CCNA – Access List Questions 2
Here you will find answers to Access list Questions – Part 2
Note: If you are not sure about Access list, please read my Access list tutorial.
Question 1
Refer to the exhibit. What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
| router#show access-lists Extended IP access list 110 10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet 20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp 30 deny tcp 172.16.0.0 0.0.255.255 any eq http 40 permit tcp 172.16.0.0 0.0.255.255 any |
A. Traffic will be dropped per line 30 of the ACL.
B. Traffic will be accepted per line 40 of the ACL.
C. Traffic will be dropped, because of the implicit deny all at the end of the ACL.
D. Traffic will be accepted, because the source address is not covered by the ACL.
Answer: C
Explanation
The syntax of an extended access list is:
access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port]
Notice that in our access list, the network 172.16.0.0 0.0.255.255 is specified as the source but the question asks about “HTTP traffic coming from the Internet that is destined for 172.16.12.10″, which means 172.16.0.0 0.0.255.255 is the destination network. So in this case there is no match in our access list and the traffic will be dropped because of the implicit deny all at the end of the ACL. It is surely a tricky question!
Question 2
Refer to the exhibit. Which statement describes the effect that the Router1 configuration has on devices in the 172.16.16.0 subnet when they try to connect to SVR-A using Telnet or SSH?

A. Devices will not be able to use Telnet or SSH.
B. Devices will be able to use SSH, but not Telnet.
C. Devices will be able to use Telnet, but not SSH.
D. Devices will be able to use Telnet and SSH.
Answer: B
Explanation
Let’s analyze the access list 100:
+ 10 permit tcp 172.16.16.0 0.0.0.15 host 172.16.48.63 eq 22: allows TCP traffic from network 172.16.16.0/28 to access host 172.16.48.63 with a destination port of 22 (SSH)
+ 20 permit tcp 172.16.16.0 0.0.0.15 eq telnet host 172.16.48.63: allows TCP traffic from network 172.16.16.0/28 with a source port of 23 (telnet) to access host 172.16.48.63
Notice that if a device wants to telnet (or SSH) to SVR-A server it must use the destination port of 23 (or 22), not a source port of 23 (or 22).
Access list 100 is applied on the inbound direction of Fa0/0 so it will only filter traffic from 172.16.16.0 subnet to the SVR-A server.
Access list 101 is very similar to access list 100 but it is applied on the inbound direction of Fa0/1 so it will filter traffic from SVR-A server to 172.16.16.0 subnet. In ACL 101:
+ 10 permit tcp host 172.16.48.63 eq 22 172.16.16.0 0.0.0.15: allows TCP traffic from host 172.16.48.63 with a source port of 22 (SSH) to access network 172.16.16.0/28.
+ 20 permit tcp host 172.16.48.63 172.16.16.0 0.0.0.15 eq telnet: allows TCP traffic from host 172.16.48.63 to access network 172.16.16.0/28 with a destination port of telnet.
Notice that the returned traffic from SVR-A to network 172.16.16.0/28 (resulting from telnet or SSH session) will have a source port of 23 (Telnet) or 22 (SSH)
In conclusion, the first statements of each ACL will allow devices to “SSH” to SVR-A. But they can’t telnet because of the implicit deny all at the end of the ACL.
In this question, the second statements of each ACL can be considered “wrong” if we intend to filter telnet or SSH traffic and they have no effect on the Telnet or SSH traffic.
Question 3
Refer to the exhibit. Which three variables (router, protocol port, and router ACL direction) apply to an extended ACL that will prevent student 01 from securely browsing the internet?
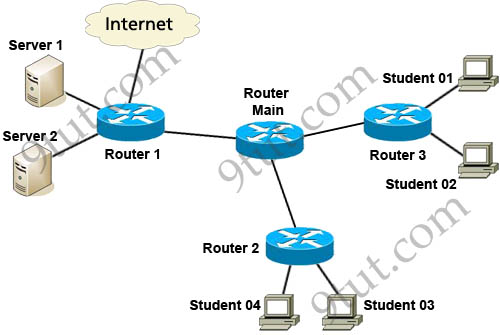
A. OUT
B. Router 3
C. HTTPS
D. IN
E. Router 1
Answer: B C D
Explanation
There are 3 routers we can place this access list: Router 1, Router Main and Router 3 but in theory, an extended access list should be placed close to the source -> Router 3 is the best choice -> B is correct.
The traffic we need to filter here is “securely browsing the internet” so it is HTTPS -> C is correct.
Finally we should apply this access list to the inbound direction so that Router 3 will filter this traffic before making routing decision. It helps save processing resources on Router 3 -> D is correct.
Question 4
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: A F
Explanation
Dynamic ACLs have the following security benefits over standard and static extended ACLs:
+ Use of a challenge mechanism to authenticate individual users
+ Simplified management in large internetworks
+ In many cases, reduction of the amount of router processing that is required for ACLs
+ Reduction of the opportunity for network break-ins by network hackers
+ Creation of dynamic user access through a firewall, without compromising other configured security restrictions
(Reference: CCNA Exploration 4 – Dynamic ACLs)
Question 5
Which command shows if an access list is assigned to an interface?
A. show ip interface [interface] access-lists
B. show ip access-lists interface [interface]
C. show ip interface [interface]
D. show ip access-lists [interface]
Answer: C
Explanation
The output of “show ip interface [interface]” command is shown below:
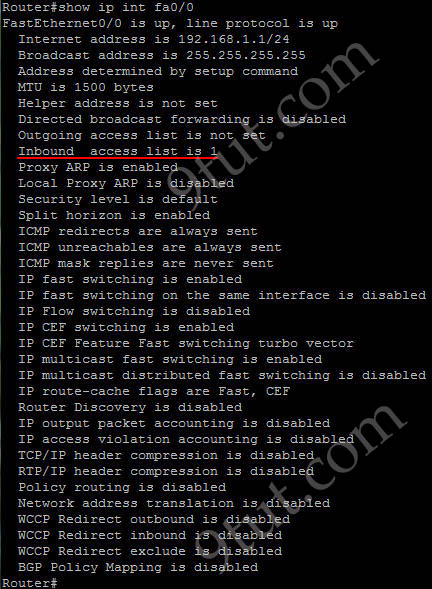
In the output we can see the access list 1 is applied to this interface on inbound direction.
Question 6
Which item represents the standard IP ACL?
A. access-list 50 deny 192.168.1.1 0.0.0.255
B. access-list 110 permit ip any any
C. access-list 2500 deny tcp any host 192.168.1.1 eq 22
D. access-list 101 deny tcp any host 192.168.1.1
Answer: A
Explanation
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
Question 7
Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 8
A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?
A. reflexive
B. extended
C. standard
D. dynamic
Answer: D
Explanation
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml
Question 9
Which parameter standard access list takes into consideration for traffic filtering decisions?
A. Source MAC address
B. Destination IP address
C. Destination MAC address
D. Source IP address
Answer: D
Question 10
In which solution is a router ACL used?
A. protecting a server from unauthorized access
B. controlling path selection, based on the route metric
C. reducing router CPU utilization
D. filtering packets that are passing through a router
Answer: D



Helllllloooooo guys. I passed my exam last Wednesday with a hit of 907. I was really happy. The questions were all the same from the dumps(SHEKAR). Only a very very few were new. Nonetheless the new qns had the same concept rounding off. The sims were the usual EIGRP, ACL & VTP. Only in ACL there was just alittle play around, this time it was host B. The EIGRP a new router was added. And well there is something to note on the VTP sim. The show mac-address-table is a bug to the sim. Therefore, you can either use show mac or rather show mac address-table.
My thanks to the 9tut online community, to my colleagues Denis & Rogers, my teachers, and to God almighty. I wish you all the best guys. I’m going for the CCNA security soon and am planning to take my exam this coming October. And I hope to eat Christmas with my CCNP. cheers and all the best!
Question 1.
Would that access list not be configured on an outbound interface? To deny parts of the 172.16.0.0 Network out. I didn’t think the internet would be processed by this access list as the internet would need an inbound access list? I would have chosen
D. Traffic will be accepted, because the source address is not covered by the ACL.
Can anyone explain to me why the internet would get processed by this access list?
Can someone post the link for shekar’s dump.I am unable to find.Thanks
We have access list configured for outbound from the source (172.16.0.0/22) to destination (any).but the question is about inbound so we dont have any access list configured for inbound destination ip 172.16.12.10 for the protocol http and FYI- at the end of the ACL all will be deny by default. So the traffic will be denyed whatever comes to 172.16.12.10.Hence the answer will be
C. Traffic will be dropped, because of the implicit deny all at the end of the ACL
@Anbu
If we don’t have an access list for the inbound destination 172.16.12.10 then why would it be denied by an implicit deny all of an access list that isn’t there?
Am I missing something? Can someone please explain why the internet would get processed by this access list?
9tut,
It seemed everybody is confusing with Q4. Referring comment from vikas at page1.
>>vikas
>>November 29th, 2011
>>@9tut
>>ur ans for qn 4 is wrong please justify..
>>9tut
>>November 29th, 2011
>>@vikas: The question wants to ask about characteristics of dynamic acl. Answer A is also >>correct but the best answers should be D & F.
Appreciate if you could update the answer. tq
Hello everyone,
I would appreciate if you could send me Shekar dumps to abdirisakoe@gmail.com
can anyone plz explain me the question no 4 more specifically?
can anyone plz explain me the question no 2 more specifically,the access-list 101 commands
?
Would Q3 not be A, C, E
A. OUT
C. HTTPS
E. Router 1
Surely by putting the access list on router 1 you would be preventing https access to the other servers?
Ignore the above. Wasnt thinking straight…..
look at question number 9,i think the answer is wrong.because traffic are filtered base on the destination ip address.the interface closet to the destination.the correct answer should be B
@arindam
Question 2
The Dirty Part iS With Ports…
For Access-100
Sequence 10 … Permit “Source”Hosts 172.16.16.x .. “Destination” Host 172.16.48.63 eq 22
So The Source Will b 172.16.16.any:xx Destination iS 172.16.48.63:22
“:xx” << Port Number
Sq 20 Permit "Source" 172.16.16.x:23 "Destination" Host 172.16.48.63
And When u Run a Program iT Takes a Random Port…So This iS a Wrong Statement..
ACL 101 .. iS The Same ACL But oN iT's Way Back ;) Source iS Destination And Destination iS a Source.
&The 2nd Statement iN 101 iS Wrong Cuz When u Run a Program..iT Gets a Random Port…. SAME
Hope i Didnt Missed Up :)
@Chris
Question 3
As 9tut Said: an extended access list should be placed close to the source ..<<< We Do iT Close To The Source Cuz iT's So Specific, Only Deny What We Ask For, So We Save The Router Process ;) And Make iT Close To The Source.
& Also Keep iN Mind: Standard Access List Should b Placed Close To The Destination So iT Doesnt Block Much Access Bcuz u Only Permit or Deny Source Address.
As u Say iF We Did iT oN Router1 …. iT Will Prevent YEA…But u Loaded The Processor oF The Routers With Useless Processes.
@Vola
Question 9!
The Syntax oF Standard ACL
Access-List (0-99) Permit/Deny SOURCE-IP-Address Wild-Card
Now The Question Asking What iS The Standard Access List Built oN ?
“Source Ip Address”
What u Ment By Ur Answer iS We Should Put iT Close To The Destination So We Dont Block Much Access.
Hope i Made iT Clear
nancy in the house, eat my shorts
just passed today, only studied 9tut, dumps – Jericho and brar – i dont even get past 100 questions in this dumps. Study the concepts, memorize commands and questions like features of protocols, etc. Make sure you can do subnetting mentally to reduce time. SIMS- EIGRP, ACL2 and VTP. Exact sims in 9tut with few changes in the given but same concept. Good luck to you all!!
THANKS Philip
Hello everyone,
I would appreciate if you could send me Shekar dumps to wayne.goeden@gmail.com
@Waynego
Here is the link of Shekar dumps
http://www.examcollection.com/cisco/Cisco.ActualTests.640-802.v2012-07-15.by.Sekhar.697q.vce
@9tut and Anbu, and Barry in regards to the question #1. I have talked to a CCIE and a CCNA person and they say the answer is letter D: Traffic will be accepted, because the source address is not covered by the ACL. Why? because in the question, there is no clue or it does not even mention the direction and we assume that it goes from the internal traffic (172.16.0.0) BUT if the traffic is coming from the OUTSIDE TO THE INSIDE, there is no ALCs listed so traffic will be passed, I even trief on a real device and it ALLOWED TRAFFIC, so I think everybody is getting wrong the quetion
@alex: The question states clearly: “if the traffic is processed by this ACL” so we should suppose that traffic coming from Internet is filtered by this ACL.
@9tut, thank you, this is a tricky question, damn, I hope not to see it in the test :)
Hello,
Can someone please send me the latest dumps? Thanks in advance. wdcruz20@gmail.com
Hello Folks,
can anyone tel me which dumps are valid now and which are the latest dumps? please send the latest dumps to harsharahul43@gmail.com or sriharsha.nori@gmail.com
Thanks
somebody email me the VCE program i can use for shekar dumps, or the downloaded ones i have cant open… kindly email me “krisstyle2@live.com”
Q 1
Q1
@berry,@all
remind the ACl rules :
* list is read from the top ( if match found it wont go to next line) yes there is invisible Implicit deny but at the Bottom of list. so if match found it wont go to next step
in Q1
access 110 deny tcp 172.16.0.0 0.0.255.255 any eq telnet
access 120 deny tcp 172.16.0.0 0.0.255.255 any eq smtp
access 130 deny tcp 172.16.0.0 0.0.255.255 any eq www ” ( match will found at this line ) ” hence it wont execute next step
access 140 permit tcp 172.16.0.0 0.0.255.255 any
It will deny all http traffic but ( not due to implicit deny. Because of access-group 130. only if you have applied in order )
@barry
i’m with you .. i think in Q1 answer D is the correct one because there is no ACL denying traffic from the internet to a destination of 172.16.12.10 …
the implicit deny denies all traffic FROM this host not TO it !!
anybody can justify the answer ??
@fadi
permit tcp any eq 80 172.16.10.12 0.0.0.0
if u type this command then only traffic will be allowed but this statement is missing, so due to implicit “deny all” at last….packet will be dropped
@9tut
Question 4:
Can the answer be D and F.
http://www.cisco.com/en/US/products/sw/secursw/ps1018/products_tech_note09186a00800a5b9a.shtml#lockandkey
Question 4: I also think D should be correct
D. you can set a time-based security policy.
A dynamic access list is an access list that allows temporary access after a user has authenticated with the router.
A dynamic access list could be created to give complete privileges for a predetermined amount of time. After a configured time limit expires, the session is closed and traffic is again denied. This form of access list is also referred to as lock-and-key security.
@Pavan, Dennis: Answer D is only correct for Time-based ACL:
http://www.cisco.com/en/US/products/sw/secursw/ps1018/products_tech_note09186a00800a5b9a.shtml#timebasedtimerange
@Barry ->> once you configured an access list, there is always an implicit deny all at the end of the access list. so all address thats not mention on the access list command will be denied, unless you put a permit ip any any on your acl command. i suggest, study more about access list so that you will know what is happening.
@fadi ->> here’s how access list works.. always remember, once you configured the access list, there is always a “DENY ALL THAT’S NOT LISTED AS PERMITTED ON THE ACCESS LIST WHETHER OUTBOUND OR INBOUND DIRECTION”. So the case on Q1, the network address 172.16.0.0 is being configured on the access list, there is a 3 times deny on this access list (Telnet, SMTP, HTTP) and the last one is that, 172.16.0.0 is permitted any TCP (that’s not being denied) to any destination, so! from 172.16.0.0 network going to any destination (Thru TCP) is PERMITTED!!!
So the question is, What will happen to HTTP traffic coming from internet to the destination 172.16.0.0??
Remember, once you configure an access list on one router, there is always! an INVISIBLE DENY ALL THAT’S NOT LISTED AS PERMITTED ON THE ACCESS LIST WHETHER OUTBOUND OR INBOUND DIRECTION…
**router#show access-lists
Extended IP access list 110
10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet
20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp
30 deny tcp 172.16.0.0 0.0.255.255 any eq http
40 permit tcp 172.16.0.0 0.0.255.255 any**
so there’s no command that it permits HTTP from internet going to 172.16.0.0, so it’s a deny. it will be drop. If you want to permit the HTTP from the internet, then apply
**permit tcp any any**
D. Traffic will be accepted, because the source address is not covered by the ACL. -> WRONG
it should be like this
D. Traffic will be dropped, because the source address is not covered by the ACL
POR FAVOR
hi,I have exam ccna after 4 days , please send the latest dumps
hani_2012_rad@yahoo.com
thank you
Hello friends,
Having my CCNA exam this week please send me latest dumps to k007umar@gmail.com,Thanks in advance…………….
in Q1 I think traffic will pass through the acl if the source address is the specified in the permit line otherwise it will be denied.
I have my CCNA exam the next week please send me latest dumps to dj_albertini33@hotmail.com.. Thanks and good luck
Hallo Ladies and Gentelman
I am taking my exams CCNA in December but I need help from you guys, Please could anyone send me latest exam so I could go through.
Many Thanks
Bashir
Hallo Ladies and Gentelman
I am taking my exams CCNA in December but I need help from you guys, Please could anyone send me latest exam so I could go through. email bashka23@hotmail.com
Many Thanks
Bashir
@Bashir look for latest dumps at http://www.examcollection.com 640-802.html
i cant open vce files any help please! kimcman10@yahoo.com
What is the latest Dump from ExamCollection as i Take the 640-802 exam on Friday…
please Mail me jmaneveldt@gmail.com
Hello JAY
JAY use Sekhar and brar dumps from http://www.examcollection.com and enjoy ur dumps
Rgds
ALEX*
@ALEX*
Hi
How do i use Sekhar and brar dumps? I’ve been trying them for the last 2 days but i can’t open them. The VCE software that i am downloading is said to be trial versions thus it’s only opening the first 5 questions only. Please do help am writing my CCNA on the 7th of Dec 2012. kevynjr001@gmail.com
Thanks in advance
Kevynjr!!
can someone please send me the latest dump?
sc.rpion13@hotmail.com
Hello Bashir even i do planned to attend ccna exam on dec end, So if u get latest send me to ovpremcss@gmail.com
hi , My exams CCNA today