CCNA Access List Sim
Question
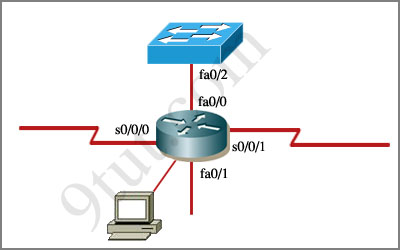
An administrator is trying to ping and telnet from Switch to Router with the results shown below:
Switch>
Switch> ping 10.4.4.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.3,timeout is 2 seconds:
.U.U.U
Success rate is 0 percent (0/5)
Switch>
Switch> telnet 10.4.4.3
Trying 10.4.4.3 …
% Destination unreachable; gateway or host down
Switch>
Click the console connected to Router and issue the appropriate commands to answer the questions.
Answer and Explanation
Note: If you are not sure about Access-list, please read my Access-list tutorial. You can also download this sim to practice (open with Packet Tracer) here: http://www.9tut.com/download/9tut.com_CCNA_Access_List_Sim.pkt
For this question we only need to use the show running-config command to answer all the questions below
Router>enable
Router#show running-config
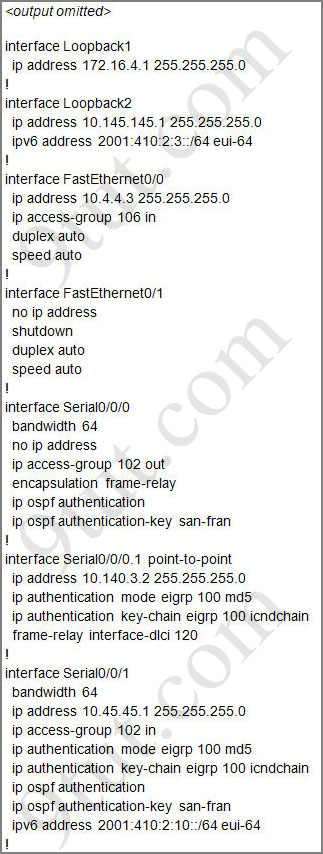
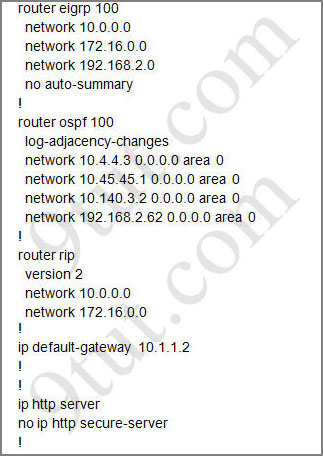
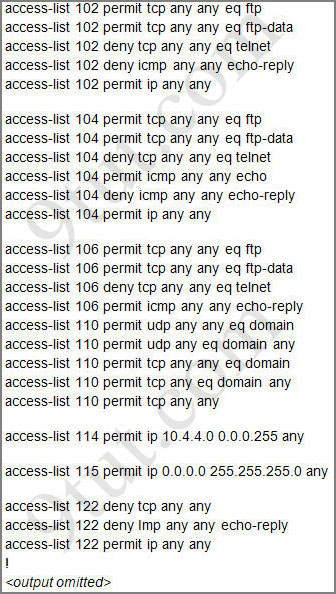
Question 1:
Which will fix the issue and allow ONLY ping to work while keeping telnet disabled?
A – Correctly assign an IP address to interface fa0/1
B – Change the ip access-group command on fa0/0 from “in” to “out”
C – Remove access-group 106 in from interface fa0/0 and add access-group 115 in.
D – Remove access-group 102 out from interface s0/0/0 and add access-group 114 in
E – Remove access-group 106 in from interface fa0/0 and add access-group 104 in
Answer: E
Explanation:
Let’s have a look at the access list 104:
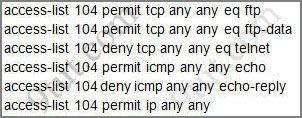
The question does not ask about ftp traffic so we don’t care about the two first lines. The 3rd line denies all telnet traffic and the 4th line allows icmp traffic to be sent (ping). Remember that the access list 104 is applied on the inbound direction so the 5th line “access-list 104 deny icmp any any echo-reply” will not affect our icmp traffic because the “echo-reply” message will be sent over the outbound direction.
Question 2:
What would be the effect of issuing the command ip access-group 114 in to the fa0/0 interface?
A – Attempts to telnet to the router would fail
B – It would allow all traffic from the 10.4.4.0 network
C – IP traffic would be passed through the interface but TCP and UDP traffic would not
D – Routing protocol updates for the 10.4.4.0 network would not be accepted from the fa0/0 interface
Answer: B
Explanation:
From the output of access-list 114: access-list 114 permit ip 10.4.4.0 0.0.0.255 any we can easily understand that this access list allows all traffic (ip) from 10.4.4.0/24 network
Question 3:
What would be the effect of issuing the command access-group 115 in on the s0/0/1 interface?
A – No host could connect to Router through s0/0/1
B – Telnet and ping would work but routing updates would fail.
C – FTP, FTP-DATA, echo, and www would work but telnet would fail
D – Only traffic from the 10.4.4.0 network would pass through the interface
Answer: A
Explanation:
First let’s see what was configured on interface S0/0/1:
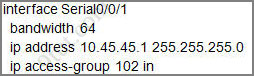
Recall that each interface only accepts one access-list, so when using the command “ip access-group 115 in” on the s0/0/1 interface it will overwrite the initial access-list 102. Therefore any telnet connection will be accepted (so we can eliminate answer C).
B is not correct because if telnet and ping can work then routing updates can, too.
D is not correct because access-list 115 does not mention about 10.4.4.0 network. So the most reasonable answer is A.
But here raise a question…
The wildcard mask of access-list 115, which is 255.255.255.0, means that only host with ip addresses in the form of x.x.x.0 will be accepted. But we all know that x.x.x.0 is likely to be a network address so the answer A: “no host could connect to Router through s0/0/1” seems right…
But what will happen if we don’t use a subnet mask of 255.255.255.0? For example we can use an ip address of 10.45.45.0 255.255.0.0, such a host with that ip address exists and we can connect to the router through that host. Now answer A seems incorrect!
Please comment if you have any idea for this sim!
Other lab-sims on this site:



On Question 2
What would be the effect of issuing the command ip access-group 114 in to the fa0/0 interface?
A – Attempts to telnet to the router would fail
B – It would allow all traffic from the 10.4.4.0 network
C – IP traffic would be passed through the interface but TCP and UDP traffic would not
D – Routing protocol updates for the 10.4.4.0 network would not be accepted from the fa0/0 interface
The access-list is access-list 114 permit ip 10.4.4.0 0.0.0.255 any
There is no permit any any
So there is an explicit deny at the end.
Would B still the correct?
@ Abe: Yes B is still the correct answer.
ACL make filtering sequentially.
So considering implicit deny at the end our access-list will be like this:
access-list 114 permit ip 10.4.4.0 0.0.0.255 any
access-list 114 deny ip 10.4.4.0 any any
It means if a host from network 10.4.4.0 send any traffic to any ip address,1st permit line will be executed. An ACL execution is stopped when it matches any line in ACL so it will not read deny line and stopped after matching first line of ACL.
@ Vikas
Thanks
@Vikas
It can not be “access-list 114 deny ip 10.4.4.0 any any”
The implicit deny at the end of an access-list is like that:
access-list 114 deny ip any any
In question 3
I think the right answer is D
cause the access list on the serial interface s0/0/1 is applied in means traffic going in
but the traffic comming out which is comming from interface f0/0 from network 10.4.4.0
will pass am i right?
@samehesk
D may not be the right option as it says only 10.4.4.0 traffic passes through. Traffic other than 10.4.4.0 can also pass through as there is no ACL applied on the outbound direction on s0/0/1
for question 3. I think B is correct
Because only address x.x.x.0 can pass, so broacast upadates address of routing protocol can’t pass. (RIPv1: 255.255.255.255, RIPv2: 224.0.0.9, OSPF: 224.0.0.5/.6, EIGRP: 224.0.0.10)
for question 3:
We can consider option A as only the answer compare to other available answers which are quite wrong. So option A is a comparitively true answer but conseptually it’s not necessarily true. Because “what will happen if we don’t use a subnet mask of 255.255.255.0? For example we can use an ip address of 10.45.45.0 255.255.0.0, such a host with that ip address exists and we can connect to the router through that host. Now answer A seems incorrect!” (As explained above)
@Dhivyaa
For question 3 i think D is correct because the traffic from the lan 10.4.4.0 can pass in the out direction, as i said
we have interface f0/1 shutdown
we have interface s0/0/0 i have a doubt about this one but it has access list 102 in the in direction and it has a subinterface connected to a frame relay i am not sure if traffic can be routed to the s0/0/1 in the out direction or not.
but if A was correct he could have used deny any if he wants to deny all hosts
Hi guys,
I try to understand the first question but have no idea why the answer is E. Can some shed some lights please?
Much appreciated.
Thanks.
Sorry forgot to mention Question 1:
Access-list 104 denied the Telnet………..Then How can u access the telnet.Once u removed that line Access-list 104 deny tcp any(Host) any (Destination) eq telnet u can able to take telnet.
Hi everyone,
pls, can i get a link like 9tut,for those in juniper networks. i want to write my jncia er next week.9tut thanks for what you are doing for ccna candidates.pls,need a quick response
Let me explain why the answer for the 3-rd question is A.
Access-list 115 would permit only traffic coming from IP addresses like x.x.x.0.
But if you check the routing table of the router you can see there are only /24 routes and no gateway of last resort. So no host with IP address x.x.x.0 will be able to get an answer from the router, as the router will consider it a network address or it won’t find it in the routing table
@Chris:
What happen if Router connect to another RouterX through s0/0/1, And RouterX connect to a network with prefix-length /16?
Result is that there are many hosts with ip address x.x.x.0 connect to routerX can connect to Router through s0/0/1.
Right?
i think the question reffers to the current network layout
in the current network layout, interface s0/0/1 don’t connect to any exact router, that mean it connect to a large network.
interface S0/0/1 has IP address 10.45.45.1/24, so it’s only a /24 out there :)
if they want to refer /24, the current layout will show RouterX connect to router. In this case, they hide it, and we must think about large
Come back my answer, B is perfect choice here.
Because ping and telnet may not work for /24 prefix, but they can pass through network with prefix first statement is correct, “telnet and ping would work”
example 192.168.0.0/23 (IP address 192.168.1.0/23)
But all routing updates will be denied by interface s0/0/1. Routing update of routing protocols use multicast ip 224.0.0.x with x#0, second statement is also correct “routing updates fail”
Now I think I understand what you were trying to say: that out there might be another router, let’s assume its IP address 10.45.45.2/24, running for example EIGRP, and advertising a /23 route like 192.168.0.0/23. Ok, I admit you might be right about this, but I would wait for somebody to bump into this lab on his/her exam and issue a “show ip route” command at the console of the router to see what prefixes are in the routing table, then share the output here, as a comment. I guess the output will shed some light onto this question :)
question 3 answer is ‘A’ due to the fact that the question stats to issue the command “access-group 115 in on the s0/0/1 interface”. The router will filter traffic comming IN the router through s0/0/1. access-list on s0/0/1 will allow telnet, ftp, and network protocols if it is comming from a x.x.x.0 network ip adddress ( permit ip ) so answer B nd C are incorrect. IPs from network of 10.4.4.0 (10.4.4.1-10.4.4.254) cannot enter the router through s0/0/1 due to access-list 15 only address 10.4.4.0 which is a network address and this is known from int f0/0 so that is unlikely. So the explanation is correct. HINT 10.4.4.0 IPs can pass through the router but They will not be entering from S0/0/1
I’m sorry for oot..
but can anyone help me? I will have CCNA certification exam at 24th Jan 2011, but i don’t find any link that can get a FREE simulator/file CCNA EXAM CERTIFICATION to pass the exam. If it exists, you mus pay.
Can anyone help me ? email me at raditya_cp@hotmail.com
thankss
DOWNLOAD FILE FRM EXAMCOLLECTION.COM ,,CLICK ON CCNA THEN CLICK FILE WHICH IS RATED 139 ABOVE ….
THEN DOWNLOAD VCE SOFTWARE TO OPEN THIS FILE
Dear My CCNA paper on 22 jan
if any one found new question or lab then kindly update me
my
mail is
zulfiqarsoomro@yahoo.com
I Study 9tut and 356 Q ….
thanks
Zulfiqar,
U r good with that… Just make sure u understand concepts…
Study from the same.. did my exam 2day, and got a 1000… It is possible!
hi jason x
kindly tell me about exam labs
thanx
9tut and ACME
i pass today ccna 936
labs
VTP , ACL, Eigrp
zulfiqarsoomro@yahoo.com
Dear all,
Anybody taking xam on Jan 23 & 24th from India, pls post your views and updates if any.
Thank You for all your support !
hi zulfiqar ali,
is ACME same with Test Inside v17.11 356Q?
Hi,
In the explanation for Question 3 it says: “Therefore any telnet connection will be accepted”
but the access-list 115 indicates the protocol as “ip”. How can telnet be allowed if it is using TCP via port 23?
Thanks in advance for the explanation. :)
Sorry guys, I think I got it now.
Using the protocol IP will permit all other protocols…. Unless I’m wrong.
I have tried Question using GNS 3,
IMHO The correct answer is B, routing update would fail after several time begins with dynamic link possibly down. (as vnpro has explained)
Host with x.x.x.0 (but with valid subnet such as class B) still can connect if routed with static protocol.
Thank you, please correct…
Mondo props to 9tut for this site and for helping me pass the exam today. Keep it up!
Question 3:
A is correct.
There exist host addresses with shorter subnetmasks, but the interface itself has 255.255.255.0. So there can only come traffic allong from hosts with equal or longer subnetmask. And those wont pass, for not being 0 in the last byte.
Question 1: Regarding answer B
1) Why answer B is Wrong?
2) please make this statement correct if I am wrong,
//out bound of fa 0/0
a) access-list 106 deny tcp any any eq telnet
this will not allow to establish a telnet connection, since destination will be the switch’s telnet port this will be blocked.
b) access-list 106 permit icmp any any echo-reply
when a ping is introduced by the switch, echo-reply will be send by the router.
then whats the
b-1) source port=
b-2) destination port=
Can some one answer for
1)
2) b-1, b-2
thanks in advance!
Pls help me.
Question 2 : Answer b.
here we have to assume all trafic= ip tracfic
no tcp, udp, icmp traffic
So from the given answers the b is the acceptable.
Am I correct?
Question 1
Why the answer isn’t B….. when i change from ip access-group 106 “in” to “out” , i can ping to 10.4.4.3 router but can’t telnet…
why answer B is wrong?
Pls explain
hi can someone please tell me what are the functions used with icmp in access list 104? like echo,echo reply,echo request
thank you
in Q3 your point is true but here they assign the subnet mask 255.255.255.0 so in this subnet mask x.x.x.0 host is not possible
@Rani
Question 1: Regarding answer B
1) Why answer B is Wrong?
This is what I think:
It is mentioned in question “administrator is trying to ping and telnet from Switch to Router” & we have to allow ONLY ping to work while keeping telnet disabled.
So, we are concerned with ping/telnet from Switch –> Router.
Remember telnet (23) is a destination port.
When we telnet from swtich –> router , source port number(on switch) will be some number greater than 1023 and destination port will be 23.
example:
Sw (local port: eg. 1045 ) ———- > Router (telnet : 23)
Router will reply using source port 23 but will use destination port towards switch as 1045
Hence, “access-list 106 deny tcp any any eq telnet” (outbound on fa0/0) will have no effect on telnet traffic from switch to Router as desetination port is 1045.
But this access-list (outbound on fa0/0) will filter telnet traffic (ie when destination port is 23) i.e when we telnet from router to switch.
I hope this helps. :)
guys, just want to clarify about this particular sim exam… if simulation like this, do we need to apply the configuration and save it, or this only serve a reference to the questions? just what 9tut told above..
TIA…
Hi, for this question, i Think that we need more information… may be a show ip route ospf, focus in those routes that the router learn through serial 0/0/1… if the masks of those networks are /24 or longer the answer will be A…
What do you think?
PD… Please excuse my english
sorry, i´m talking about question 3
“But what will happen if we don’t use a subnet mask of 255.255.255.0? For example we can use an ip address of 10.45.45.0 255.255.0.0, such a host with that ip address exists and we can connect to the router through that host. Now answer A seems incorrect!”
In this case 10.45.45.0 would be just a normal host address and can be applied to a host like normal.
Hope this helps.
Yes, you are wright… but i think that the options are propoussed for this situation only (networks with subnet mask 24/ or longer), if the situation were other (subnet mask 16/ or longer) may be the options will be others and “No host could connect to Router through s0/0/1″ would be excluded from the options. But it´s only my personal opinion.
PD: Thanx to 9tut and ACME, i pass today ccna 1000/1000. Labs VTP , ACL-2, Eigrp
@ques no 1
both options B & E should be correct…….
make it more clear plzzzzzzzzzz
sorry choice B will allow both telnet & ping, so its wrong
option E is the only correct ans….
regarding Q. 1 — why answer “b” is not correct .. ??
question 3
I think this is trick question. You can’t write access list with netmask, you have to put wildcard mask, right?
This means acces list would be scrambled and interface wouldn’t permit any traffic.
Because of that, A (No host could connect to Router through s0/0/1) is correct answer.
Question no 3 is incorrect. Actually the access-list 115 itself is incorrect. You cannot have an access list with ip 0.0.0.0. I have created whole senario in packet tracer. It didnot take the command “access-list 115 permit 0.0.0.0 255.255.255.0 any”.
rest with question no 1 and 2 the answers were correct as mentioned above.
Q1 – E
Q2 – B