lot for you and for 9tut
@seun
i sent the dumps i hope u got it acknowledge me soon
thankz
@waqas @seun
How much Time did u spend to read dumps and sims ?
@ N
I Gave 3 to 4 months to both dumps that i use and slowly slowly doing all questions but for the exam in the last 3 week i gave alot of time to both dumps and labs…
@waqas
Hi- do you think you could send the dumps to me as well?
thx
ftyawb@hotmail.com
i passed my exam on 15 nov..labs vtp,acl2,eigrp,my dumpz sekhar 697 ques..dumpz are valid
1.host c should be able to web access(http) to finance server
access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
2. host in lan nor the core would not alow in any way communication with finance server
access-list 100 deny ip any host 172.22.242.23
3.all host in lan or core would be able to access public web server
access-list 100 permit ip any any
@ rana @ waqas
I am reading Shekhar’s Dumps and sims in 9 tut, Do i have to study Brar’s as well ..?
fail today with 801/1000. sims same as here but i want to find out if after configuring the ACL as in here without pinging will it affect ur score. cause is gave 4o% on ACL.
my question was to allow host B access to the financial web server.and my configuration goes like this
corp 1(config)access-list 101 permit tcp host 192.168.33.2 host 172.22.242.23 eq 80
corp 1(config)access-list 101 deny tcp any host 172.22.242.23 eq 80
corp 1(config)access-list 101 permit ip any any
corp 1(config) interface fa0/1
corp 1(config-if)ip access-group 101 out
corp 1(config-if)end
then copy running-config startup-config
can some tell me what is wrong with this configuration and if u don’t ping or verify at the end of the configuration will it affect ur score?
thanks alot guys.
@Vola
Could you tell us all the requirements you were asked for? You have only listed one of them, usually you get at least 2 more
@vola
You should state the whole requirements for the ACL.
Based on your configuration, you allowed host B to access finance web server and deny any other host web access but allow any other access and permit everything else?
Hi,
I did CCNA this morning, I failed (775) and i used this syntax :
access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
but it didn’t work. It told me i had a syntax problem, so i let a comment during the exam.
I don’t understand.
I spoke with a CCNP switch person and she told me i had to use this syntax : ip access-list extended name permit ip host X.X.X.X host X.X.X.X eq 80.
Any suggestion?
passed yesterday, labs still valid VTP ACL2 EIGRP
syntax : ip access-list extended name permit ip host X.X.X.X host X.X.X.X eq 80
syntax : ip access-list 100 permit ip host 192.168.33.3 host 172.22.242.23 eq 80
do anyone get sim other than….
VTP EIGRP OR ACL????
IF THERE ARE OTHER SIMS PLEASE INFORM
passed ccna exam this morning, thanks 9tut, labs still valid vtp acl2 eigrp
@greg
Your syntax was right. I think you were not in a right mode, like user>, privilege# or global(config)
@9tut: the interface you applied the access list is not correct. When you are applying an extended accesslist, it is the source interface you apply it to not the destination interface. Extended access list traffic should not even get to the destination interface at all. It just a waste of valuable bandwidth. Please check your statement again. The best implementation is
Interface fastethernet0/0
Ip access-group 100 in. This command will filter all traffic from 192.168.33.0 network. Even though your implementation is correct, you will not get the full points because it was applied to the wrong interface.
@Mintah Ghana
Notice: We have to apply the access-list to Fa0/1 interface (not Fa0/0 interface) so that the access-list can filter traffic coming from both the LAN and the Core networks. If we apply access list to the inbound interface we can only filter traffic from the LAN network.
@Ghana……..per the question, your to block the Core network too. The only way to do this is to apply it to FA0/1 out.
Mike is right, it’s because base on the task given we need to filter from the outside packet(LAN & CORE) going to server and accurately “interface Fa0/1″ should be apply for filter both(LAN & CORE) the outside packet..
Oh I see. You guys are right. That’s too bad I couldn’t see/read that too. My concentration was on the LAN. Thanks guys for the correction.
Don’t forget to specify what packet should be filter..thats IT :-)
i took the exam on saturday, november 24th and passed with flying colors… thanks a lot 9tut! the sims were exactly those here..vtp sim, acl sim the one with modifications ( core, lan, finance server and public server…) and the eigrp sim. the think is not just to learn the questions and simulations but to understand the why and how… and this site did it for me. thanks again to all that posted!
besides the labs, what are the some of the regular questions on the exam?
thanks
I cleared my CCNA exam – 920,thanks to all of you guys for having discussion here,which cleard so many doubts of mine..thanks 9tut, shekhar.
Sims were Acl2,vtp,eigrp.and around 4-5 new questions…
Taking my Ccna Tomorrow morning but i got a question regarding this ACL SIM. The main scenario shown above states “that will allow ONLY host C web access to the Finance Web Server.” however when looking at the steps from 9tut they use
“access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80″
however on the other scenarios they use something like
“access-list 100 permit ip host 192.168.33.3 host 172.22.242.23″
My confusion is that on both of the statements they only say access and dont specify Web Browser for example , like one of the other scenarios do.
So why use tcp on one and ip on the other?
Thank you.
@ Anonymous
Its because on the main scenario there’s the keyword “WEB ACCESS” .
Hope that helps.
Good Luck tomorrow.
@ Anonymous
Make it specify that web access(80) packet only should be allow to transmit into the destination and other types of access from host c should filter
and this line statement should be “access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80″
Hi.
Took the exam and wondering where i got wrong. There are only 2 servers. public and finance
() Host B will be allowed to access finance server using web
() Block other traffic from host B to Finance
() Block traffic from core and lan to finance
() Permit access from core and lan to the public server
my config is as follows.
access-list 100 permit tcp host B Host finace eq www
access-list 100 deny ip any host finance
acess-list 100 permit ip any any
int fa0/1 > ip access-group out
can any1 share their thoughts? Thanks.
@JR
did you save config?
Yup..i did..
also,..i was able to access finance from host b using web browser and not from the other hosts. All hosts were able to access public. I made sure to save my config copy run start.
@JR
Why do you think you made mistake in this sim?
@ JP ypur santex are not complete
access-list 100 permit tcp host B Host finace eq www ..ok
access-list 100 deny ip any host finance.xxxx
access-list 100 deny tcp not ip… if you deny ip nothing goes through
access-list 100 deny tcp any host finance eq 80
acess-list 100 permit ip any any…ok
int fa0/1 > ip access-group out…..ok
@CCNAJACOB
() Block other traffic from host B to Finance
() Block traffic from core and lan to finance
It is clearly says “other” traffic. But they didn’t mention exactly what kind, so we have to use “ip”
i have a question was it a number ACL or Name ACL ? to me the configurations are right
@JR
i have a question was it a number ACL or Name ACL ? to me the configurations are right