CCNA – Access List Questions 2
Here you will find answers to Access list Questions – Part 2
Note: If you are not sure about Access list, please read my Access list tutorial.
Question 1
Refer to the exhibit. What will happen to HTTP traffic coming from the Internet that is destined for 172.16.12.10 if the traffic is processed by this ACL?
| router#show access-lists Extended IP access list 110 10 deny tcp 172.16.0.0 0.0.255.255 any eq telnet 20 deny tcp 172.16.0.0 0.0.255.255 any eq smtp 30 deny tcp 172.16.0.0 0.0.255.255 any eq http 40 permit tcp 172.16.0.0 0.0.255.255 any |
A. Traffic will be dropped per line 30 of the ACL.
B. Traffic will be accepted per line 40 of the ACL.
C. Traffic will be dropped, because of the implicit deny all at the end of the ACL.
D. Traffic will be accepted, because the source address is not covered by the ACL.
Answer: C
Explanation
The syntax of an extended access list is:
access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port]
Notice that in our access list, the network 172.16.0.0 0.0.255.255 is specified as the source but the question asks about “HTTP traffic coming from the Internet that is destined for 172.16.12.10″, which means 172.16.0.0 0.0.255.255 is the destination network. So in this case there is no match in our access list and the traffic will be dropped because of the implicit deny all at the end of the ACL. It is surely a tricky question!
Question 2
Refer to the exhibit. Which statement describes the effect that the Router1 configuration has on devices in the 172.16.16.0 subnet when they try to connect to SVR-A using Telnet or SSH?

A. Devices will not be able to use Telnet or SSH.
B. Devices will be able to use SSH, but not Telnet.
C. Devices will be able to use Telnet, but not SSH.
D. Devices will be able to use Telnet and SSH.
Answer: B
Explanation
Let’s analyze the access list 100:
+ 10 permit tcp 172.16.16.0 0.0.0.15 host 172.16.48.63 eq 22: allows TCP traffic from network 172.16.16.0/28 to access host 172.16.48.63 with a destination port of 22 (SSH)
+ 20 permit tcp 172.16.16.0 0.0.0.15 eq telnet host 172.16.48.63: allows TCP traffic from network 172.16.16.0/28 with a source port of 23 (telnet) to access host 172.16.48.63
Notice that if a device wants to telnet (or SSH) to SVR-A server it must use the destination port of 23 (or 22), not a source port of 23 (or 22).
Access list 100 is applied on the inbound direction of Fa0/0 so it will only filter traffic from 172.16.16.0 subnet to the SVR-A server.
Access list 101 is very similar to access list 100 but it is applied on the inbound direction of Fa0/1 so it will filter traffic from SVR-A server to 172.16.16.0 subnet. In ACL 101:
+ 10 permit tcp host 172.16.48.63 eq 22 172.16.16.0 0.0.0.15: allows TCP traffic from host 172.16.48.63 with a source port of 22 (SSH) to access network 172.16.16.0/28.
+ 20 permit tcp host 172.16.48.63 172.16.16.0 0.0.0.15 eq telnet: allows TCP traffic from host 172.16.48.63 to access network 172.16.16.0/28 with a destination port of telnet.
Notice that the returned traffic from SVR-A to network 172.16.16.0/28 (resulting from telnet or SSH session) will have a source port of 23 (Telnet) or 22 (SSH)
In conclusion, the first statements of each ACL will allow devices to “SSH” to SVR-A. But they can’t telnet because of the implicit deny all at the end of the ACL.
In this question, the second statements of each ACL can be considered “wrong” if we intend to filter telnet or SSH traffic and they have no effect on the Telnet or SSH traffic.
Question 3
Refer to the exhibit. Which three variables (router, protocol port, and router ACL direction) apply to an extended ACL that will prevent student 01 from securely browsing the internet?
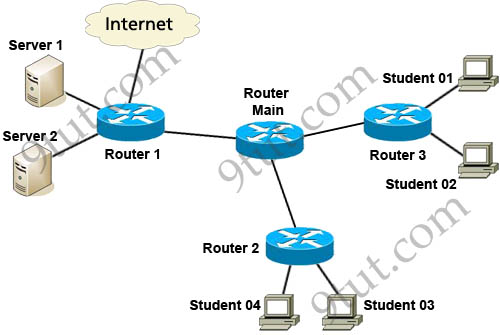
A. OUT
B. Router 3
C. HTTPS
D. IN
E. Router 1
Answer: B C D
Explanation
There are 3 routers we can place this access list: Router 1, Router Main and Router 3 but in theory, an extended access list should be placed close to the source -> Router 3 is the best choice -> B is correct.
The traffic we need to filter here is “securely browsing the internet” so it is HTTPS -> C is correct.
Finally we should apply this access list to the inbound direction so that Router 3 will filter this traffic before making routing decision. It helps save processing resources on Router 3 -> D is correct.
Question 4
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: A F
Explanation
Dynamic ACLs have the following security benefits over standard and static extended ACLs:
+ Use of a challenge mechanism to authenticate individual users
+ Simplified management in large internetworks
+ In many cases, reduction of the amount of router processing that is required for ACLs
+ Reduction of the opportunity for network break-ins by network hackers
+ Creation of dynamic user access through a firewall, without compromising other configured security restrictions
(Reference: CCNA Exploration 4 – Dynamic ACLs)
Question 5
Which command shows if an access list is assigned to an interface?
A. show ip interface [interface] access-lists
B. show ip access-lists interface [interface]
C. show ip interface [interface]
D. show ip access-lists [interface]
Answer: C
Explanation
The output of “show ip interface [interface]” command is shown below:
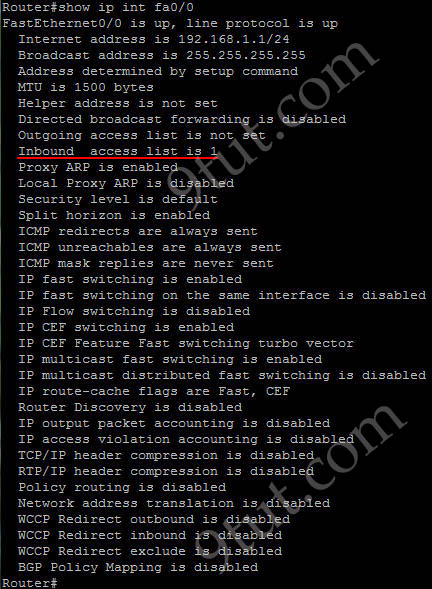
In the output we can see the access list 1 is applied to this interface on inbound direction.
Question 6
Which item represents the standard IP ACL?
A. access-list 50 deny 192.168.1.1 0.0.0.255
B. access-list 110 permit ip any any
C. access-list 2500 deny tcp any host 192.168.1.1 eq 22
D. access-list 101 deny tcp any host 192.168.1.1
Answer: A
Explanation
The standard access lists are ranged from 1 to 99 and from 1300 to 1999 so only access list 50 is a standard access list.
Question 7
Which statement about access lists that are applied to an interface is true?
A. you can apply only one access list on any interface
B. you can configure one access list, per direction, per layer 3 protocol
C. you can place as many access lists as you want on any interface
D. you can configure one access list, per direction, per layer 2 protocol
Answer: B
Explanation
We can have only 1 access list per protocol, per direction and per interface. It means:
+ We can not have 2 inbound access lists on an interface
+ We can have 1 inbound and 1 outbound access list on an interface
Question 8
A network engineer wants to allow a temporary entry for a remote user with a specific username and password so that the user can access the entire network over the internet. Which ACL can be used?
A. reflexive
B. extended
C. standard
D. dynamic
Answer: D
Explanation
We can use a dynamic access list to authenticate a remote user with a specific username and password. The authentication process is done by the router or a central access server such as a TACACS+ or RADIUS server. The configuration of dynamic ACL can be read here: http://www.cisco.com/en/US/tech/tk583/tk822/technologies_tech_note09186a0080094524.shtml
Question 9
Which parameter standard access list takes into consideration for traffic filtering decisions?
A. Source MAC address
B. Destination IP address
C. Destination MAC address
D. Source IP address
Answer: D
Question 10
In which solution is a router ACL used?
A. protecting a server from unauthorized access
B. controlling path selection, based on the route metric
C. reducing router CPU utilization
D. filtering packets that are passing through a router
Answer: D



@ SIMBA
what you need to do first in the question is a summarization:
The normal masks for these networks are as below:
172.29.16.0 255.255.255.0
172.29.17.0 255.255.255.0
172.29.18.0 255.255.255.0
172.29.19.0 255.255.255.0
Now taking into consideration the third octect (where the changes take place):
128 64 32 16 8 4 2 1
0 0 0 1 0 0 0 0 – 16
0 0 0 1 0 0 0 1 – 17
0 0 0 1 0 0 1 0 – 18
0 0 0 1 0 0 1 0 – 19
Look that only the las 2 bits 2 and 1 change to for the networks, bits from 128 to 4 remain the same… that means that we can use the following mask that will take into consideration ONLY the those networks..
172.29.16.0 255.255.252.0
with that you can figure out the wildcard use the following method:
255.255.255.255
(minus) – 255.255.252. 0
———————-
0 . 0 . 3 . 255
The answer will be:
c. access-list 10 permit 172.29.16.0 0.0.3.255
I hope this helps…
Ok, I know this was asked before by Jayesh, but I’m a little confused by Muthu’s response because can only choose two answers.
Who is correct, 9tut or jericho?
Sorry, this pertains to question 4
Question 4
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: A F
Question 3 states to keep student 1 off the internet with HTTPS. If we apply the extended access list to the interface closest to student 01 as we should by convention, then student 1 cannot open a https connection to the servers on our LAN either. So would it not be better to put a out statement on the connection to the internet? Or would we instead add a permit statement on the interface close to the student to allow them internal lan https? Seems like the first choice would be less work so this case problem confuses me…
hi can any one send me the latest dumps (fatma.thabet.89@gmail.com)
hello, plz send me latest dump
email (bido_love41@yahoo.com)
pllllllllllllz i have exam after 5 days
hi can any one send me the latest dumps (jonykhoury@hotmail.com)
@Mohamed @Johny go to http://www.examcollection.com.Read the comments on different dump to find the lastet ones to use. I pass my ccna exam today ! As of 6/20/2012, the following dumps are still valid
Cisco ActualTests 640-802 v2012-02-26 by Jericho 632q.vce
Cisco Acme 640-802 v2012-04-18 by Collisio 487q.vce
Hope this helps!
Question 8
the answer is reflexive acl check the correct answer not dynamic
Muthu,
I do think you are right.
The ACL, as a general rule eare to be placed as close as possible to the source of the traffic that is denied/allow. Standard ACL should be placed as close to the destination as possible.
But: if the student wants to connect to Srv 1 or Srv 2 using HTTPS, then the ACL would be wrong put.
the second “but”: in the questions it is stated only what we need to know and we have to make a decision based on that so the right answer would be “B, C and D”.
Hey guys, xallax and 9tut admin,
Q2 is a very tricky question.
9tut did too many explanation regarding the answer, however, we can point out from the tricky question and from the exhibit, we can conlude that “access-list 101″ will not be included anymore when we analyze the question because it only asked for the “host in 172.16.16.0 subnet to connect to SVR-A”, we only consider “left-to-right” direction, we don’t care about “right-to-left”. so by looking at access-list 100 we can finally conclude that only SSH is allowed, second line is an invalid statement because a host can only establish telnet connection with a destination port number 23 not a source port number 23.
Heloo people I pass the exam with 960 on 27 this moht the questions are from 9tut and I study from Cisco.ActualTest.640-802.v2012-02-26.by.Jericho.632q .vce the simulations are acl2,eigrp,vtp the same from 9tut with difrent ip addresss. Thahks to 9tut
@Kris
you only studied Jericho dump?
well — I finally scheduled the test for tomorrow
Q2: No option is correct if implicit deny come into picture
SSH should be denied due to implicit deny.
hi kris, thank God u passed d exam , please help forward ur dumps to my mail. kmlydd2007@yahoo.co.uk. thanks
Dear all,
can anybody put right access-list for this request, please?
Host C needed to get web (HTTP) access to the Finance server
No other traffic from Host C should be allowed to the finance server
No traffic from the LAN or core should be allowed to the finance server
All hosts in the core and LAN should be able to access the Public web server (did not state protocol)
Please notice that IP address of Public Server is unknown.
Thank you.
i am appearing ccna exam on coming friday 27th and m only following Jericho dumps is that enough please reply as soon as possible have little time for preparation thanks
reply plzzz
please someone tell me that in ACL we deny the traffic through Interface……so is there any other way or place in which we can deny traffic…>>>>>>> plz help me
Hi Anonymous,
ACL do the filtering decision based on the IP addresses. If the physical interface has no IP address and the subinterface has IP address, you put the ACL to that subinterface. Is that what u are asking?
Hi criniks, make sure you know the material and concepts behind them, before following the dumps! I myself passed ICND1 last October, and I’m going to take ICND2 tomorrow. I took this approach because I failed CCNA before, and I realize one-take approach is too much for me. I use Odom’s books and the included network simulator to study. I found out about this site and now come here often. Dumps may help only when you know the material and want to enforce your memory and knowledge, but don’t rely on them totally!
Only questions Without giving notes,its not good..
That too Questions are very less…
I want to thank 9tut and everyone here for his or her contribution. My challenge is that i don’t access-list to my satisfaction no matter the way it is explained most especially the direction of the traffic as in inbound or outbound. I am sitting for the exam next week.
Anticipating your candid reply.
confused gal —- access lists are on the exam — you need to understand them
are Dynamic access lists in the syllabus ? will we get configurations from them too ?
Hi Muditha, the syllabus only mentions ‘describe the purpose and types of ACLs’ And Odom ICND2 book only put dynamic ACL (aka lock-and-key security) in the misc topic with a small section. So I guess we dont have to study the config, for now.
i am confused about Question NO 4 .
9tut say correct answer are A,F
But in dump of Collisio ,jericho the answer is D,F
Who is correct? tell me thank u.
Hi Sarwar, I think it’s safe to say D is not correct as there’s another type of ACL available, i.e. time-based ACL
Q.4) when i went through acl’s i found that “you can set a time-based security policy.” is also an benefit of dynamic acl ?
is that right ?
SOME ANSWERS HERE ARE WRONG
@NAZ CCIE: Please tell me which questions are wrong?
@aJmAL
Define In, Out, Inbound, Outbound, Source, and Destination
This topic is very simple if u draws it from the following scenario
The router uses the terms in, out, source, and destination as references. Traffic on the router can be compared to traffic on the highway. If you were a law enforcement officer in Pennsylvania and wanted to stop a truck going from Maryland to New York, the source of the truck is Maryland and the destination of the truck is New York. The roadblock could be applied at the Pennsylvania–New York border (out) or the Maryland–Pennsylvania border (in). replace with town/cities which u are familiar with.
When you refer to a router, these terms have these meanings.
• Out—Traffic that has already been through the router and leaves the interface. The source is where it has been, on the other side of the router, and the destination is where it goes.
• In—Traffic that arrives on the interface and then goes through the router. The source is where it has been and the destination is where it goes, on the other side of the router.
• Inbound —if the access list is inbound, when the router receives a packet, the Cisco IOS software checks the criteria statements of the access list for a match. If the packet is permitted, the software continues to process the packet. If the packet is denied, the software discards the packet.
• Outbound—if the access list is outbound, after the software receives and routes a packet to the outbound interface, the software checks the criteria statements of the access list for a match. If the packet is permitted, the software transmits the packet. If the packet is denied, the software discards the packet.
The in ACL has a source on a segment of the interface to which it is applied and a destination off of any other interface. The out ACL has a source on a segment of any interface other than the interface to which it is applied and a destination off of the interface to which it is applied.
I just hope that u will grasp one or two things from this scenario.
9tut help me if I am giving this man poison
@9tut
Thnks 4yo valuable website, ques, answers & explanations
Hie all aspiring CCNA network engineers and already in the field?
Can any one send me the vce engine software (Visual CertExam Suite) and dumbs from collision 486q by Jericho 632q or Bruce 564q by DHAKANI 615Q. I tried to google the vce engine, but got a trial version which only exhibited five questions.
My id is musinawellaz@gmail.com
Pliz help- I am preparing for ccna final exam on this month end (August 2012),so pliz again send me latest dumbs from collision 486q by Jericho 632q or Bruce 564q by DHAKANI 615Q.
Here is another site that provides some details at times. It may fit someone learning style:
http://www.freeccnaworkbook.com/labs/
DID IT!!…907…thx 9tut!!!!..CCNA certified….tons of questions from this site…read from top to bottom every question, because you will not know what pops up..q5 on exam…good luck to all!!
Q1 – again I hope not a real exam question unless the structure is wrong here.
Here we have to assume plenty, assume that because we have the source and it is a private range we are therefore using the access list to block or allow certain traffic out of the local network to the web. So that means this ACL could be applied in bound on the internal interface or outbound on the external interface, because it is extended I would put it on the internal interface. Now that we have assumed the placement I would say assuming an appropriate static NAT is in place the web traffic would hit out routers outside interface make its way to the desired destination host (internal) no impact, however the return voyage will encounter the ACL on the inbound interface. Now the catch: “http” is not a valid entry, it should be “web” or 80. So we can ignore line 30 (which the IOS would never have allowed to be entered) and as such the permit 172.16.0.0/16 to Any will apply and the round trip would be a success. In truth there is no correct answer, I think line 30 is a typo, probably meant to be 80 or web.
Tested this in Packet Tracer to confirm.
super sites
please send me ccna interview dumps.
thank you
zakialam125@yahoo.com
please am writing ccna nextweek. please help with vita info. thanks
@all anyone see this in exam?Question 4
Which two statements apply to dynamic access lists? (choose two)
A. they offer simpler management in large internetworks.
B. you can control logging messages.
C. they allow packets to be filtered based on upper-layer session information.
D. you can set a time-based security policy.
E. they provide a level of security against spoofing.
F. they are used to authenticate individual users.
Answer: A F
dumps answers are D and F thanks
On question 1: In line 30 of the ACL, isn’t 172.16.12.10 within the address block of 172.16.0.0/16? Wouldn’t the specified wildcard mask make it 172.16.0.0-172.16.255.255? I figured since ACLs filter traffic from first entry through the last entry, then followed by the implicit deny that line 30 would catch HTTP traffic before the implicit deny would.
I understand question 1 now. I was briefly confused on ACL command syntax. Thanks
Pls, can somebody send me the latest dumps, i have exam this month,
my email is asholet98@hotmail.com
Thanks
@xallax
Refer to following command: access-list permit ip 10.4.4.0 0.0.0.255 any
What would be the effect of issuing the command ip access-group 114 in to the fa0/0 interface?
A-Attempts to telnet to the router would fail.
B-It would allow all traffic from the 10.4.4.0 network.
C-IP traffic would be passed through the Interface but TCP and UDP traffic would not.
D-Routing protocol updates for the 10.4.4.0 network would not be accepted from the fa0/0 interface
the correct answer is B or C
what well be the answer if the question change to:
What would be the effect of issuing the command ip access-group 114 out to the fa0/0 interface?
@smart86
access-list 114 permit ip 10.4.4.0 0.0.0.255 any
allow everything that has a source of 10.4.4.0/24 and goes to anywhere
ip access-group 114 out
allows all outgoing traffic that come from 10.4.4.0/24
ip access-group 114 in
allows all incoming traffic that come from 10.4.4.0/24
notice the 2 keywords IN and OUT
@xallax
so the correct answer as your explanation well be
B for: ( ip access-group 114 in to the fa0/0 interface)
& A for: (ip access-group 114 out to the fa0/0 interface)
is it true
in above i mean C not A for: (ip access-group 114 out to the fa0/0 interface)
@xallax.
please verfiy me if i’m corect or not in :
B for: ( ip access-group 114 in to the fa0/0 interface)
& C for: (ip access-group 114 out to the fa0/0 interface)
is it true
and how about this question:
which layer of osi modal does IPsec operate?
network
transport
session
application
in the dumps they choose transport but I think it is in network layer
@smart86
A-Attempts to telnet to the router would fail.
this is true only if you block the telnet port (23). this is not the case
B-It would allow all traffic from the 10.4.4.0 network.
“FROM”. this is true as the direction for the applied ACL is IN
C-IP traffic would be passed through the Interface but TCP and UDP traffic would not.
IP = TCP+UDP. you can’t have just IP traffic without TCP and UDP. false
D-Routing protocol updates for the 10.4.4.0 network would not be accepted from the fa0/0 interface
there is nothing said about routing updates, the only information given is about passing traffic from a certain source. false
if the direction was OUT then B would still be correct.
it would allow to exit all packets that come from 10.4.4.0/24. this also means “It would allow all traffic from the 10.4.4.0 network”
@smart86
as per wikipedia:
“IPsec is an end-to-end security scheme operating in the Internet Layer of the Internet Protocol Suite.”
Internet Layer in the TCP/IP model is equal to the Network Layer in the OSI model.
you are correct, the first option is correct
Question 1.
Would that access list not be configured on an outbound interface? To deny parts of the 172.16.0.0 Network out. I didn’t think the internet would be processed by this access list as the internet would need an inbound access list? I would have chosen
D. Traffic will be accepted, because the source address is not covered by the ACL.