CCNA – Access List Questions 2
Here you will find answers to Access list Questions – Part 2
Note: If you are not sure about Access list, please read my Access list tutorial.
Question 1
Refer to the exhibit. What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
| router#show access-lists Extended IP access list 110 10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet 20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp 30 deny tcp 172.16.0.0 0.0.255.255 any eq http 40 permit tcp 172.16.0.0 0.0.255.255 any |
A. Traffic will be dropped per line 30 of the ACL.
B. Traffic will be accepted per line 40 of the ACL.
C. Traffic will be dropped, because of the implicit deny all at the end of the ACL.
D. Traffic will be accepted, because the source address is not covered by the ACL.
Answer: C
Explanation
The syntax of an extended access list is:
access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port]
Notice that in our access list, the network 172.16.0.0 0.0.255.255 is specified as the source but the question asks about “HTTP traffic coming from the Internet that is destined for 172.16.12.10″, which means 172.16.0.0 0.0.255.255 is the destination network. So in this case there is no match in our access list and the traffic will be dropped because of the implicit deny all at the end of the ACL. It is surely a tricky question!
Question 2
Refer to the exhibit. Which statement describes the effect that the Router1 configuration has on devices in the 172.16.16.0 subnet when they try to connect to SVR-A using Telnet or SSH?

A. Devices will not be able to use Telnet or SSH.
B. Devices will be able to use SSH, but not Telnet.
C. Devices will be able to use Telnet, but not SSH.
D. Devices will be able to use Telnet and SSH.
Answer: B
Explanation
Let’s analyze the access list 100:
+ 10 permit tcp 172.16.16.0 0.0.0.15 host 172.16.48.63 eq 22: allows TCP traffic from network 172.16.16.0/28 to access host 172.16.48.63 with a destination port of 22 (SSH)
+ 20 permit tcp 172.16.16.0 0.0.0.15 eq telnet host 172.16.48.63: allows TCP traffic from network 172.16.16.0/28 with a source port of 23 (telnet) to access host 172.16.48.63
Notice that if a device wants to telnet (or SSH) to SVR-A server it must use the destination port of 23 (or 22), not a source port of 23 (or 22).
Access list 100 is applied on the inbound direction of Fa0/0 so it will only filter traffic from 172.16.16.0 subnet to the SVR-A server.
Access list 101 is very similar to access list 100 but it is applied on the inbound direction of Fa0/1 so it will filter traffic from SVR-A server to 172.16.16.0 subnet. In ACL 101:
+ 10 permit tcp host 172.16.48.63 eq 22 172.16.16.0 0.0.0.15: allows TCP traffic from host 172.16.48.63 with a source port of 22 (SSH) to access network 172.16.16.0/28.
+ 20 permit tcp host 172.16.48.63 172.16.16.0 0.0.0.15 eq telnet: allows TCP traffic from host 172.16.48.63 to access network 172.16.16.0/28 with a destination port of telnet.
Notice that the returned traffic from SVR-A to network 172.16.16.0/28 (resulting from telnet or SSH session) will have a source port of 23 (Telnet) or 22 (SSH)
In conclusion, the first statements of each ACL will allow devices to “SSH” to SVR-A. But they can’t telnet because of the implicit deny all at the end of the ACL.
In this question, the second statements of each ACL can be considered “wrong” if we intend to filter telnet or SSH traffic and they have no effect on the Telnet or SSH traffic.
Question 3
Refer to the exhibit. Which three variables (router, protocol port, and router ACL direction) apply to an extended ACL that will prevent student 01 from securely browsing the internet?
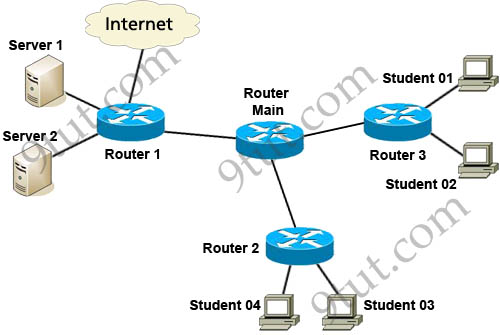
A. OUT
B. Router 3
C. HTTPS
D. IN
E. Router 1
Answer: B C D
Explanation
There are 3 routers we can place this access list: Router 1, Router Main and Router 3 but in theory, an extended access list should be placed close to the source -> Router 3 is the best choice -> B is correct.
The traffic we need to filter here is “securely browsing the internet” so it is HTTPS -> C is correct.
Finally we should apply this access list to the inbound direction so that Router 3 will filter this traffic before making routing decision. It helps save processing resources on Router 3 -> D is correct.
Question 4
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: A F
Explanation
Dynamic ACLs have the following security benefits over standard and static extended ACLs:
+ Use of a challenge mechanism to authenticate individual users
+ Simplified management in large internetworks
+ In many cases, reduction of the amount of router processing that is required for ACLs
+ Reduction of the opportunity for network break-ins by network hackers
+ Creation of dynamic user access through a firewall, without compromising other configured security restrictions
(Reference: CCNA Exploration 4 – Dynamic ACLs)
Question 5
Which command shows if an access list is assigned to an interface?
A. show ip interface [interface] access-lists
B. show ip access-lists interface [interface]
C. show ip interface [interface]
D. show ip access-lists [interface]
Answer: C
Explanation
The output of “show ip interface [interface]” command is shown below:
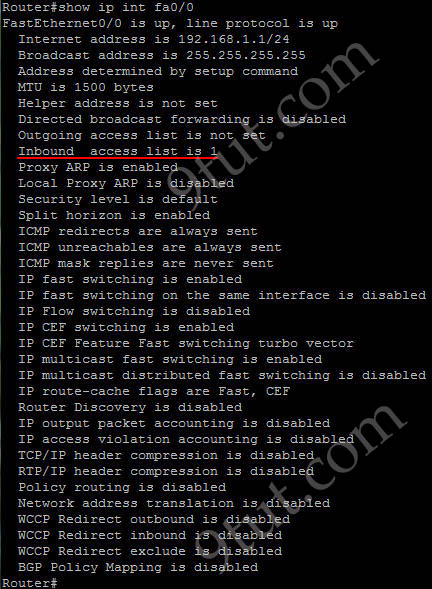
In the output we can see the access list 1 is applied to this interface on inbound direction.
Question 6
Which item represents the standard IP ACL?
A. access-list 50 deny 192.168.1.1 0.0.0.255
B. access-list 110 permit ip any any
C. access-list 2500 deny tcp any host 192.168.1.1 eq 22
D. access-list 101 deny tcp any host 192.168.1.1
Answer: A
Explanation
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
Question 7
Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 8
A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?
A. reflexive
B. extended
C. standard
D. dynamic
Answer: D
Explanation
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml
Question 9
Which parameter standard access list takes into consideration for traffic filtering decisions?
A. Source MAC address
B. Destination IP address
C. Destination MAC address
D. Source IP address
Answer: D
Question 10
In which solution is a router ACL used?
A. protecting a server from unauthorized access
B. controlling path selection, based on the route metric
C. reducing router CPU utilization
D. filtering packets that are passing through a router
Answer: D



This guy butt sahib, is Nawaz’s relative and he made lot of money in Lahore model Town with the help of LDA. He is one of the Qabza groups of PMLN….
I was reading through some of your articles on this internet site and I conceive this site is really informative! Retain posting. Cornelius posted an update http://bbs.6ug.net/read-htm-tid-126569.html
hi everyone, at last, in q4, which are the correct answer: A&F or D&F?
Question number 2 is not clear with the explanation given.
Can anyone explain it elaborately?
please look at question 4 it’s differ from the dumb , in the dumb the solution is D,F please support
I agree with Anonymous statement on April 3, Q2 is not clear. Anyone with a better explanation why the answer is B and not D?
Regarding Q2
traffic will be filtered 2 times, I mean once per ACL
ACL 100 is inspecting traffic coming from LAN 172.16.16.0/28 going to the SSH/Telnet Server, so a packet would look like this for SSH:
source IP: 172.16.16.20 srcport 6372 dst IP 172.16.48.63 dst port 22
for telnet :
source IP: 172.16.16.20 srcport 6372 dst IP 172.16.48.63 dst port 23
ACL 101 will inspect the REPLY, so traffic would look like:
src IP 172.16.48.63 srcport port 22 dst IP: 172.16.16.20 dstport 6372
for telnet :
src IP 172.16.48.63 src port 23 dstIP: 172.16.16.20 dst 6372
if you compare the packets against each line of the ACL´S you will see that line 20 on ACL 101 is NOT allowing the TELNET response, it seems like is allowing host 172.16.48.63 to INICIATE traffic against the network 172.16.16.0/28.
in other words line 20 on ACL101 allos this kind of packets:
src IP 172.16.48.63 srcport port 6372 dst IP: 172.16.16.20 dstport 23
Hope this Helps
hi i’m taking exam in few day’s
hi
i’m taking exam in few day’s
i’m taking exam,
what should i prepare well plz help me,
i’m confuesing in vlsm,cidr,subneting.
172.16.48.63/20 es una direccion de difusion es una direccion ip invalida
teniendo 172.16.48.63/20 respuesta A
lista de acceso extendida siempre en el lado de la direccion de origen
en este caso la direccion de origen es SVR – A 172.16.48.63/20
Y COMO LA LISTA DE ACCESO 100 SE CONFIGURO EN fa0/0 el router filtra el acceso
la lista de acceso 101 se configuro correctamente ojo
en la primera linea permite utilizar SSH
en la segunda linea no puede hacer telnet a causa de la negación implícita todo al final de la ACL.
Hi there. Taking CCNA in a weeks. Can anyone send me latest dumps?
spymrigen@gmail.com
In Q#2
Am I understand correctly that when pocket returns from server it has- SSH source port- because
first statement in ACL 101 is port 22 not telnet. So it looks only at first statement.
Please response if this is correct.
q6 in today exam
hello everybody.Q4 is correct it is incorrect on most of dumps ,now i just read about it from CCNA exploration 4..
have a look..
Benefits of Dynamic ACLs
Dynamic ACLs have the following security benefits over standard and static extended ACLs:
1.Use of a challenge mechanism to authenticate individual users
2.Simplified management in large internetworks
3.In many cases, reduction of the amount of router processing that is required for ACLs
4.Reduction of the opportunity for network break-ins by network hackers
5.Creation of dynamic user access through a firewall, without compromising other configured security restrictions
answer is A and F..
Hi guys i’m taking the exam on monday can u pliz send me some latest dumps..thankyou all my email address is gchalwe@yahoo.com
Pliz i will sit for the exam next month, can someone send me the latest dumps on email: olesimbe@yahoo.com
i need a help i need latest ccna dump and i will appreciate that
this is my email (mca.1990@hotmail.com)
my exam is too close
thanks guys
Hola a todos creo q la pregunta 2 al principio me confundio pero despues de analizarla bien no es tan complicada.
**********
En el punto 20 de la 100 podemos leerlo asi: se permite acceso de la red 172.16.16.0/28 con puerto de ORIGEN Telnet a el SERVER 172.16.48.63 (no especifica puerto DEST).
**********
En el punto 20 de la 101 podemos leerlo asi: se permite acceso del SERVER 172.16.48.63 a la red 172.16.16.0/28 puerto ORIGEN telnet
**********
En conclusion en ninguna de las sentencias especifica q tiene acceso al Server al puerto de destino telnet.
If some body has the lastest dumps please share them with me I will appreciate it. CCNA certificate comes soon. jockrlos16@hotmail.com
Hola si alguien tiene los ultimos dumps para poder practicar les agradeceria si me los pueden compartir gracias. jockrlos16@hotmail.com
regarding ques 1:
traffic being dropped solely matters upon which direction the access list is set. this ques can’t assume that the acl is set both directions. this is wrong. this acl was made for one direction only that is towards the isp not towards the host. this ques is meaningless unless it specifies the network layout and the TWO interfaces it is applied on by a foolish administrator
Anonymous Apr 5 2013,
def not D for Q4 – that’s for time-based acls
Q10 why is the answer D and not A
plz help on this
access list 135 deny tcp 172.16.16.0 0.0.15.255 172.16.32.0 0.0.15.255 eq telnet
access-list 135 permit ip any any
ACL is used to control incoming packet on E0, which three statement are true
a) Address 172.16.1.1 will b denied telnet access to address 172.16.37.5
b) Address 172.16.31.1 will b permit ftp access to address 172.16.45.1
c) Address 172.16.1.1 will b permit telnet access to address 172.16.32.1
d) Address 172.16.16.1 will b permit telnet access to address 172.16.32.1
e) Address 172.16.16.1 will b permit telnet access to address 172.16.50.1
f) Address 172.16.30.12 will b denied telnet access to address 172.16.32.12
ans: b,c, e why f is wrong?
@anonymous, the range of ’172.16.16.0 0.0.15.255′ is from 172.16.16.1 to 172.16.31.255 while ’172.16.32.0 0.0.15.255′ is from 172.16.32.1 to 172.16.47.255. Looking at option F address 172.16.30.12 falls under the range 172.16.16.1 to 172.16.31.255, so it’s gonna be denied based on the first access list command. Hope that’s clear
Q2. guys the command does not have a “permit any any” at the end so hence it does not matter it would not be able to use any other protocol ? this is what i think ? if 9tut could comment on it that would be great ?
I do agree with anonymous June 2nd 2013, Q1 The ACL doesn’t work in more than one direction actually, however I did the exam one year ago and the kind of responses giving here are correct.
A la pregunta esta
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.+
Is erroneus, I think that is the D and F.
someone can confirm?
Yo, that’s what’s up trufthully.
Dumps are good tools to review for the exam, but be certain that the answers are correct. I came across this question, and don’t agree with the answer. Any one have any thoughts on this?
A network administrator has configured access list 173 to prevent Telnet and ICMP traffic from reaching a server with the address of 192.168.13.26. Which commands can the administrator issue to verify that the access list is working properly? (Choose three)
A. Router# ping 192.168.13.26
B. Router# debug access-list 173
C. Router# show open ports 192.168.13.26
D. Router# show access-lists
E. Router# show ip interface
The answers that are stated correct are (A), (D), (E). By performing (D) and (E), you’re looking at the configuration. But by performing (A), you’re not really testing the access list because your pinging locally from the router. The access list will not deny outbound traffic that is generated locally. How does this assist you in ensuring the ACL is working properly?
q3 in exam today
hi admin,
i appreciate the assistance uv been in helping us with ccna questions for study…io would also ask sincerely that you try update the questions on this site to make them more relevant to us the new ccna takers, and also update the sim questions…wld luv to get a reply on my comment.
thanks a lot still.
Thanks 9tut for this great ACL exam prep questions.. it really helps reinforce this topic very glad..:)
hello ! 9tut Guys, thenx so much for ur awesome and unquantifiably biulful materials,GLORY TO GOD FOR UR EXISTENCE, I passed yesterday with 881/1000, all questions were from 9tut and spike dumps, with approximately minor modifications.
simulations were : ACCESS-LIST2, VTP, AND EIGRP-
(EIGRP sim had alot of problems in configurations, the second router was not responding during confinguration so i decided to leave it),
get latest dump from.
9tut.weebly .com
(remove space before .com)
on question 2
subnet cam ssh to server
but server cannot ssh to subnet
subnet can not telnet to server
but server can telnet to subnet
its a crap question.
as you have to assume it means telnet and ssh from subnet to server
and ignore the other way round.
answer b is only correct when telnetting or ssh ing from subnet to server.
Hi guys,
FYI – Q7 , 8 , 9 were in the exam today.
consider a router with an ethernet e0 and serial s0 . An inbound acl is applied to e0 .
Does it filter even the packets that are coming from the serial and entering into the e0. No acl is applied on s0 . Please HELP.
THe Q1 and the previous ACL page Q7 has kind of confused me ..
@ jose zamora and any one
use the following links to get the latest dumbs
http://www.examcollection.com/cisco
/Cisco.ActualTests.640-802.v2013-01-28.by.Spike.662q.vce.file.html and http://www.examcollection.com/cisco/Cisco.ActualTests.640-802.v2013-01-28.by.Spike.662q.vce.file.html
I got this site from my pal who shared with me regarding this site and now this time I am visiting this website and reading very informative articles or reviews here.
isabel marant sneakers http://www.isabelmarantonlinemall.com/
I am sorta annoyed at the way you normally place the ACL on the inbound direction (as per Q3) but for the ACL Lab its on the outbound direction. Yuk.
9tut, for Q3, are you sure the answer of Q3 is correct answer in CCNA exam???
Extended ACL is usually put close to source in book, but if you put there, how will you block internet access for HTTPS from student 01 to internet unless you can not specify serial port of Router 1 to internet? Or does this question just ask us to assume there is no HTTPS server inside LAN?
Unless anyone got 1000 score in CCNA exam and marked B C D, I don’t see it’s correct answer for this question
9tut, for Q2, When host connects to ssh and telnet port to the server, it uses randomly generated ports. In order for server to respond to the request, how ACL works with this? If port is specified as service name ‘telnet’, does router identifies automatically the packet is for returning telnet request??? If not, shouldn’t all outgoing ports have to be open for LAN with servers?
Hello Guys I hope you will be fine there. I have CCNA (640-802) and CCNA security (640-554) Vouchers on special discount of 58% for World wide, with six months expiry date till you purchase. Each voucher cost 70USD.
Details Required For CCNA Voucher For Discount Processing:
1-Full Name. 1st Name & Last Name (as you want to appear on certificate & documents)
2-Country.
3-City.
4-State.
5-Pin Code (or Area Code)
6-Residential Address (or where you can collect your Certificate or further correspondence
can be received)
7-Date of birth
Add me on Skype through this information which is written below:
Skype Name: rockon660
you can also email me at this email address which is written below:
madeelqaiser@gmail.com
If you have any Questions feel free to contact me.
Thanks,
Best regards,
Adeel
Guys please send me latest dumps ccna640-802 as i am taking the exam on mid of september 13 can u please send me latest dumps. My email address is atpl21@yahoo.com.
Thanks
I have the exam on 10th, can anyone send me the latest dumps please, shujaansari@outlook.com
q 10 in today exman !!
Phat March 30th, 2013 hi everyone, at last, in q4, which are the correct answer: A&F or D&F?
Hi guys for those who have passed ccna 640-802 which dump is more reliable the one from spike or acme? If u have new dumps kindly send to cacsalanga@yahoo.com