CCNA – Access List Questions 2
Here you will find answers to Access list Questions – Part 2
Note: If you are not sure about Access list, please read my Access list tutorial.
Question 1
Refer to the exhibit. What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
| router#show access-lists Extended IP access list 110 10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet 20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp 30 deny tcp 172.16.0.0 0.0.255.255 any eq http 40 permit tcp 172.16.0.0 0.0.255.255 any |
A. Traffic will be dropped per line 30 of the ACL.
B. Traffic will be accepted per line 40 of the ACL.
C. Traffic will be dropped, because of the implicit deny all at the end of the ACL.
D. Traffic will be accepted, because the source address is not covered by the ACL.
Answer: C
Explanation
The syntax of an extended access list is:
access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port]
Notice that in our access list, the network 172.16.0.0 0.0.255.255 is specified as the source but the question asks about “HTTP traffic coming from the Internet that is destined for 172.16.12.10″, which means 172.16.0.0 0.0.255.255 is the destination network. So in this case there is no match in our access list and the traffic will be dropped because of the implicit deny all at the end of the ACL. It is surely a tricky question!
Question 2
Refer to the exhibit. Which statement describes the effect that the Router1 configuration has on devices in the 172.16.16.0 subnet when they try to connect to SVR-A using Telnet or SSH?

A. Devices will not be able to use Telnet or SSH.
B. Devices will be able to use SSH, but not Telnet.
C. Devices will be able to use Telnet, but not SSH.
D. Devices will be able to use Telnet and SSH.
Answer: B
Explanation
Let’s analyze the access list 100:
+ 10 permit tcp 172.16.16.0 0.0.0.15 host 172.16.48.63 eq 22: allows TCP traffic from network 172.16.16.0/28 to access host 172.16.48.63 with a destination port of 22 (SSH)
+ 20 permit tcp 172.16.16.0 0.0.0.15 eq telnet host 172.16.48.63: allows TCP traffic from network 172.16.16.0/28 with a source port of 23 (telnet) to access host 172.16.48.63
Notice that if a device wants to telnet (or SSH) to SVR-A server it must use the destination port of 23 (or 22), not a source port of 23 (or 22).
Access list 100 is applied on the inbound direction of Fa0/0 so it will only filter traffic from 172.16.16.0 subnet to the SVR-A server.
Access list 101 is very similar to access list 100 but it is applied on the inbound direction of Fa0/1 so it will filter traffic from SVR-A server to 172.16.16.0 subnet. In ACL 101:
+ 10 permit tcp host 172.16.48.63 eq 22 172.16.16.0 0.0.0.15: allows TCP traffic from host 172.16.48.63 with a source port of 22 (SSH) to access network 172.16.16.0/28.
+ 20 permit tcp host 172.16.48.63 172.16.16.0 0.0.0.15 eq telnet: allows TCP traffic from host 172.16.48.63 to access network 172.16.16.0/28 with a destination port of telnet.
Notice that the returned traffic from SVR-A to network 172.16.16.0/28 (resulting from telnet or SSH session) will have a source port of 23 (Telnet) or 22 (SSH)
In conclusion, the first statements of each ACL will allow devices to “SSH” to SVR-A. But they can’t telnet because of the implicit deny all at the end of the ACL.
In this question, the second statements of each ACL can be considered “wrong” if we intend to filter telnet or SSH traffic and they have no effect on the Telnet or SSH traffic.
Question 3
Refer to the exhibit. Which three variables (router, protocol port, and router ACL direction) apply to an extended ACL that will prevent student 01 from securely browsing the internet?
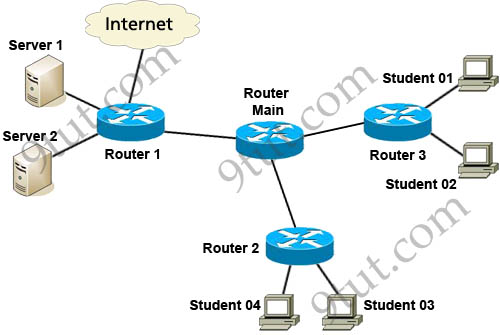
A. OUT
B. Router 3
C. HTTPS
D. IN
E. Router 1
Answer: B C D
Explanation
There are 3 routers we can place this access list: Router 1, Router Main and Router 3 but in theory, an extended access list should be placed close to the source -> Router 3 is the best choice -> B is correct.
The traffic we need to filter here is “securely browsing the internet” so it is HTTPS -> C is correct.
Finally we should apply this access list to the inbound direction so that Router 3 will filter this traffic before making routing decision. It helps save processing resources on Router 3 -> D is correct.
Question 4
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: A F
Explanation
Dynamic ACLs have the following security benefits over standard and static extended ACLs:
+ Use of a challenge mechanism to authenticate individual users
+ Simplified management in large internetworks
+ In many cases, reduction of the amount of router processing that is required for ACLs
+ Reduction of the opportunity for network break-ins by network hackers
+ Creation of dynamic user access through a firewall, without compromising other configured security restrictions
(Reference: CCNA Exploration 4 – Dynamic ACLs)
Question 5
Which command shows if an access list is assigned to an interface?
A. show ip interface [interface] access-lists
B. show ip access-lists interface [interface]
C. show ip interface [interface]
D. show ip access-lists [interface]
Answer: C
Explanation
The output of “show ip interface [interface]” command is shown below:
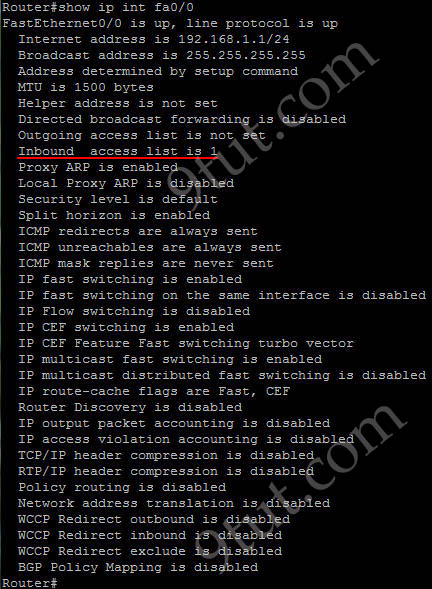
In the output we can see the access list 1 is applied to this interface on inbound direction.
Question 6
Which item represents the standard IP ACL?
A. access-list 50 deny 192.168.1.1 0.0.0.255
B. access-list 110 permit ip any any
C. access-list 2500 deny tcp any host 192.168.1.1 eq 22
D. access-list 101 deny tcp any host 192.168.1.1
Answer: A
Explanation
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
Question 7
Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 8
A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?
A. reflexive
B. extended
C. standard
D. dynamic
Answer: D
Explanation
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml
Question 9
Which parameter standard access list takes into consideration for traffic filtering decisions?
A. Source MAC address
B. Destination IP address
C. Destination MAC address
D. Source IP address
Answer: D
Question 10
In which solution is a router ACL used?
A. protecting a server from unauthorized access
B. controlling path selection, based on the route metric
C. reducing router CPU utilization
D. filtering packets that are passing through a router
Answer: D



Q2: this question seems to be tricky — I dont like questions like this because I may catch the trick on the exam == as per usual — this is not something that I saw while taking the course
@geedub
Well, welcome to the world of networking. It might look tricky, or even complicated. But, once you master the concept, all you need to do is apply it.
Q2. is actually testing your ability of source ports and destination ports, and how to differentiate the two….eg SSH is port 22 and Telnet is port 23.
Hint: master your port numbers…source/destination…….
@geedub..
ACLs are used for security on the network as VLANs would be, so they are tricky as you said but I think easy when you come to understand them how you apply them. Probably you need to go across very many scenarios in order to master them.
The most important trick in question 2 is to know that the ACLs are applied in different directions.
The protocol and its corresponding port number like SSH =22, Telnet =23. Be carefull where they are placed on the ACL statement ( is it at source or destination). ready the question again and remember the direction required. In this case, it is towards the SVR-A, so only consider the first two statements and determine your answer.
I think Networking is very interesting after mastering the concepts, I like it more now.
hi , anyone kindly send me the latest dumps israel_bigay@yahoo.com
thanks
Hi…
Question 4
Which two statements apply to dynamic access lists? (choose two)
in jericho dums i read the ans D and F
and here A and F
which one is correct?
Simplified management in large internetworks.
Q2 there’s something wrong from the output
Network 172.16.16.0/20, MEANS THAT subnet mask is 255.255.240.0 so the wildcard mask will be 0.0.15.255
I’ve a doubt in question no 3.
In this question, it has been specified that an extended ACL that will prevent student 01 from securely browsing the INTERNET should be implemented.
From the diagram given in the question, we can notice that there are two servers in their network itself. As per the answer given, if we apply ACL in Router 3 to block https in inbound direction, the student will not be able to access the servers in his network using HTTPS.
So, Applying ACL in Router 1 in outbound direction to block HTTPS from the source IP of student 1 will satisfy the condition exactly, it seems.
Has any one attempted this question in exam with the given answer and obtained full mark for this question. Please comment.
Hi Jayesh,
For your question, answers A,D and F seems correct. Please go through the link http://www.cisco.com/en/US/docs/ios/11_3/security/configuration/guide/sclock.pdf.
There under the heading ‘Benefits of Lock and Key’(Dynamic access list) we can find answers A and F.
Under the heading ‘When To Use Lock-and-Key’ we can find answer D
After entering access-list statements, tjen you determined that you made a mistake, is there a way where you can modify a specific line without copying it into a text editor?
@ebb
Be specific. Show some examples. It might make your question easy to approach.
can we apply access-list to sub intererfaces???
Passed my Cert today with a 841! its not the highest but its still a pass.
nice job guys
do i have to configurations during ccna exam
@ epi
its printing mistake
it must be 172.16.16.0/28
not /20
hey anyone cand send me the latest dumps please jpaudel1@hotmail.com
hello. can somebody help me in this question http://s1163.photobucket.com/albums/q558/asabata12/?action=view¤t=12.jpg
my answer is letter A because172.16.1.0/24 network is entering router A so the it should be ip access-group 10 in but the answer was letter D access-group 10 out
hello, plz send me latest dump,
Email : mo3taz_mo7amad@yahoo.com
@killerbee
The access-list is Standard, therefore it must be placed close to the destination
Dear all,
you may also want to check below site for some useful resources. Good luck to all of us!
careercert.info
hi 9tut. i have a question from april 2012 dump by acme, c3po on this web link below:
C:\Users\SIMBA\Desktop\nat pat acl.MHT
it would better help me understand if you expalin to me what “mynats” is or what it stands for and is the prefix length the subnet mask, for exaple prefix-lenght 19 would mean class “b”with 3 bits borrowed and incremenrt 32 and prefix-lenght 18 would be class be class “b”with with 2 bits borrowed, therefore increment 64? thanks ur site has been very helpful.
Anonymous May 9th, 2012 hi 9tut. i have a question from april 2012 dump by acme, c3po on this web link below:
C:\Users\SIMBA\Desktop\nat pat acl.MHT
it would better help me understand if you expalin to me what “mynats” is or what it stands for and is the prefix length the subnet mask, for exaple prefix-lenght 19 would mean class “b”with 3 bits borrowed and incremenrt 32 and prefix-lenght 18 would be class be class “b”with with 2 bits borrowed, therefore increment 64? thanks ur site has been very helpful.
@simba: Please read my Access list tutorial: http://www.9tut.com/access-list-tutorial you will understand it.
Q2:
The answer is B but why is it not A? Because I thought for telnet you have to use the access-class command instead of access group. Or do you only use the access-class for telnet and not SSH?
Q10,i thought option A is equally correct,am a bit confused
@bola
User names and passwords are the primary security feature used for authorization, ACL’s can add additional security but they are not the primary security feature.
Hi all, I am taking CCNA 640-802 exam first time on 30/05/2012. Could anyone please send me latest dumps which are valid for UK? My e-mail address is puneet_gill84@yahoo.co.uk. Many thanks.
you cant use port numbers as a source just a destination and this was not used in the course work
suppose i want both access list in question to work what do i do without using the ip permit any any..
suppose i want both access list in question 3 to work what do i do without using the ip permit any any
i see,tnx
@9tut
Question 2: B. >>>> I got it right the first time i answer it from diff. dumps but with wrong reason.
my 1ST REASON is that i thought IP add w/ source port in ACL is wrong syntax :-) coz its not familiar to apply source port we usually saw it on destination…. but then when i check it with the Packet tracer its good and it can be applied… which lead me to….
my 2ND REASON is that i thought SSH have more priority than telnet… like the theory we have in enable password and enable secret which if both is configured the enable secret will be the one to use… :-)
thanks for the tutorial that was a big help !
Thanks to 9TUT. passed 933/1000 .
wow salman good yar
please send me some latest question on samyak1985@gmail.com
@alla! Many Thanks for your input, I wish you could expand bit more on: Question 1
What will happen to HTTP traffic coming from the Internet! I know the ans but not with confidence. Shed more light if you can.
@bmw
What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
router#show access-lists
Extended IP access list 110
10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet
[DENY] … [only TCP traffic] … [coming from 172.16.0.0/16] … [with ANY destination] … [and the destination port is EQual to TELNET]
it drops all attempts by local hosts to access any telnet servers. (on port 23)
20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp
drops all attempts by local hosts to access any SMTP servers (on port 25)
30 deny tcp 172.16.0.0 0.0.255.255 any eq http
drops all attempts by local hosts to access any HTTP servers (on port 80, the regular port to open web pages. in other words: no more google!)
40 permit tcp 172.16.0.0 0.0.255.255 any
allows connections made by local hosts on any other ports except 23, 25 and 80.
*implied line at the end*
deny any any
drop any other traffic coming from anywhere going anywhere (including from outside to the inside).
the question is “What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?”
i see nothing like
“permit tcp any 172.16.0.0 0.0.255.255 eq http” or “permit tcp any host 172.16.12.10 eq http” or anything else similar.
this means but one thing: traffic is dropped.
@9tut
please correct Q1, it has no exhibit so the text referring to the exhibit should be removed. thank you
@xallax: The exhibit here refers to the output of the “show access-lists” command.
@9tut
you’re talking about the output from the CLI. my bad :)
@xallax: VOW that was quite mind boggling, but nicely explained therefor I am thankful to you and your team and many participatns here!
@xallax: VOW that was quite mind boggling, but nicely explained therefor I am thankful to you and your team and many participants here!
@ xallax
I’ve been wondering the same thing. My VCE has the same question:
router# show access-lists
Extended IP access list 110
10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet
20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp
30 deny tcp 172.16.0.0 0.0.255.255 any eq http
40 permit tcp 172.16.0.0 0.0.255.255 any
Q) What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.0 if the traffic is processed by this ACL?
A) Traffic will be dropped per line 30 of the ACL
B) Traffic will be accepted per line 40 of the ACL
C) Traffic will be dropped, because of the implicit deny at the end of the ACL
D) Traffic will be accepted, because the source address is not covered by the ACL
Correct answer is C
I’ve been struggling with this one because it seems like it should be dropped per line 30. And there is a permit statement (line 40) that should allow that range. I’m guessing the answer is C because the permit statement is missing an additional”any”? Can anybody confirm this?
@mike
same as above. there’s no line to permit it so it will be blocked due to the “deny any any” at the end
@xallax
But what about line 40? It is a permit statement that includes 172.16.12.0.
I was under the impression that a packet “trickles down” and ACL and is acted upon the first match, in this case line 40 (which would allow the packet in this case).
If this is not the case, then the ACLs used to allow/disallow TELNET for one host are incorrect, because they have only one line and are dependent on the implicit deny to disallow other hosts. There is no permit ip any any statement on the TELNET acls used in these questions (Question 2 of this page is a good example)
That’s why I’m thinking there must be something wrong with line 40.
Thanks!
OMG, I’ve been studying so much I’m going delirious.
It’s a “deny” statement on line 30…….
Ughh, so my real question is why isn’t it denying the packet based on line 30? The address matches the range and it equals http?
never mind, somehow I didn’t see this question above, i thought it was missing from 9tut.
9tut did an excellent job of explaining, it’s because it’s looking at the source address
hi 9tut and everyone. i have an access-list question i dont know how to figure out the answer. i know that the answer is “c” from the dump but dont know how they got the answer. here is the question below:
an acce-list was writtenb in four statementsshown in the graphic (below). which single access-list statement will combine all four of these statements into a single statement that will have exactly the same effect?
_______________________________________
access-list 10 permit 172.29.16.0 0.0.0.255
access-list 10 permit 172.29.17.0 0.0.0.255
access-list 10 permit 172.29.18.0 0.0.0.255
access-list 10 permit 172.29.19.0 0.0.0.255
_______________________________________
….continued from simba
a. access-list 10 permit 172.29.16.0 0.0.0.255
b. access-list 10 permit 172.29.16.0 0.0.1.255
c. access-list 10 permit 172.29.16.0 0.0.3.255
d. access-list 10 permit 172.29.16.0 0.0.15.255
e. access-list 10 permit 172.29.16.0 0.0.255.255
dump says answer is “c” but I thought “e” would be correct. Just need simple explanation as I already know this is a standard acl. Thanks guys and 9tut.
The question says:
What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
LAN <——— RT <———- Internet
This is what is see… the questions is talking about the traffic that comes from the Internet to the LAN Host… line 30 deny tcp 172.16.0.0 0.0.255.255 any eq http, applies for the traffic from Source 172.16.0.0 to any where using the destinatioan port 80 (internet)
and line 40 permit tcp 172.16.0.0 0.0.255.255 any permitts trafic from the LAN to any where…
So I see that there is not line allowing or permitting the Traffic from the Internet to the LAN… therefore the implicit deny any any line will take effect…
Now… the questions does not specify in which direction the ACL has been applied, assuming the ACL was applied INSIDE from the LAN to the INTERNET and INSIDE from INTERNET to the LAN, C would be the most acceptable answer… buuut, if the ACL was apllied only INSIDE from LAN to INTERNET, therefore there is not answer acceptable in the options provided
Comments?