CCNA Access List Sim
Question
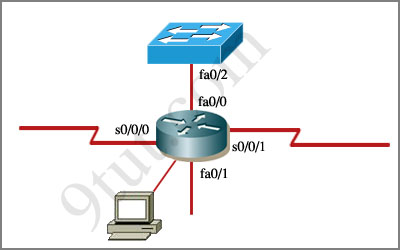
An administrator is trying to ping and telnet from Switch to Router with the results shown below:
Switch>
Switch> ping 10.4.4.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.3,timeout is 2 seconds:
.U.U.U
Success rate is 0 percent (0/5)
Switch>
Switch> telnet 10.4.4.3
Trying 10.4.4.3 …
% Destination unreachable; gateway or host down
Switch>
Click the console connected to Router and issue the appropriate commands to answer the questions.
Answer and Explanation
Note: If you are not sure about Access-list, please read my Access-list tutorial. You can also download this sim to practice (open with Packet Tracer) here: http://www.9tut.com/download/9tut.com_CCNA_Access_List_Sim.pkt
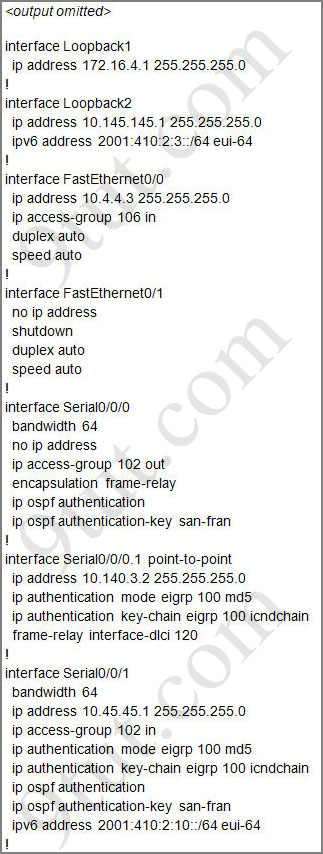
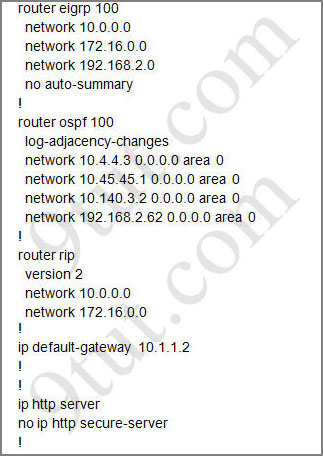
For this question we only need to use the show running-config command to answer all the questions below
Router>enable
Router#show running-config
Question 1:
Which will fix the issue and allow ONLY ping to work while keeping telnet disabled?
A – Correctly assign an IP address to interface fa0/1
B – Change the ip access-group command on fa0/0 from “in” to “out”
C – Remove access-group 106 in from interface fa0/0 and add access-group 115 in.
D – Remove access-group 102 out from interface s0/0/0 and add access-group 114 in
E – Remove access-group 106 in from interface fa0/0 and add access-group 104 in
Answer: E
Explanation:
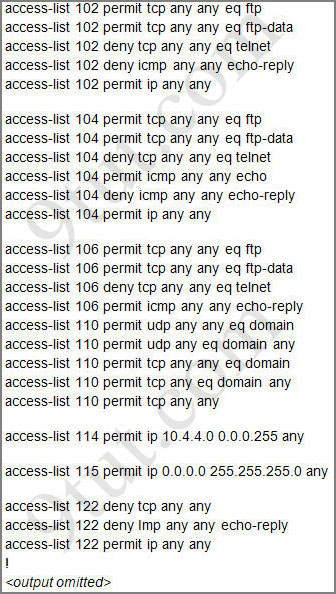
Let’s have a look at the access list 104:
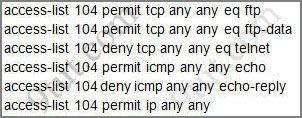
The question does not ask about ftp traffic so we don’t care about the two first lines. The 3rd line denies all telnet traffic and the 4th line allows icmp traffic to be sent (ping). Remember that the access list 104 is applied on the inbound direction so the 5th line “access-list 104 deny icmp any any echo-reply” will not affect our icmp traffic because the “echo-reply” message will be sent over the outbound direction.
Question 2:
What would be the effect of issuing the command ip access-group 114 in to the fa0/0 interface?
A – Attempts to telnet to the router would fail
B – It would allow all traffic from the 10.4.4.0 network
C – IP traffic would be passed through the interface but TCP and UDP traffic would not
D – Routing protocol updates for the 10.4.4.0 network would not be accepted from the fa0/0 interface
Answer: B
Explanation:
From the output of access-list 114: access-list 114 permit ip 10.4.4.0 0.0.0.255 any we can easily understand that this access list allows all traffic (ip) from 10.4.4.0/24 network
Question 3:
What would be the effect of issuing the command access-group 115 in on the s0/0/1 interface?
A – No host could connect to Router through s0/0/1
B – Telnet and ping would work but routing updates would fail.
C – FTP, FTP-DATA, echo, and www would work but telnet would fail
D – Only traffic from the 10.4.4.0 network would pass through the interface
Answer: A
Explanation:
First let’s see what was configured on interface S0/0/1:
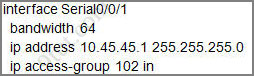
Recall that each interface only accepts one access-list, so when using the command “ip access-group 115 in” on the s0/0/1 interface it will overwrite the initial access-list 102. Therefore any telnet connection will be accepted (so we can eliminate answer C).
B is not correct because if telnet and ping can work then routing updates can, too.
D is not correct because access-list 115 does not mention about 10.4.4.0 network. So the most reasonable answer is A.
But here raise a question…
The wildcard mask of access-list 115, which is 255.255.255.0, means that only host with ip addresses in the form of x.x.x.0 will be accepted. But we all know that x.x.x.0 is likely to be a network address so the answer A: “no host could connect to Router through s0/0/1” seems right…
But what will happen if we don’t use a subnet mask of 255.255.255.0? For example we can use an ip address of 10.45.45.0 255.255.0.0, such a host with that ip address exists and we can connect to the router through that host. Now answer A seems incorrect!
Please comment if you have any idea for this sim!
Other lab-sims on this site:



@Deepti,
where i can get pass4sure latest dumps. please let me know i m taking exam this month end
Answer is “A”.
ACL 115 states to permit source host address that has IP address with the fourth octet “0″. You can never have a match with this statement because any IP address that has its fourth octet with a value of “0″ will always be a network address, no matter what the subnetmask is. And a network address will never be a source IP. therefore you can never satisfy that statement. So implicit deny all will take effect causing no host to connect through router s0/0/0.
Please comment if someone else agrees with me.
thanks….
my mistake.. Applies only for /24 onwards.
Regarding the confusion over question 3
Here is the command as issued:
access-list 115 permit ip 0.0.0.0 255.255.255.0 any
if my understanding is correct, 0.0.0.0 matches any host ip address, so that part is fine
however, 255.255.255.0 is supposed to be a wildcard mask, which would make the first three octets zero, and the last would be a 0-255 value for the net mask. i have never seen a net mask that looks like 0.0.0.240 or the like.
so it looks to me as if A is the correct answer simply because no incoming packet can have this value for a net mask.
if i’m completely off my rocker, hopefully someone will point it out :)
Shaun, you had a problem with 255.255.255.0 being a legitimate wildcard mask. So do I.
You also wrote the following ” … i have never seen a net mask (wildcard mask is the correct term here) that looks like 0.0.0.240 or the like …
I agree ! Proper netmasks should look like 0.0.0.3, 0.0.0.7, 0.0.0.15, 0.0.0.31, 0.0.0.63, 0.0.0.127, and 0.0.0.255
Yes, that’s mostly what I meant.
The original wildcard mask is listed as 255.255.255.0
In terms of net mask, that looks like 0.0.0.
My conclusion was based on never having seen a net mask that looks like that. My guess is they didn’t translate the net mask into a wildcard mask . . .
@3rd Question:
access-list 115 permit ip 0.0.0.0 255.255.255.0 any
“only host with ip addresses in the form of x.x.x.0 will be accepted”
the router at the other end of that serial link could never have the IP of 10.45.45.0, that IP is illegal on the 10.45.45.0/24 network. this means that nothing on the other end of the serial link or beyond that could connect to the configured router.
answer A, perfectly correct
This website has really been a blessing to me.
I’ll be writing my ccna exam by the end of this month, pls if anybody has the latest dumps, kindly send to my mail, Snowflakes162003@yahoo.com. God bless you.
Someones probably said this but I don’t want to look, the reason that A is right in the final question is because the netmask of the f0/0 network is 255.255.255.0
Therefore, hosts are all coming from the last 8 bits, therefore the wildcard of 255.255.255.0 would accept all bits in the first 24 bits or the network address, but always match 0 in the last 8 host bits. Therefore the only address that are accepted are x.x.x.0 with no exception. Hope that helps.
its from ICND 2 ??
Hey Guys! Did you download the simulation file ACL1 above from this page ? If u did, have u performed the command “show running-config” and see the following line:
line vty 0 4
login
This means the vty line password wasn’t set and even if we issue command ” ip access-group 114 in” on the interface f0/0, we CAN NOT telnet the Router from the switch. In this case, the switch can ping the router and vice versa. So, according to me, the right answer for the question 2 is:
A. Attempts to telnet to the router would fail
Or the one who created the simulation forgot to set the line vty password!
What do you think ?
what’s the router’s Enable password in this sim?
http://www.9tut.com/download/9tut.com_CCNA_Access_List_Sim.pkt
@Hi: You can find the password in the description of this lab (It is “cisco”).
Hi Zackie, I agree with your anser to Q2.
the login command enabled password check on line vty 0 4, but there is no password which means the access to virtual terminal (no matter which interface) is denied.
@9tut: thanks, I found the password in anther sim :)
need some help on ccna exam module
Well, for me the correct answer is B.
Telnet and ping could work, because if any other host from a /23 subnet, with an IP X.X.X.0/23 (indeed possible) tries, the router will allow that traffic through that interface. However, routing updates are all multicast for this router´s config: 224.0.0.5,224.0.0.6,224.0.0.9, 224.0.0.10, and none of them will be allowed to come into the router.
the sh ip int bri clearly show that s0/0/1 is administatively down,thus could not fw any packet
For question 2 the correct answer is B because it´s reffered to the command ip access-group 114 in and it´s effects on the network. Telnet will really not work but not because that specific command. There is no relationship in my point of view.
thankful to every user who has contributed to 9tut, it made me achieve CCNA certification today :)
almost all question were from Cisco.TestInside.640-802.v17.14.by.Acme.356q.vce and simulations were same as on this site.
@AAMIR: What are the simulations you have got? could you share some questions ?
The answer is A.
I have setup the packet tracer sim with a router on Ser0/0/1. I try to telnet from that router to the IP address 10.45.45.1 and can’t connect with the default ACL. I also setup SSH on the Routers. I can SSH to 10.45.45.1, but when you place ACL 115 on that interface both SSH and Telent stop working. You also start getting routing update errors and other communication problems. 0.0.0.0 255.255.255.0, means that any thing matching 0.0.0.x (where x is a number between 0 – 255) should be permitted, but is any IP that starts with 0 valid? No.
i give exam within 25th sep to 30th september,anybody tell me about the lattest dumps??
pls help me………
I have pass the exam today, thanks to 9tut and everyone else who was supporting me.
I recommend to Shaun’s talk
Regarding the question posed at the end of the SIM:
“But what will happen if we don’t use a subnet mask of 255.255.255.0? For example we can use an ip address of 10.45.45.0 255.255.0.0, such a host with that ip address exists and we can connect to the router through that host. Now answer A seems incorrect!”
Not so! We know that the ip address of s0/0/1 is 10.45.45.1/24. So no host with an IP address outside of that subnet can connect anyway, irregardless of the ACL bound to that interface. Answer A is correct given the parameters of the SIM.
FOR Q3 “C” IS THE ANSWER for access-list 102 is applied on “inbound” on S/0/0/1 and in the Q3 says if access-list 115 is applied on “outbound” what would be the outcome. So 2 different access-lists such as 102 and 115 can be applied. and the latter would not affect the former coz both are applied on different bounds.
Hi all ‘;’;For this sim, we have to apply comment and verify before answering or what???
Please help…..Thanks/
Hi Everyone,
I passed today with a score of 973
Basis this experience I can say acme dump and simulations on this website are enough to help clear the exam.
Thanks to whoever had given the acme dump link and thanks to 9tut for the simulations.
hey guys some of the answers here are wrong with regards to the ACL questions when u use the packet tracer
can some help with the wild card calculation pls!!
@emmanuel
so…
you have to think like this:
what is the first IP i have to filter?
what is the last IP i have to filter?
do i have any IPs between the first and last IP that shouldn’t be filter like those 2?
do i have any IPs inside the wildcard i will use that shouldn’t be filtered?
case 1:
first IP: 10.0.1.25
last IP: 10.0.7.44
now the questions.
if i have no problems filtering the IPs between 1.25 and 7.44 then i can think of a big wildcard mask
i’m thinking of using a mask of 0.0.7.255
this would be perfect for the range in question.
if there are no problems filtering the IPs from 10.0.0.1 to 10.0.1.24 then i can use this wildard mask
if there are no problems filtering the IPs from 10.0.7.45 to 10.0.7.254 then i can use this wildcard mask
if everything is ok then my answer is: 10.0.0.0 0.0.7.255
case 2:
i want to filter IPs starting at 10.0.1.25, ending at 10.0.1.52
and
filter IPs starting at 10.0.7.34, ending at 10.0.7.45
now i have to think of 2 wildcard masks.
the first would be a block of 0.63
the second would be a block of 0.15
*********************
what’s with the block sizes?
they are the reverse of subnet masks.
subnet masks are somthing like:
0 – 256 IPs (we count the subnet ID and the broadcast IP too)
128 – 128 IPs
192 – 64
224 – 32
240 – 16
248 – 8
252 – 4
254 – 2 (not usable if in 4th octet)
255 – 1 (not usable if in 4th octet)
now let’s think of wildcard masks. they work this way:
you start at a certain point, you cover a certain range.
usable blocks:
0 – only this one
1 – not usable in first octet
3 – filter 4 IPs, starts at a multiple of 4 (0 is a multiple of 4 too! 0*4=0!)
7 – filter 8 IPs, starts at a multiple of 8
15 – filter 16 IPs, starts at M16
31 – filter 32, starts at M32
63 – filter 64, starts at M64
127 – filter 128, starts at M128 (starts at 0 or 128)
255 – filter 256 IPs (counting from 0 to 255 you have 256 IPs). this also translates to “all possible values in this octet and the octets after this one
you see the relation between them?
my subnetwork is 172.20.7.32 /28 = 255.255.255.240 (has 16 IPs, 14 usable)
if i want to filter this entire subnet i will use which wildcard mask? 0.0.0.15 (filters 16 IPs).
from where does the filtering start? from the multiple of 16: 32.
172.20.7.32 0.0.0.15
my subnetwork is 62.34.34.0/24
i want to filter from 62.34.34.8 to 62.34.34.15
look again: from 8 to 15. those could very well go into a subnet of their own, right? a subnet with a mask of 248.
we do this simple math: 255-248=7.
wilcard to use: 0.0.0.7 (set 7 in 4th octet because that where we are filtering on this case)
starting IP? multiple of (7+1 = 8). we start at 8.
subnet: 23.223.65.0 /16
i want to filter: from 23.223.65.0 to 23.223.65.65
i will use 3 wildcard masks for this:
0.0.0.63 to filter from .0 to .63
0.0.0.0 to filter .64
0.0.0.0 to filter .65
i could’ve used a big wildcard mask: 0.0.0.127, but then i had problems with the IPs outside my interest: from .66 to .126
******************
i hope this helps you, cheers
mistype:
usable blocks:
0 – only this one
1 – not usable in *last* octet
Cleared CCNA today, so funny 1000/1000 is my score, ACL, EIGRP, VTP (all here in 9tut), 53 questions, about 3 to 5 question not in collisio/acme but manageable anyway. Thanks 9TUT CCIP here i come.
@xallax
in the question 2 the option A is also true as i think so !!!
A – Attempts to telnet to the router would fail
B – It would allow all traffic from the 10.4.4.0 network
because we have denied the telnet session in the access list so if we will request for the telnet to the router then it will deny so in this way option A is also true?
is it true as per the my thinking or not? please explain …. help me out!!!!!!!
What is valid reason for a switch to deny port access to new devices when port security is enabled?
A. The denied MAC addresses have already been learned or confgured on another secure interface in the
same VLAN.
B. The denied MAC address are statically configured on the port.
C. The minimum MAC threshold has been reached.
D. The absolute aging times for the denied MAC addresses have expired.
answer in dump was given B. but I think it is C. so please someone clarify my problem
@piyush
there is the only one way to deny the new device from the existing switch by the configuring the static port security to the switch……
so in the question they have writen “valid reason for a switch to deny port access to new devices” ….. in this way they want the reason and the reason is only one that is static port security dont allow the new device untill we manually allow that device on the perticular port of switch……so the answer is B ans surly corect piyush….
@xallax
i would got in the wrong way in the question 2 so i understud now and the answer which is given is true!!!
@piyush @suraj
this question has been asked and answered on todd lammle’s forum
the answer is A.
http://www.lammle.com/discussion/showthread.php?s=e0e332e4f9464ae4b46c4a122092e2b4&p=10222&mode=linear#post10222
@xallax i read the post but what is wrong with option C. if maximum number of mac address that are allowed by switch are learned then also it will not allow the new device to be connected… please explain
@xallas my mistake now i m sure abt answer. thanks for help :-)
Hi all,
i will going to take my exam by the end of october…….can anybody tell me the latest dumps??
Is collisio the latest……….????
I am preparing through it…….
hi please anyone help me i am going to give the exam on 15 oct please tell me which dumps should i go for & lab also
if u have dumps please send me the link
What happen if I have this subnet 172.16.0.0 / 23
I can have a host ip address starting on 0
this is my first subnet 172.16.0.0 to 172.16.2.255
so the ip add 172.16.1.0 is a use host ip address… you can apply it
I think the ans A to Q3 is the correct because the access-list 115 don’t use an specify protocol. Plus the subnet on s0/0/0 dont match the requirements of the crazy: permit ip 0.0.0.0 255.255.255.0 any.
I apply this ip to my computer with no problem
ip 172.16.1.0
mask 255.255.254.0
default gateway 172.16.0.1
I am confused, can someone please explain me 1 question, as per downloaded sim, question says 106 to be removed and add in 104, but 104 does permit ping, so how is 104 addition is valid, please help.
@Ram
The following 2 lines fix the requirement by allowing Ping.
access-list 104 permit icmp any any echo
access-list 104 deny icmp any any echo-reply
access-list 104 permit tcp any any eq ftp
access-list 104 deny tcp any any eq telnet
access-list 104 permit icmp any any echo
access-list 104 deny icmp any any echo-reply
access-list 104 permit ip any any
i am going on 21 oct for exam plzzzzz help me in my exam sims and dums i am confused so plz tel me urgently plzzzzzzzzzzzzz frnds
umar.raza03@gmail.
plzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz
shall we answer the 2 & 3 questions without doing sim in real exam
@9tut or Xalax:::::from where can i download the packet tracer v5.3 so that i can open up the labs???