CCNA Access List Sim
Question
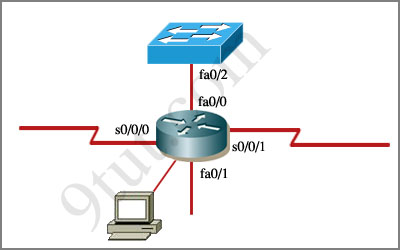
An administrator is trying to ping and telnet from Switch to Router with the results shown below:
Switch>
Switch> ping 10.4.4.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.3,timeout is 2 seconds:
.U.U.U
Success rate is 0 percent (0/5)
Switch>
Switch> telnet 10.4.4.3
Trying 10.4.4.3 …
% Destination unreachable; gateway or host down
Switch>
Click the console connected to Router and issue the appropriate commands to answer the questions.
Answer and Explanation
Note: If you are not sure about Access-list, please read my Access-list tutorial. You can also download this sim to practice (open with Packet Tracer) here: http://www.9tut.com/download/9tut.com_CCNA_Access_List_Sim.pkt
For this question we only need to use the show running-config command to answer all the questions below
Router>enable
Router#show running-config
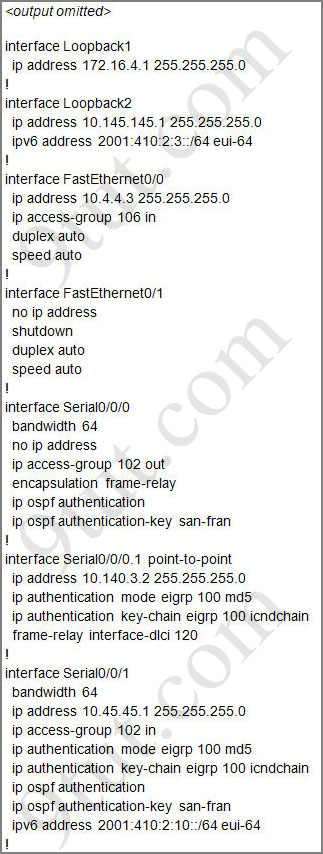
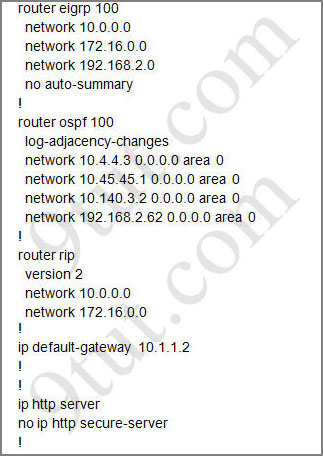
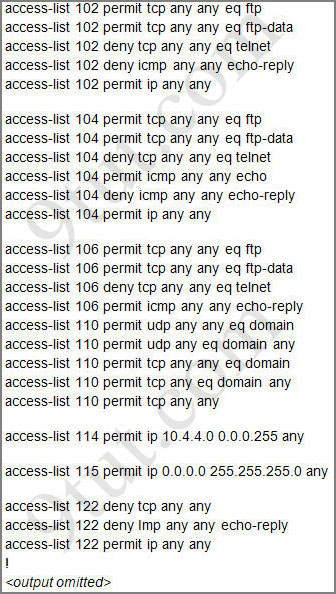
Question 1:
Which will fix the issue and allow ONLY ping to work while keeping telnet disabled?
A – Correctly assign an IP address to interface fa0/1
B – Change the ip access-group command on fa0/0 from “in” to “out”
C – Remove access-group 106 in from interface fa0/0 and add access-group 115 in.
D – Remove access-group 102 out from interface s0/0/0 and add access-group 114 in
E – Remove access-group 106 in from interface fa0/0 and add access-group 104 in
Answer: E
Explanation:
Let’s have a look at the access list 104:
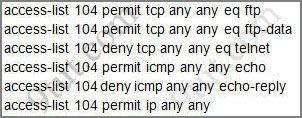
The question does not ask about ftp traffic so we don’t care about the two first lines. The 3rd line denies all telnet traffic and the 4th line allows icmp traffic to be sent (ping). Remember that the access list 104 is applied on the inbound direction so the 5th line “access-list 104 deny icmp any any echo-reply” will not affect our icmp traffic because the “echo-reply” message will be sent over the outbound direction.
Question 2:
What would be the effect of issuing the command ip access-group 114 in to the fa0/0 interface?
A – Attempts to telnet to the router would fail
B – It would allow all traffic from the 10.4.4.0 network
C – IP traffic would be passed through the interface but TCP and UDP traffic would not
D – Routing protocol updates for the 10.4.4.0 network would not be accepted from the fa0/0 interface
Answer: B
Explanation:
From the output of access-list 114: access-list 114 permit ip 10.4.4.0 0.0.0.255 any we can easily understand that this access list allows all traffic (ip) from 10.4.4.0/24 network
Question 3:
What would be the effect of issuing the command access-group 115 in on the s0/0/1 interface?
A – No host could connect to Router through s0/0/1
B – Telnet and ping would work but routing updates would fail.
C – FTP, FTP-DATA, echo, and www would work but telnet would fail
D – Only traffic from the 10.4.4.0 network would pass through the interface
Answer: A
Explanation:
First let’s see what was configured on interface S0/0/1:
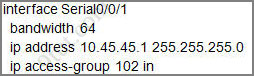
Recall that each interface only accepts one access-list, so when using the command “ip access-group 115 in” on the s0/0/1 interface it will overwrite the initial access-list 102. Therefore any telnet connection will be accepted (so we can eliminate answer C).
B is not correct because if telnet and ping can work then routing updates can, too.
D is not correct because access-list 115 does not mention about 10.4.4.0 network. So the most reasonable answer is A.
But here raise a question…
The wildcard mask of access-list 115, which is 255.255.255.0, means that only host with ip addresses in the form of x.x.x.0 will be accepted. But we all know that x.x.x.0 is likely to be a network address so the answer A: “no host could connect to Router through s0/0/1” seems right…
But what will happen if we don’t use a subnet mask of 255.255.255.0? For example we can use an ip address of 10.45.45.0 255.255.0.0, such a host with that ip address exists and we can connect to the router through that host. Now answer A seems incorrect!
Please comment if you have any idea for this sim!
Other lab-sims on this site:



pls information of cisco send in surajccna123@gmail.com and top institude in india send full information
PLZ I WANT CCNA SOFTWARE SO HOW TO DOWNLOAD PLZ TELL MEEEEE
@ Q1
hi all, the Q1 is not well explained, how do we come by the details of access-list 104?
i can`t see it from the output of the show running-config command up there
somebody please explain to me!!!!!
oh, my mistake i have seen the access-list sorry every body , am ok now
anyone got this question in the exam? any modifications to report? same questions? etc
About Q1, answer B:
Consider the telnet connection THROUGH the router (not TO the router).
For example, we connect another switch2 to router Fa0/1 interface and configure in like first Switch1.
Without “ip access-group 106 in” and without “ip access-group 106 out” in the router configuration, we can telnet from Switch1 to Switch2.
The telnet-packets with destination port 23 will go from Switch1 to Switch2, and then the packets with source port 23 will go back to Switch1.
If we configure “ip access-group 106 out” in the router, the backward telnet-packets from Switch2 to Switch1 with source port 23 will be blocked because of implicit “deny ip any any”.
Telnet connection THROUGH the router will be blocked, but telnet connection TO the router CLI will be permitted.
I configured “access-list 106 deny tcp any eq telnet any”, but the packets from router CLI to Switch1 with source port 23 are still permitted.
Maybe this is made for not to block telnet connection to Cisco devices.
P.S. sorry for my BAD English )))
Any comments to my previous message?
@fanat
so… you’ve removed the access-list filters. no wonder telnetting works from sw1 to sw2 and vice-versa :)
@xallax
You don`t understand.
I:
1) load this sim from 9tut.com and open it in Packet Tracer
2) add new Switch2 and connect it to Router Fa0/1
3) configure Router Fa0/1 with ip 10.5.5.3/24
4) configure Switch2 Vlan1 interface with ip 10.5.5.1/24 and it`s default gateway as 10.5.5.3
5) configure Router and Switch2 vty 0 4 lines with “password cisco” and “login”
6) configure “no ip access-group 106 in” on Router Fa0/0 interface
Now I can telnet from Switch1 to BOTH Router and Switch2 because all access lists are removed.
Then:
7) I configure “ip access-group 106 out” on Router Fa0/0 interface
And now I CANNOT telnet from Switch1 to Switch2 (forward packets will go from Switch1 to Switch2 through Router, and backward packets from Switch2 to Switch1 will be blocked on Router Fa0/0 outbound direction because of implicit “deny ip any any”).
At the same time I CAN telnet form Switch1 to Router (forward packets will go from Switch1 to Router, and backward packets from Router to Switch1 WILL NOT BE BLOCKED, but implicit “deny ip any any” remains)
Why? Am I wrong?
@fanat
yada yada yada
just upload your pkt file somewhere and post the link here so we can all have a look at your config :)
in question 3 we already have an access list so 102 access list is overwrite .and 115 access list does not work here.according t0 102 access list echo reply & telnet deny.and all other traffic is permitted so according to this concept option FTP, FTP-DATA, echo, and www would work but telnet would fail is valid.correct me if i am using wrong logic !!!!!!!!!!!
@xallax please give me answer
Just a comment, interfaces can accept just one access-list per direction, per direction, therefore we can assign two access-list(one In, one out) to the same interface
Sorry per direction, per address
@furqan
also remember that you can have one ACL per direction. 1 in, 1 out.
both acls are inbound .so 115 cannot be given.now give answer
@xallax i am waiting for your answer
@furqan
only hosts with the IP address ending in .0 could send data through the router.
as 9tut explains, this could be possible on class A and class B networks.
since we don’t have that option then we pick the next best one which is option A.
no, there won’t be any ftp, http, icmp traffic going on since the source will most likely not have an IP address that ends with 0
MY MISTAKE ,I WAS C0NFUSING WILDCARD MASK WITH SUBNET MASK.ANYWAYS I G0T THE P0INT THAT LAST 0CTAT IS WE CARE AB0UT & ITS ZER0.AND AS WE CANT ASSIGN NETW0RK ADDRESS T0 H0ST S0 N0 TRAFFIC FL0WS THR0UGH
@furqan
“ip access-group 115 in” overwrites the “acl 102 in” state at interface (you can check it by typing it in), so you get two rules applied to that interface:
1st allows all traffic from addresses that ends with .0 (255.255.255.0 wildcard) and
2nd denies everything else (implicit deny ip any any)
so that’s why there would be no connectivity
btw
@EVERYONE_WHO_LOOKS_FOR_DUMPS
there’s a huge dump collection on http://examcollection.com. Click on “Cisco” link and then search for 640-802
Oh, kinda slowpoke answer)
@xallax
http://dl.dropbox.com/u/15659109/9tut.com_CCNA_Access_List_Sim_WTF.pkt
Here’s modified sim, with problem which was told by Fanat123123, and I don’t understand why is there still full telnet connectivity from RouterC to SwitchC if we put 106 out on fa0/0, too
But that issue is lost when you move 106th acl on fa 0/0 in
@bogdan: ACL is not affected traffic generated by the router. Try to connect a host to Switch0 and to establish telnet connection with SwitchC. You will not able to connect.
I really dont understand the answer to Q1…(unless there is a typo?)
I cant see why Pings wouldn’t work anyway as it is with ACL106 on F0/0 of the router?
doesnt this line allow it..??
“access-list 106 permit icmp any any echo-reply”
@DrumGeek
that rule allows icmp replies that goes to router
in that situation router will be able to ping other network devices: it sends echo-requests through OUT interface, and get echo-replies through IN interface, but it won’t get any ping requests (cuz they are denied with implicit deny ip any any at the bottom of acl) – so it won’t answer with echo-reply, that will entail ping inaccessability of the router
hi
Q1
why i don’t use ACL 102 in instead of 104
thank y 9tut
@ibraham
yep indeed… actually you can use acl 102 in instead of 104. you can ping but can’t telnet.
but none of the answers mention acl 102. so stick it with answer D and “because the “echo-reply” message will be sent over the outbound direction”
sorry if i got it wrong :D
QUESTION 1 :
Remember that the access list 104 is applied on the inbound direction so the 5th line “access-list 104 deny icmp any any echo-reply” will not affect our icmp traffic because the “echo-reply” message will be sent over the outbound direction.
what does these last two lines means ,when it says “echo-reply” message will be sent over the outbound direction.
thanks
@ hamid
“echo-reply” is the answer for “ping” which is generated from router, and router will send the answer out from fa0/0.
Question 3.
as per my knowledge Wild card mask is the inverse of subnetmask so 255.255.255.0 wild card mask means 0.0.0.255 subnetmask, which is wrong subnetmask and all traffic will deny by implicit deny all…
Q3:-
the ans is ‘A’
–b’cus the access-list first apply is source ip + waildcard mask and the last apply is destination ip + waildcard mask……..
–access list 115 the first apply 0.0.0.0 255.255.255.0 is the source ip and the last apply any is destination ip……
Q3:
Doesn’t 0.0.0.0 255.255.255.0 mean the ip address range 0.0.0.0 – 0.0.0.255/24 ?
For Question 3 , acl 115 allows hosts in the 0 subnet, in the ip range of 0.0.0.1 – 0.0.0.254
The above comment “For Question 3 , acl 115 allows hosts in the 0 subnet, in the ip range of 0.0.0.1 – 0.0.0.254″ should be :
For Question 3 , acl 115 allows hosts in the 0 network, in the ip range of 0.0.0.1 – 0.0.0.254
which is not valid (I think).
Sorry about the confusion.
i tot that an access control list should look lyk this: access-list 100 permit ip 192.168.1.0 0.0.0.255 any…..am confused with an access-list that looks lyk this: access-list 100 permit ip 192.168.1.0 255.255.255.0 any…isn’t 255.255.255.0 a subnet mask not a wildcard mask?
0.0.0.0 mean this host only i see it after the ip not before
how it can be ?
Hi
i took the test yesterday basically everything is the same unfortunately i found this site the day before the test and failed have to retake anyway the eigrp sim and vtp sim are the same but there’s an access list sim where you have to give host D access to finance web server while blocking from accessing to anywhere else at the same time you have to block access hosts A,B and C from accessing to webserver and only access to the other webserver.
there’s 2 webservers (1for finance webserver and 1for webserver “dont remember name” those 2 webserver have a class B IPs)
4 hosts A,B,C and D connected to a switch and the switch connected to a Router (same router connecting the 2 web servers and a computer connected to the routers console
If anyone remember this sim can you help me please!!!! email mirazoboy@aol.com
BTW The LAN IP Used is a Class C
I can hardly remember the topology like this http://dl.dropbox.com/u/6887378/Access-list%20packet%20trace.pkt
MZO — Yes, I remember the problem — this is the problem that stopped me from passing.
I panicked. The pen I was given stopped writing. I write big and I take my time figure these things out. I believe the problem said something about 3 lines. I think that the answer has to do with placement (in or out) and implicit deny. Make your own example in packet tracer. Don’t worry about the names or the adddresses. Look at the flow. Look at what you want to block and what you want to allow. Practice so you dont panic
Q. 3
Access-list 115 permit ip 0.0.0.0 255.255.255.0
a wildcard mask.
Int s0/0/1 add. is 10.45.45.1 255.255.255.0
is it a wildcard mask?
means, according to ac-list, any add. first 3 octet may be any number, but the last octet no. must be 1.
anything wrong ! Please put your openion.
Thank-you.
God bless all. I am included too.
Hi,
i going to exam on 10th march and i have prepared only 9tut simulation ac anyone tll me it is sufficient or not.
Q3
personaly i dont know wich network mask match this wildcard…for me is a wrong subnet mask
255.255.255.0 means 10.45.45.1 0.0.0.255
there is somewhone out there who can answer this question 10.45.45.1/???
hi evryone i am new here am contemplating on doing my CCNA, please give me every required information i need to know will be higly appreciated.thanks
my emali add is aleroxgood@yahoo.com. thanks
hi every one i know am not really good but if you really check which i discovered, literally between access list 104 and 106 statement
here it is:
this is what i change and my switch was ping 10.4.4.3 how come did you guys confirm very well…. need urgent answer.
RouterC(config)#int fa0/0
RouterC(config-if)#ip acce
RouterC(config-if)#access-list 106 permit ip any any
RouterC(config)#end
and later configured>
RouterC(config)#int fa0/0
RouterC(config-if)#no ip access-group 104 in
RouterC(config-if)#ip access-group 106 in
RouterC(config-if)#end
RouterC#
%SYS-5-CONFIG_I: Configured from console by console
exit
and here was the ping result
SwitchC>ping 10.4.4.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.4.4.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/5/9 ms
ver good help
cisco X
q3– I think that this is very tricky because I didnt see the 255.255.255.0– originally I saw it as 255.255.255.255 — my mind did a trick on me
@all
plz help me in 2 eq. & give me correct ans…
Which command will show the MAC addresses of stations connected to switch ports?
A. show mac-address
B. show arp
C. show table
D. show switchport
Refer to the exhibit. After a RIP route is marked invalid on Router_1, how much time will elapse before that
route is removed from the routing table?
A. 30 seconds
B. 60 seconds
C. 90 seconds
D. 180 seconds
E. 240 seconds
Answer: B
plz send me correct ans???????????