CCNA – Access List Questions 2
Here you will find answers to Access list Questions – Part 2
Note: If you are not sure about Access list, please read my Access list tutorial.
Question 1
Refer to the exhibit. What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
| router#show access-lists Extended IP access list 110 10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet 20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp 30 deny tcp 172.16.0.0 0.0.255.255 any eq http 40 permit tcp 172.16.0.0 0.0.255.255 any |
A. Traffic will be dropped per line 30 of the ACL.
B. Traffic will be accepted per line 40 of the ACL.
C. Traffic will be dropped, because of the implicit deny all at the end of the ACL.
D. Traffic will be accepted, because the source address is not covered by the ACL.
Answer: C
Explanation
The syntax of an extended access list is:
access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port]
Notice that in our access list, the network 172.16.0.0 0.0.255.255 is specified as the source but the question asks about “HTTP traffic coming from the Internet that is destined for 172.16.12.10″, which means 172.16.0.0 0.0.255.255 is the destination network. So in this case there is no match in our access list and the traffic will be dropped because of the implicit deny all at the end of the ACL. It is surely a tricky question!
Question 2
Refer to the exhibit. Which statement describes the effect that the Router1 configuration has on devices in the 172.16.16.0 subnet when they try to connect to SVR-A using Telnet or SSH?

A. Devices will not be able to use Telnet or SSH.
B. Devices will be able to use SSH, but not Telnet.
C. Devices will be able to use Telnet, but not SSH.
D. Devices will be able to use Telnet and SSH.
Answer: B
Explanation
Let’s analyze the access list 100:
+ 10 permit tcp 172.16.16.0 0.0.0.15 host 172.16.48.63 eq 22: allows TCP traffic from network 172.16.16.0/28 to access host 172.16.48.63 with a destination port of 22 (SSH)
+ 20 permit tcp 172.16.16.0 0.0.0.15 eq telnet host 172.16.48.63: allows TCP traffic from network 172.16.16.0/28 with a source port of 23 (telnet) to access host 172.16.48.63
Notice that if a device wants to telnet (or SSH) to SVR-A server it must use the destination port of 23 (or 22), not a source port of 23 (or 22).
Access list 100 is applied on the inbound direction of Fa0/0 so it will only filter traffic from 172.16.16.0 subnet to the SVR-A server.
Access list 101 is very similar to access list 100 but it is applied on the inbound direction of Fa0/1 so it will filter traffic from SVR-A server to 172.16.16.0 subnet. In ACL 101:
+ 10 permit tcp host 172.16.48.63 eq 22 172.16.16.0 0.0.0.15: allows TCP traffic from host 172.16.48.63 with a source port of 22 (SSH) to access network 172.16.16.0/28.
+ 20 permit tcp host 172.16.48.63 172.16.16.0 0.0.0.15 eq telnet: allows TCP traffic from host 172.16.48.63 to access network 172.16.16.0/28 with a destination port of telnet.
Notice that the returned traffic from SVR-A to network 172.16.16.0/28 (resulting from telnet or SSH session) will have a source port of 23 (Telnet) or 22 (SSH)
In conclusion, the first statements of each ACL will allow devices to “SSH” to SVR-A. But they can’t telnet because of the implicit deny all at the end of the ACL.
In this question, the second statements of each ACL can be considered “wrong” if we intend to filter telnet or SSH traffic and they have no effect on the Telnet or SSH traffic.
Question 3
Refer to the exhibit. Which three variables (router, protocol port, and router ACL direction) apply to an extended ACL that will prevent student 01 from securely browsing the internet?
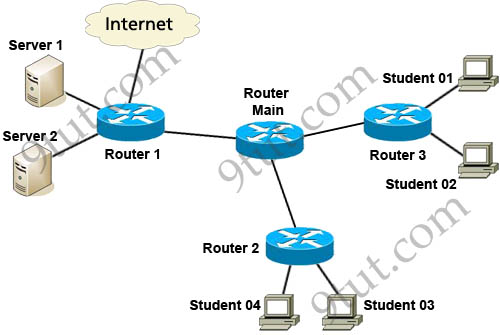
A. OUT
B. Router 3
C. HTTPS
D. IN
E. Router 1
Answer: B C D
Explanation
There are 3 routers we can place this access list: Router 1, Router Main and Router 3 but in theory, an extended access list should be placed close to the source -> Router 3 is the best choice -> B is correct.
The traffic we need to filter here is “securely browsing the internet” so it is HTTPS -> C is correct.
Finally we should apply this access list to the inbound direction so that Router 3 will filter this traffic before making routing decision. It helps save processing resources on Router 3 -> D is correct.
Question 4
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: A F
Explanation
Dynamic ACLs have the following security benefits over standard and static extended ACLs:
+ Use of a challenge mechanism to authenticate individual users
+ Simplified management in large internetworks
+ In many cases, reduction of the amount of router processing that is required for ACLs
+ Reduction of the opportunity for network break-ins by network hackers
+ Creation of dynamic user access through a firewall, without compromising other configured security restrictions
(Reference: CCNA Exploration 4 – Dynamic ACLs)
Question 5
Which command shows if an access list is assigned to an interface?
A. show ip interface [interface] access-lists
B. show ip access-lists interface [interface]
C. show ip interface [interface]
D. show ip access-lists [interface]
Answer: C
Explanation
The output of “show ip interface [interface]” command is shown below:
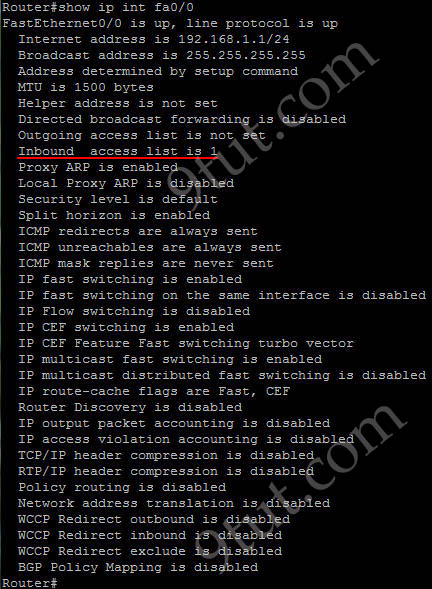
In the output we can see the access list 1 is applied to this interface on inbound direction.
Question 6
Which item represents the standard IP ACL?
A. access-list 50 deny 192.168.1.1 0.0.0.255
B. access-list 110 permit ip any any
C. access-list 2500 deny tcp any host 192.168.1.1 eq 22
D. access-list 101 deny tcp any host 192.168.1.1
Answer: A
Explanation
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
Question 7
Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 8
A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?
A. reflexive
B. extended
C. standard
D. dynamic
Answer: D
Explanation
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml
Question 9
Which parameter standard access list takes into consideration for traffic filtering decisions?
A. Source MAC address
B. Destination IP address
C. Destination MAC address
D. Source IP address
Answer: D
Question 10
In which solution is a router ACL used?
A. protecting a server from unauthorized access
B. controlling path selection, based on the route metric
C. reducing router CPU utilization
D. filtering packets that are passing through a router
Answer: D



hi,
of all the above questions, which are the most important?
have any of the above questions come in the recent CCNA?
thx
i am afraid to understanding ACL list question’
Need a proper explanation for Question No 2 . if we take the implicit deny at the end of the access list in to consideration then answer A is correct as there is no permit ip any any.
if we dont consider the implicit deny and the permit ip any any then anser D is correct as both connections are allowed. Can some one pls explain how is it that answer B is correct.
@ Dez
I did not see this question on the exam last week. I retake the exam(CCNA) on Tuesday. It is a very tricky question in regards to the sh ip access-list output line 2(extended access-list 20 permit tcp 172.16.16.0 eq telnet….etc…it is correct but you have to look at where the source is and the direction it is going.
Other than that everything else is straight forward.
I don’t think the question will be this difficult on the exam. Maybe ICND but not CCNA
@Anybody
@9tut
Whether can we use tab key to fill the full cmds??
Also can we use shortcut cmds in exam like we use in gns3 or packet tracer??
eg:sh run, sh ip int br, sh ip rout…
thanks.
TY 9tut.
Today I have passed the CCNA. (860/825)
50 questions 3 labs (VTP, EIGRP, ACL). 35 from 9tut.
Also thanks a lot Brar and Sekhar (still valid from examcollection)
Ty again 9tut
Brar and Sekhar’s examcollections files are not openig , it showing only five ques.
Q1- is not complete.
“HTTP traffic coming from the Internet that is destined for 172.16.12.10 ” can be either allowed or denied depending on “which interface of the router and in which direction” the ACL is applied.
Today I have passed with 960/1000……..Thanks to GOD
Thanks to 9TUT …….Sekhar……P4S..
SIM=VTP,EIGRP same as 9TUT & Access list same as 9TUT…
hi,
In question one:
“HTTP traffic coming from the Internet that is destined for 172.16.12.10″, the ACL in the question blocked the answer to internet:
IP internet (request) >>>> server 172.16.12.10 ACL no apply
Server 172.16.12.10(Answer) >>>> IP internet ACL apply
So, the alternative will be A?…. I will wait ur opinion…i assume that ACL is applied for default (out).
Q4 in the dumb the correct answer is B & F …here is A & F any explanation to this which answer is the correct one?????/
@Anybody
@9tut
Question 4
It exists:
-Standard ACL
-Extended ACL
-Reflexive ACL
-Dynamic ACL
-Time-based ACL
D. is a good answer ???
Q2,
Is it ok to write “eq 22″ in between IP addresses, rather than at the end (IS THIS CONTEXT OK..!!)..?
And this Q2 is MFing me, why will ACL deny traffic if LINE 20 permits it…
There is no reaching till the end, it will permit telnet or ssh traffic in LINES 10 & 20. AM I RIGHT…?
PLS help ffs….
Archit, can you be more clear?
@the people those who have pass the exam
@9tut
Whether can we use tab key to fill the full cmds??
Also can we use shortcut cmds in exam like we use in gns3 or packet tracer??
eg:sh run, sh ip int br, sh ip rout…
thanks.
Could someone send the last dumps? Thank you! mgiurni@gmail.com
Q4, I also think it should be D&F, any ideas? anyone?
@Archit:Q2: 2 points.
1. Extended ACL provides facility for SRC and DST ports
2. Telnet traffic has DST port=23, not source port=23 as in ACL100 line20. Same holds true for ACL101 line 20 – should have been SRC port=23.
Can someone send me new dumps PLEASE… my exam is next week… THANKS!!!
my email is asenriquezjr@yahoo.com
Q2… the wildcards are 0.0.0.15 in the ACLs. Shouldnt they be 0.0.15.255? Considering that the network is 172.16.16.0/20. If the network was 172.16.16.0/28 I think the ACLs would be right.
I dont know what the answer is… A (for most nework 172.16.16.0/20) or B (for 172.16.16.1 to 172.16.16.15).
Do v need to know dynamic ACL’s for CCNA?
is any change for the ccna exam ,i need explain please , 9tut, i will take the exam in two weeks ..
Valid Que :D
Q:9
what is the answer of Q 2?
q8 – valid!
To be honest the question 1 is incomplete and the ACL are bidireccional. It does not say where is applied. Answer A is as good as C.
Also, internet is not able to reach this network 172.16.12.10. because it is a private network.
I think question 1 is complete and the answer is right. Its quit simple when you examine the question. The question is: What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL. The keyword is HTTP traffic FROM THE INTERNET, DESTINED for 172.16.12.10; looking at the access-list, non of the source ip address of the entries is talking about traffic from the internet (i.e 0.0.0.0 255.255.255.255 or any). All the entries in the access-list makes reference to the source network 172.16.0.0 which is not what the question is asking about. Hence the implicit deny statement at the end of the access-list will deny any traffic (including traffic from the internet) apart from tcp traffic from 172.16.0.0. This makes answer C the correct answer
The application of the access-list on an interface makes a difference on how it works, but in this scenario (Question 1) you don’t have to know how it is implemented (i.e. IN/OUT) before you can answer the question. whether it is implemented IN or OUT is not directly relevant to the question.
Question 4.
Why below answer incorrect?
D. you can set a time-based security policy
Can someone explains me
What’s IN, and OUT = ACLS
please
mjahanzaib@hotmail.com please mail me latest Dumps . i am giving exam in next month thanks in advance
This is for those who needs latest dumps. This dumps and 9tut, its enough for you to pass exam. just remember me in your prayers. Best of luck…..
http://www.examcollection.com/cisco/Cisco.ActualTests.640-802.v2012-07-15.by.Sekhar.697q.vce.file.html
Q4 . A.F is correct.
D is time-based ACL.
Hi….
I prepare to pass ccna exam the first march…… please pray for me
Q3 / Question 3
A. OUT
B. Router 3
C. HTTPS
D. IN
E. Router 1
Answer: B C D
I chose A B C , this choice would be putting the ACL in the Serial interface of R3 hence it would be “out” and it would still function.
The decisive factor of choosing between BCD and ABC is that:
- “apply this access list to the inbound direction (Ethernet/FastEthernet) so that Router 3 will filter this traffic before making routing decision. It helps save processing resources on Router 3″
I need insights on this one, thank you!
thanks kkpp
Q4
E-F
By the cisco documentation, it’s also good against spoofing.
http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml
@Arturo Pacardo Jr
Hi..
If you apply the ACL to the serial interface, it will work.
However the Router will accept the packet–> look through its routing table to determine through which interface the packet should be forwarded–> then it checks the serial interface ACL and drops the packet.
*Extended ACL should be placed as close as possible to the destination in this case Router 1 in.
Basically as in many cisco questions there are many right answer, but only one of them is the most accurate one ;)
@Anon
I see. Thank you for clearing that one up!
@Anon
What you said:
“*Extended ACL should be placed as close as possible to the destination in this case Router 1 in.”
- this theory applies to Standard ACL, where you should put the ACL closest to the destination. Because on Standard ACL you only declare the source address unlike in Extended you can state the destination too.
It is contradicting to 9tut’s explanation. 9tut said:
“an extended access list should be placed close to the source -> Router 3 is the best choice -> B is correct.”
The reason of putting the extended ACL near the source is that:
” It helps save processing resources on Router”
can anybody help me with this one?
the exam asked to block other access from host C except telent and block every traffic from every other host from network to Finanace Web Server. Permit every traffic from networks to Public Web Server. Thanks!
Hi everyone,
Could you explain me about the answer for question 9?
Thanks in advance
Question 3 looks wrong.
We are asked to block students from “securely browsing the internet” for that answers should be:
A C E
If not we are blocking access to https on server 1 and server 2.
It doesn’t matter if it saves cycles on router’s processors, you are blocking more than you should. If you want to save cycles… you could prevent them from using the network completely…
if they were asking for block students from “using secure browsing”, the answers provided will be ok.
hello mostafa refer to Ur question the answer is no you cannot use tap key to fill the full cmds it wont work like that and you cannot use short cut either you have to put the full command in on the CLI hope it as
answers your question
@Arturo
Sorry, I meant Extended ACL should be placed as close as possible to the source, as you mentioned.
taking the exam on 14-03(thurs) PLS if u av d latest dump send it to femhab@yahoo.com
Superbly illmuintaing data here, thanks!
Does anyone knows are the dynamic and reflexive ACLs are tested in CCNA final exam?
thanks